https://github.com/NeoTheCapt/PowerScanner
面向HW的红队半自动扫描器
https://github.com/NeoTheCapt/PowerScanner
Last synced: 5 months ago
JSON representation
面向HW的红队半自动扫描器
- Host: GitHub
- URL: https://github.com/NeoTheCapt/PowerScanner
- Owner: NeoTheCapt
- License: gpl-2.0
- Created: 2021-01-23T19:00:16.000Z (almost 5 years ago)
- Default Branch: master
- Last Pushed: 2021-12-16T07:55:41.000Z (almost 4 years ago)
- Last Synced: 2024-11-21T14:38:45.641Z (about 1 year ago)
- Language: Java
- Size: 1.23 MB
- Stars: 220
- Watchers: 6
- Forks: 48
- Open Issues: 0
-
Metadata Files:
- Readme: README.md
- License: LICENSE
Awesome Lists containing this project
- awesome-hacking-lists - NeoTheCapt/PowerScanner - 面向HW的红队半自动扫描器 (Java)
README
# PowerScanner
* 面向HW的红队半自动扫描器(Burp插件)
* 适合有经验的渗透测试人员。
* 注:误报率高!!!所有报告结果需经手动手动确认。
* By Brian.W AKA BigCHAN
## Features
* 通过缩短payload长度、降低发包数量提高对WAF的隐蔽性,同时提高误报率。
* 所有测试项不依赖回显,发现隐蔽漏洞
* BypassWAF:各种Headers随机化(IP随机化、Cookie清空、User-agent随机化、HOST随机化)
* BypassWAF:锚点随机化,随机锚点{{|RANDOMSTR|}},{{|RANDOMINT|}}
* BypassWAF:json unicode编码
## Check list
注意:所有检测项只包含无害化PoC,不包含利用程序
* 扫描Sql注入
* 扫描命令注入
* 扫描敏感文件
* 扫描路径穿越
* 报告敏感参数(参数明看起来可能是漏洞点)
* fastjson检测
* log4j检测
* 路由请求到第三方工具,比如xray、zaproxy
## TODO
* 不增加发报量的前提下,修改对照逻辑,降低误报率
* 敏感文件扫描按照目录扫描(最高遍历一级目录)
* BypassWAF:膨胀Post body
