https://github.com/Sh1Yo/request_smuggler
Http request smuggling vulnerability scanner
https://github.com/Sh1Yo/request_smuggler
bugbounty request-smuggling rust scanner security web
Last synced: 10 months ago
JSON representation
Http request smuggling vulnerability scanner
- Host: GitHub
- URL: https://github.com/Sh1Yo/request_smuggler
- Owner: Sh1Yo
- License: gpl-3.0
- Archived: true
- Created: 2021-07-19T15:30:28.000Z (over 4 years ago)
- Default Branch: main
- Last Pushed: 2022-08-11T08:10:22.000Z (over 3 years ago)
- Last Synced: 2025-04-10T10:11:22.760Z (10 months ago)
- Topics: bugbounty, request-smuggling, rust, scanner, security, web
- Language: Rust
- Homepage:
- Size: 32.2 KB
- Stars: 227
- Watchers: 8
- Forks: 30
- Open Issues: 2
-
Metadata Files:
- Readme: README.md
- License: LICENSE
Awesome Lists containing this project
- awesome-hacking-lists - Sh1Yo/request_smuggler - Http request smuggling vulnerability scanner (Rust)
README
[](https://twitter.com/sh1yo_)
[](https://ko-fi.com/B0B858X5E)




Request smuggler
Http request smuggling vulnerability scanner
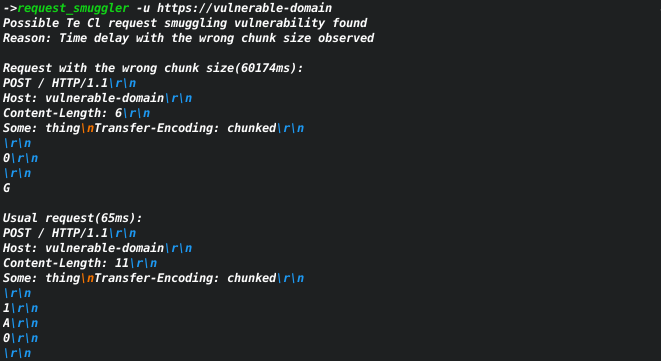
Based on the amazing [research](https://portswigger.net/research/http-desync-attacks-request-smuggling-reborn) by [James Kettle](https://twitter.com/albinowax).
The tool can help to find servers that may be vulnerable to request smuggling vulnerability.
## Archived
The tool needs a lot of improvements, and I don't have enough time to support it as I have another large project - [x8](https://github.com/Sh1Yo/x8). I will probably return to this project in the future.
## Usage
```
USAGE:
request_smuggler [OPTIONS] --url
FLAGS:
-h, --help Prints help information
-V, --version Prints version information
OPTIONS:
--amount-of-payloads low/medium/all [default: low]
-t, --attack-types
[ClTeMethod, ClTePath, ClTeTime, TeClMethod, TeClPath, TeClTime] [default: "ClTeTime" "TeClTime"]
--file
send request from a file
you need to explicitly pass \r\n at the end of the lines
-H, --header Example: -H 'one:one' 'two:two'
-X, --method [default: POST]
-u, --url
-v, --verbose
0 - print detected cases and errors only,
1 - print first line of server responses
2 - print requests [default: 0]
--verify how many times verify the vulnerability [default: 2]
```
## Installation
- Linux
- from releases
- from source code (rust should be installed)
```bash
git clone https://github.com/Sh1Yo/request_smuggler
cd request_smuggler
cargo build --release
```
- using cargo install
```bash
cargo install request_smuggler --version 0.1.0-alpha.2
```
- Mac
- from source code (rust should be installed)
```bash
git clone https://github.com/Sh1Yo/request_smuggler
cd request_smuggler
cargo build --release
```
- using cargo install
```bash
cargo install request_smuggler --version 0.1.0-alpha.2
```
- Windows
- from releases