https://github.com/HightechSec/scarce-apache2
A framework for bug hunting or pentesting targeting websites that have CVE-2021-41773 Vulnerability in public
https://github.com/HightechSec/scarce-apache2
bash-script bug-hunting cve-2021-41773 hacktoberfest pentesting
Last synced: 5 months ago
JSON representation
A framework for bug hunting or pentesting targeting websites that have CVE-2021-41773 Vulnerability in public
- Host: GitHub
- URL: https://github.com/HightechSec/scarce-apache2
- Owner: HightechSec
- License: mit
- Created: 2021-10-07T01:31:13.000Z (about 4 years ago)
- Default Branch: main
- Last Pushed: 2021-10-07T08:25:26.000Z (about 4 years ago)
- Last Synced: 2024-08-05T17:45:34.337Z (over 1 year ago)
- Topics: bash-script, bug-hunting, cve-2021-41773, hacktoberfest, pentesting
- Language: Shell
- Homepage:
- Size: 490 KB
- Stars: 62
- Watchers: 2
- Forks: 18
- Open Issues: 1
-
Metadata Files:
- Readme: README.MD
- License: LICENSE.md
Awesome Lists containing this project
- awesome-hacking-lists - HightechSec/scarce-apache2 - A framework for bug hunting or pentesting targeting websites that have CVE-2021-41773 Vulnerability in public (Shell)
README
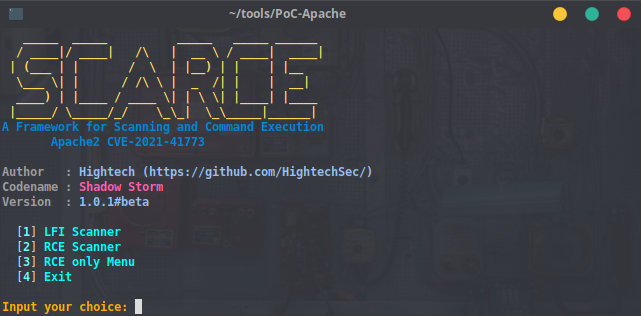
# ScaRCE Framework - CVE-2021-41773 Hunter
[](https://github.com/HightechSec/scarce-apache2/blob/master/LICENSE.md)










This tool can scan websites with CVE-2021-41773 Vulnerability that are affecting Apache2 Webserver, ScaRCE can run too for executing Remote Command Injections at the webservers that found from the scanning method (Only if the **MOD_CGI** is Enabled at the targeted webserver). This tool works with the provided Single target or Mass Target from a file list. Only use this tool for `Bug Hunting`/ `Pentesting Purposes`.
## Installation
```
- git clone https://github.com/HightechSec/scarce-apache2
- cd scarce-apache2
- bash scarce.sh
```
or you can install in your system like this
```
- git clone https://github.com/HightechSec/scarce-apache2
- cd scarce-apache2
- sudo cp scarce.sh /usr/bin/scarce && sudo chmod +x /usr/bin/scarce
- $ scarce
```
## Usage
- Menu's
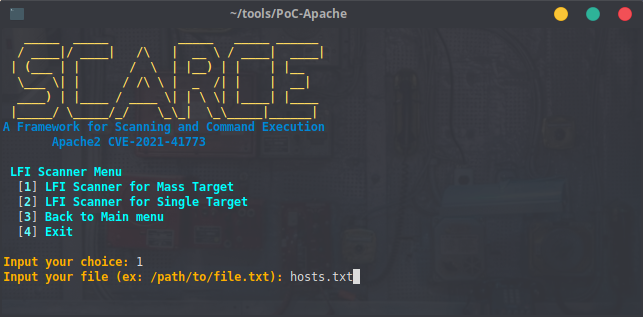
- Menu `1` is for scanning LFI Vulnerability from a provided file that contains the `list of the target url` or a provided `single target url`.
- Menu `2` is for scanning RCE Vulnerability from a provided file that contains the `list of the target url` or a provided `single target url`.
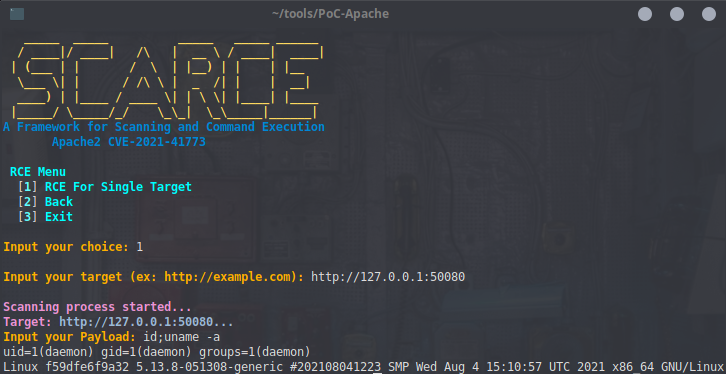
- Menu `3` is for Executing RCE from a provided `single target url`. This will work for the `Maybe Vuln` Results or sometimes with a `500 Error Response`.
- URL Format
- Use ```http://``` like ```http://example.com``` or ```https://``` like ```https://example.com``` for the url formatting at Single Target usages
- For Url or IP that has been provided from a ```List```, **Don't Use** the URL Formatting like eg:
- https://target.com
- http://hackerone.com
- https://bugcrowd.com
## Requirements
* curl
* bash
* git
# Credits
Thanks to:
- [CVE-2021-41773 Reproduced](https://twitter.com/ptswarm/status/1445376079548624899) by [@ptswarm](https://twitter.com/ptswarm)
- [Executing RCE in CVE-2021-41773](https://twitter.com/hackerfantastic/status/1445531829985968137) by [@hackerfantastic](https://twitter.com/hackerfantastic)
- [Removing 5xx Error when Running RCE](https://twitter.com/lukejahnke/status/1445560511270064138) by [@lukejahnke](https://twitter.com/lukejahnke)