https://github.com/KTZgraph/sarenka
OSINT tool - gets data from services like shodan, censys etc. in one app
https://github.com/KTZgraph/sarenka
censys-api cve cve-databases cve-search cwe cwe-search django django-rest-framework docker osint osint-python python3 react react-persist react-redux react-thunk reactjs reconnaissance scraping-websites shodan-api
Last synced: 10 months ago
JSON representation
OSINT tool - gets data from services like shodan, censys etc. in one app
- Host: GitHub
- URL: https://github.com/KTZgraph/sarenka
- Owner: KTZgraph
- License: mit
- Created: 2020-01-21T17:14:26.000Z (about 6 years ago)
- Default Branch: master
- Last Pushed: 2023-05-04T15:42:26.000Z (almost 3 years ago)
- Last Synced: 2024-05-22T06:17:08.140Z (over 1 year ago)
- Topics: censys-api, cve, cve-databases, cve-search, cwe, cwe-search, django, django-rest-framework, docker, osint, osint-python, python3, react, react-persist, react-redux, react-thunk, reactjs, reconnaissance, scraping-websites, shodan-api
- Language: Python
- Homepage: https://pawlaczyk.github.io/sarenka/
- Size: 136 MB
- Stars: 618
- Watchers: 24
- Forks: 88
- Open Issues: 52
-
Metadata Files:
- Readme: README.md
- License: LICENSE
Awesome Lists containing this project
- awesome-ip-search-engines - Sarenka (universal)
- awesome-hacking-lists - KTZgraph/sarenka - OSINT tool - gets data from services like shodan, censys etc. in one app (Python)
- awesome-security-vul-llm - KTZgraph/sarenka - square) - Sarenka 是一个开源情报工具,用于收集和理解攻击表面。它可以从搜索引擎获取互联网连接设备的信息,并提供 Common Vulnerabilities and Exposures (CVE),Common Weakness Enumeration (CWE) 数据库,以及将 CVE 映射到 CWE 的数据库。此外,它还提供了简单的工具如哈希计算器,香农熵计算器和基本端扫描器。 (LLM分析过程)
- awesome-rainmana - KTZgraph/sarenka - OSINT tool - gets data from services like shodan, censys etc. in one app (Python)
README

[](https://github.com/pawlaczyk/sarenka/releases/latest)
[](https://github.com/pawlaczyk/sarenka/releases/latest)
[](https://github.com/pawlaczyk/sarenka/releases/latest)

[](https://github.com/pawlaczyk/sarenka/releases/latest)
[](https://github.com/pawlaczyk/sarenka/releases/latest)


[](https://github.com/pawlaczyk/sarenka/blob/master/LICENSE)
**♥ Free Software, requires only free accounts to third part services ♥**
> Lack of knowledge ... that is the problem.
>
>
>[William Edwards Deming]
**SARENKA** is an Open Source Intelligence (**OSINT**) tool that helps you in obtaining and understanding **Attack Surface**.
The main goal is gathering information from search engines for Internet-connected devices (**https://censys.io/**, **https://www.shodan.io/**, **https://www.criminalip.io/ko**).
It scrapes data about Common Vulnerabilities and Exposures (**CVE**), Common Weakness Enumeration (**CWE**) and also has a database where CVEs are mapped to CWE.
It returns data about the local machine - local installed software (from Windows Registry), local network information (python libraries, popular cmd commads).
For now, the application also has simple tools like a hash calculator, shannon entropy calculator and very simple port scanner.
More cryptography-math tools and reconnaissance scripts are planned.
The app is alive and has been rewritten from scratch on branch [develop](https://github.com/pawlaczyk/sarenka/tree/new_master).
