Ecosyste.ms: Awesome
An open API service indexing awesome lists of open source software.
https://github.com/0x0be/PEpper
An open source script to perform malware static analysis on Portable Executable
https://github.com/0x0be/PEpper
malware malware-analysis python3 static-analysis
Last synced: 3 months ago
JSON representation
An open source script to perform malware static analysis on Portable Executable
- Host: GitHub
- URL: https://github.com/0x0be/PEpper
- Owner: 0x0be
- Created: 2019-07-13T15:15:36.000Z (over 5 years ago)
- Default Branch: master
- Last Pushed: 2023-05-23T00:52:01.000Z (over 1 year ago)
- Last Synced: 2024-08-06T13:11:56.133Z (6 months ago)
- Topics: malware, malware-analysis, python3, static-analysis
- Language: YARA
- Homepage:
- Size: 2.06 MB
- Stars: 309
- Watchers: 18
- Forks: 71
- Open Issues: 3
-
Metadata Files:
- Readme: README.md
Awesome Lists containing this project
README

PEpper
An open source tool to perform malware static analysis on Portable Executable
# Installation
```console
eva@paradise:~$ git clone https://github.com/blackeko/PEpper/
eva@paradise:~$ cd PEpper
eva@paradise:~$ pip3 install -r requirements.txt
eva@paradise:~$ python3 pepper.py ./malware_dir
```
# Screenshot
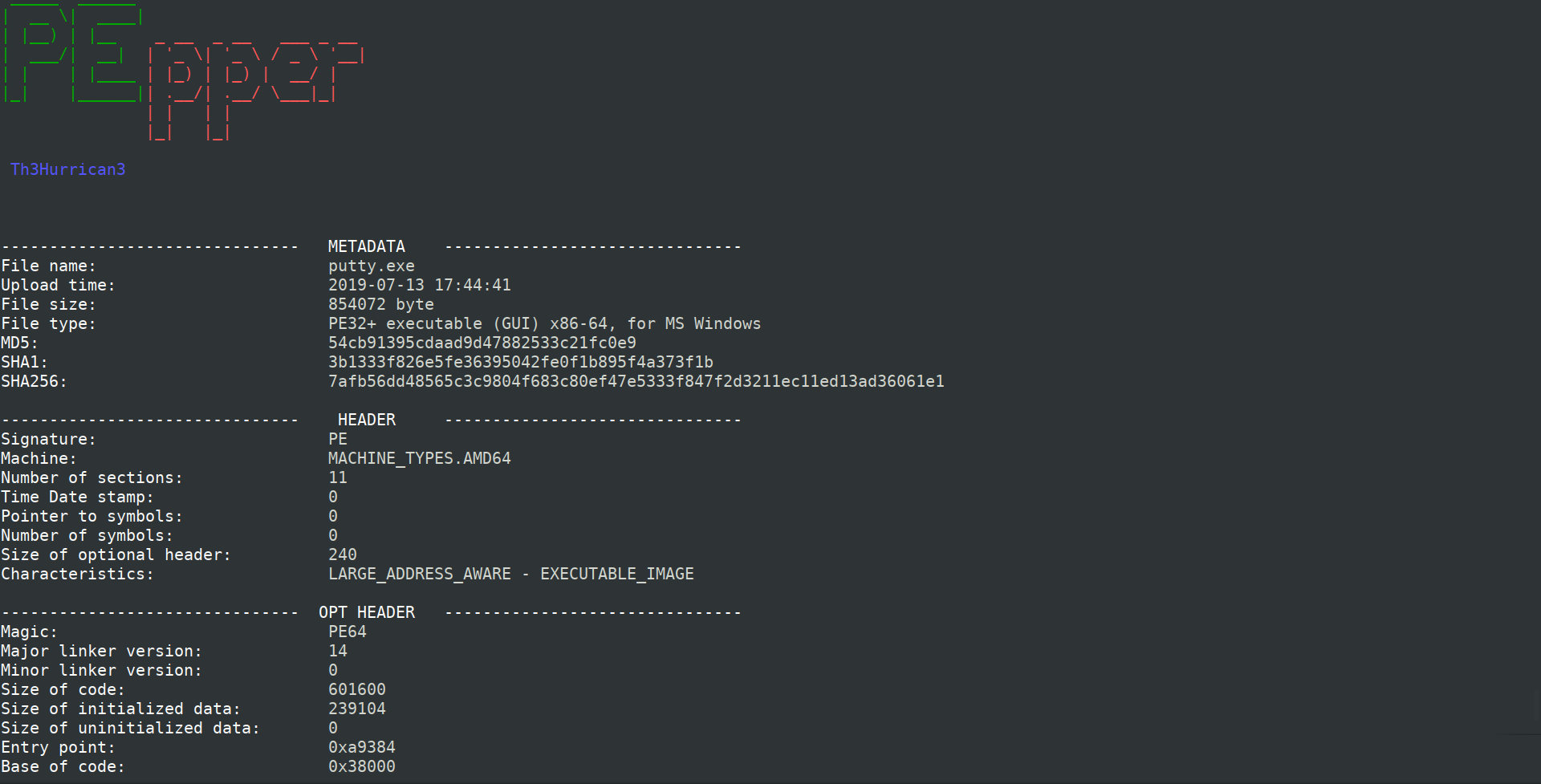
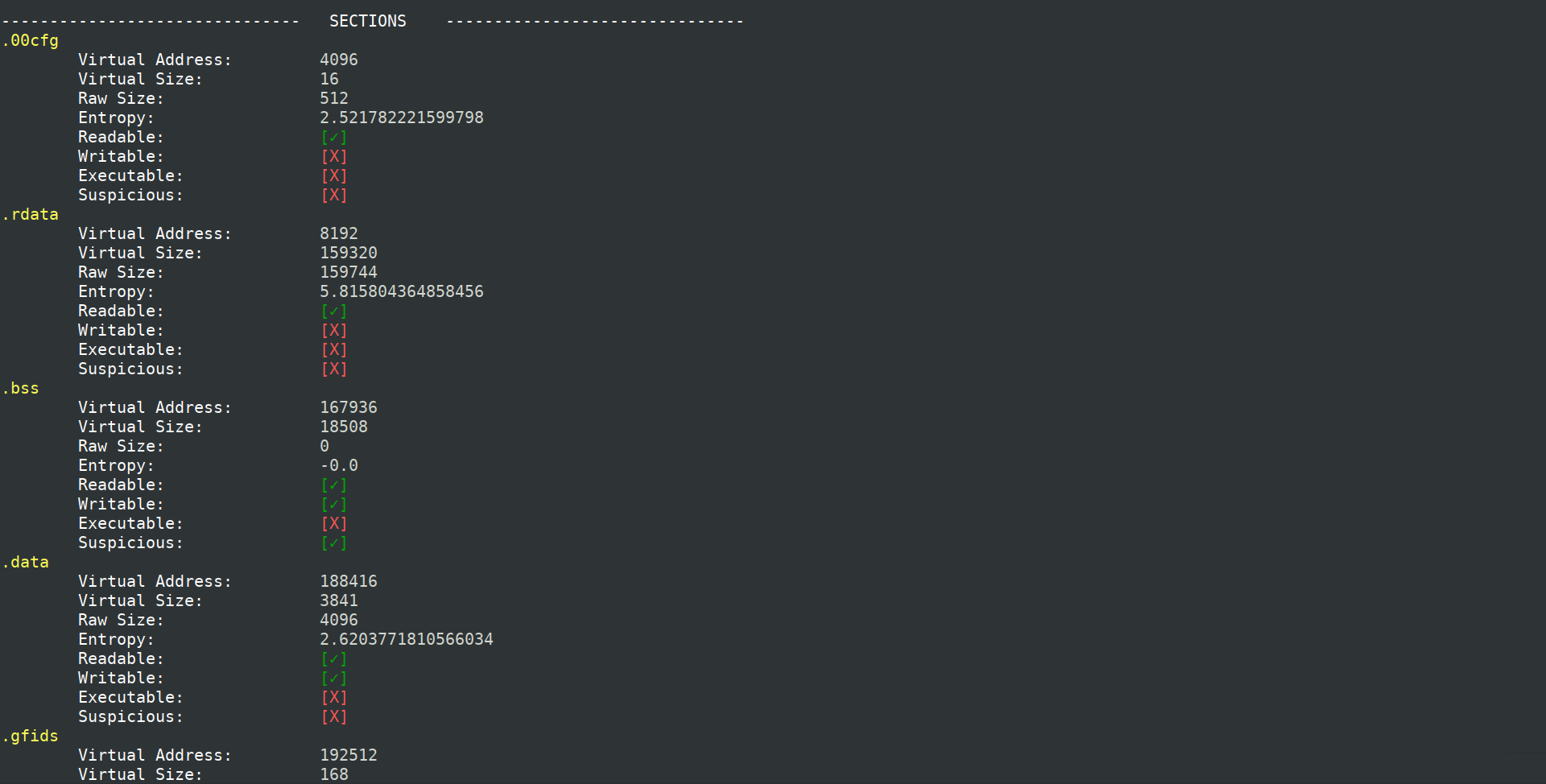
