https://github.com/P0cL4bs/WiFi-Pumpkin-deprecated
DEPRECATED, wifipumpkin3 -> https://github.com/P0cL4bs/wifipumpkin3
https://github.com/P0cL4bs/WiFi-Pumpkin-deprecated
access-point hacking man-in-the-middle mitm python sniffing wifi wireless
Last synced: 3 months ago
JSON representation
DEPRECATED, wifipumpkin3 -> https://github.com/P0cL4bs/wifipumpkin3
- Host: GitHub
- URL: https://github.com/P0cL4bs/WiFi-Pumpkin-deprecated
- Owner: P0cL4bs
- Archived: true
- Created: 2015-06-27T00:56:21.000Z (almost 10 years ago)
- Default Branch: deprecated
- Last Pushed: 2020-04-18T19:32:52.000Z (about 5 years ago)
- Last Synced: 2025-01-29T14:01:49.432Z (5 months ago)
- Topics: access-point, hacking, man-in-the-middle, mitm, python, sniffing, wifi, wireless
- Language: Python
- Homepage: http://wifipumpkin3.github.io/
- Size: 16 MB
- Stars: 3,108
- Watchers: 268
- Forks: 720
- Open Issues: 39
-
Metadata Files:
- Readme: README.md
Awesome Lists containing this project
README
# This repository is ⛔️ DEPRECATED, [wifipumpkin3](https://github.com/P0cL4bs/wifipumpkin3) is Released, checkout!

[](https://travis-ci.org/P0cL4bs/WiFi-Pumpkin/)

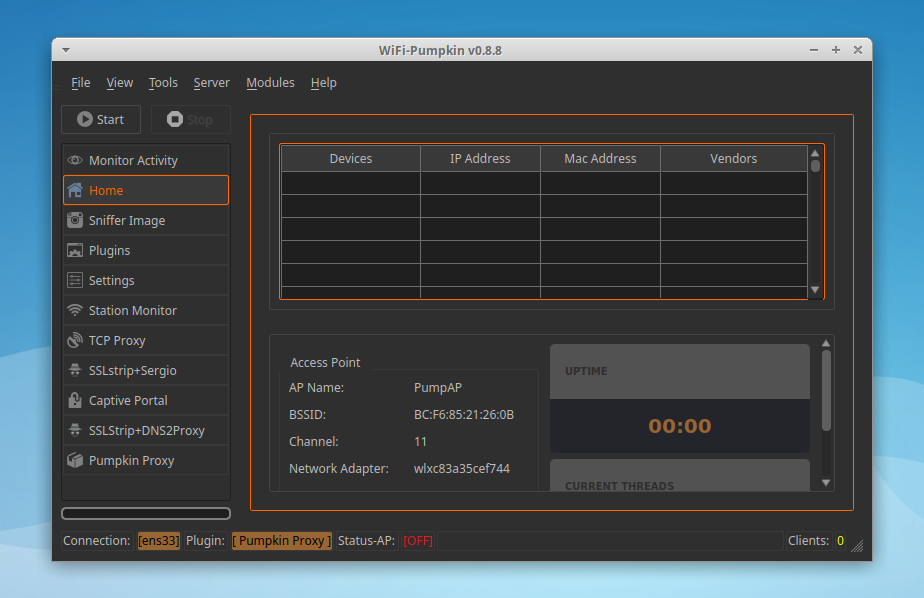
WiFi-Pumpkin - Framework for Rogue Wi-Fi Access Point Attack
### Description
The WiFi-Pumpkin is a rogue AP framework to easily create these fake networks, all while forwarding legitimate traffic to and from the unsuspecting target. It comes stuffed with features, including rogue Wi-Fi access points, deauth attacks on client APs, a probe request and credentials monitor, transparent proxy, Windows update attack, phishing manager, ARP Poisoning, DNS Spoofing, Pumpkin-Proxy, and image capture on the fly. moreover, the WiFi-Pumpkin is a very complete framework for auditing Wi-Fi security check the list of features is quite broad.