# Contributors
[](https://github.com/parkjunmin/)
[](https://github.com/rpedrica/)
[](https://github.com/rafalwojaczek/)
# SARENKA was mentioned here:
* [ncybersec](https://www.facebook.com/ncybersec/posts/1671427243027993)
* [llllap3xllll](https://www.instagram.com/p/CI8tXMNg3yI/)
* [securityonline.info](https://securityonline.info/sarenka-obtaining-and-understanding-attack-surface//)
* [haxf4rall.com](https://haxf4rall.com/2020/12/30/sarenka-obtaining-and-understanding-attack-surface/)
* [hackdig.com](http://hackdig.com/12/hack-245463.htm)
* [findglocal.com](http://www.findglocal.com/BR/Ananindeua/1436460569931544/Computer-Network-%26-Technology)
* [台灣數位國土安全部 - DDHS](https://www.facebook.com/DDHS.TW/)
* [laptrinhx.com](https://laptrinhx.com/sarenka-osint-tool-data-from-services-like-shodan-censys-etc-in-one-place-3347349303/)
* [kitploit.com](https://www.kitploit.com/2021/01/sarenka-osint-tool-data-from-services.html)
* [attackware.com](https://attackware.com/index.php/2021/01/07/sarenka-osint-tool-data-from-services-like-shodan-censys-etc-in-one-place/security-world-news/admin/)
* [hacking.land](https://www.hacking.land/2021/01/sarenka-osint-tool-data-from-services.html)
* [cyberfishnews.com](https://cyberfishnews.com/sarenka-osint-tool-data-from-services-like-shodan-censys-etc-in-one-place-19097.html)
* [modernnetsec.io](https://modernnetsec.io/sarenka-osint-tool-data-from-services-like-shodan-censys-etc-in-one-place/)
* [spywarenews.com](https://spywarenews.com/index.php/2021/01/07/sarenka-osint-tool-data-from-services-like-shodan-censys-etc-in-one-place/security-world-news/admin/)
* [cert.europa.eu](https://cert.europa.eu/cert/alertedition/en/VulnerabilitiesDBMS.html)
* [dfir.pro](http://dfir.pro/index.php?link_id=109300&utm_source=feedburner&utm_medium=feed&utm_campaign=Feed%3A+dfirpro+%28IT+%26+Security+NewsFeed+%29)
* [iransec.net](https://iransec.net/forums/topic/550-sarenka/?tab=comments#comment-605)
* [hacker-gadgets.com](https://hacker-gadgets.com/blog/2021/01/07/sarenka-osint-tool-data-from-services-like-shodan-censys-etc-in-one-place/)
