https://github.com/649/Apache-Struts-Shodan-Exploit
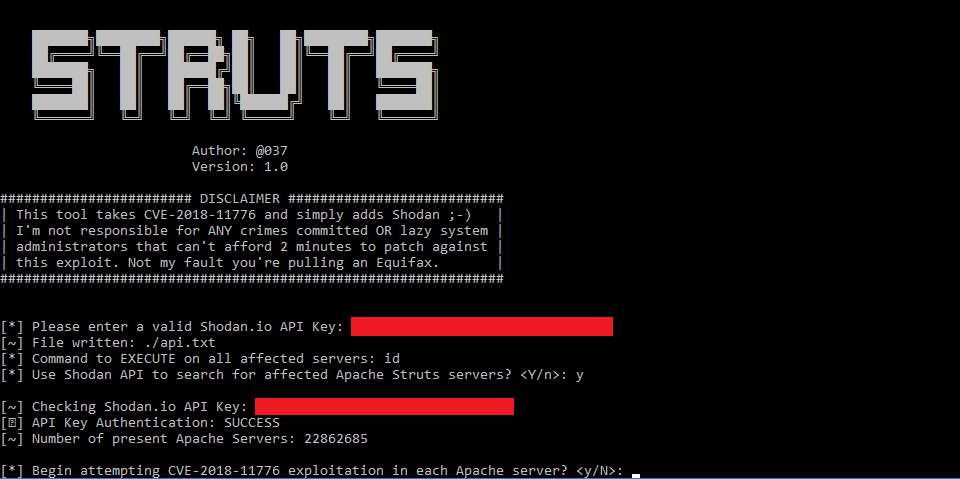
This tool takes advantage of CVE-2018-11776 and Shodan to perform mass exploitation of verified and vulnerable Apache Struts servers.
https://github.com/649/Apache-Struts-Shodan-Exploit
Last synced: 6 months ago
JSON representation
This tool takes advantage of CVE-2018-11776 and Shodan to perform mass exploitation of verified and vulnerable Apache Struts servers.
- Host: GitHub
- URL: https://github.com/649/Apache-Struts-Shodan-Exploit
- Owner: 649
- Created: 2018-08-29T19:50:26.000Z (about 7 years ago)
- Default Branch: master
- Last Pushed: 2018-08-30T00:16:01.000Z (about 7 years ago)
- Last Synced: 2024-11-17T01:28:49.602Z (12 months ago)
- Language: Python
- Size: 23.4 KB
- Stars: 52
- Watchers: 3
- Forks: 16
- Open Issues: 1
-
Metadata Files:
- Readme: README.md
Awesome Lists containing this project
- awesome-ip-search-engines - Apache-Struts-Shodan-Exploit
README
# APACHE STRUTS SHODAN EXPLOIT POC
* Author: [@037](https://twitter.com/037)
Original code can be found [here](https://github.com/hook-s3c/CVE-2018-11776-Python-PoC).
This tool takes advantage of CVE-2018-11776 and Shodan to perform mass exploitation of verified and vulnerable Apache Struts servers.
Shodan search parameter has been left out to weed out any skids trying to use this tool for malicious reasons. This tool is created to be treated as a proof of concept for researchers not an attack tool.
It's important to also mention this tool verifies if the host is vulnerable before performing the exploit process. Making simulated attacks stealthy.
### Prerequisites
You're required to install Python 3.x
```
apt-get install python3
```
You are also required to have Shodan module installed
```
pip install shodan
```
### Using Shodan API
This tool requires you to own an upgraded Shodan API
You may obtain one for free in [Shodan](https://shodan.io/) if you sign up using a .edu email.