* BypassWAF:膨胀Get URL
* CMS识别
# How To Use
加载插件,设置主动在线扫描,打开浏览器,设置代理到burp,剩下的就是点点点就行了。
## 主动扫描
* (optional) 为了控制发包数目,防止被WAF封,取消勾选其他所有主动扫描插件
* 加载插件
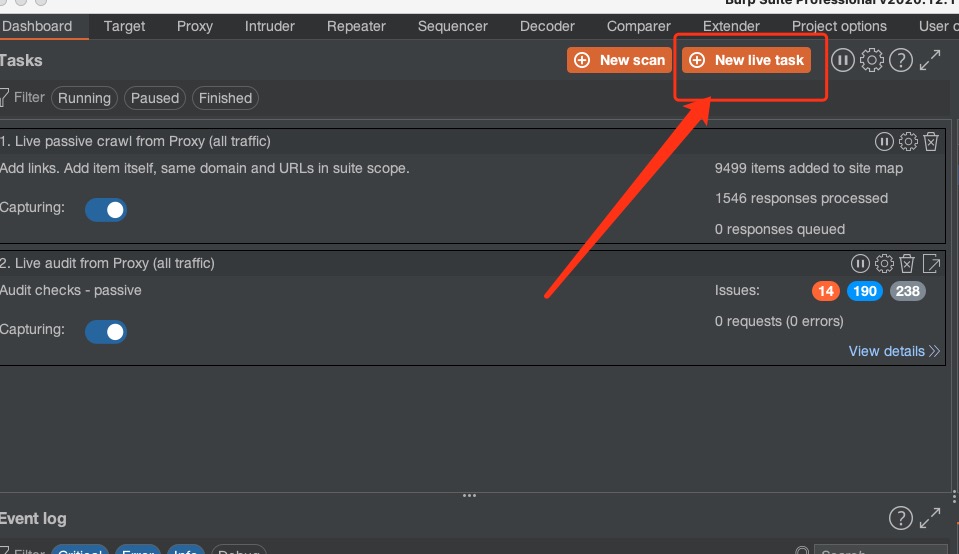
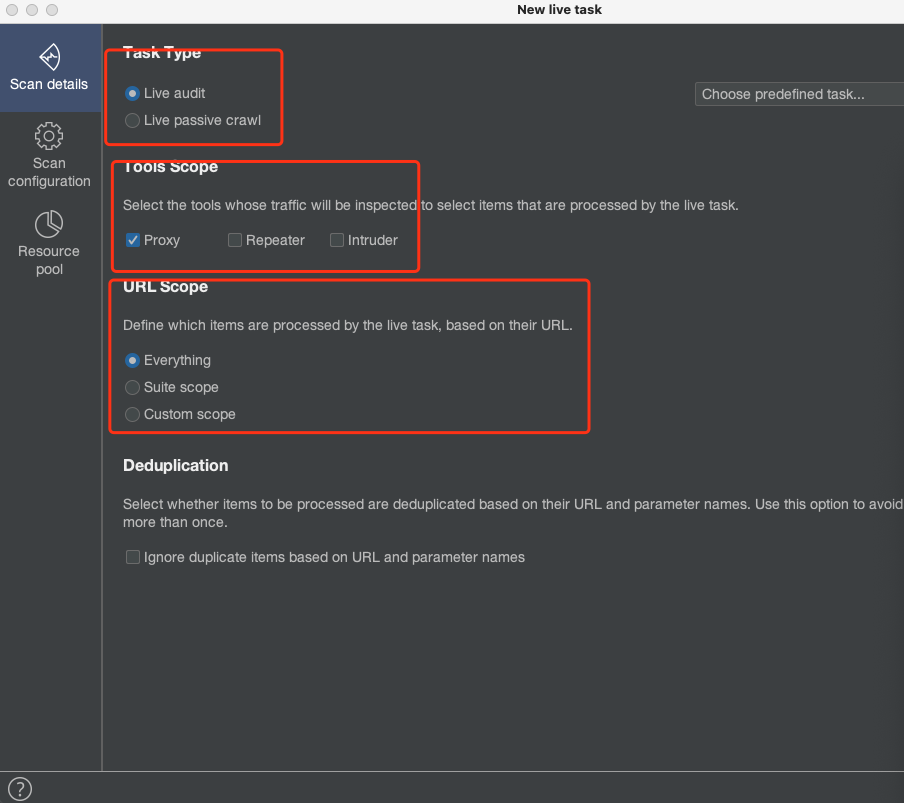
* 新建在线主动扫描
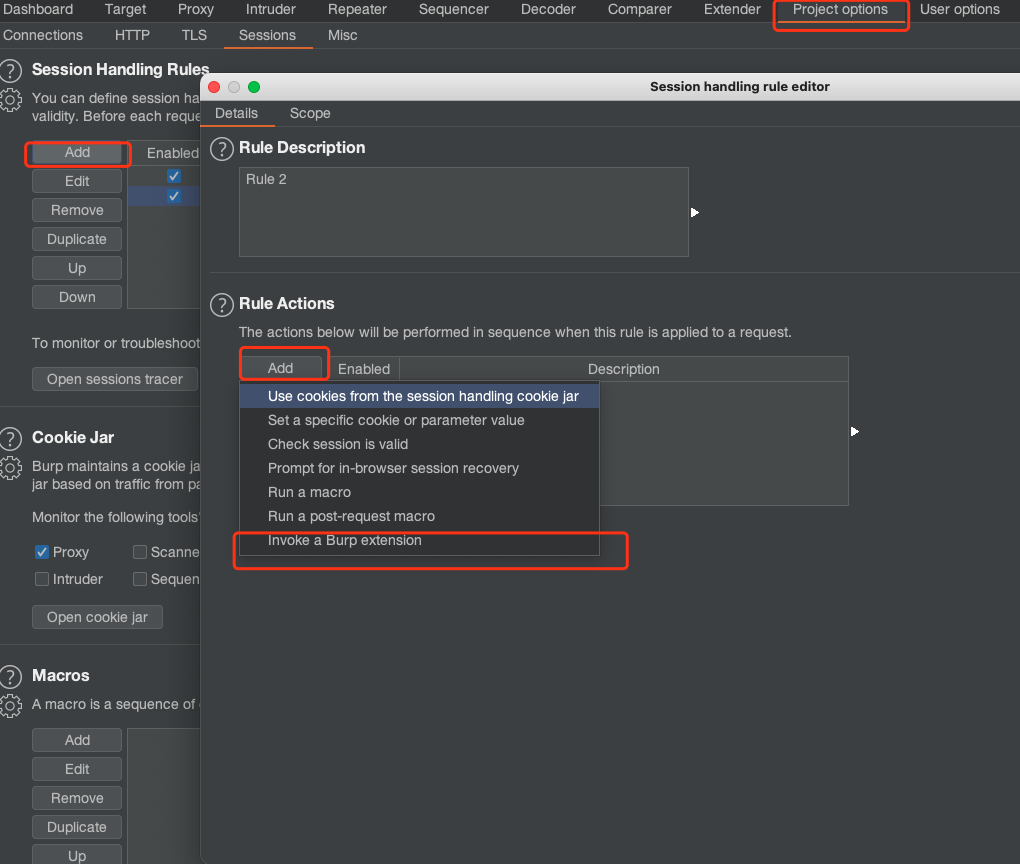
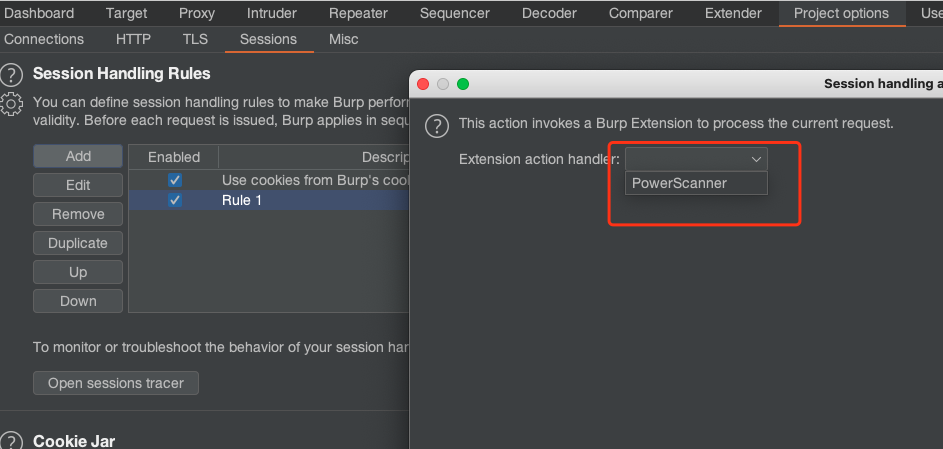
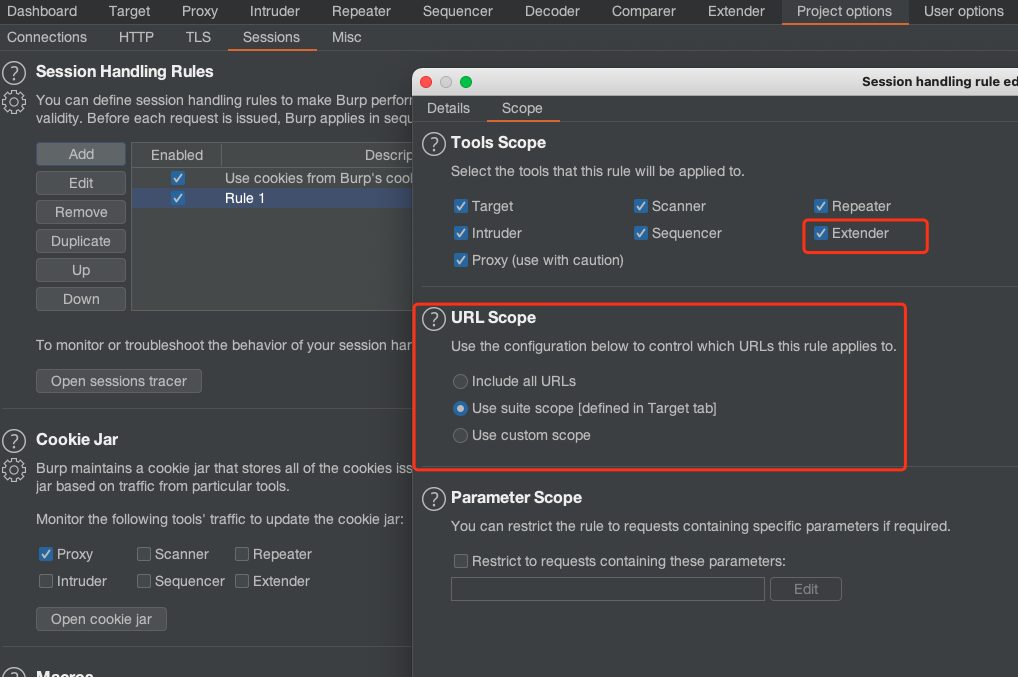
## Bypass WAF
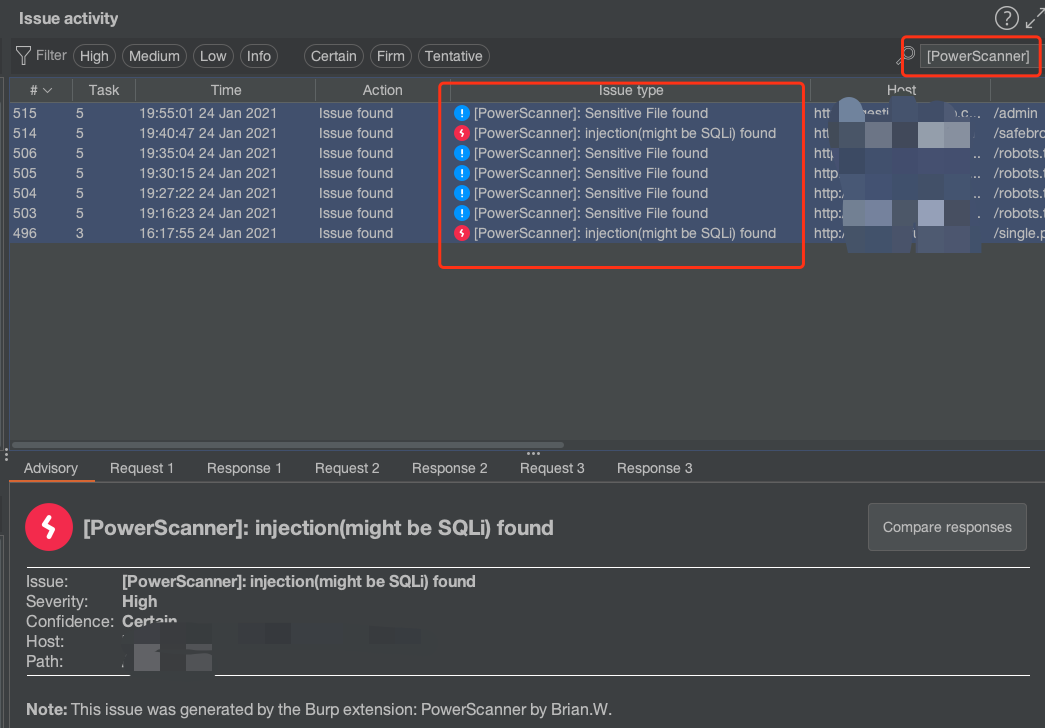
## 扫描结果