* [vulners.com](https://vulners.com/kitploit/KITPLOIT:491559930238488010)
* [redpacketsecurity.com](https://www.redpacketsecurity.com/sarenka-osint-tool-data-from-services-like-shodan-censys-etc-in-one-place/)
* [kali-linuxtr.net](https://kali-linuxtr.net/sarenka-open-source-intelligence-osint-tool)
* [anonymousmedia.org](https://anonymousmedia.org/2021/01/07/sarenka-osint-tool-data-from-services-like-shodan-censys-etc-in-one-place/)
* [pentesttools.net](https://pentesttools.net/sarenka-osint-tool-data-from-services-like-shodan-censys-etc/)
* [wangshit.xyz](https://wangshit.xyz/sarenka-osint-tool-data-from-services-like-shodan-censys-etc-in-one-place/)
* [geekychild.com](https://geekychild.com/hack-penetration-tool/sarenka-osint-tool-data-from-services-like-shodan-censys-etc-in-one-place/)
* [hacker.observer](https://hacker.observer/sarenka-osint-tool-data-from-services-like-shodan-censys-etc-in-one-place/)
* [nuomiphp.com](https://www.nuomiphp.com/github/zh/5ff88c65e4570e7ee973117d.html)
* [danielonsecurity.com](https://danielonsecurity.com/links/)
* [haktechs](https://www.haktechs.com/hacking-pentesting-tools/sarenka-osint-tool-data-from-services-like-shodan-censys-etc-in-one-place/)
* [cybeseclabs.com](https://www.cybeseclabs.com/2021/01/07/sarenka-osint-tool-data-from-services-like-shodan-censys-etc-in-one-place/?fbclid=IwAR0HsqzT9UK-lReusUu0xEz2REN9uFZxXyOdr3dRrZ4uI8C0oseA8mZJSak)
* [vk.com](https://vk.com/wall-105076815_33626)
* [hacking.reviews](https://www.hacking.reviews/2021/01/sarenka-osint-tool-data-from-services.html)
* [thehacker.co](https://thehacker.co/pentest/information-gathering-pentest/sarenka-osint-tool-data-from-services-like-shodan-censys-etc)
* [iguru.gr](https://iguru.gr/2021/01/11/sarenka-ergaleio-osint-dedomena-apo-ypiresies-opos-shodan-kai-censys/)
* [en.iguru.gr](https://en.iguru.gr/2021/01/11/sarenka-ergaleio-osint-dedomena-apo-ypiresies-opos-shodan-kai-censys/)
* [rucore.net](https://rucore.net/p/archives/9740)
