https://github.com/PwnDexter/Invoke-EDRChecker
Checks running processes, process metadata, Dlls loaded into your current process and the each DLLs metadata, common install directories, installed services, the registry and running drivers for the presence of known defensive products such as AV's, EDR's and logging tools.
https://github.com/PwnDexter/Invoke-EDRChecker
Last synced: 8 months ago
JSON representation
Checks running processes, process metadata, Dlls loaded into your current process and the each DLLs metadata, common install directories, installed services, the registry and running drivers for the presence of known defensive products such as AV's, EDR's and logging tools.
- Host: GitHub
- URL: https://github.com/PwnDexter/Invoke-EDRChecker
- Owner: PwnDexter
- License: bsd-3-clause
- Created: 2019-10-17T20:58:41.000Z (over 6 years ago)
- Default Branch: master
- Last Pushed: 2023-10-09T11:30:27.000Z (over 2 years ago)
- Last Synced: 2024-11-21T18:36:58.901Z (over 1 year ago)
- Language: PowerShell
- Homepage:
- Size: 419 KB
- Stars: 241
- Watchers: 5
- Forks: 49
- Open Issues: 0
-
Metadata Files:
- Readme: README.md
- License: LICENSE
Awesome Lists containing this project
- awesome-hacking-lists - PwnDexter/Invoke-EDRChecker - Checks running processes, process metadata, Dlls loaded into your current process and the each DLLs metadata, common install directories, installed services, the registry and running drivers for the p (PowerShell)
README
# Invoke-EDRChecker
The script will check running processes, process metadata, Dlls loaded into your current process and the each DLLs metadata, common install directories, installed services, the registry and running drivers for the presence of known defensive products such as AV's, EDR's and logging tools.
This script can be loaded into your C2 server as well for example in PoshC2, place the script into your modules directory, load the module then run it. Note: this script is now included in PoshC2 so no need to manually add it.
The script also has capacity to perform checks against remote targets if you have the privileges to do so, these checks are presently limited however to process checking, common install directories and installed services.
