https://github.com/In3tinct/See-SURF
Python tool to find potential Server Side Reqest Forgery (SSRF) vulnerability parameters.
https://github.com/In3tinct/See-SURF
Last synced: 5 months ago
JSON representation
Python tool to find potential Server Side Reqest Forgery (SSRF) vulnerability parameters.
- Host: GitHub
- URL: https://github.com/In3tinct/See-SURF
- Owner: In3tinct
- License: gpl-3.0
- Created: 2019-06-22T00:58:13.000Z (over 6 years ago)
- Default Branch: master
- Last Pushed: 2025-06-08T00:53:27.000Z (6 months ago)
- Last Synced: 2025-06-08T01:37:59.600Z (6 months ago)
- Language: Python
- Homepage:
- Size: 507 KB
- Stars: 320
- Watchers: 9
- Forks: 68
- Open Issues: 7
-
Metadata Files:
- Readme: README.md
- License: LICENSE
- Citation: CITATION.cff
Awesome Lists containing this project
- awesome-hacking-lists - In3tinct/See-SURF - Python tool to find potential SSRF parameters (Python)
README
# See-SURF
A Python based scanner to find potential SSRF parameters in a web application. See-SURF helps you detect potential SSRF parameters and validates the finding it by making a DNS/HTTP request back to your server. It can be added to your arsenal of recon while doing bug hunting/web security testing.
## Citation
Please cite, If you use this software in your Research papers, articles etc.
```
@software{Agrawal_See-SURF_Detect_SSRF_2019,
author = {Agrawal, Vaibhav},
month = jul,
title = {{See-SURF: Detect SSRF security vulnerability}},
url = {https://github.com/In3tinct/See-SURF},
version = {2.0.0},
year = {2019}
}
```
## Tech/framework used
Built with
- `Python3`
## Installation
`git clone https://github.com/In3tinct/See-SURF.git`
`cd See-SURF/`
`pip3 install BeautifulSoup4`
`pip3 install requests`
## How to use?
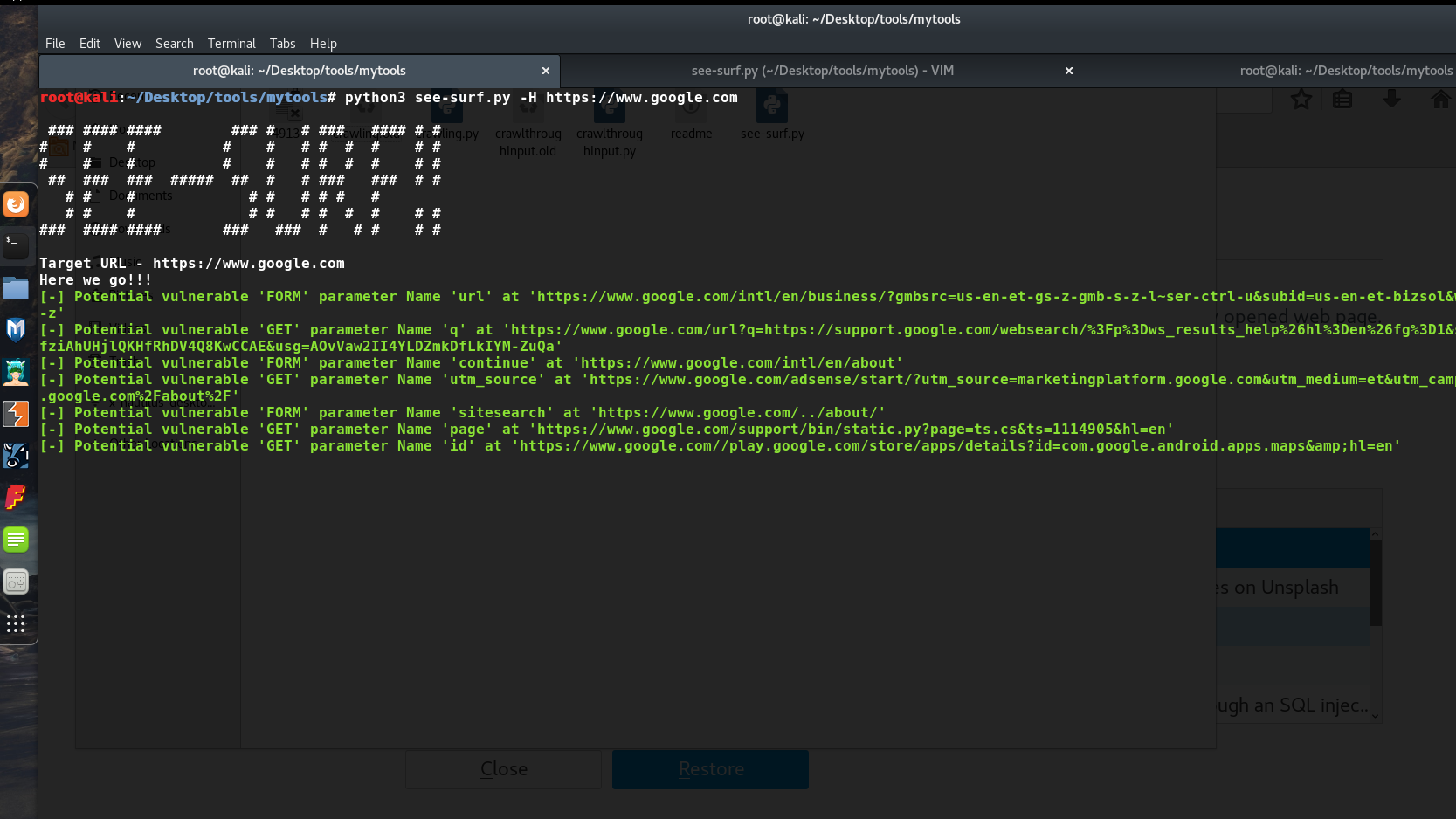
Complete Command would look like this
`python3 see-surf.py -H https://www.google.com -c cookie_name1=value1 cookie_name2=value2 -b burp_file.xml -p http://72.72.72.72:8000`
` -H - Host name/Ip address fo the target`
` -c - Cookies for authenticated scanning, seperated by space (Some websites use multiple cookies for session tracking`
` -b (Optional but recommended) - Spider the request using burp, export the site map file and give it to see-surf as input (check detailed features on how to do it)`
` -p (Optional but recommended) - Your own web server/burp collaborator, the script will try to connect back for validation of SSRF params`
## Features
1) Multi-threaded In-built crawler to run and gather as much data as possible to parse and identify potentially vulnerable SSRF parameters with a strong regex matches in GET/POST URL parameters containing, potentially vulnerable keywords like URL/website etc. Also, checks the parameter values for any URL or IP address passed.
For Example, Matches would look like -
For GET request - `google.com/url=https://yahoo.com`
`google.com/q=https://yahoo.com`