* [hackerzzz.com](https://hackerzzz.com/2021/01/11/sarenka-osint-tool-data-from-services-like-shodan-censys/)
* [my.oschina.net](https://my.oschina.net/u/4579293/blog/4885529)
* [kalilinuxtutorials.com](https://kalilinuxtutorials.com/sarenka/)
* [pintait.com](https://www.pintait.com/sarenka/)
* [osintbrasil.blogspot.com](https://osintbrasil.blogspot.com/2021/01/sarenka-e-uma-ferramenta-de.html)
* [wenyanet.com](https://www.wenyanet.com/opensource/ko/60407b4e1e5ba078c87a6d81.html)
* [federatica.space](https://federatica.space/p/211996)
* [giters.com](https://giters.com/pawlaczyk/sarenka?amp=1)
* [redhotcyber.com](https://www.redhotcyber.com/post/sarenka-uno-strumento-osint-connesso-a-shodan-censys-cve-dns-whois)
* [haktechs.com](https://www.haktechs.com/hacking-pentesting-tools/sarenka-an-osint-tool-that-gets-data-from-services-like-shodan-censys-etc-in-one-app/)
* [hakin9.org](https://hakin9.org/sarenka-an-osint-tool-that-gets-data-from-services-like-shodan-censys-etc-in-one-app/)
* [www.libhunt.com](https://www.libhunt.com/l/python/topic/reconnaissance)
* [cybersec365.org](https://cybersec365.org/pentesting-tools/sarenka-osint-shodan-censys/)
* [reddit.com user mikeis075](https://web.archive.org/web/20220524074859/https://www.reddit.com/r/hacking/comments/upx3hl/sarenka_an_osint_tool_that_gets_data_from/)
* [blackhatethicalhacking.com](https://www.blackhatethicalhacking.com/tools/sarenka/)
# Features
- get data from **https://censys.io/** by ip
- get data from **https://www.shodan.io/** by ip
- get data from **https://www.criminalip.io/** by ip
- get **DNS** data
- get **WHOIS** data
- **banner** grabbing
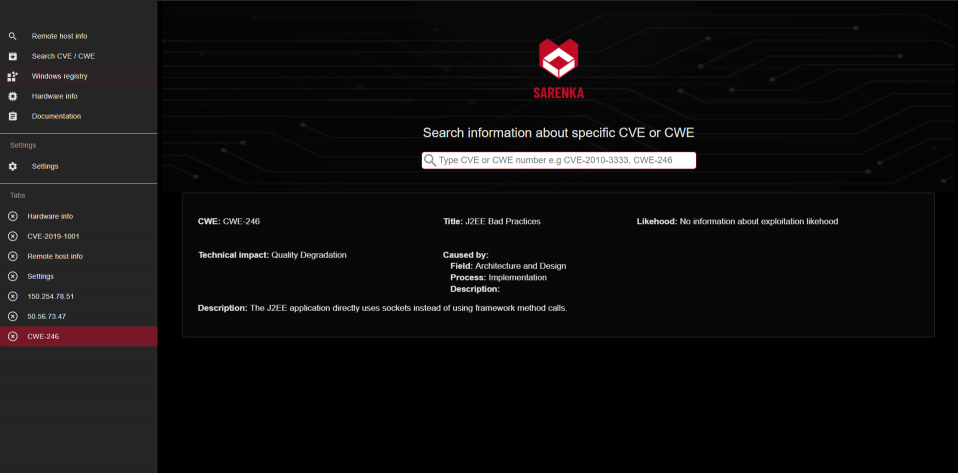
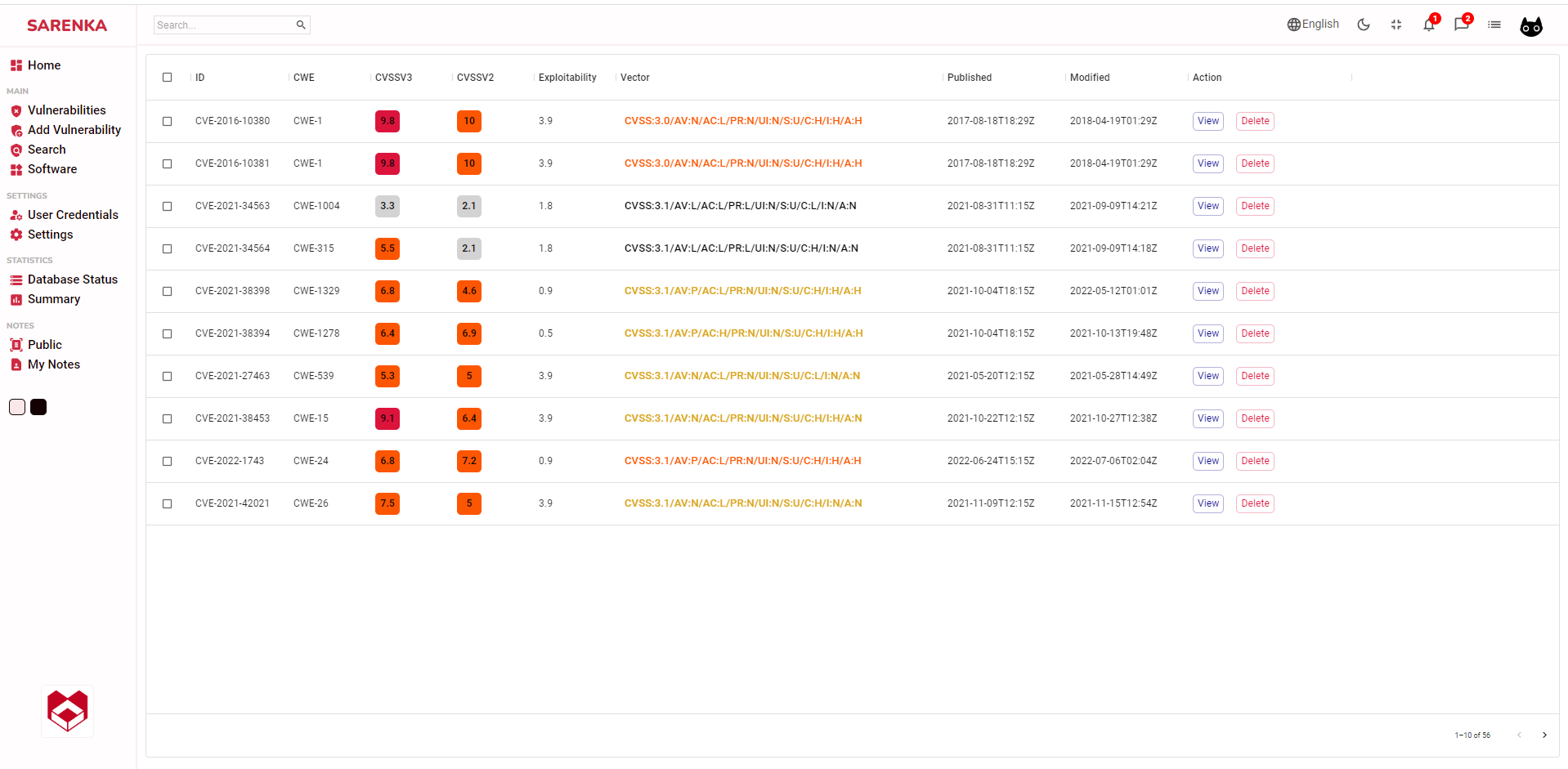
- find **CVEs** by **CWE**
- generate pdf report
You can also:
- calculate **hashes** based on user string
- calculate **shannon entropy** based on user string
- check is **port** open|closed (instead always use nmap if you can - it is slow)
# Installation
Our team tests the application on Windows 10 and Kali Linux with Python 3.8.