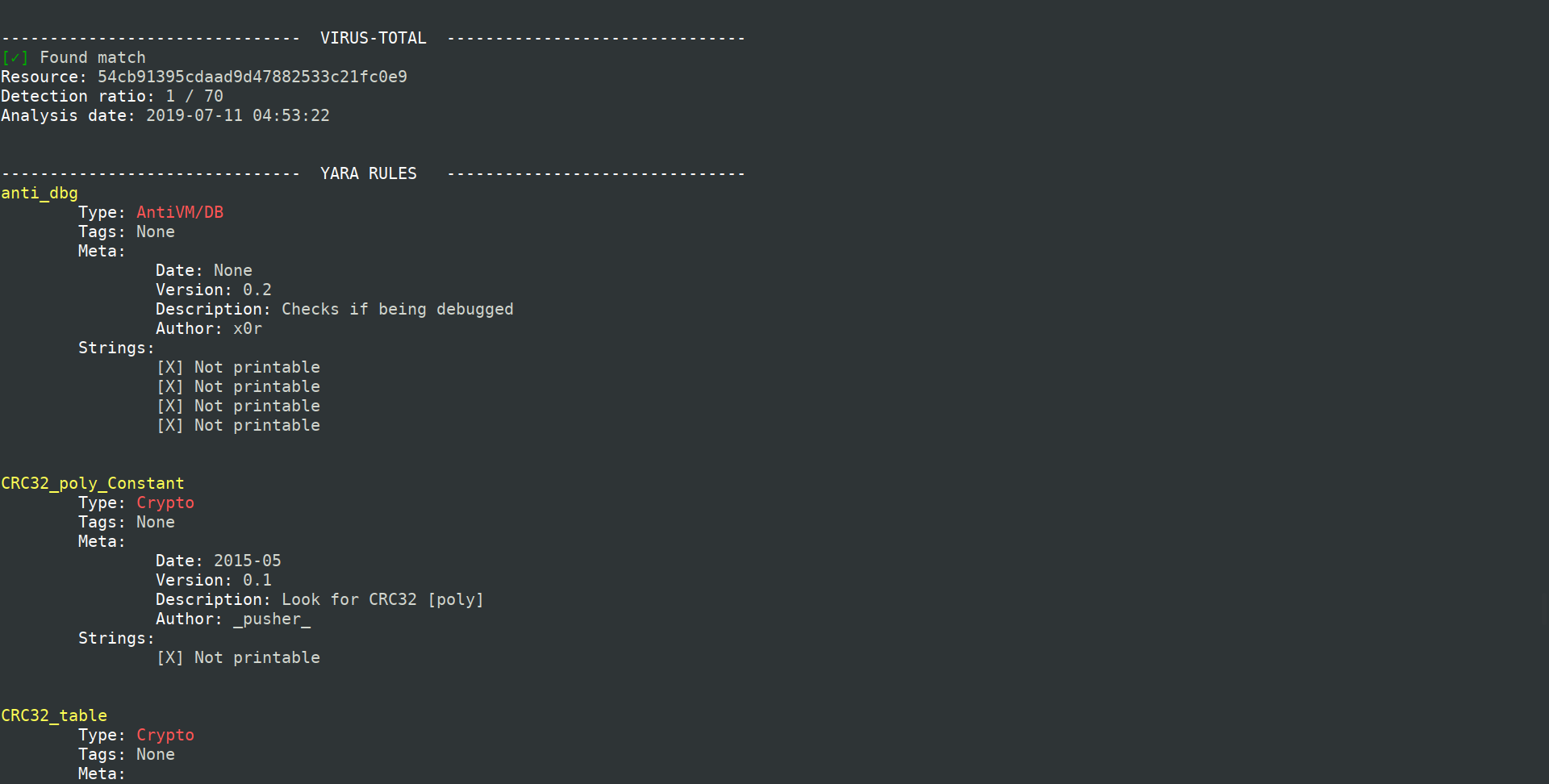
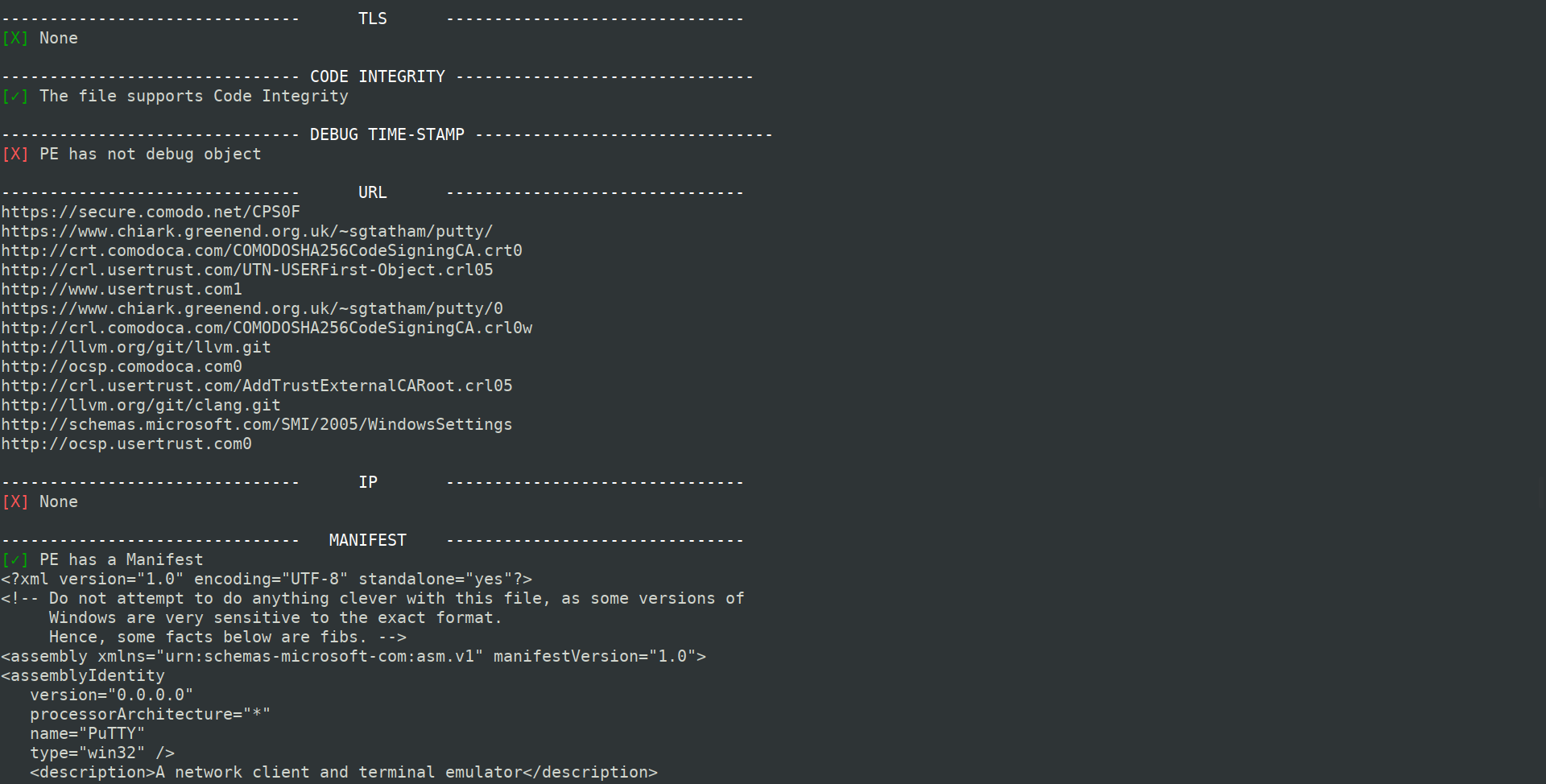
and more rows..
# CSV output
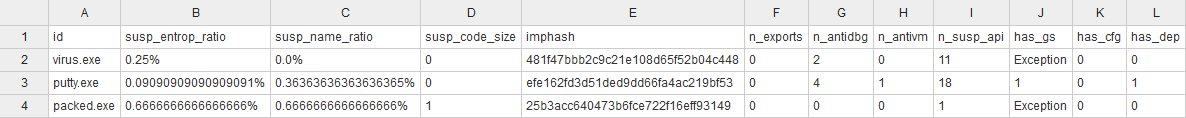
and more columns..
# Feature extracted
- **Suspicious entropy** ratio
- **Suspicious name** ratio
- Suspicious **code size**
- Suspicious **debugging time-stamp**
- Number of **export**
- Number of **anti-debugging** calls
- Number of **virtual-machine detection** calls
- Number of **suspicious API** calls
- Number of **suspicious strings**
- Number of **YARA** rules matches
- Number of **URL** found
- Number of **IP** found
- *Cookie on the stack* (**GS**) support
- *Control Flow Guard* (**CFG**) support
- *Data Execution Prevention* (**DEP**) support
- *Address Space Layout Randomization* (**ASLR**) support
- *Structured Exception Handling* (**SEH**) support
- *Thread Local Storage* (**TLS**) support
- Presence of **manifest**
- Presence of **version**
- Presence of **digital certificate**
- **Packer** detection
- **VirusTotal** database detection
- **Import hash**
# Notes
- Can be run on *single* or *multiple* PE (placed inside a directory)
- Output will be saved (in the same directory of *pepper.py*) as **FILENAME-output.csv**
- To use **VirusTotal scan**, add your private key in the module called "virustotal.py" (Internet connection required)
- 
# Credits
Many thanks to those who indirectly helped me in this work, specially:
- The [LIEF](https://github.com/lief-project/LIEF) project and its awesome library
- [PEstudio](https://www.winitor.com/), a really amazing software to analyze PE
- [PEframe](https://github.com/guelfoweb/peframe) from [guelfoweb](https://github.com/guelfoweb), an incredible widespread tool to perform static analysis on Portable Executable malware and malicious MS Office documents
- [Yara-Rules](https://github.com/Yara-Rules/rules) project, which provides compiled signatures, classified and kept as up to date as possible