For POST/FORMS - ``
2) Takes burp's sitemap as input. Check detailed features for more details.
3) Supply cookies for an authenticated scanning.
`python3 see-surf.py -H https://www.google.com -c cookie_name1=value1 cookie_name2=value2`
4) By default, normal mode is On, with a verbose switch you would see the same vulnerable param in different endpoints. The same parameter may not be sanitized at all places. But verbose mode generates a lot of noise.
`python3 see-surf.py -H https://www.google.com -c cookie_name1=value1 cookie_name2=value2 -t 20 -v`
Example:
https://google.com/path/1/urlToConnect=https://yahoo.com
https://google.com/differentpath/urlToConnect=https://yahoo.com
5) Exploitation - Makes an external request to burp collaborator or any other http server with the vulnerable parameter to confirm the possibility of SSRF. (An external redirect vulnerability can potentially be vulnerable to SSRF)
### Detailed Features
[-] -b switch Burp's site map shows the information that Burp collects as you explore your target application like URLs collected etc. Provide burp sitemap files for a better discovery of potential SSRF parameters. The script would first parse the burp file and try to identify potential params and then run the built in crawler on it
Browser the target with your burpsuite running at the background, make some GET/POST requests, the more the better. Then go to target, right click-> "Save selected Items" and save it. Provide to the script as follows.
`python3 see-surf.py -H https://www.google.com -c cookie_name1=value1 cookie_name2=value2 -b burp_file.xml`
)
[-] -p switch Fire up burpsuite collaborator and pass the host with -p parameter Or start a simple python http server and wait for the
vulnerable param to execute your request. (Highly Recommended)
(This basically helps in exploiting GET requests, for POST you would need to try to exploit it manually)
Payload will get executed with the param at the end of the string so its easy to identify which one is vulnerable.
For example: http://72.72.72.72:8000/vulnerableparam
`python3 see-surf.py -H https://www.google.com -c cookie_name1=value1 cookie_name2=value2 -p http://72.72.72.72:8000`

## Citation
Please cite, If you use this software in your Research papers, articles etc.
```
@software{Agrawal_See-SURF_Detect_SSRF_2019,
author = {Agrawal, Vaibhav},
month = jul,
title = {{See-SURF: Detect SSRF security vulnerability}},
url = {https://github.com/In3tinct/See-SURF},
version = {2.0.0},
year = {2019}
}
```
## Contribute
- Report bugs.
- Suggestions for improvement.
- Suggestions for future extensions.
## Future Extensions
- Include more places to look for potential params like Javascript files.
- Exploitation, send internal/localhost URLs and check responses, instead of external server.
- Finding potential params during redirection.
- Hidden parameters.
## License
GNUV3 © [In3tinct]