SARENKA requires:
* [Python](https://www.python.org/downloads/)
##### Clone repository
```
$ git clone https://github.com/pawlaczyk/sarenka.git
```
##### Go to application directory
```
$ cd ./sarenka
```
##### Create venv
```
$ python3 -m venv env
```
##### Activate venv
Powershell
```
$ ./env/Scripts/Activate.ps1
```
cmd
```
$ ./env/Scripts/activate.bat
```
##### Install requirements
```
$ pip3 install -r ./requirements.txt
```
##### Build application with sarenka.py script
```
$ python ./sarenka/sarenka.py
```
# Getting started
####Please create accounts on services:
- https://account.shodan.io/register
- https://censys.io/register
##### Application - default http://localhost:8000/
```
# go to sarenka/sarenka
$ python backend/manage.py runserver
```
#####Add user credentials at "Settings"
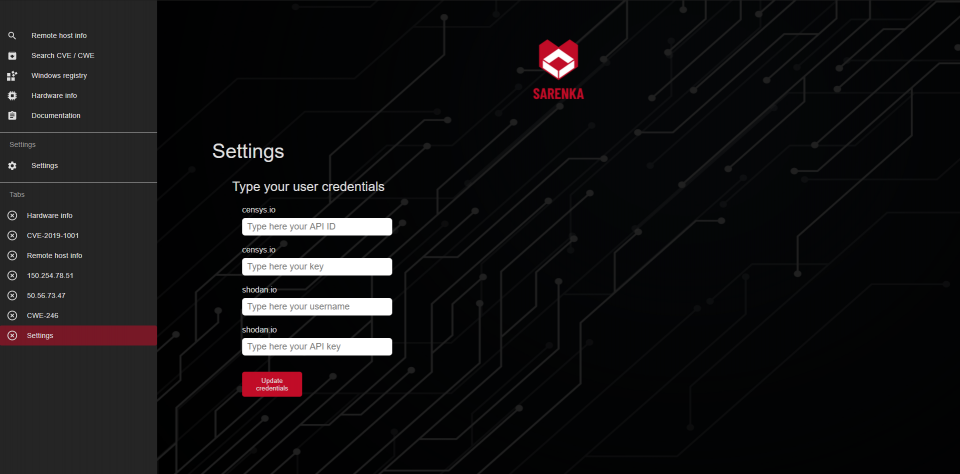
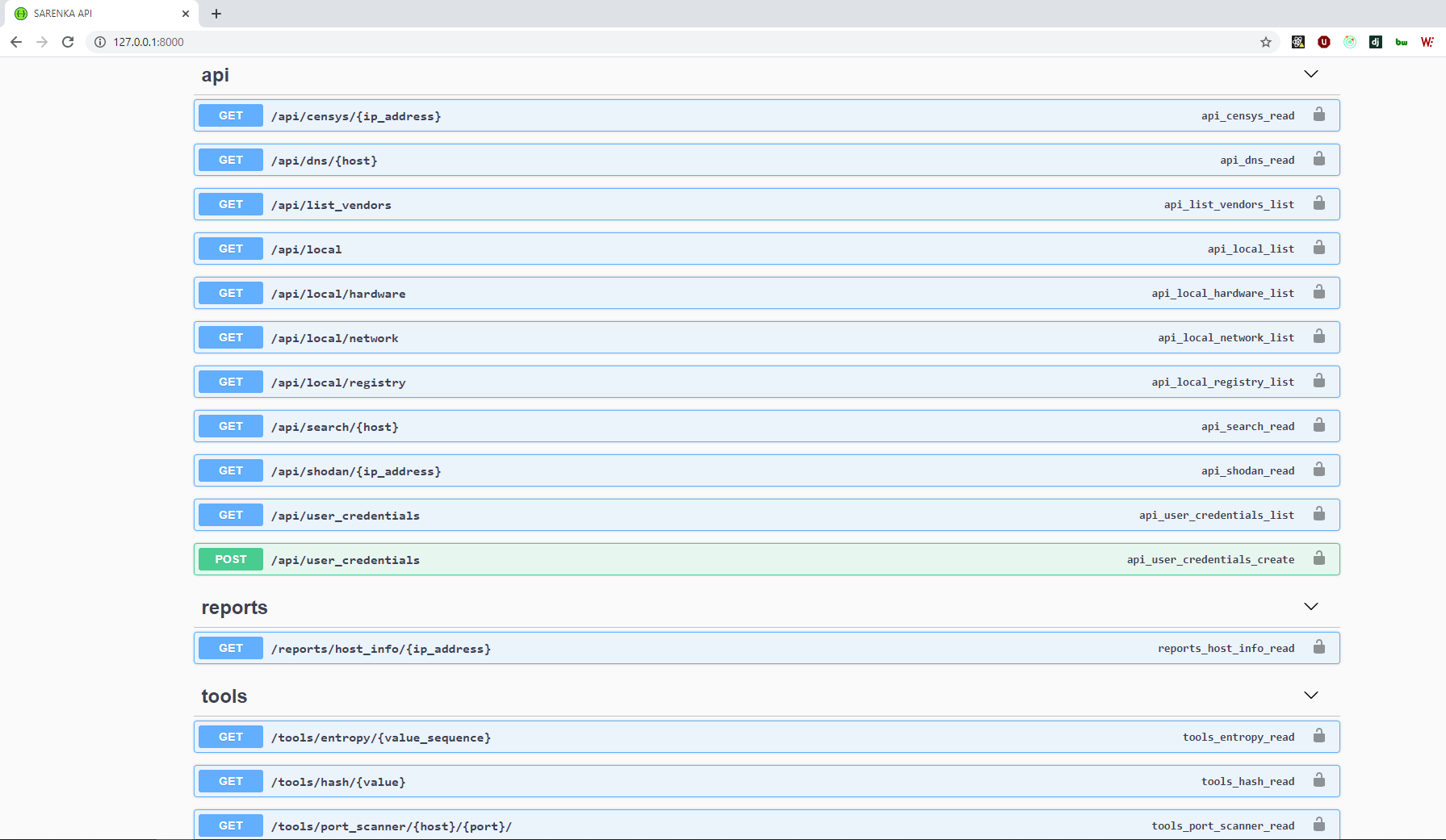
# Screenshots

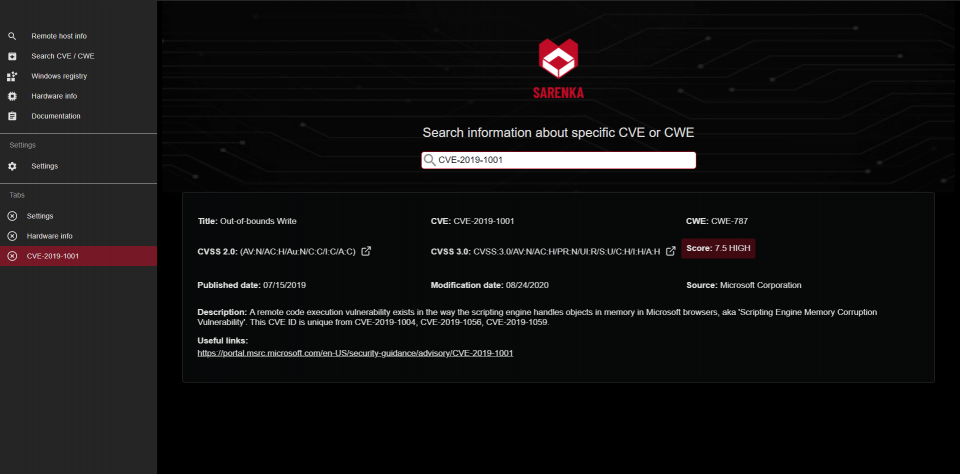
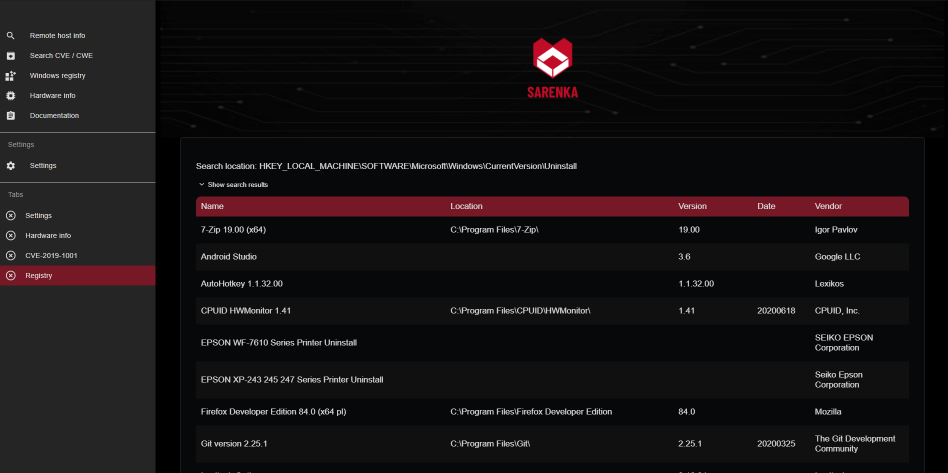
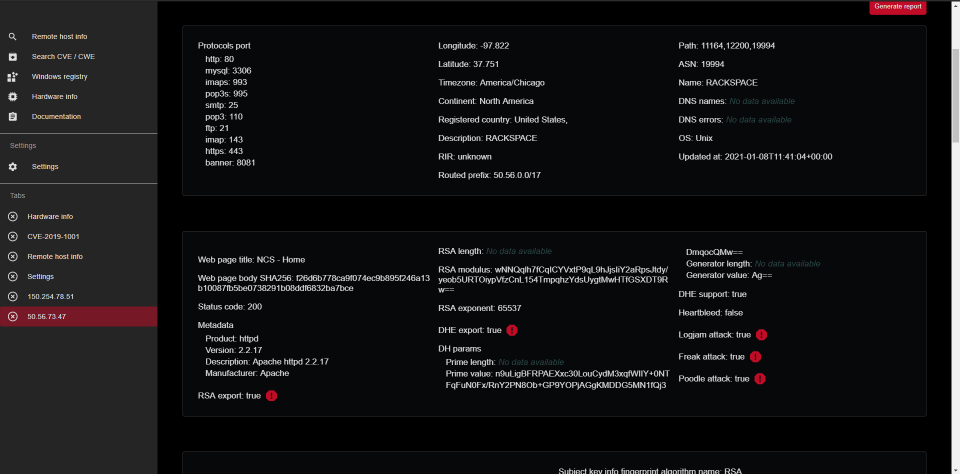
#### Suggestions are welcome
[1.1]: http://i.imgur.com/tXSoThF.png (twitter icon with padding)
