https://github.com/FULLSHADE/Auto-Elevate
Escalate from a low-integrity Administrator account to NT AUTHORITY\SYSTEM without an LPE exploit by combining a COM UAC bypass and Token Impersonation
https://github.com/FULLSHADE/Auto-Elevate
Last synced: 8 months ago
JSON representation
Escalate from a low-integrity Administrator account to NT AUTHORITY\SYSTEM without an LPE exploit by combining a COM UAC bypass and Token Impersonation
- Host: GitHub
- URL: https://github.com/FULLSHADE/Auto-Elevate
- Owner: FULLSHADE
- Created: 2021-12-16T01:15:47.000Z (about 4 years ago)
- Default Branch: main
- Last Pushed: 2021-12-19T22:06:18.000Z (about 4 years ago)
- Last Synced: 2024-11-13T01:52:01.514Z (over 1 year ago)
- Language: C++
- Homepage:
- Size: 59.6 KB
- Stars: 155
- Watchers: 2
- Forks: 65
- Open Issues: 1
-
Metadata Files:
- Readme: README.md
Awesome Lists containing this project
- awesome-hacking-lists - FULLSHADE/Auto-Elevate - Escalate from a low-integrity Administrator account to NT AUTHORITY\SYSTEM without an LPE exploit by combining a COM UAC bypass and Token Impersonation (C++)
README
# Auto-Elevate
This tool demonstrates the power of UAC bypasses and built-in features of Windows. This utility auto-locates `winlogon.exe`, steals and impersonates it's process TOKEN, and spawns a new SYSTEM-level process with the stolen token. Combined with UAC bypass method #41 (ICMLuaUtil UAC bypass) from hfiref0x's UACME utility, this utility can auto-elevate a low privileged Administrative account to NT AUTHORITY\SYSTEM.
----
The following image demonstrates using UACME combined with Auto-Elevate to go from a low-privileged Administrator account to NT AUTHORITY\SYSTEM on Windows 10 21H1.

The following image demonstrates escalation from a high-privileged Administrator account to SYSTEM without a UAC bypass
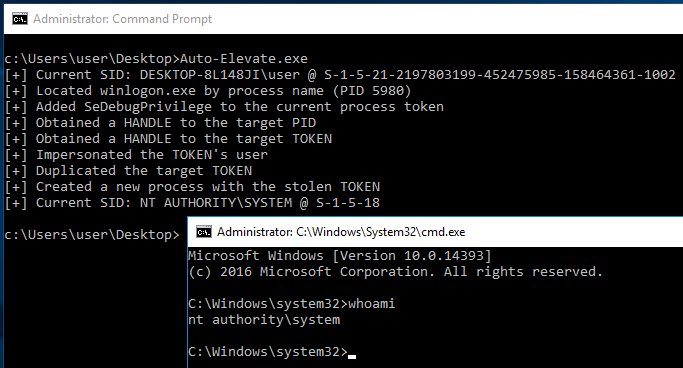
## Technical Explanation
The following steps are performed by Auto-Elevate to escalate from a low-privileged Administrator to SYSTEM:

### Auto-Elevate
1. The winlogon.exe process is located by enumerating the systems running processes with CreateToolhelp32Snapshot, Process32First, and Process32Next
2. SeDebugPrivilege is enabled for the current process via a call to AdjustTokenPrivileges, as it's required to open a HANDLE to winlogon.exe
3. A handle to the winlogon.exe process is opened by calling OpenProcess, for this call PROCESS\_ALL\_ACCESS is used (however, it's overkill)
4. A handle to winlogon's process token is retrieved by calling OpenProcessToken combined with the previously obtained process handle
5. The user (SYSTEM) of winlogon is impersonated by calling ImpersonateLoggedOnUser
6. The impersonated token handle is duplicated by calling DuplicateTokenEx with SecurityImpersonation, this creates a duplicated token we can use
7. Using the duplicated, and impersonated token a new CMD instance is spawned by calling CreateProcessWithTokenW
## To-Do
- [ ] Implement a standalone version of method 41 from UACME (or similar) to automate the process further
## MITRE ATT&CK Mapping
- Token Manipulation: [T1134](https://attack.mitre.org/techniques/T1134/)
- Access Token Manipulation: Token Impersonation/Theft: [T1134.001](https://attack.mitre.org/techniques/T1134/001/)
- Access Token Manipulation: Create Process with Token: [T1134.002](https://attack.mitre.org/techniques/T1134/002/)
- Access Token Manipulation: Make and Impersonate Token: [T1134.003](https://attack.mitre.org/techniques/T1134/003/)