https://github.com/649/Pingpon-Exploit
Exploit for Mass Remote Code Execution on GPON home routers (CVE-2018-10562) obtained from Shodan.
https://github.com/649/Pingpon-Exploit
Last synced: 8 months ago
JSON representation
Exploit for Mass Remote Code Execution on GPON home routers (CVE-2018-10562) obtained from Shodan.
- Host: GitHub
- URL: https://github.com/649/Pingpon-Exploit
- Owner: 649
- Created: 2018-05-15T17:31:21.000Z (over 7 years ago)
- Default Branch: master
- Last Pushed: 2018-05-26T06:44:44.000Z (over 7 years ago)
- Last Synced: 2024-11-17T01:28:49.818Z (about 1 year ago)
- Language: Python
- Size: 25.4 KB
- Stars: 21
- Watchers: 1
- Forks: 14
- Open Issues: 0
-
Metadata Files:
- Readme: README.md
Awesome Lists containing this project
- awesome-ip-search-engines - Pingpon Exploit Shodan
README
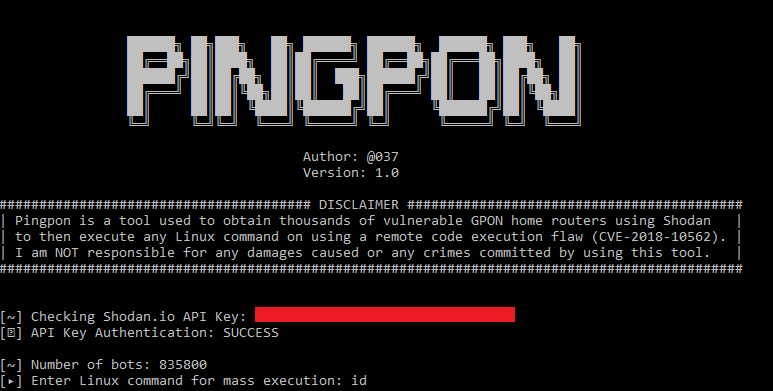
# PINGPON EXPLOIT
* Author: [@037](https://twitter.com/037)
Pingpon is a tool used to obtain thousands of vulnerable GPON home routers using Shodan.io to then execute any Linux command on using a remote code execution flaw (CVE-2018-10562).
## DISCLAIMER
I am NOT responsible for any damages caused or any crimes committed by using this tool.
Original Script: [github.com/f3d0x0/GPON](https://github.com/f3d0x0/GPON)
### Prerequisites
You're required to install Python 3.x
```
apt-get install python3
```
You also require to have the Shodan and Request modules installed
```
pip install shodan
```
```
pip install requests
```
### Using Shodan API
This tool requires you to own an upgraded Shodan API
You may obtain one for free in [Shodan](https://shodan.io/) if you sign up using a .edu email