https://github.com/4lph4shell/alphashell-terminal-bash
AlphaShell Host Terminal bash v7.4.7 grom
https://github.com/4lph4shell/alphashell-terminal-bash
base64 brute-force bypass cms database-access ddos ddos-attack-tools decoder dumper eval fake-data hashing-algorithm perl sha256-hash shell shellscript sql terminal-based terminal-emulator whmcs
Last synced: 11 months ago
JSON representation
AlphaShell Host Terminal bash v7.4.7 grom
- Host: GitHub
- URL: https://github.com/4lph4shell/alphashell-terminal-bash
- Owner: 4lph4shell
- License: apache-2.0
- Created: 2024-10-17T15:39:30.000Z (over 1 year ago)
- Default Branch: master
- Last Pushed: 2024-11-27T14:33:11.000Z (over 1 year ago)
- Last Synced: 2024-11-27T15:33:32.271Z (over 1 year ago)
- Topics: base64, brute-force, bypass, cms, database-access, ddos, ddos-attack-tools, decoder, dumper, eval, fake-data, hashing-algorithm, perl, sha256-hash, shell, shellscript, sql, terminal-based, terminal-emulator, whmcs
- Language: PHP
- Homepage: https://4lph4.ir
- Size: 2.51 MB
- Stars: 1
- Watchers: 1
- Forks: 2
- Open Issues: 0
-
Metadata Files:
- Readme: README.md
- License: LICENSE
Awesome Lists containing this project
README
# AlphaShell-Terminal-bash
# Orginal files
AlphaShell-Host/Server-Terminal-bash

# Full Package

Depending on the scope of changes and feature enhancements that are added to an existing web shell’s source code, these updates can be tedious and time consuming for bad actors. For this reason, it’s common to see code for web shells reused among different, unaffiliated attackers.

# Alfa-Shell-v7.4.7-GROM

The ALFA-TEaM shell contains an enormous number of features, the latest version v7.4.7.
When comparing v7.47’s PHP code, we can see the following new features, which are not present in v3 of the web shell:

The first three are just variations of existing features (e.g coldumper) and relatively common among multi-featured PHP web shells.
Let’s focus on the behavior of the last three features: ** fakepage, config_grabber, and archive_manager. **
# Fake Page
In my opinion, ** fakepage ** is of the most interesting new features added to v7.4.7. It allows the attacker to create an on-the-fly phishing page for the two most common hosting control panels: cPanel and DirectAdmin.
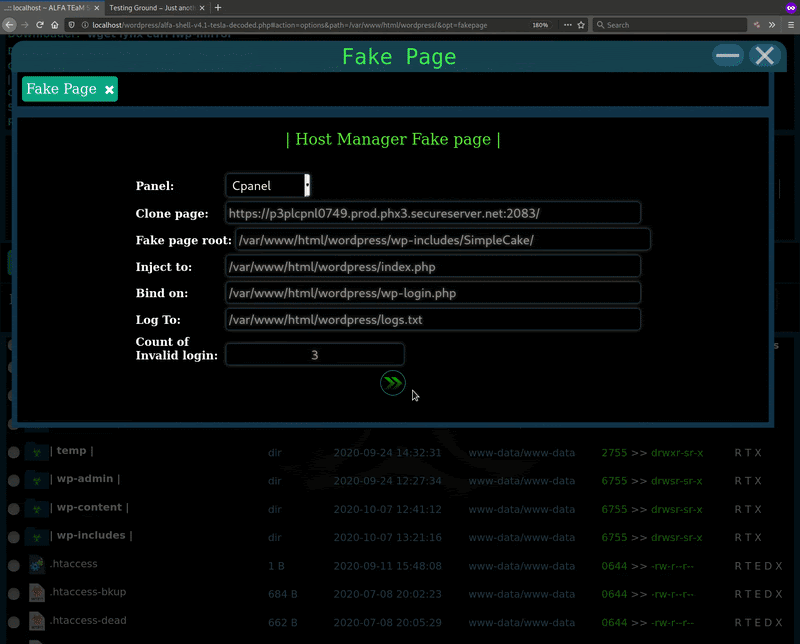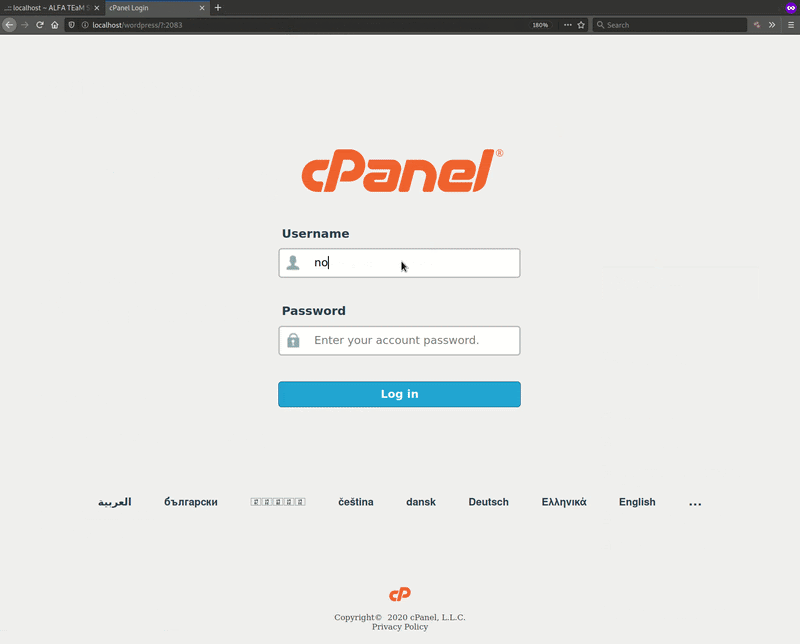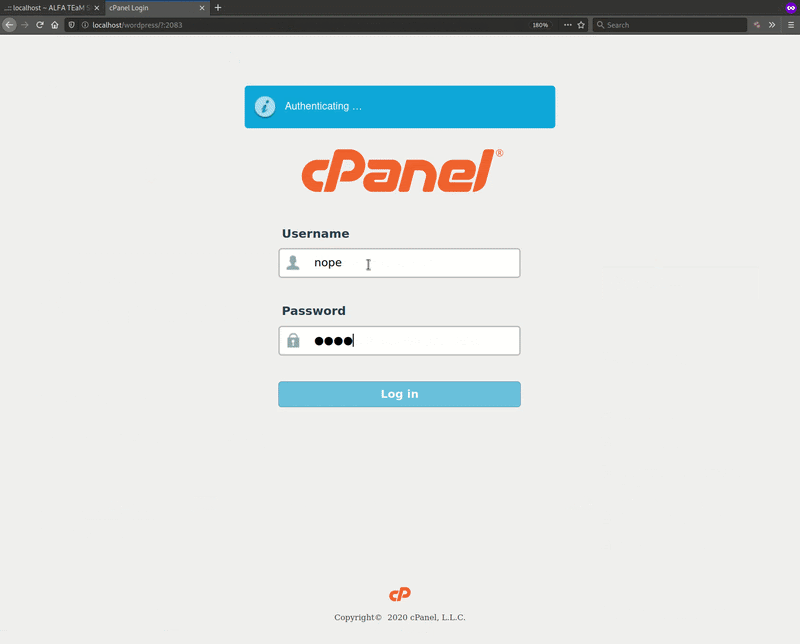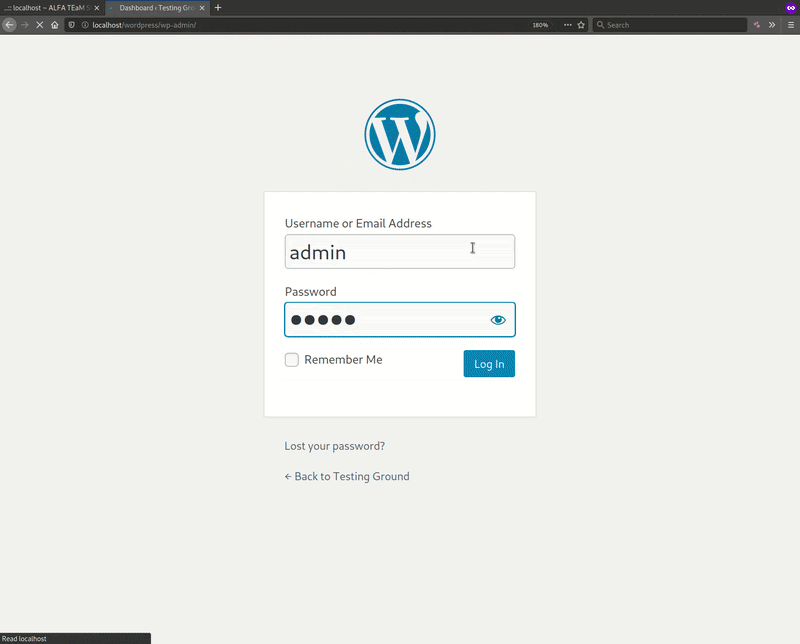
As demonstrated above, there are a few parameters that the attacker can input when setting up the fake control panel page from the web shell. I’ve explained them in more detail below to help you understand what is going on here.
# config_grabber
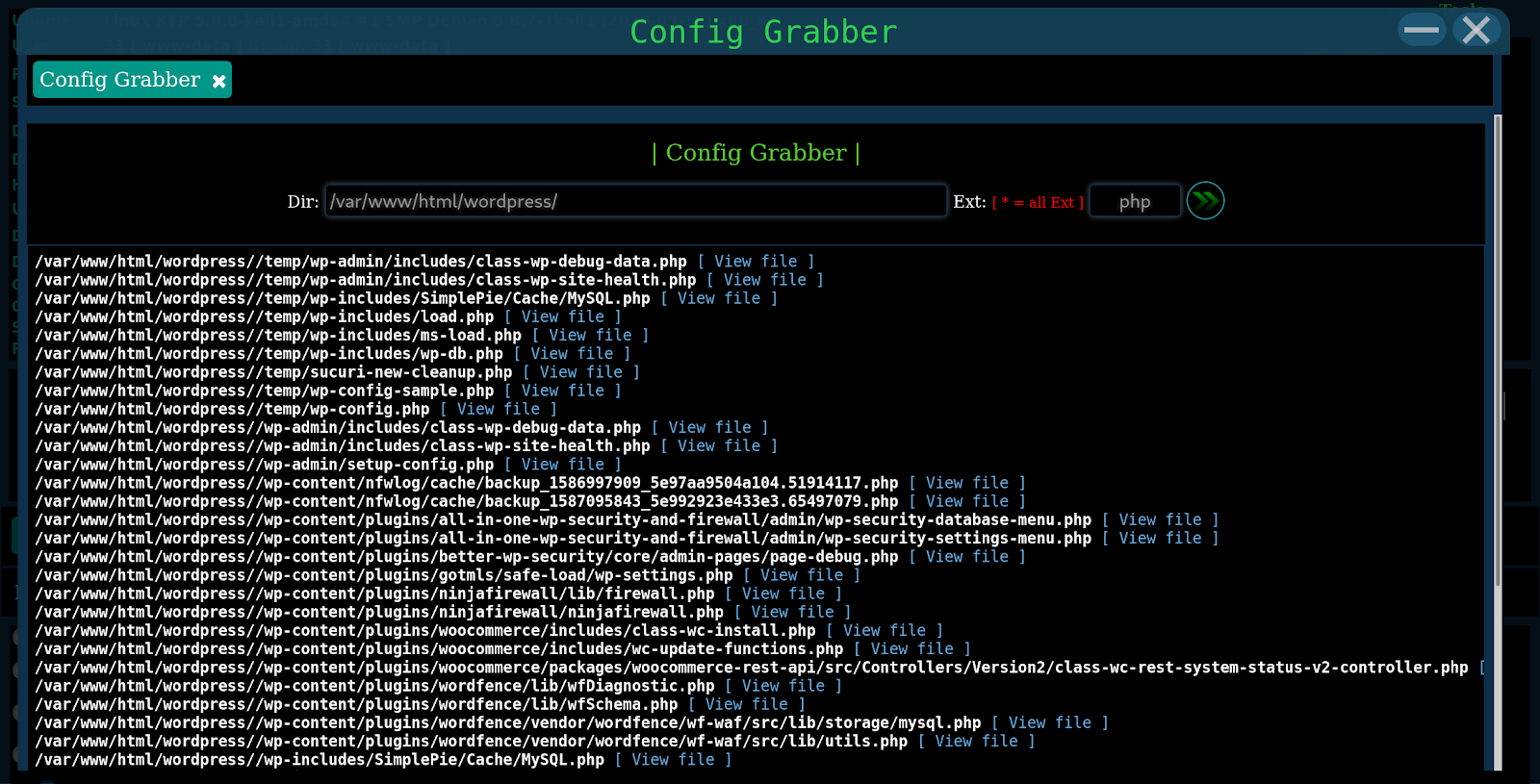
This feature is used to recursively search for configuration files. It uses two functions; alfaconfig_grabber for the display in the web shell and Alfa_ConfigGrabber for performing the search.
While in theory this could be a potentially helpful feature, these searches return many files (as seen above), including those that don’t contain any MySQL database user login information whatsoever. This is due to greedy search terms contained in the $pattern function, causing it to return a lot of unneeded results.
# Archive Manager
)
The Archive Manager feature allows the attacker to quickly unpack archive files (e.g .zip, .tar.gz, .gz, etc) into the server’s memory by generating a Phar PHP resource. The attacker can then manage the contents as if they had unpacked the archive in a file manager, but it is instead loaded into memory and doesn’t unpack to a directory.
## ⚠️ WARNING: LEGAL DISCLAIMER
This tool is intended for **educational and ethical use only**. The author is not liable for any illegal use or misuse of this tool. Users are solely responsible for their actions and must ensure they have explicit permission to scan the target systems.

** ALFA TEaM Shell ~ v7.4.7-GROM ** contains a lot of features useful to an attacker and is also polished in terms of its interface. What is especially interesting is to observe the evolution of the tool and see what features have been added with each new version. This also helps give someone insight into what is important to an attacker, not solely from a website owner’s perspective.
# US


## 🌐 Socials:
[](https://www.4lph4.ir)
[](https://instagram.com/4lph4.co)
[](https://t.me/ALPH4Co)
[](https://t.me/ALPH4ir)
[](https://www.youtube.com/@4lph4co)