Ecosyste.ms: Awesome
An open API service indexing awesome lists of open source software.
https://github.com/OWASP/joomscan
OWASP Joomla Vulnerability Scanner Project https://www.secologist.com/
https://github.com/OWASP/joomscan
0day exploit joomla joomla-cms joomscan owasp scanner vulnerability-scanners vunerability
Last synced: 7 days ago
JSON representation
OWASP Joomla Vulnerability Scanner Project https://www.secologist.com/
- Host: GitHub
- URL: https://github.com/OWASP/joomscan
- Owner: OWASP
- License: gpl-3.0
- Created: 2016-09-01T09:06:17.000Z (almost 8 years ago)
- Default Branch: master
- Last Pushed: 2024-04-21T13:09:15.000Z (2 months ago)
- Last Synced: 2024-05-01T11:53:14.483Z (about 2 months ago)
- Topics: 0day, exploit, joomla, joomla-cms, joomscan, owasp, scanner, vulnerability-scanners, vunerability
- Language: Raku
- Homepage: https://www.secologist.com/open-source-projects
- Size: 281 KB
- Stars: 1,016
- Watchers: 55
- Forks: 242
- Open Issues: 21
-
Metadata Files:
- Readme: README.md
- Changelog: CHANGELOG.md
- License: LICENSE.md
Lists
- awesome-bugbounty-tools - joomscan - OWASP Joomla Vulnerability Scanner Project (Miscellaneous / CMS)
- awesome-bugbounty-tools - joomscan - OWASP Joomla Vulnerability Scanner Project (Miscellaneous / CMS)
- awesome-bugbounty-tools - joomscan - OWASP Joomla Vulnerability Scanner Project (Miscellaneous / CMS)
- awesome - joomscan - OWASP Joomla Vulnerability Scanner Project (Raku)
README


[](https://github.com/rezasp/joomscan/blob/master/LICENSE.md)
[](http://twitter.com/OWASP_JoomScan)
[](http://www.twitter.com/rezesp)
[](http://www.twitter.com/Ali_Razmjo0)
[](http://www.toolswatch.org/2018/05/black-hat-arsenal-usa-2018-the-w0w-lineup/)
[](http://www.toolswatch.org/2018/01/black-hat-arsenal-asia-2018-great-lineup/)


======
OWASP JoomScan Project
======
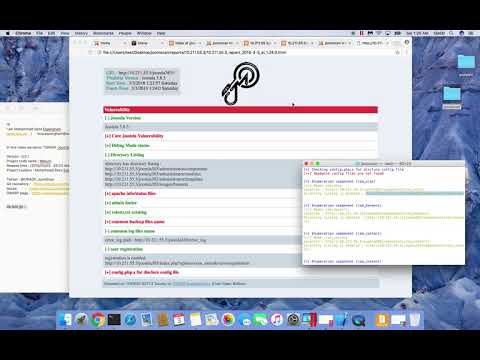
OWASP Joomla! Vulnerability Scanner (JoomScan) is an open source project, developed with the aim of automating the task of vulnerability detection and reliability assurance in Joomla CMS deployments. Implemented in Perl, this tool enables seamless and effortless scanning of Joomla installations, while leaving a minimal footprint with its lightweight and modular architecture. It not only detects known offensive vulnerabilities, but also is able to detect many misconfigurations and admin-level shortcomings that can be exploited by adversaries to compromise the system. Furthermore, OWASP JoomScan provides a user-friendly interface and compiles the final reports in both text and HTML formats for ease of use and minimization of reporting overheads.
OWASP JoomScan is included in Kali Linux distributions.
* **Read More**: https://www.secologist.com/open-source-projects
### WHY OWASP JOOMSCAN ?
Automated ...
*Version enumerator
*Vulnerability enumerator (based on version)
*Components enumerator (1209 most popular by default)
*Components vulnerability enumerator (based on version)(+1030 exploit)
*Firewall detector
*Reporting to Text & HTML output
*Finding common log files
*Finding common backup files
# INSTALL
git clone https://github.com/rezasp/joomscan.git
cd joomscan
perl joomscan.pl
For Docker installation and usage
# Build the docker image
docker build -t rezasp/joomscan .
# Run a new docker container with reports directory mounted at the host
docker run -it -v /path/to/reports:/home/joomscan/reports --name joomscan_cli rezasp/joomscan
# For accessing the docker container you can run the following command
docker run -it -v /path/to/reports:/home/joomscan/reports --name joomscan_cli --entrypoint /bin/bash rezasp/joomscan
# JOOMSCAN ARGUMENTS
Usage: joomscan.pl [options]
--url | -u | The Joomla URL/domain to scan.
--enumerate-components | -ec | Try to enumerate components.
--cookie | Set cookie.
--user-agent | -a | Use the specified User-Agent.
--random-agent | -r | Use a random User-Agent.
--timeout | set timeout.
--about | About Author
--update | Update to the latest version.
--help | -h | This help screen.
--version | Output the current version and exit.
# OWASP JOOMSCAN USAGE EXAMPLES
Do default checks...
```perl joomscan.pl --url www.example.com```
or
```perl joomscan.pl -u www.example.com```
Enumerate installed components...
```perl joomscan.pl --url www.example.com --enumerate-components```
or
```perl joomscan.pl -u www.example.com --ec```
Set cookie
```perl joomscan.pl --url www.example.com --cookie "test=demo;"```
Set user-agent
```perl joomscan.pl --url www.example.com --user-agent "Googlebot/2.1 (+http://www.googlebot.com/bot.html)"```
or
```perl joomscan.pl -u www.example.com -a "Googlebot/2.1 (+http://www.googlebot.com/bot.html)"```
Set random user-agent
```perl joomscan.pl -u www.example.com --random-agent```
or
```perl joomscan.pl --url www.example.com -r```
Set proxy
```perl joomscan.pl --url www.example.com --proxy http://127.0.0.1:8080```
or
```perl joomscan.pl -u www.example.com --proxy https://127.0.0.1:443```
Update Joomscan...
```perl joomscan.pl --update```
# OWASP PAGE
[https://www.owasp.org/index.php/Category:OWASP_Joomla_Vulnerability_Scanner_Project](https://www.owasp.org/index.php/Category:OWASP_Joomla_Vulnerability_Scanner_Project)
# GIT REPOSITORY
[https://github.com/rezasp/joomscan](https://github.com/rezasp/joomscan)
# ISSUES
[https://github.com/rezasp/joomscan/issues](https://github.com/rezasp/joomscan/issues)
# PROJECT LEADERS
* Mohammad Reza Espargham [ reza[dot]espargham[at]owasp[dot]org ]
* Ali Razmjoo [ ali[dot]razmjoo[at]owasp[dot]org ]
OWASP JoomScan introduction (Youtube)
[](https://www.youtube.com/watch?v=Ik2CJ9LkuoI)