https://github.com/AlessandroZ/BeRoot
Privilege Escalation Project - Windows / Linux / Mac
https://github.com/AlessandroZ/BeRoot
Last synced: 8 months ago
JSON representation
Privilege Escalation Project - Windows / Linux / Mac
- Host: GitHub
- URL: https://github.com/AlessandroZ/BeRoot
- Owner: AlessandroZ
- License: lgpl-3.0
- Created: 2017-04-14T12:47:31.000Z (over 8 years ago)
- Default Branch: master
- Last Pushed: 2024-10-04T11:54:01.000Z (about 1 year ago)
- Last Synced: 2025-04-11T10:17:25.007Z (8 months ago)
- Language: Python
- Homepage:
- Size: 18.4 MB
- Stars: 2,517
- Watchers: 104
- Forks: 459
- Open Issues: 6
-
Metadata Files:
- Readme: README.md
- License: LICENSE.txt
Awesome Lists containing this project
- awesome-rainmana - AlessandroZ/BeRoot - Privilege Escalation Project - Windows / Linux / Mac (Python)
- awesome-hacking-lists - AlessandroZ/BeRoot - Privilege Escalation Project - Windows / Linux / Mac (Python)
- awesome-privilege-escalation - BeRoot
README
# BeRoot Project
BeRoot Project is a post exploitation tool to check common misconfigurations to find a way to escalate our privilege. \
It has been added to the [pupy](https://github.com/n1nj4sec/pupy/) project as a post exploitation module (so it will be executed in memory without touching the disk).
This tool does not realize any exploitation. It mains goal is not to realize a configuration assessment of the host (listing all services, all processes, all network connection, etc.) but to print only information that have been found as potential way to escalate our privilege.
This project works on Windows, Linux and Mac OS. You could find the Windows version [here](https://github.com/AlessandroZ/BeRoot/tree/master/Windows) and the Linux and Mac OS [here](https://github.com/AlessandroZ/BeRoot/tree/master/Linux)
I recommend reading the README depending on the targeted OS, to better understand what's happening.
I tried to implement most techniques described in this picture:
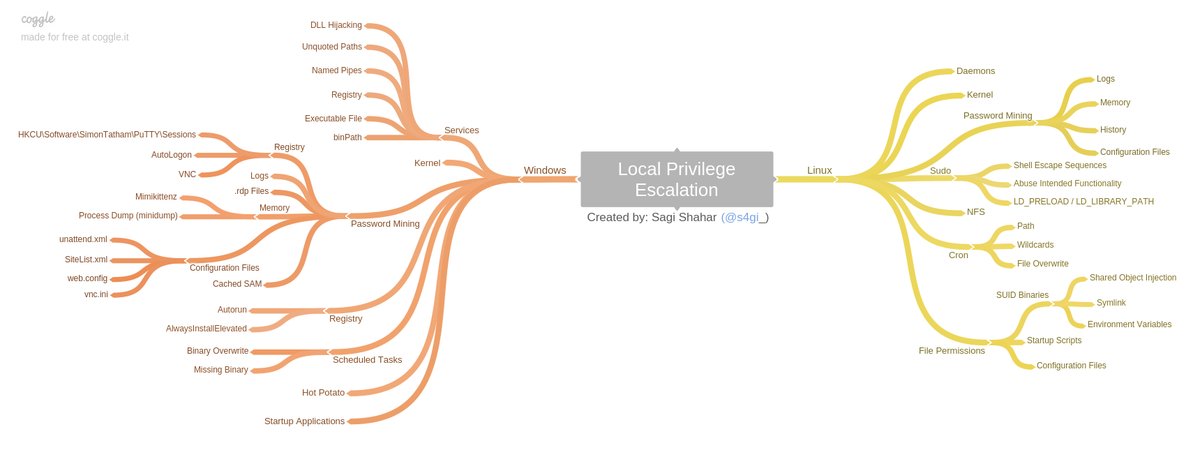
Enjoy ;)
Interesting projects
----
* [Windows / Linux Local Privilege Escalation Workshop](https://github.com/sagishahar/lpeworkshop)