https://github.com/Johnng007/Live-Forensicator
A suite of Tools to aid Incidence Response and Live Forensics for - Windows (Powershell) | Linux (Bash) | MacOS (Shell)
https://github.com/Johnng007/Live-Forensicator
bash eventlog-analysis eventlogs forensicator forensics forensics-investigations incident-response linux linux-shell live-forensic log4j macos powershell ransomeware
Last synced: 5 months ago
JSON representation
A suite of Tools to aid Incidence Response and Live Forensics for - Windows (Powershell) | Linux (Bash) | MacOS (Shell)
- Host: GitHub
- URL: https://github.com/Johnng007/Live-Forensicator
- Owner: Johnng007
- Created: 2022-02-07T20:23:14.000Z (almost 4 years ago)
- Default Branch: main
- Last Pushed: 2024-09-27T17:31:18.000Z (about 1 year ago)
- Last Synced: 2024-11-21T18:37:14.482Z (about 1 year ago)
- Topics: bash, eventlog-analysis, eventlogs, forensicator, forensics, forensics-investigations, incident-response, linux, linux-shell, live-forensic, log4j, macos, powershell, ransomeware
- Language: JavaScript
- Homepage:
- Size: 16.1 MB
- Stars: 542
- Watchers: 22
- Forks: 84
- Open Issues: 0
-
Metadata Files:
- Readme: README.md
Awesome Lists containing this project
- awesome-hacking-lists - Johnng007/Live-Forensicator - A suite of Tools to aid Incidence Response and Live Forensics for - Windows (Powershell) | Linux (Bash) | MacOS (Shell) (JavaScript)
README
📝 Forensicator 📝
WINDOWS(PowerShell) | LINUX(Bash) | MacOS(Bash)
SCRIPTS TO AID LIVE FORENSICS & INCIDENCE RESPONSE
```bash
___________ .__ __
\_ _____/__________ ____ ____ _____|__| ____ _____ _/ |_ ___________
| __)/ _ \_ __ \_/ __ \ / \ / ___/ |/ ___\\__ \\ __\/ _ \_ __ \
| \( <_> ) | \/\ ___/| | \\___ \| \ \___ / __ \| | ( <_> ) | \/
\___ / \____/|__| \___ >___| /____ >__|\___ >____ /__| \____/|__|
\/ \/ \/ \/ \/ \/
v4.0.1
```
# 🤔 ABOUT
Live Forensicator is part of the Black Widow Toolbox, it aims to assist Forensic Investigators and Incident responders in carrying out a quick live forensic investigation.
It achieves this by gathering different system information for further review for anomalous behavior or unexpected data entry, it also looks out for unusual files or activities and points it out to the investigator.
It is paramount to note that these scripts have no inbuilt intelligence it's left for the investigator to analyze the output and decide on a conclusion or conduct a deeper investigation.
# 🖳 Forensicator For WINDOWS
The windows version of Forensicator is written in Powershell.
Forensicator for Windows has added the ability to analyze Event Logs, it queries the event logs for certain log IDs that might point to unusual activity or compromise.
[Check out Forensicator for Windows](https://github.com/Johnng007/Live-Forensicator/tree/main/Windows)
# 👨💻 Forensicator For MacOS
The MacOS version is a shell script.
[Check out Forensicator for MacOS](https://github.com/Johnng007/Live-Forensicator/tree/main/MacOS/)
# 👩💻 Forensicator For LINUX
The Linux version is written in Bash.
[Check out Forensicator for Linux](https://github.com/Johnng007/Live-Forensicator/tree/main/Linux)
> #### NOTE:
> The Bash codes were written for cross-compatibility across Linux distros so therefore efforts were made to use OS native commands while avoiding secondary utilities like `net-tools`.
## ✍ General Notes
* Run the scripts as a privileged user to get value.
* Forensicator Activities may be flagged by IDS or IPS Solutions so take note.
* Forensicator results are output in nice-looking html files with an index file. You can find all extracted Artifacts in the script's working directory.
*
Forensicator Can Search through all the folders within a system looking for files with similar extensions as well-known Ransomware, Albeit this search can take a long time, but is helpful if the Alert you received is related to a Ransomware attack
*
Forensicator can capture network traffic, this is useful when your investigation has to do with assets communicating with known malicious IPs, this way you can parse the pcapng file to Wireshark and examine for C&C servers.
*
Sometimes it may be paramount to maintain the integrity of the Artifacts, where lawyers may argue that they might have been compromised on transit to your lab.
