Ecosyste.ms: Awesome
An open API service indexing awesome lists of open source software.
https://github.com/marakew/syser
syser debugger x32/x64 ring3 with source level debugging/watch view/struct view
https://github.com/marakew/syser
debugger reverse-engineering struct-viewer windows x64 x86-64
Last synced: about 1 month ago
JSON representation
syser debugger x32/x64 ring3 with source level debugging/watch view/struct view
- Host: GitHub
- URL: https://github.com/marakew/syser
- Owner: marakew
- Created: 2018-09-11T18:52:22.000Z (almost 6 years ago)
- Default Branch: master
- Last Pushed: 2024-04-05T12:08:13.000Z (3 months ago)
- Last Synced: 2024-04-05T13:28:43.736Z (3 months ago)
- Topics: debugger, reverse-engineering, struct-viewer, windows, x64, x86-64
- Language: C++
- Homepage: https://gitlab.com/marakew/syser
- Size: 5.79 MB
- Stars: 265
- Watchers: 26
- Forks: 93
- Open Issues: 0
-
Metadata Files:
- Readme: readme.md
Lists
- awesome-assembler - Syser Kernel Debugger - graphical interfaces and supports assembly debugging and source code debugging. (Debuger / Self-hosted hex assemblers)
README
the original [syser debugger](https://github.com/yanfengwu-syser/syserdebugger) now is opensource
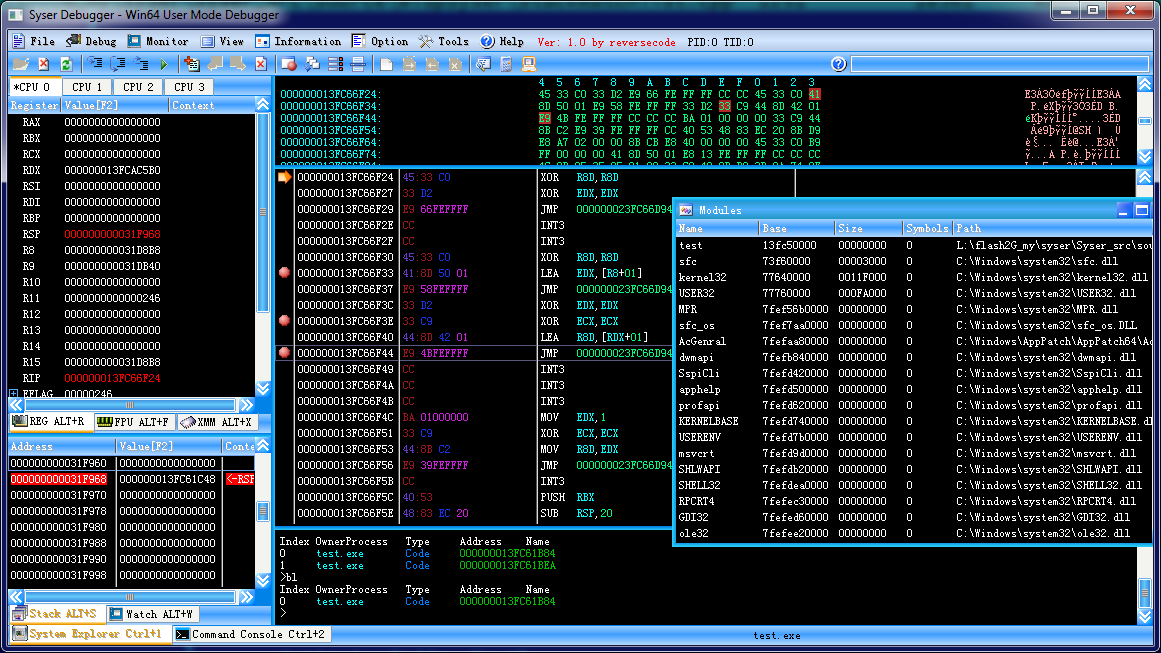
reverse engineering old syser win32 debugger
improved handle x64 arch and fix some bugs
my syser IDA reverse engineering [database idb](https://github.com/marakew/rep/tree/master/syser)
you able to see about my reverse engineering skills
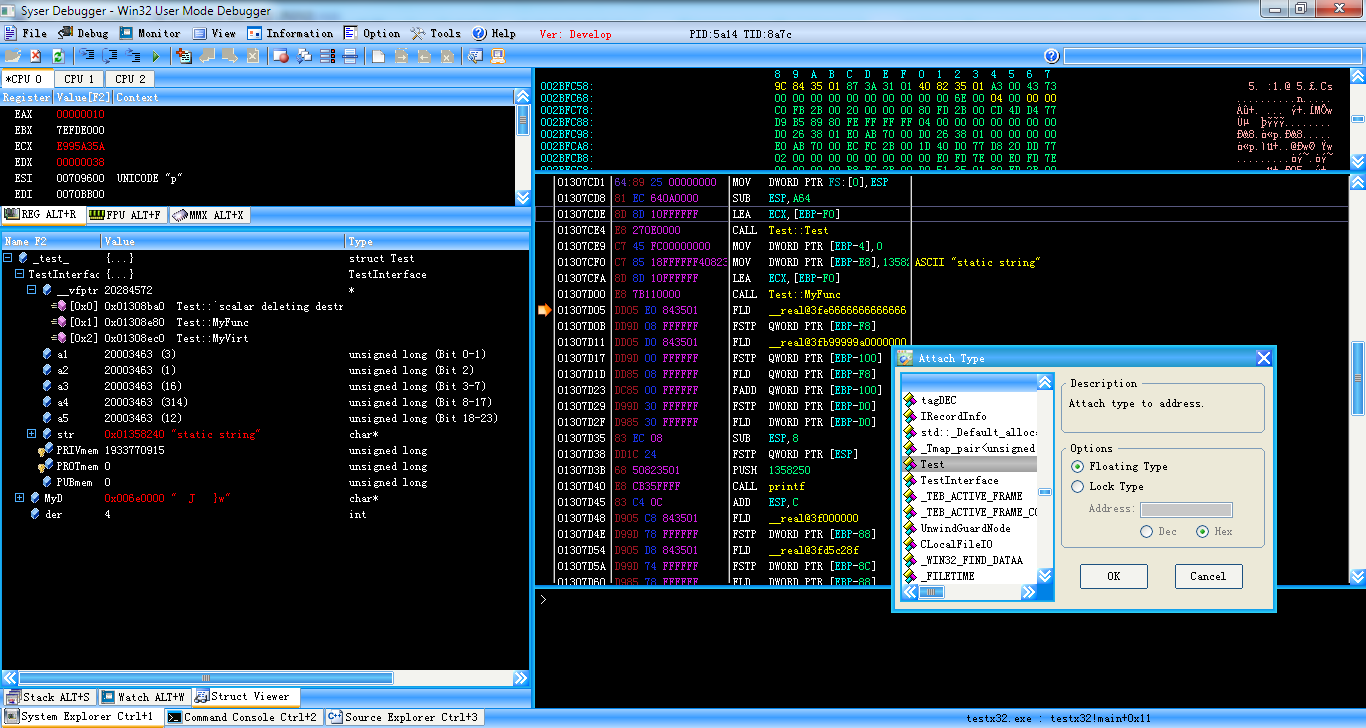
struct viewer
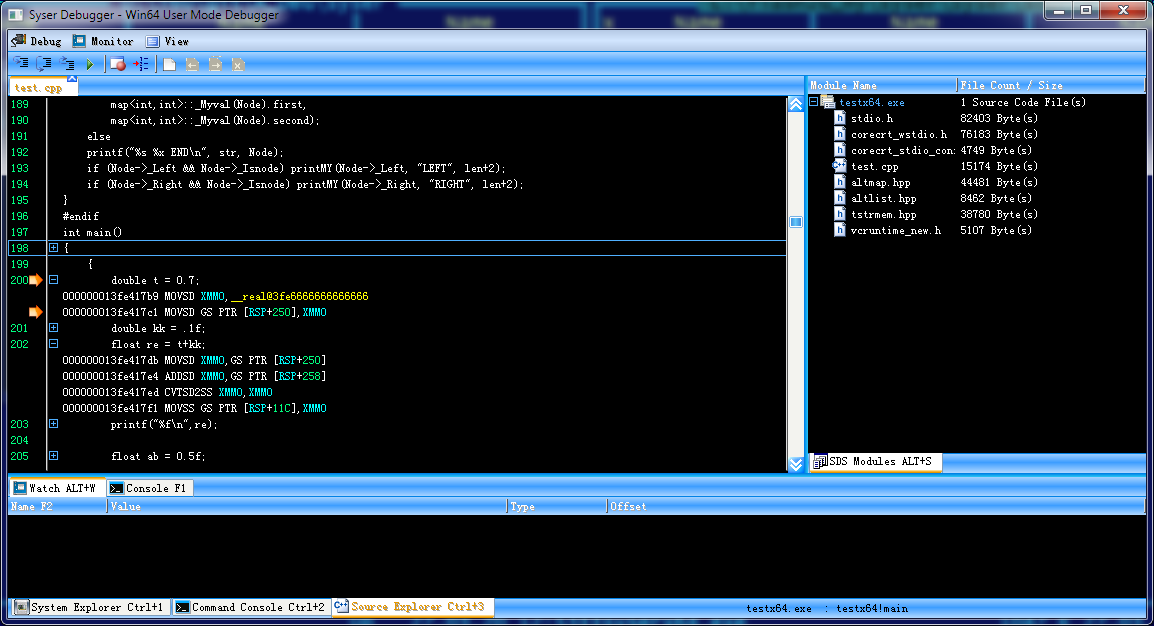
note: pdb2sds.exe .pdb .sds must be same arch!