### Installation
- Python 2.7
```sh
git clone https://github.com/P0cL4bs/WiFi-Pumpkin.git
cd WiFi-Pumpkin
./installer.sh --install
```
or download [.deb](https://github.com/P0cL4bs/WiFi-Pumpkin/releases) file to install
```sh
sudo dpkg -i wifi-pumpkin-0.8.8-all.deb
sudo apt-get -f install # force install dependencies if not install normally
```
refer to the wiki for [Installation](https://github.com/P0cL4bs/WiFi-Pumpkin/wiki/Installation)
### Features
- Rogue Wi-Fi Access Point
- Deauth Attack Clients AP
- Probe Request Monitor
- DHCP Starvation Attack
- Credentials Monitor
- Transparent Proxy
- Windows Update Attack
- Phishing Manager
- Partial Bypass HSTS protocol
- Support beef hook
- ARP Poison
- DNS Spoof
- Patch Binaries via MITM (BDF-Proxy)
- LLMNR, NBT-NS and MDNS poisoner (Responder)
- Pumpkin-Proxy (ProxyServer (mitmproxy API))
- Capture images on the fly
- TCP-Proxy (with [scapy](http://www.secdev.org/projects/scapy/))
- Moduled plugins and proxys
- Wireless Mode support hostapd-mana/hostapd-karma attacks
- Capitve-portals [new]
### Donation
##### paypal:
[](https://www.paypal.com/cgi-bin/webscr?cmd=_s-xclick&hosted_button_id=PUPJEGHLJPFQL)
##### Via BTC:
1HBXz6XX3LcHqUnaca5HRqq6rPUmA3pf6f
### Plugins
| Plugin | Description |
| :----------------------------------------------------------- | :---------------------------------------------------------------------------------------------------------------------------------------------- |
| [Dns2proxy](https://github.com/LeonardoNve/dns2proxy) | This tools offer a different features for post-explotation once you change the DNS server to a Victim. |
| [Sstrip2](https://github.com/LeonardoNve/sslstrip2) | Sslstrip is a MITM tool that implements Moxie Marlinspike's SSL stripping attacks based version fork @LeonardoNve/@xtr4nge. |
| [Sergio_proxy](https://github.com/supernothing/sergio-proxy) | Sergio Proxy (a Super Effective Recorder of Gathered Inputs and Outputs) is an HTTP proxy that was written in Python for the Twisted framework. |
| [BDFProxy](https://github.com/davinerd/BDFProxy-ng) | Patch Binaries via MITM: BackdoorFactory + mitmProxy, bdfproxy-ng is a fork and review of the original BDFProxy @secretsquirrel. |
| [Responder](https://github.com/lgandx/Responder) | Responder an LLMNR, NBT-NS and MDNS poisoner. Author: Laurent Gaffie |
| [PumpkinProxy]() | Intercepting HTTP data, this proxy server that allows to intercept requests and response on the fly
| [CaptivePortals]() | Captive-Portal allow the Attacker block Internet access for users until they open the page login page where a password is required before being allowed to browse the web. |
### Transparent Proxy
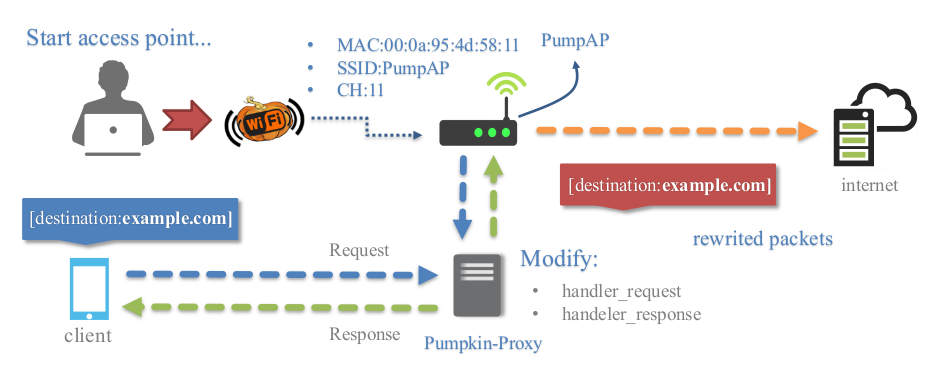
Transparent proxies(mitmproxy) that you can use to intercept and manipulate HTTP traffic modifying requests and responses, that allow to inject javascripts into the targets visited. You can easily implement a module to inject data into pages creating a python file in directory "plugins/extension/" automatically will be listed on Pumpkin-Proxy tab.
#### Plugins Example Dev
```python
from mitmproxy.models import decoded # for decode content html
from plugins.extension.plugin import PluginTemplate
class Nameplugin(PluginTemplate):
meta = {
'Name' : 'Nameplugin',
'Version' : '1.0',
'Description' : 'Brief description of the new plugin',
'Author' : 'by dev'
}
def __init__(self):
for key,value in self.meta.items():
self.__dict__[key] = value
# if you want set arguments check refer wiki more info.
self.ConfigParser = False # No require arguments
def request(self, flow):
print flow.__dict__
print flow.request.__dict__
print flow.request.headers.__dict__ # request headers
host = flow.request.pretty_host # get domain on the fly requests
versionH = flow.request.http_version # get http version
# get redirect domains example
# pretty_host takes the "Host" header of the request into account,
if flow.request.pretty_host == "example.org":
flow.request.host = "mitmproxy.org"
# get all request Header example
self.send_output.emit("\n[{}][HTTP REQUEST HEADERS]".format(self.Name))
for name, valur in flow.request.headers.iteritems():
self.send_output.emit('{}: {}'.format(name,valur))
print flow.request.method # show method request
# the model printer data
self.send_output.emit('[NamePlugin]:: this is model for save data logging')
def response(self, flow):
print flow.__dict__
print flow.response.__dict__
print flow.response.headers.__dict__ #convert headers for python dict
print flow.response.headers['Content-Type'] # get content type
#every HTTP response before it is returned to the client
with decoded(flow.response):
print flow.response.content # content html
flow.response.content.replace('