[2.1]: http://i.imgur.com/P3YfQoD.png (facebook icon with padding)
[1]: https://twitter.com/OsintSarenka
[2]: https://www.facebook.com/sarenka.osint.5
- Want some feature, other tool, library functionality?
- Have any idea or question? [![alt text][1.1]][1]
- Don't hesitate to contact [](https://github.com/pawlaczyk/) .
#### Databases
Details in documentation.
## Tech
* [Renderforest](https://www.renderforest.com/)
* [gawk](http://gnuwin32.sourceforge.net/packages/gawk.htm)
* [chocolatey](https://chocolatey.org/)
* [PyCharm](https://www.jetbrains.com/pycharm/)
And of course SARENKA itself is open source with a [public repository][sarenka]
on GitHub.
#### Planned features
- Rewrite documentation in English (end of 2021)
- trello/ github instead of Jira
- Cover 100% code by tests
- typing backend
- document all functions and class
- Docker
- online demo
- Jenkins
- GraphQL
- Selenium Scrapers
- More pentesting tools
- Google Dorks
- Abstract Algebra calculator
- Number Theory calculator
- Server certificate validator
- tests on Linux
- NLP
- d3js visualizations
- alternative pure version for command line
##### CI/CD Tools
- https://circleci.com/
- https://github.com/snyk-bot
#### Tested manually
- Kali Linux kali-rolling 2020.2; Python 3.8.2
- Windows 10; Python 3.8.5
### Documentation
Till end of March, 2021 documentation will be available only in Polish!
The documentation is availabe [here](https://pawlaczyk.github.io/sarenka/).
# Authors
[](https://github.com/pawlaczyk/) [](https://github.com/michalpawlaczyk) [](https://github.com/k-slonka)
##### Contact
[](https://github.com/pawlaczyk/)
# License
SARENKA is **licensed** under the **[MIT License]**.
# Develop branch
[MIT License]: https://github.com/pawlaczyk/sarenka/blob/master/LICENSE
[GitHub]: https://github.com/pawlaczyk/sarenka
[documentation]: https://pawlaczyk.github.io/sarenka/
[public repository]: https://github.com/pawlaczyk/sarenka
[//]: # (These are reference links used in the body of this note and get stripped out when the markdown processor does its job. There is no need to format nicely because it shouldn't be seen. Thanks SO - http://stackoverflow.com/questions/4823468/store-comments-in-markdown-syntax)
[sarenka]:
[git-repo-url]:
[William Edwards Deming]: