https://github.com/Gilzy/403Bypasser
https://github.com/Gilzy/403Bypasser
Last synced: about 1 month ago
JSON representation
- Host: GitHub
- URL: https://github.com/Gilzy/403Bypasser
- Owner: Gilzy
- Created: 2021-05-21T13:56:31.000Z (about 4 years ago)
- Default Branch: main
- Last Pushed: 2022-09-27T10:23:30.000Z (over 2 years ago)
- Last Synced: 2024-11-18T16:57:31.499Z (7 months ago)
- Language: Python
- Size: 122 KB
- Stars: 54
- Watchers: 4
- Forks: 32
- Open Issues: 2
-
Metadata Files:
- Readme: README.md
Awesome Lists containing this project
- awesome-burp-extensions - 403Bypasser - A Burp Suite extension made to automate the process of bypassing 403 pages. (Web Application Firewall Evasion / SSRF)
README
## 403Bypasser
A Burp Suite extension made to automate the process of bypassing 403 pages. Heavily based on Orange Tsai's talk [Breaking Parser Logic: Take Your Path Normalization off and Pop 0days Out!
](https://www.youtube.com/watch?v=CIhHpkybYsY)
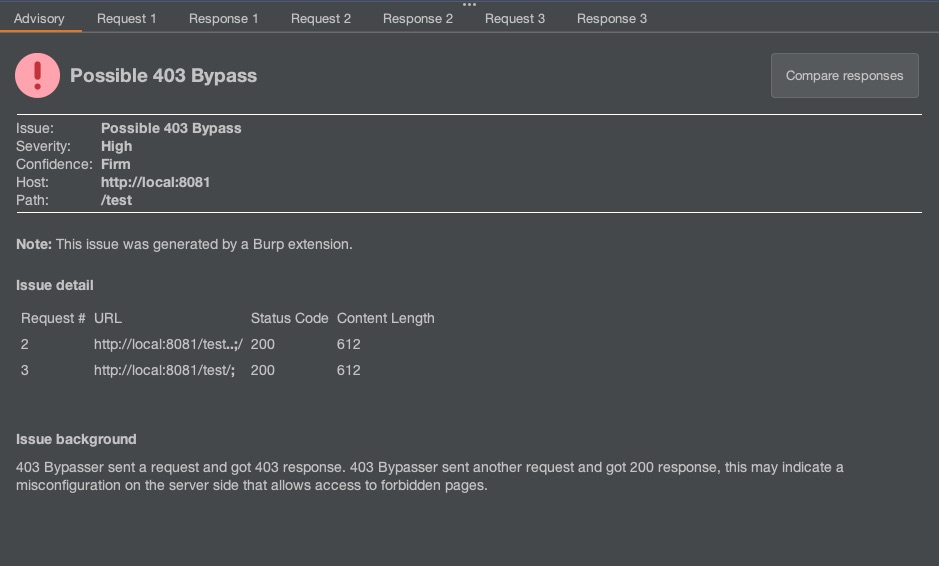
### Features
- Runs with every possible permutation for query-based payloads.
For instance `https://www.example.com/api/v1/users` with payload `..;` will result in testing the following:
```
https://www.example.com..;/api/v1/users
https://www.example.com/api..;/v1/users
https://www.example.com/api/v1..;/users
https://www.example.com/..;api/v1/users
https://www.example.com/api/..;v1/users
https://www.example.com/api/v1/..;users
https://www.example.com/api/v1/users/..;
https://www.example.com/api/v1/users/..;/
```
- Header payloads are added to the original request. In case the header already exists in the original request its value is replaced.
- For GET requests the extension will try to bypass Forbidden pages by changing the method to POST with an empty body.
- The extension will attempt to downgrade HTTP/1.1 to HTTP/1.0 and remove all headers as shown by [Abbas.heybati](https://infosecwriteups.com/403-bypass-lyncdiscover-microsoft-com-db2778458c33)
- Supports manual activation through context menu.
- Payloads are supplied by the user under dedicated tab, default values are stored in `query payloads.txt` and `header payloads.txt`.
- Issues are added under the Issue Activity tab.