https://github.com/0xkayala/nucleifuzzer
NucleiFuzzer is a robust automation tool that efficiently detects web application vulnerabilities, including XSS, SQLi, SSRF, and Open Redirects, leveraging advanced scanning and URL enumeration techniques
https://github.com/0xkayala/nucleifuzzer
fuzzing-templates gauplus hakrawler katana nuclei nuclei-templates nucleifuzzer paramspider uro waybackurls
Last synced: 5 months ago
JSON representation
NucleiFuzzer is a robust automation tool that efficiently detects web application vulnerabilities, including XSS, SQLi, SSRF, and Open Redirects, leveraging advanced scanning and URL enumeration techniques
- Host: GitHub
- URL: https://github.com/0xkayala/nucleifuzzer
- Owner: 0xKayala
- Created: 2023-05-22T16:21:15.000Z (over 2 years ago)
- Default Branch: main
- Last Pushed: 2025-03-26T05:37:16.000Z (7 months ago)
- Last Synced: 2025-04-05T19:04:31.794Z (6 months ago)
- Topics: fuzzing-templates, gauplus, hakrawler, katana, nuclei, nuclei-templates, nucleifuzzer, paramspider, uro, waybackurls
- Language: Shell
- Homepage: https://github.com/0xKayala/NucleiFuzzer
- Size: 138 KB
- Stars: 1,494
- Watchers: 16
- Forks: 226
- Open Issues: 0
-
Metadata Files:
- Readme: README.md
- Funding: .github/FUNDING.yml
Awesome Lists containing this project
README
NucleiFuzzer = Nuclei + Paramspider + waybackurls + gauplus + hakrawler + katana + Fuzzing Templates
## Overview
`NucleiFuzzer` is an advanced automation tool designed to streamline and optimize web application security testing by integrating a suite of powerful URL discovery and vulnerability scanning tools. It combines `ParamSpider`, `Waybackurls`, `Katana`, `Gauplus`, and `Hakrawler` to comprehensively gather and enumerate potential entry points for web applications. Leveraging the power of `Nuclei`, it scans these endpoints using `fuzzing-templates` to effectively uncover a wide range of vulnerabilities.
The enhanced `NucleiFuzzer` is built for speed and accuracy, utilizing advanced URL validation, deduplication with `uro`, and precise HTTP filtering using `httpx`. This tool provides `security professionals`, `bug bounty hunters`, and `web developers` with a seamless workflow to detect and address security risks, ensuring robust web application protection.
## Key Features:
1. Comprehensive URL Discovery: Integrates multiple tools (`ParamSpider`, `Waybackurls`, `Katana`, `Gauplus`, and `Hakrawler`) to ensure exhaustive coverage of URLs and parameters.
2. Enhanced Vulnerability Scanning: Uses `Nuclei` with `fuzzing-templates` to identify critical security issues with precision.
3. Advanced Filtering and Validation: Removes duplicates and irrelevant results using `uro` and `httpx` for cleaner and more focused scanning.
4. Rate Limiting for Efficiency: Allows customizable request rates for optimal performance during scans.
5. Customizable and User-Friendly: Easy-to-configure options for domains, files, and output directories, catering to both individual and batch scans.
Take advantage of `NucleiFuzzer` to safeguard your web applications against vulnerabilities and attacks with an enhanced, efficient, and reliable security testing solution!
**Note:** `Nuclei` + `Paramspider` + `waybackurls` + `gauplus` + `hakrawler` + `katana` + `Fuzzing Templates` = `NucleiFuzzer`
**Important:** Make sure the tools `Nuclei`, `Paramspider`, `waybackurls`, `gauplus`, `hakrawler`, `katana`, `httpx` & `uro` are installed on your machine and executing correctly to use the `NucleiFuzzer` without any issues.
### Tools included:
- [Nuclei](https://github.com/projectdiscovery/nuclei) `git clone https://github.com/projectdiscovery/nuclei.git`
- [ParamSpider](https://github.com/0xKayala/ParamSpider) `git clone https://github.com/0xKayala/ParamSpider.git`
- [waybackurls](https://github.com/tomnomnom/waybackurls) `git clone https://github.com/tomnomnom/waybackurls.git`
- [gauplus](https://github.com/bp0lr/gauplus) `git clone https://github.com/bp0lr/gauplus.git`
- [hakrawler](https://github.com/hakluke/hakrawler) `git clone https://github.com/hakluke/hakrawler.git`
- [katana](https://github.com/projectdiscovery/katana) `git clone https://github.com/projectdiscovery/katana.git`
- [httpx](https://github.com/projectdiscovery/httpx) `git clone https://github.com/projectdiscovery/httpx.git`
- [uro](https://github.com/s0md3v/uro) `https://github.com/s0md3v/uro.git`
### Templates:
[Fuzzing Templates](https://github.com/projectdiscovery/nuclei-templates) `git clone https://github.com/projectdiscovery/nuclei-templates.git`
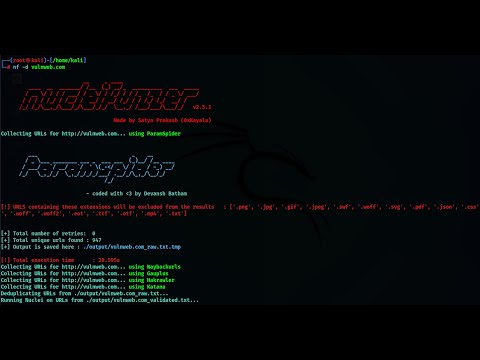
## Screenshot

## Output



## Usage
```sh
nf -h
```
This will display help for the tool. Here are the options it supports.
```console
NucleiFuzzer: A Powerful Automation Tool for Web Vulnerability Scanning
Usage: /usr/bin/nf [options]
Options:
-h, --help Display help information
-d, --domain Single domain to scan for vulnerabilities
-f, --file File containing multiple domains/URLs to scan
-o, --output Specify output folder for scan results (default: ./output)
```
## Installation:
To install `NucleiFuzzer`, follow these steps:
```
git clone https://github.com/0xKayala/NucleiFuzzer.git && cd NucleiFuzzer && sudo chmod +x install.sh && ./install.sh && (command -v nf &> /dev/null && nf -h || echo "Installation failed: Command 'nf' not found. Please check for errors during installation.") && cd .. || echo "Failed to clone or navigate to NucleiFuzzer repository. Please check your setup."
```
## Examples:
Here are a few examples of how to use NucleiFuzzer:
- Run `NucleiFuzzer` on a single domain:
```sh
nf -d example.com
```
- Run `NucleiFuzzer` on multiple domains from a file:
```sh
nf -f file.txt
```
## Practical Demonstration:
For a Practical Demonstration of the NucleiFuzzer tool see the below video 👇
[ ](https://www.youtube.com/embed/2K2gTCHt6kg)
](https://www.youtube.com/embed/2K2gTCHt6kg)
## Star History
## Contributing
Contributions are welcome! If you'd like to contribute to `NucleiFuzzer`, please follow these steps:
1. Fork the repository.
2. Create a new branch.
3. Make your changes and commit them.
4. Submit a pull request.
Made by
`Satya Prakash` | `0xKayala` \
A `Security Researcher` and `Bug Hunter` \
## Connect with me:
## Support me:



