https://github.com/CBLabresearch/PhantomExecution
Self Cleanup in post-ex job
https://github.com/CBLabresearch/PhantomExecution
Last synced: 4 months ago
JSON representation
Self Cleanup in post-ex job
- Host: GitHub
- URL: https://github.com/CBLabresearch/PhantomExecution
- Owner: CBLabresearch
- Created: 2024-09-09T05:42:10.000Z (over 1 year ago)
- Default Branch: main
- Last Pushed: 2024-09-10T10:43:22.000Z (over 1 year ago)
- Last Synced: 2024-09-10T12:03:07.739Z (over 1 year ago)
- Language: C++
- Size: 431 KB
- Stars: 5
- Watchers: 0
- Forks: 0
- Open Issues: 0
-
Metadata Files:
- Readme: README.md
Awesome Lists containing this project
- awesome-hacking-lists - CBLabresearch/PhantomExecution - Self Cleanup in post-ex job (C++)
README
# PhantomExecution

> Self Cleanup in post-ex job, suit for CobaltStrike
When the target of process injection is the current process, and when the post-ex job is executed and the thread exits, the memory will look like this
Then, perform 5 screenshots:
So, we use the RDI itself to clean up itself and the memory area which the post-ex job is executed.
This is also a general memory execution plugin
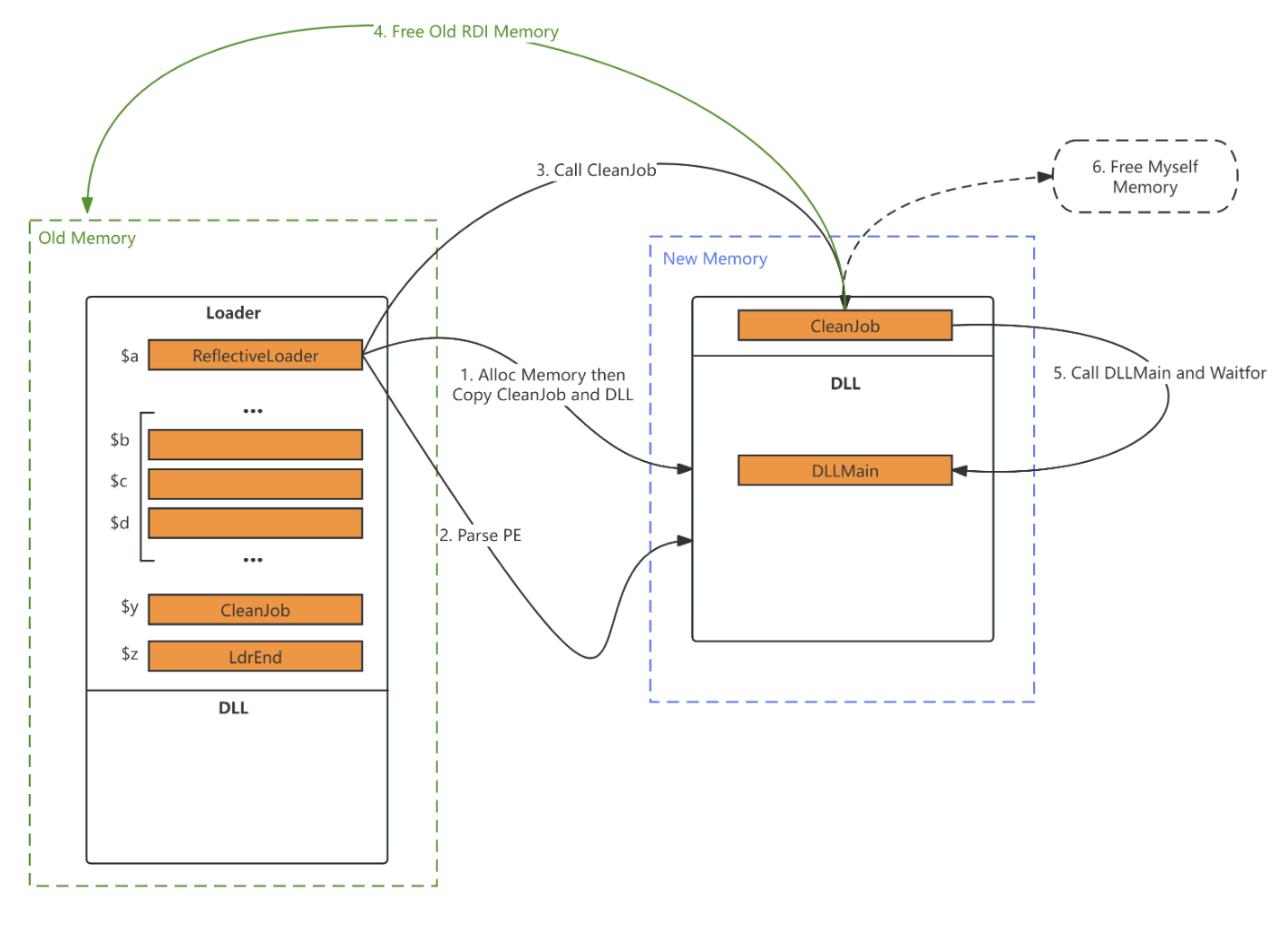
The code is not beautiful, and many IOCs are not evasioned. Please modify it according to OPSEC principles. This code only shows the self clean technology.
writeup: https://mp.weixin.qq.com/s/V4EdhGzyzxln0LzU99hqpA
conference: https://github.com/knownsec/KCon/blob/master/2024/%E9%AB%98%E7%BA%A7%E6%81%B6%E6%84%8F%E8%BD%AF%E4%BB%B6%E5%BC%80%E5%8F%91%E4%B9%8BRDI%E7%9A%84%E8%BF%9B%E5%8C%96.pdf