Ecosyste.ms: Awesome
An open API service indexing awesome lists of open source software.
https://github.com/Ch0pin/medusa
Binary instrumentation framework based on FRIDA
https://github.com/Ch0pin/medusa
android android-malware dynamic-analysis frida frida-scripts frida-snippets malware medusa penetration-testing pentest
Last synced: 2 months ago
JSON representation
Binary instrumentation framework based on FRIDA
- Host: GitHub
- URL: https://github.com/Ch0pin/medusa
- Owner: Ch0pin
- License: gpl-3.0
- Created: 2020-06-24T08:21:13.000Z (about 4 years ago)
- Default Branch: master
- Last Pushed: 2024-04-13T18:32:46.000Z (3 months ago)
- Last Synced: 2024-04-14T08:53:18.766Z (3 months ago)
- Topics: android, android-malware, dynamic-analysis, frida, frida-scripts, frida-snippets, malware, medusa, penetration-testing, pentest
- Language: Python
- Homepage: https://github.com/Ch0pin/medusa/wiki
- Size: 51 MB
- Stars: 1,372
- Watchers: 43
- Forks: 208
- Open Issues: 5
-
Metadata Files:
- Readme: README.md
- License: LICENSE
Lists
- awesome-stars - Ch0pin/medusa - Binary instrumentation framework based on FRIDA (Python)
- awesome-android-security - MEDUSA
- awesome-android-tools - medusa
- awesome-hacking-lists - Ch0pin/medusa - Binary instrumentation framework based on FRIDA (Python)
- awesome-hacking-lists - medusa - Binary instrumentation framework based on FRIDA (Python)
- awesome-hacking-lists - medusa - Binary instrumentation framework based on FRIDA (Python (1887))
README

# Description
**MEDUSA** is an extensible and modularized framework that automates processes and techniques practiced during the **dynamic analysis** **of Android and iOS Applications**.
# Installation
1. Clone this repo
2. Navigate to the medusa's directory
3. Run the following command:
```
$ pip install -r requirements.txt --upgrade
```
## Known issues
In macOS installation you may encounter the following issue:
>Readline features including tab completion have been disabled because
no supported version of readline was found. To resolve this, install
pyreadline3 on Windows or gnureadline on Linux/Mac.
You can resolve this by installing python's gnureadline:
```
pip install gnureadline
```
## Using docker
You can find the docker file in the medusa/ directory.
1. Build with
```
$ docker build -t medusa:tag1 ./
```
2. Run with
```
$ docker run --name medusa --net=host --rm -it medusa:tag1
```
3. Run adbd in tcp/ip mode in your physical device or emulator
```
$ adb tcpip 5555
```
4. Connect to from the image to your device using:
```
root@docker# adb connect device_ip:5555
```
**System requirements:**
- Linux or macOS (currently medusa doesn't support windows)
- Python 3 (Use the latest python release and not the one shipped with macOS to avoid issues with using libedit instead of GNU's readline)
- Rooted device or emulator
- adb
- FRIDA server (running on the mobile device)
# Usage
### Check our [wiki page](https://github.com/Ch0pin/medusa/wiki) for usage details.
**Demos:**
- [MEDUSA | Android Penetration tool](https://www.youtube.com/watch?v=4hpjRuNJNDw) (credits [@ByteTheories](https://www.youtube.com/@ByteTheories))
- [MEDUSA | Android Malware Analysis 101](https://www.youtube.com/watch?v=kUqucdkVtSU) (credits [@ByteTheories](https://www.youtube.com/@ByteTheories))
- [Unpacking Android malware with Medusa](https://www.youtube.com/watch?v=D2-jREzCE9k) (credits [@cryptax](https://twitter.com/cryptax))
- [Unpacking Android APKs with Medusa](https://www.youtube.com/watch?v=ffM5R2Wfl0A) (credits [@LaurieWired](https://twitter.com/LaurieWired))
- [#Medusa - Extensible binary instrumentation framework based on #FRIDA for Android applications](https://www.youtube.com/watch?v=Hon7zETJawA) (credits [@AndroidAppSec](https://www.youtube.com/@AndroidAppSec))
- [Memory inspection with Medusa](https://www.youtube.com/watch?v=odt21wiUugQ)
- [Bypassing root detection](https://twitter.com/ch0pin/status/1381216805683924994)
Medusa consists of two main scripts: **medusa.py** and **mango.py**:
## Using medusa.py
The main idea behind MEDUSA is to be able to add or remove hooks for Java or Native methods in a large scale while keeping the process simple and effective. MEDUSA has **more than** **90** modules which can be combined, each one of them dedicated to a set of tasks. Indicatively, some of these tasks include:
- SSL pinning bypass
- UI restriction bypass (e.g. Flag secure, button enable)
- Class enumeration
- Monitoring of:
- Encryption process (keys, IVs, data to be encrypted)
- Intents
- Http communications
- Websockets
- Webview events
- File operations
- Database interactions
- Bluetooth operations
- Clipboard
- Monitoring of API calls used by malware applications, such as:
- Spyware
- Click Fraud
- Toll Fraud
- Sms Fraud
Furthermore, you can intercept Java or Native methods that belong to 3rd party apps or create complex frida modules with just few simple commands.
## Using mango.py
Mango is medusa's twin brother which can be used to:
- Parse and analyse the Android manifest
- Enumerate an application's attack entry points (exported activities, deeplinks, services etc.)
- Keep track of all your analysed applications
- Automate boring processes like:
- Set up a MITM
- Patching
- Wrap adb commands
- Set/View/Reset the device's proxy configuration
...and many many more
# Updates:
### (12/2022) Using the translator script:
1. Replace the default google_trans_new.py of you google_trans_new python package with the one from the utils/google_trans_new.py
2. Import it with medusa>use helpers/translator
# Contribute by:
- Making a pull request
- Creating a medusa module (see [how to](https://github.com/Ch0pin/medusa/wiki/Medusa#creating-a-medusa-module))
- Reporting an error/issue
- Suggesting an improvement
- Making this project more popular by sharing it or giving a star
- Buying a treat:
**Bitcoin (BTC) Address**: bc1qhun6a7chkav6mn8fqz3924mr8m3v0wq4r7jchz
**Ethereum (ETH) Address**: 0x0951D1DD2C9F57a9401BfE7D972D0D5A65e71dA4
# Screenshots
#### - SSL Unpinning

#### - Intent Monitoring

#### - Webview Monitoring

#### - File/Content provider monitoring

#### - Native Libraries Enumeration

#### - Memory READ/WRITE/SEARCH (interactive mode):

#### - Personal information exfiltration monitoring
> Hooks api calls which found to be common for this kind of malware, including:
> - Contact exfiltration
> - Call log exfiltration
> - Camera usage
> - Microphone usage
> - Location tracking
> - File uploading
> - Media recording
> - Clipboard tracking
> - Device recon
> - Screenshot capture

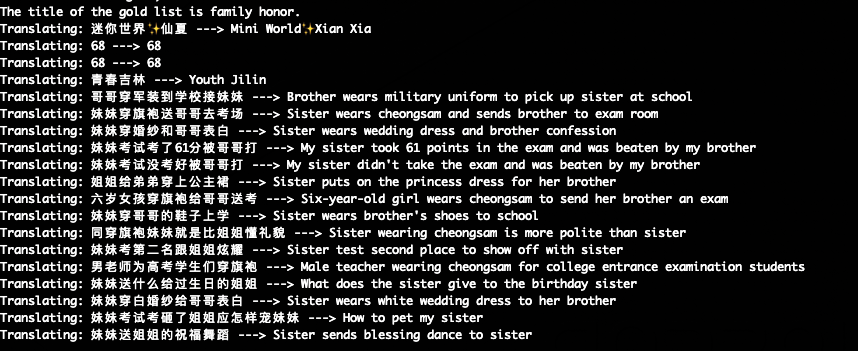
#### - Translation
> Translates the application's UI by hooking 'setText' calls


**CREDITS**:
- Special Credits to [@rscloura](https://github.com/rscloura) for his contributions
- Logo Credits: https://www.linkedin.com/in/rafael-c-ferreira
- https://github.com/frida/frida
- https://github.com/dpnishant/appmon
- https://github.com/brompwnie/uitkyk
- https://github.com/hluwa/FRIDA-DEXDump.git
- https://github.com/shivsahni/APKEnum
- https://github.com/0xdea/frida-scripts
- https://github.com/Areizen/JNI-Frida-Hook