I will continue to add and improve the list when time permits. A full roadmap can be found below.
The C# version of this tool is much improved over the PowerShell version and can be found here:
https://github.com/PwnDexter/SharpEDRChecker
Find me on twitter @PwnDexter for any issues or questions!
## Install
```
git clone https://github.com/PwnDexter/Invoke-EDRChecker.git
```
## Usage
Once the script has been loaded into your host or C2 of choice, you can use the following commands:
Run the script against the local host and perform checks based on current user integrity:
```
Invoke-EDRChecker
```
Run the script and force registry checks to be performed (for use when you are not running as admin):
```
Invoke-EDRChecker -Force
```
Run the script against a remote host, this test connectivity and try to resolve the hostname before running:
```
Invoke-EDRChecker -Remote
```
To bypass the pre-checks for remote hosts use -Ignore flag to bypass connectivity checks
```
Invoke-EDRChecker -Remote -Ignore
```
## Example Output - Note: These screenshots need updated and this has only been tested on Windows 10, more testing to come.
If processes and drivers are hidden and still found:
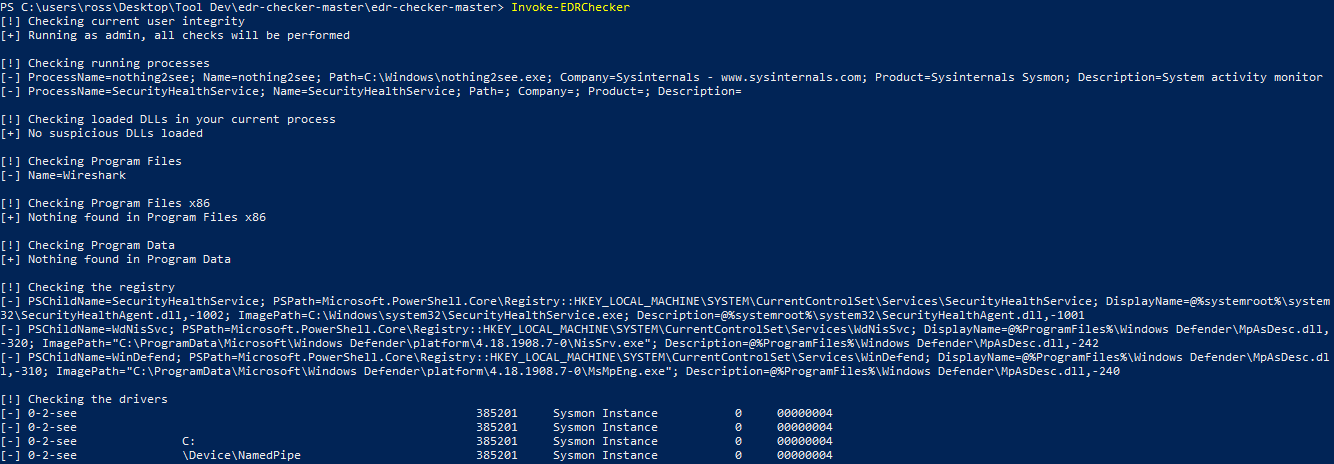
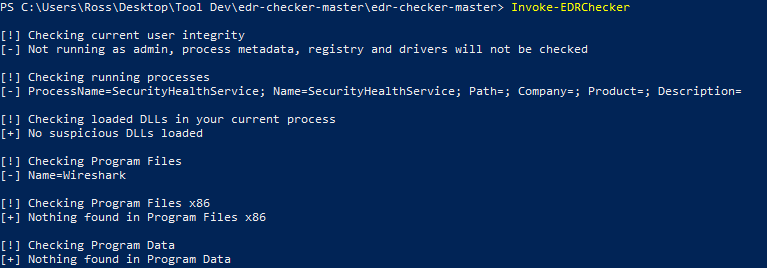
If running as non-admin to show visibility difference:
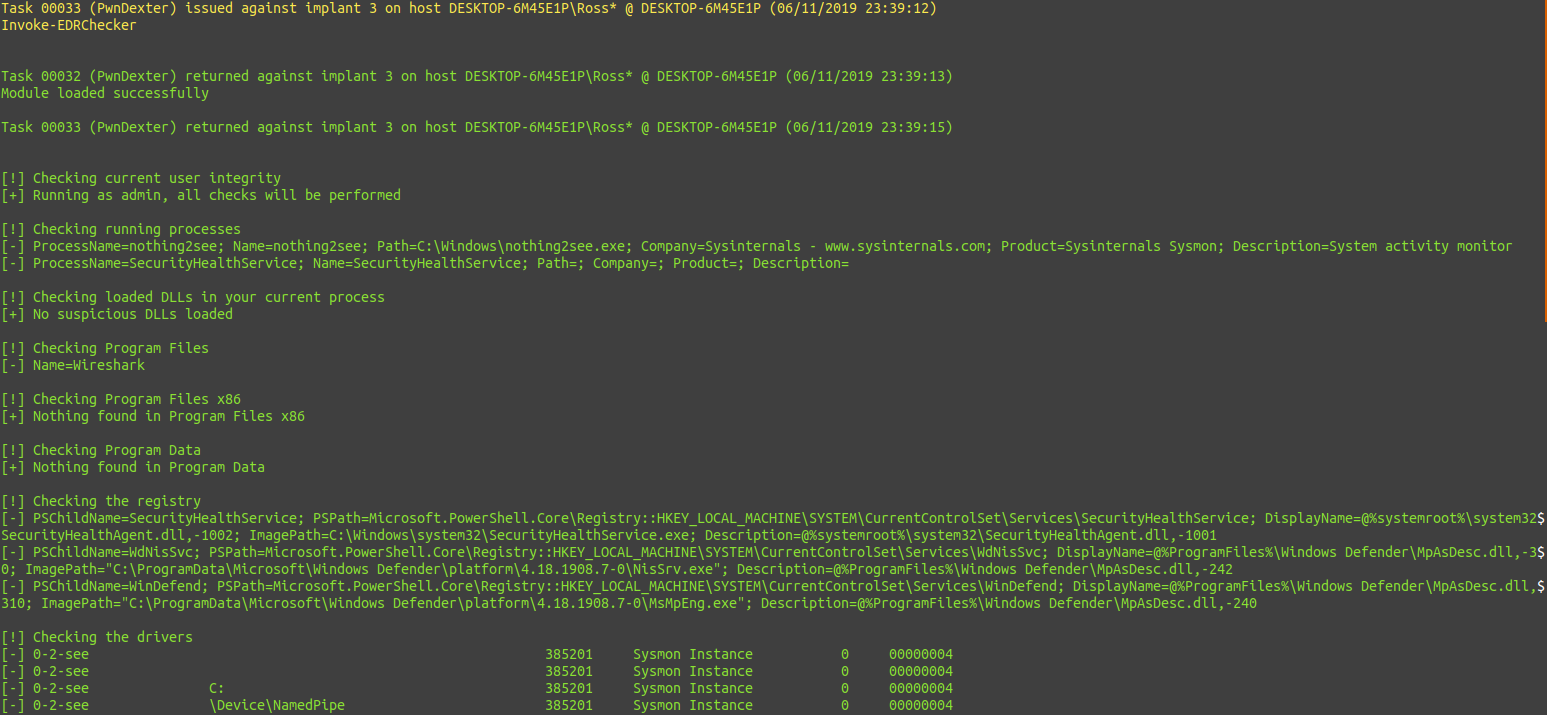
Using EDR-Checker with PoshC2:
## Roadmap
- [ ] - Add more EDR Products - never ending
- [x] - Refine beta function for registry checking
- [x] - Add in force reg check if not running as admin
- [ ] - Test across more Windows and .NET versions
- [x] - Port to c# -
- [x] - Clean up output
- [x] - Get currently loaded DLL's in your current process
- [x] - Get dll metadata of currently loaded dlls
- [x] - Add remote host query capability
- [x] - Add connectivity and DNS checks before performing edr checks
- [ ] - Add remote privilege checks before performing edr checks
- [x] - Add installed services checks
- [ ] - Port to python for unix/macos support