Ecosyste.ms: Awesome
An open API service indexing awesome lists of open source software.
https://github.com/chaitin/veinmind-tools
veinmind-tools 是由长亭科技自研,基于 veinmind-sdk 打造的容器安全工具集
https://github.com/chaitin/veinmind-tools
cloud-native cloud-security container-security containerd docker image-security security
Last synced: 3 months ago
JSON representation
veinmind-tools 是由长亭科技自研,基于 veinmind-sdk 打造的容器安全工具集
- Host: GitHub
- URL: https://github.com/chaitin/veinmind-tools
- Owner: chaitin
- License: mit
- Created: 2022-02-08T08:12:15.000Z (over 2 years ago)
- Default Branch: master
- Last Pushed: 2024-01-10T09:08:31.000Z (5 months ago)
- Last Synced: 2024-01-28T04:49:41.419Z (5 months ago)
- Topics: cloud-native, cloud-security, container-security, containerd, docker, image-security, security
- Language: Go
- Homepage: https://veinmind.chaitin.com/docs/
- Size: 20.1 MB
- Stars: 1,431
- Watchers: 16
- Forks: 173
- Open Issues: 20
-
Metadata Files:
- Readme: README.en.md
- License: LICENSE
Lists
- awesome-cloud-native-security - veinmind-tools
- awesome-cloud-security - 地址 - tools) (0x02 工具 :hammer_and_wrench: / 2 云原生工具)
- awesome-cloud-native-security - veinmind-tools
- awesome-hacking-lists - chaitin/veinmind-tools - veinmind-tools 是由长亭科技自研,基于 veinmind-sdk 打造的容器安全工具集 (Go)
- awesome-cloud-security - veinmind - 容器安全工具集 (蓝队工具 / IAC(Infrastructure-as-Code)扫描)
- awesome-stars-eryajf - chaitin/veinmind-tools - veinmind-tools 是由长亭科技自研,基于 veinmind-sdk 打造的容器安全工具集 (Go)
- awesome-ops - chaitin/veinmind-tools - 02-08|2024-01-10 | 容器安全工具集,支持容器恶意文件,弱口令,漏洞,后门等扫描能力 | (安全扫描)
README

veinmind-tools



veinmind-tools is self-developed by chaitin technology ,
cloudwalker team incubation,a container security toolset based on veinmind-sdk
## 🔥 Demo
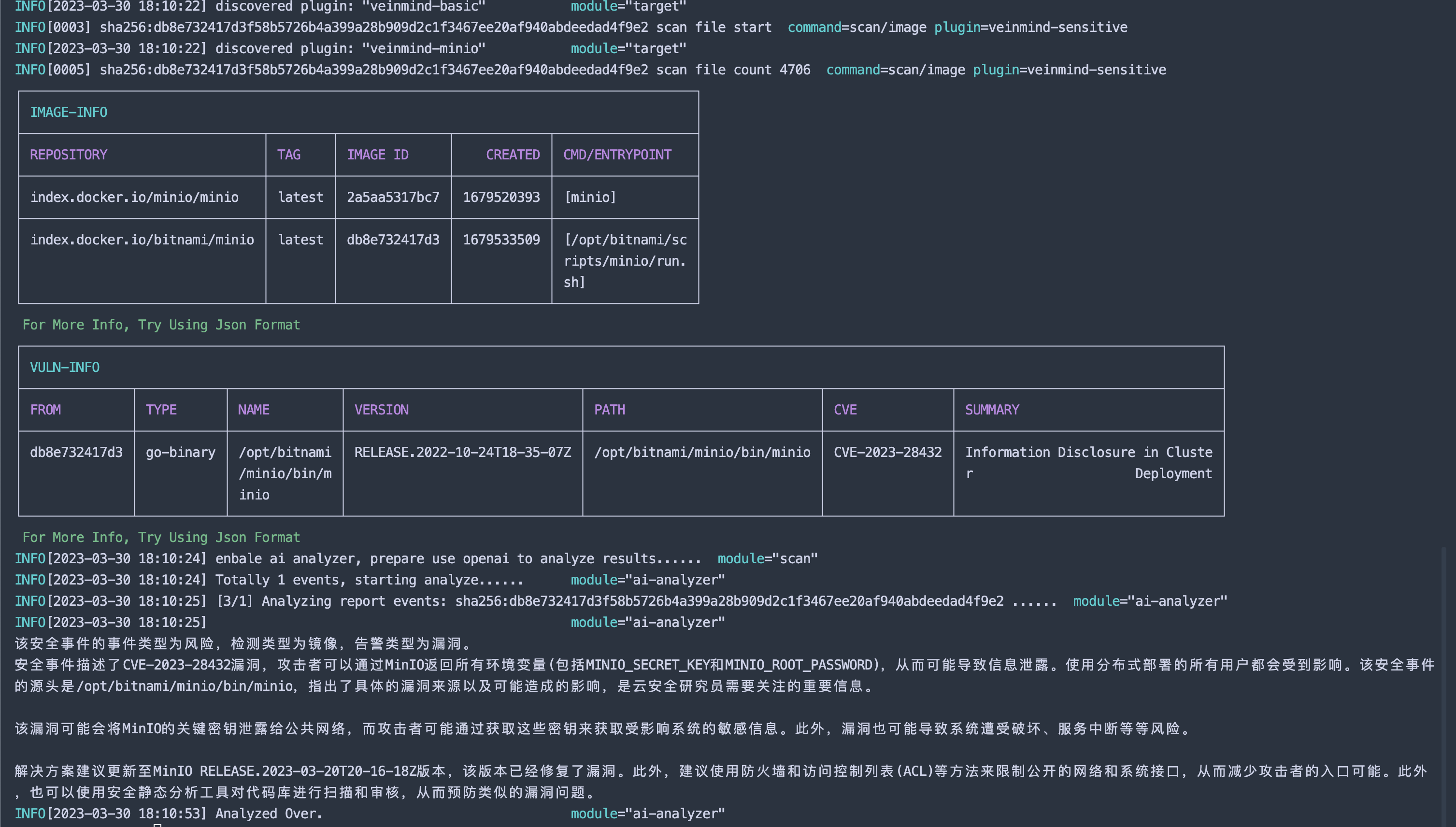
Veinmind has been connected to openai. You can use openai to conduct a user-friendly analysis of the scan results, allowing you to have a clearer understanding of the risks identified during this scan.
## 🕹️ Quick Start
### 1. Make sure docker is installed correctly on the machine
```
docker info
```
### 2. Install [veinmind-runner](https://github.com/chaitin/veinmind-tools/tree/master/veinmind-runner) image
```
docker pull registry.veinmind.tech/veinmind/veinmind-runner:latest
```
### 3. Download [veinmind-runner](https://github.com/chaitin/veinmind-tools/tree/master/veinmind-runner) parallel container startup script
```
wget -q https://download.veinmind.tech/scripts/veinmind-runner-parallel-container-run.sh -O run.sh && chmod +x run.sh
```
### 4. Quick scan local images/containers
```
./run.sh scan [image/container]
```
### 5. use ai analyze
```
./run.sh scan [image/container] --enable-analyze --openai-token
```
> Note: When using openAI, please ensure that the current network can access openAI
> When starting a parallel container, you need to manually use docker run -e http_proxy=xxxx -e https_proxy=xxxx Set proxy (in non global proxy scenarios)
### 6. generate report
```
./run.sh scan [image/container] --format=html,cli
```
> this will generate a file at path which name `report.html` or `report.json`
> you can use `,` to generate different reports,like `--format=html,cli,json` will output both `report.html` and `report.json` and cli table。
## 🔨 Toolset
| Tool | Description |
|---------------------------------------------------------------------------|--------------------------------------------------------|
| [veinmind-runner](veinmind-runner/README.en.md) | scanner host |
| [veinmind-malicious](plugins/go/veinmind-malicious/README.en.md) | Scan containers/images for malicious files |
| [veinmind-weakpass](plugins/go/veinmind-weakpass/README.en.md) | scan containers/images for weak passwords |
| [veinmind-log4j2](plugins/go/veinmind-log4j2/README.en.md) | scan containers/images for log4j2(CVE-2021-44228) |
| [veinmind-minio](plugins/go/veinmind-minio) | scan containers/images for minio(CVE-2023-28432) |
| [veinmind-sensitive](plugins/go/veinmind-sensitive/README.en.md) | scan images for sensitive information |
| [veinmind-backdoor](plugins/go/veinmind-backdoor/README.en.md) | scan images for backdoors |
| [veinmind-history](plugins/python/veinmind-history/README.en.md) | scan images for abnormal history commands |
| [veinmind-vuln](plugins/go/veinmind-vuln/README.en.md) | scan containers/images for asset information and vulns |
| [veinmind-webshell](plugins/go/veinmind-webshell) | scan containers/images for webshell |
| [veinmind-unsafe-mount](plugins/go/veinmind-unsafe-mount) | scan containers for unsafe mount |
| [veinmind-iac](plugins/go/veinmind-iac) | scan images/cluster IaC file |
| [veinmind-escape](plugins/go/veinmind-escape) | scan containers/images for escape risk |
| [veinmind-privilege-escalation](plugins/go/veinmind-privilege-escalation) | scan containers/images for privilege escalation risk |
| [veinmind-trace](plugins/go/veinmind-trace) | scan containers attack trace |
PS: All tools currently support running in parallel containers
## 🧑💻 Coding Plugins
Use example to create a veinmind-tool plugin quickly, see more at [veinmind-example](example/README.en.md)
## ☁️ Cloud-native infrastructure compatibility
| Name | Type | Compatibility |
|--------------------------------------------------------------|----------|---------------|
| [Jenkins](https://github.com/chaitin/veinmind-jenkins) | CI/CD | ✔️ |
| [Gitlab CI](https://veinmind.chaitin.com/docs/ci/gitlab/) | CI/CD | ✔️ |
| [Github Action](https://github.com/chaitin/veinmind-action) | CI/CD | ✔️ |
| DockerHub | Registry | ✔️ |
| Docker Registry | Registry | ✔️ |
| Harbor | Registry | ✔️ |
| Docker | Runtime | ✔️ |
| Containerd | Runtime | ✔️ |
| kubernetes | Cluster | ✔️ |
## 🛴 Architecture

## 🏘️ Contact Us
1. You can make bug feedback and feature suggestions directly through GitHub Issues.
2. By scanning the QR code below (use wechat), you can join the discussion group of veinmind users for detailed
discussions by adding the veinmind assistant.

## ✨ CTStack

veinmind-tools has already joined [CTStack](https://stack.chaitin.com/tool/detail?id=3) community
## ✨ 404 starlink project

veinmind-tools now joined 404 starlink project (https://github.com/knownsec/404StarLink)