https://github.com/0xdea/haruspex
Vulnerability research assistant that extracts pseudocode from the IDA Hex-Rays decompiler.
https://github.com/0xdea/haruspex
ida-plugin ida-pro idalib reverse-engineering vulnerability-research
Last synced: 9 days ago
JSON representation
Vulnerability research assistant that extracts pseudocode from the IDA Hex-Rays decompiler.
- Host: GitHub
- URL: https://github.com/0xdea/haruspex
- Owner: 0xdea
- License: mit
- Created: 2024-11-18T14:09:55.000Z (over 1 year ago)
- Default Branch: master
- Last Pushed: 2026-02-18T10:41:38.000Z (11 days ago)
- Last Synced: 2026-02-18T15:03:56.835Z (11 days ago)
- Topics: ida-plugin, ida-pro, idalib, reverse-engineering, vulnerability-research
- Language: Rust
- Homepage: https://hex-rays.com/ida-pro
- Size: 137 MB
- Stars: 101
- Watchers: 3
- Forks: 8
- Open Issues: 0
-
Metadata Files:
- Readme: README.md
- Changelog: CHANGELOG.md
- License: LICENSE
Awesome Lists containing this project
- awesome-rust - 0xdea/haruspex - Vulnerability research assistant that extracts pseudo-code from the IDA Hex-Rays decompiler [](https://github.com/0xdea/haruspex/actions/workflows/build.yml) (Applications / Security tools)
- fucking-awesome-rust - 0xdea/haruspex - Vulnerability research assistant that extracts pseudo-code from the IDA Hex-Rays decompiler [](https://github.com/0xdea/haruspex/actions/workflows/build.yml) (Applications / Security tools)
- trackawesomelist - 0xdea/haruspex (⭐10) - Vulnerability research assistant that extracts pseudo-code from the IDA Hex-Rays decompiler [](https://github.com/0xdea/haruspex/actions/workflows/build.yml) (Recently Updated / [Feb 05, 2025](/content/2025/02/05/README.md))
- awesome-ida-x64-olly-plugin - haruspex - Rays decompiler. (IDA Plugins)
- awesome-rust-with-stars - 0xdea/haruspex - code from the IDA Hex-Rays decompiler | 2026-01-30 | (Applications / Security tools)
README
# haruspex
[](https://github.com/0xdea/haruspex)
[](https://crates.io/crates/haruspex)
[](https://crates.io/crates/haruspex)
[](https://hex-rays.com/ida-pro)
[](https://twitter.com/0xdea)
[](https://infosec.exchange/@raptor)
[](https://github.com/0xdea/haruspex/actions/workflows/build.yml)
[](https://github.com/0xdea/haruspex/actions/workflows/doc.yml)
> "Hacking is the discipline of questioning all your assumptions all of the time."
>
> -- Dave Aitel
Haruspex is a blazing fast IDA Pro headless plugin that extracts pseudocode generated by IDA Pro's
decompiler in a format that should be suitable to be imported into an IDE, or parsed by static
analysis tools such as [Semgrep](https://semgrep.dev/), [weggli](https://github.com/weggli-rs/weggli),
or [oneiromancer](https://crates.io/crates/oneiromancer).
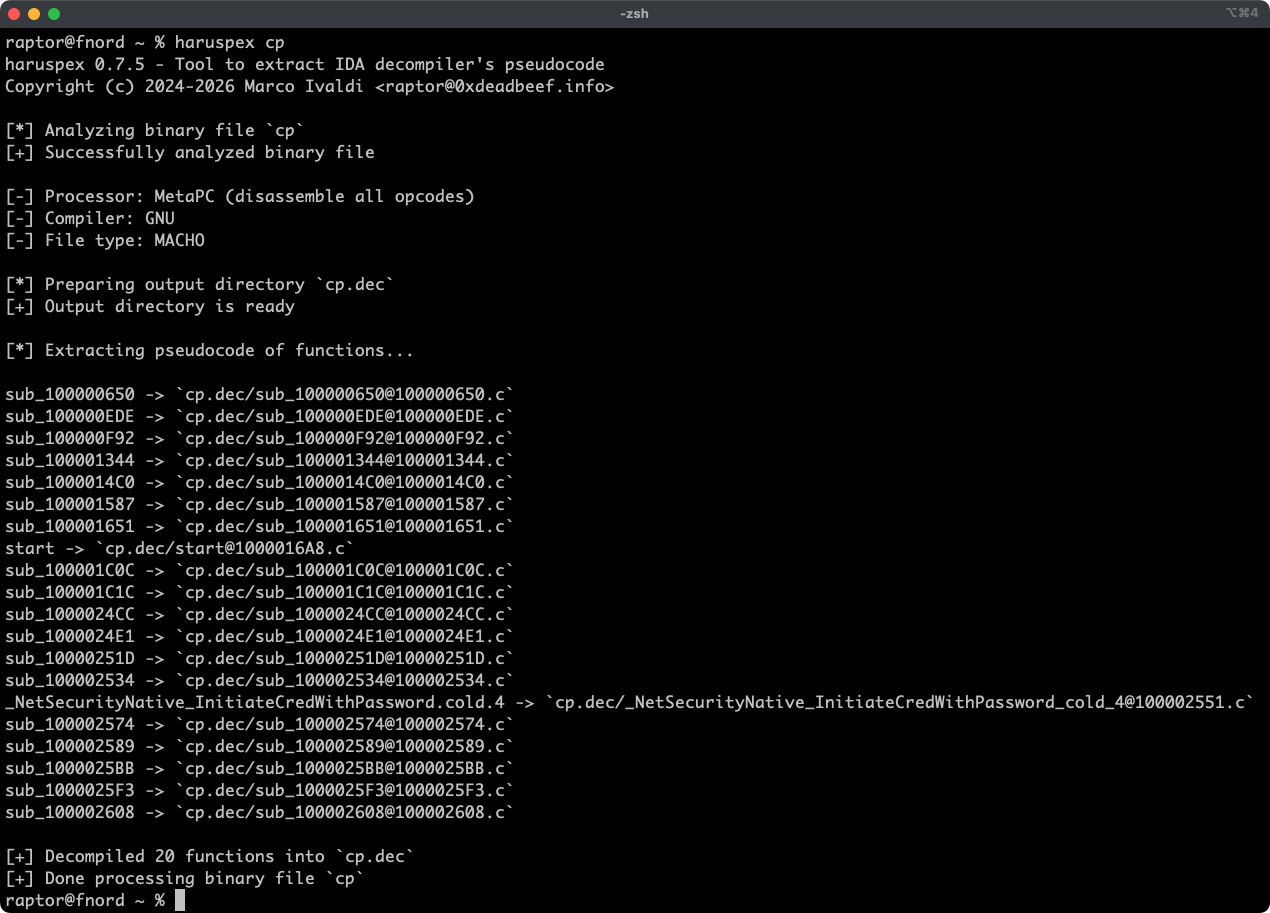
## Features
* Blazing fast, headless user experience courtesy of IDA Pro 9.x and Binarly's idalib Rust bindings.
* Support for binary targets for any architecture implemented by IDA Pro's Hex-Rays decompiler.
* Pseudocode of each function is stored in a separated file in the output directory for easy inspection.
* External crates can invoke [`decompile_to_file`] to decompile a function and save its pseudocode to disk.
## Blog posts
*
*
## See also
*
*
*
*
*
*
*
## Installing
The easiest way to get the latest release is via [crates.io](https://crates.io/crates/haruspex):
1. Download, install, and configure IDA Pro (see ).
2. Install LLVM/Clang (see ).
3. On Linux/macOS, install as follows:
```sh
export IDADIR=/path/to/ida # if not set, the build script will check common locations
cargo install haruspex
```
On Windows, instead, use the following commands:
```powershell
$env:LIBCLANG_PATH="\path\to\clang+llvm\bin"
$env:PATH="\path\to\ida;$env:PATH"
$env:IDADIR="\path\to\ida" # if not set, the build script will check common locations
cargo install haruspex
```
## Compiling
Alternatively, you can build from [source](https://github.com/0xdea/haruspex):
1. Download, install, and configure IDA Pro (see ).
2. Install LLVM/Clang (see ).
3. On Linux/macOS, compile as follows:
```sh
git clone --depth 1 https://github.com/0xdea/haruspex
cd haruspex
export IDADIR=/path/to/ida # if not set, the build script will check common locations
cargo build --release
```
On Windows, instead, use the following commands:
```powershell
git clone --depth 1 https://github.com/0xdea/haruspex
cd haruspex
$env:LIBCLANG_PATH="\path\to\clang+llvm\bin"
$env:PATH="\path\to\ida;$env:PATH"
$env:IDADIR="\path\to\ida" # if not set, the build script will check common locations
cargo build --release
```
## Usage
1. Make sure IDA Pro is properly configured with a valid license.
2. Run as follows:
```sh
haruspex
```
3. Find the extracted pseudocode of each decompiled function in the `binary_file.dec` directory:
```sh
vim .dec
code .dec
```
## Compatibility
* IDA Pro 9.0.240925 - Latest compatible: v0.2.4.
* IDA Pro 9.0.241217 - Latest compatible: v0.3.5.
* IDA Pro 9.1.250226 - Latest compatible: v0.6.2.
* IDA Pro 9.2.250908 - Latest compatible: v0.7.5.
* IDA Pro 9.3.260213 - Latest compatible: current version.
*Note: check [idalib](https://github.com/idalib-rs/idalib) documentation for additional information.*
## Changelog
* [CHANGELOG.md](CHANGELOG.md)
## TODO
* Use the `.cpp` extension instead of `.c` to output pseudocode (see
this [issue](https://github.com/0xdea/semgrep-rules/issues/12))?
* Integrate with Semgrep scanning (see ).
* Integrate with weggli scanning (see ).
* Improve decompiler output in the style of [HexRaysPyTools](https://github.com/igogo-x86/HexRaysPyTools)
and [abyss](https://github.com/patois/abyss).
* Implement parallel analysis (see ).