for source level debugging don't convert .exe to .sds
syser debugger will automatic detect .pdb for .exe
pdb2sds.exe while convert doest include source level debug info
only structs and variables
convert any .pdb or .exe by util pdb2sds.exe
load .sds file from syser menu
Menu "File"->"Load Symbol File"
check from console by command
>sdsmod
File BP(s) Size(k) CheckSum TimeStamp ModuleName
0 0k 00000001 00000001 testx64.pdb
1 Module(s)
start debug .exe
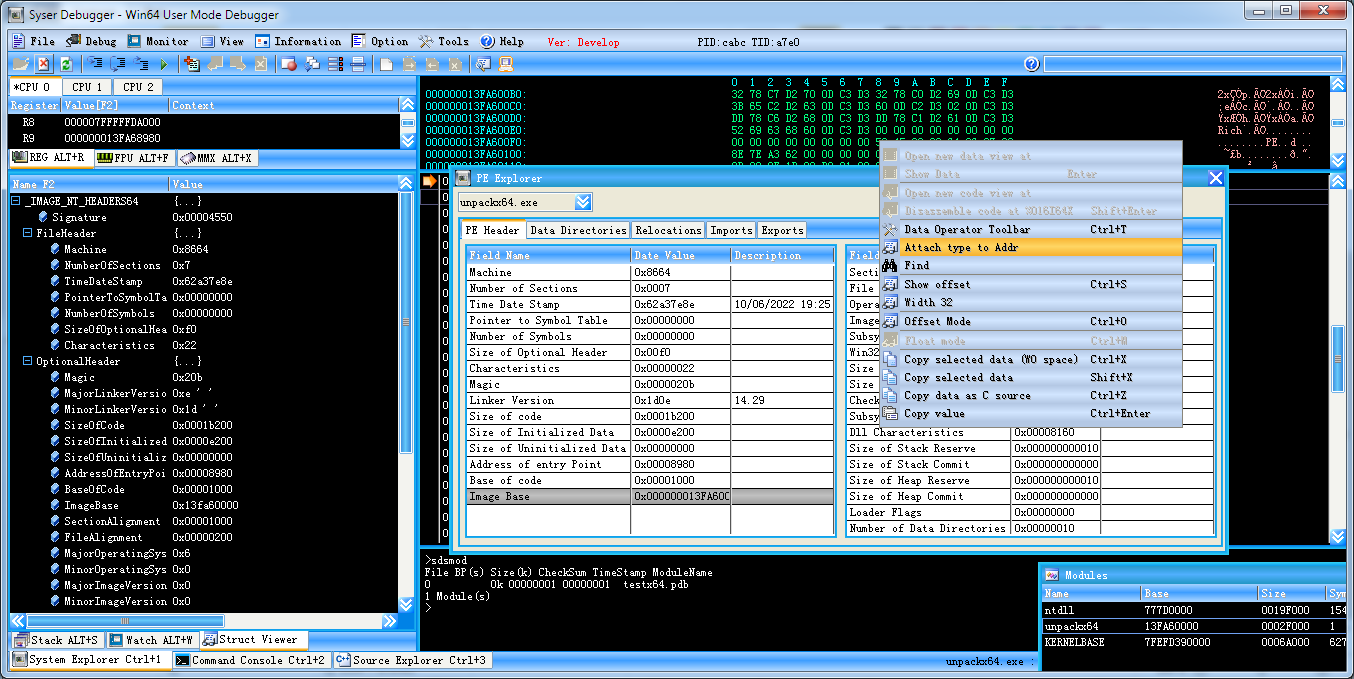
open popup menu on data window by right mouse button
choose a struct by select it
choose "Attach type to Addr"
choose "Lock Type"
enter at "Address" address of struct
[sources](source)
If you want to thank me
```
BTC 3HdQ9tLRoZ1uRGV6rfoDoUhF75DqzJa4UM
```