Forensicator can encrypt the Artifact with a unique randomly generated key using the AES algorithm, you can specify this by using the -ENCRYPTED parameter. You can decrypt it at will anywhere anytime even with another copy of Forensicator, just keep your key safe. This task is performed by the FileCryptography.psm1 file
> #### NOTE:
> This feature is only currently available in the Windows Module..
*
In the Windows module Forensictor looks out for suspicious activities within the Event Log, it has a long list of malicious executables, and PowerShell commands which it queries the event log against.
*
In the Windows module Forensictor Matches hashes of executables within the system to malicious hash databases for malware detection, Also browsing history URLs are matched against a list of latest URLs from IOCs for detection.
## Screenshot
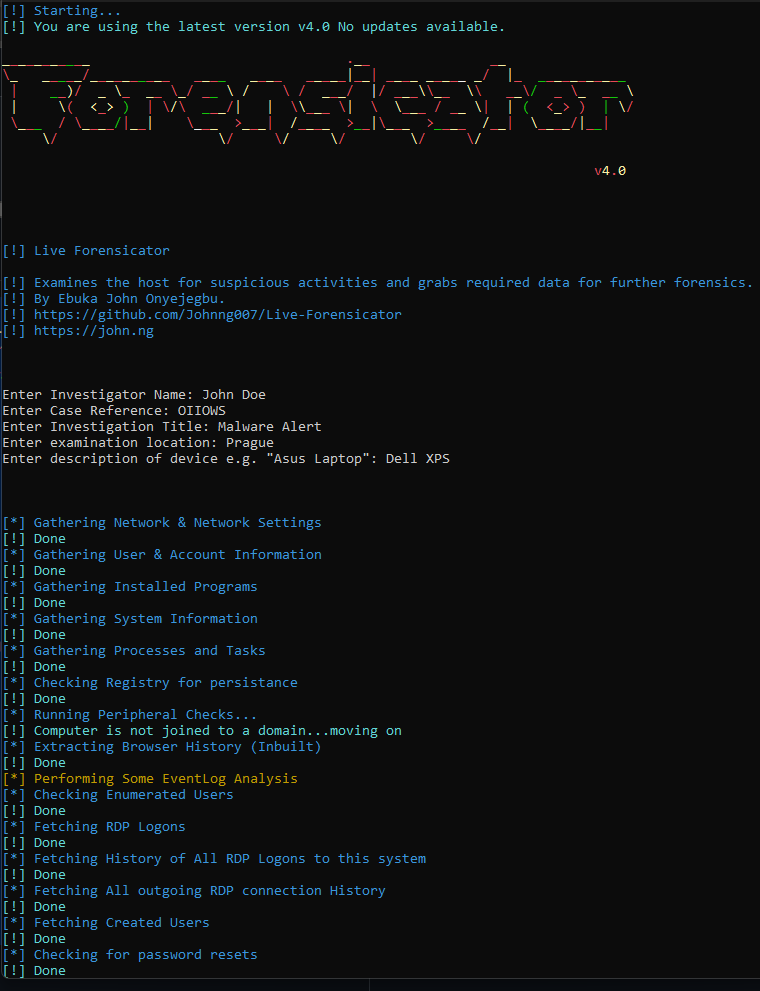
## HTML Output
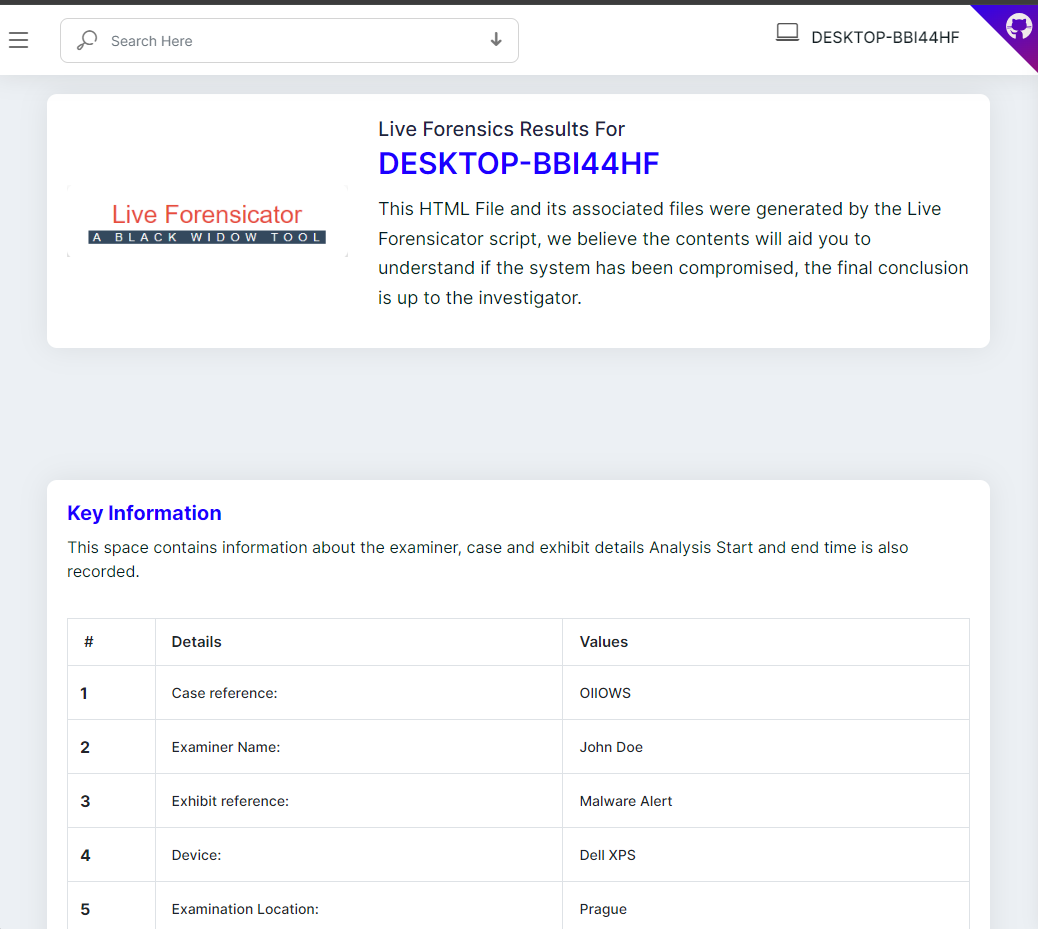
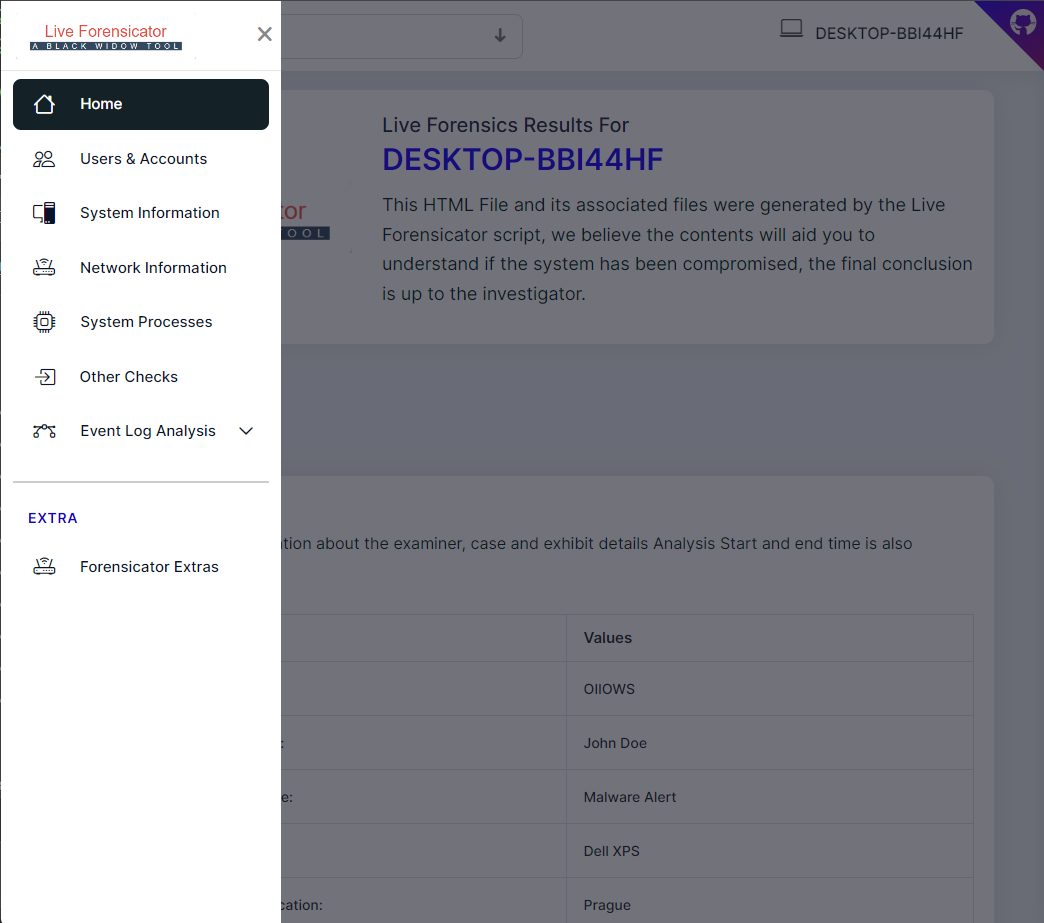
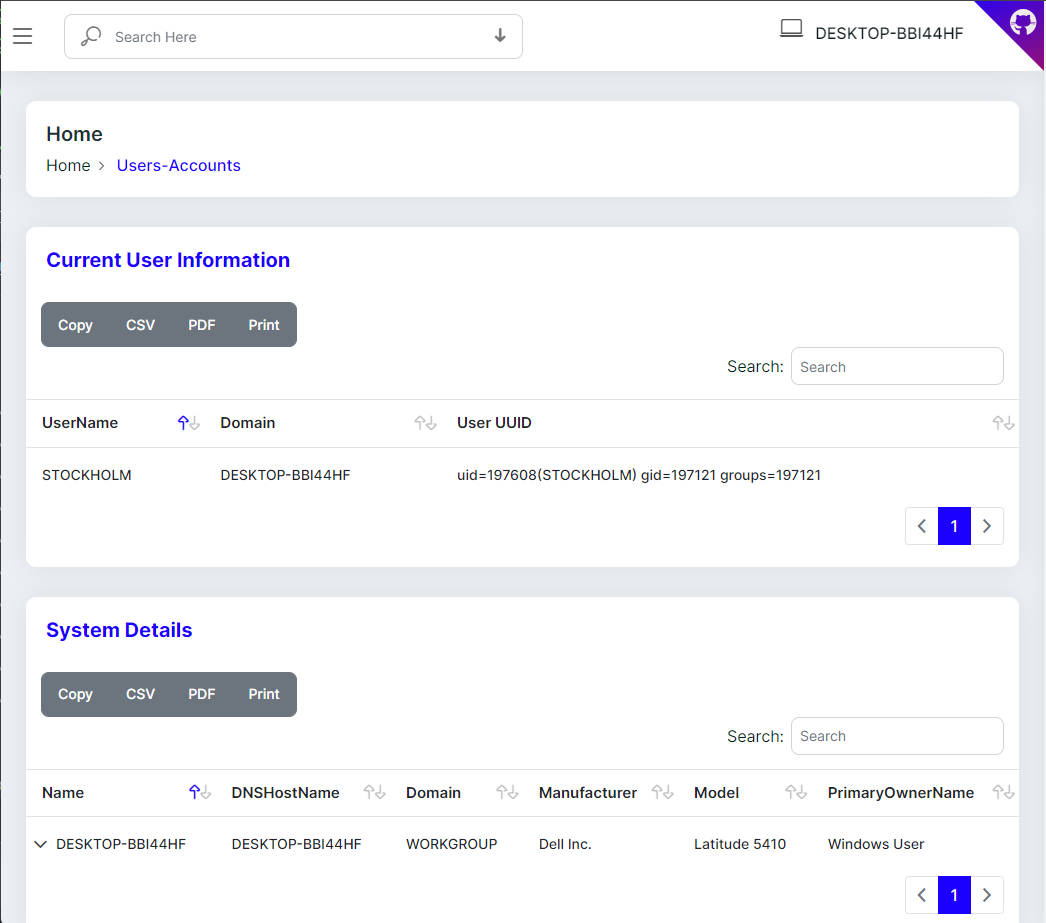
## ✨ ChangeLog
[See Wiki](https://github.com/Johnng007/Live-Forensicator/wiki/Changelog) For full Changelog.
```bash
Windows: v4.0.2 07/08/2024
1. Windows: Added hash check for malware detection.
2. Windows: Minor Bug Fixes.
3. Windows: Added a notification when Forensicator is not running as admin.
```
## 🤔 MORE TOOLS
Want to check out other Black Widow Tools?
1. [Anteater](https://github.com/Johnng007/Anteater) - A Python-based web reconnaissance tool.
2. [Nessus Pro API](https://github.com/Johnng007/PowershellNessus) - A PowerShell Script to Export and Download Nessus Scan Results via Nessus API.
## Contributing
Pull requests are welcome. For major changes, please open an issue first to discuss what you would like to change or add.
## License
[MIT](https://mit.com/licenses/mit/)
Support:
Connect with me:
