Ecosyste.ms: Awesome
An open API service indexing awesome lists of open source software.
https://github.com/knight0x07/pyc2bytecode
A Python Bytecode Disassembler helping reverse engineers in dissecting Python binaries by disassembling and analyzing the compiled python byte-code(.pyc) files across all python versions (including Python 3.10.*)
https://github.com/knight0x07/pyc2bytecode
blueteam cybersecurity disassembler infosec infosectools malware-analysis malware-research python reverse-engineering security-tools static-analysis threat-intelligence
Last synced: 3 months ago
JSON representation
A Python Bytecode Disassembler helping reverse engineers in dissecting Python binaries by disassembling and analyzing the compiled python byte-code(.pyc) files across all python versions (including Python 3.10.*)
- Host: GitHub
- URL: https://github.com/knight0x07/pyc2bytecode
- Owner: knight0x07
- Created: 2022-01-12T15:38:44.000Z (over 2 years ago)
- Default Branch: main
- Last Pushed: 2023-05-28T21:24:57.000Z (about 1 year ago)
- Last Synced: 2024-01-21T20:48:39.830Z (6 months ago)
- Topics: blueteam, cybersecurity, disassembler, infosec, infosectools, malware-analysis, malware-research, python, reverse-engineering, security-tools, static-analysis, threat-intelligence
- Language: Python
- Homepage:
- Size: 5.86 KB
- Stars: 120
- Watchers: 8
- Forks: 24
- Open Issues: 3
-
Metadata Files:
- Readme: README.md
Lists
- awesome-csirt - pyc2bytecode - code(.pyc) files across all python versions (including Python 3.10.*) (Reverse Engineering / Malware Articles and Sources)
- awesome-csirt - pyc2bytecode - code(.pyc) files across all python versions (including Python 3.10.*) (Reverse Engineering / Malware Articles and Sources)
- awesome-stars - pyc2bytecode - code(.pyc) files across all python versions (including Python 3.10.*) | knight0x07 | 110 | (Python)
- awesome-hacking-lists - knight0x07/pyc2bytecode - A Python Bytecode Disassembler helping reverse engineers in dissecting Python binaries by disassembling and analyzing the compiled python byte-code(.pyc) files across all python versions (including Py (Python)
README
# pyc2bytecode:
A Python Bytecode Disassembler helping reverse engineers in dissecting Python binaries by disassembling and analyzing the compiled python byte-code(.pyc) files across all python versions (including Python 3.10.*)
## Usage:
To run pyc2bytecode:
```
> Console Disassembled Output: python pyc2bytecode.py -p
> Save Disassembled Output to a file: python pyc2bytecode.py -p -o
```
## Demonstration:
**pyc2bytecode** can be used by researchers for reverse engineering Malicious Python Binaries and tear them apart in order to understand the inner workings of the binary statically.
We execute pyc2bytecode.py against **onlyfans.pyc** which is extracted from a recent Python ransomware sample masquerading as an **OnlyFans** executable in the wild using [pyinstxtractor.py](https://github.com/countercept/python-exe-unpacker/blob/master/pyinstxtractor.py)
Following are the analysis results extracted post execution of **pyc2bytecode**:



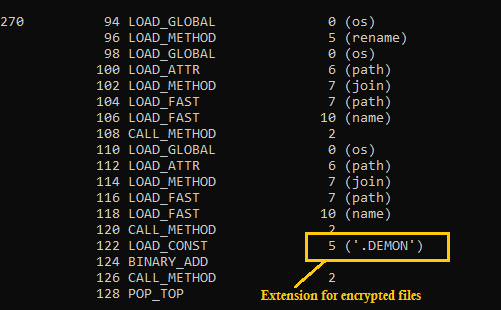

**Extract the Disassembled output into a text file**


## Future Development:
- Develop Python decompiler for recent python versions by using pyc2bytecode (Need to DIS it up :p)
## Credits & References:
i) https://github.com/google/pytype/blob/main/pytype/pyc/magic.py - Magic Numbers
ii) https://nedbatchelder.com/blog/200804/the_structure_of_pyc_files.html - PYC structure
iii) https://docs.python.org/3/library/dis.html - DIS
iv) https://docs.python.org/3/library/marshal.html- Marshal
**Thankyou, Feedback would be greatly appreciated! hope you like the tool :) - knight!**