https://github.com/Signiant/aws-iam-slack-notifer
Notifies slack when an IAM policy is created, changed or assigned to a role
https://github.com/Signiant/aws-iam-slack-notifer
aws aws-lambda iam iam-policy slack
Last synced: 8 months ago
JSON representation
Notifies slack when an IAM policy is created, changed or assigned to a role
- Host: GitHub
- URL: https://github.com/Signiant/aws-iam-slack-notifer
- Owner: Signiant
- License: mit
- Created: 2017-09-26T20:53:46.000Z (over 8 years ago)
- Default Branch: master
- Last Pushed: 2021-06-13T17:04:19.000Z (over 4 years ago)
- Last Synced: 2025-04-20T11:43:10.060Z (9 months ago)
- Topics: aws, aws-lambda, iam, iam-policy, slack
- Language: Python
- Size: 183 KB
- Stars: 33
- Watchers: 6
- Forks: 6
- Open Issues: 2
-
Metadata Files:
- Readme: README.md
- License: LICENSE
Awesome Lists containing this project
README
# aws-iam-policy-slack-notifer
Notifies slack when an IAM policy is created, changed or assigned to a role
[](https://travis-ci.org/Signiant/aws-iam-slack-notifer)
# Purpose
Notifies a slack channel when an AWS IAM policy is manipulated
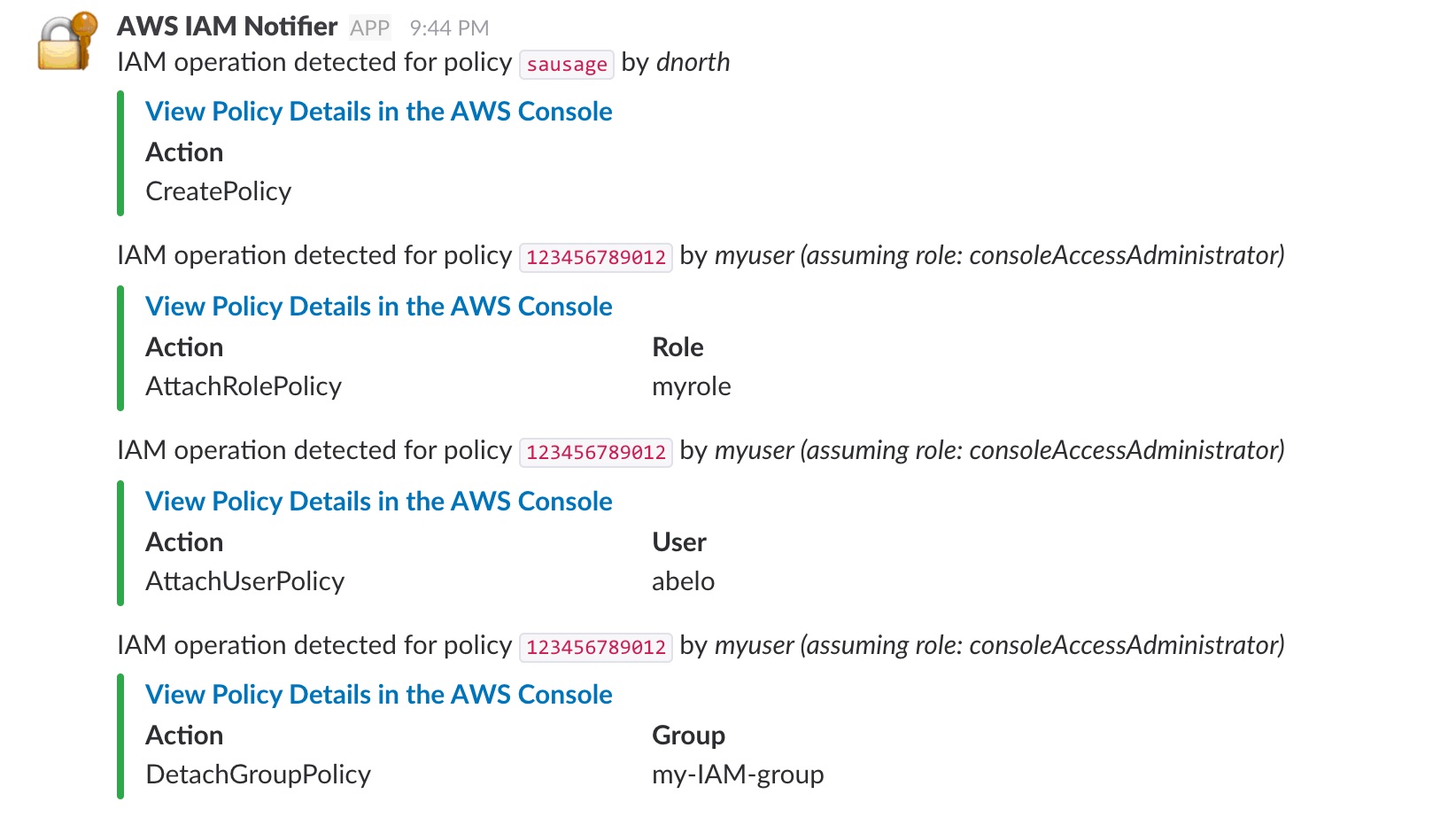
# Sample Output
# Installing and Configuring
## Slack Setup
Before installing anything to AWS, you will need to configure a "bot" in Slack to handle the posts for you. To do this:
* In Slack, choose _Manage Apps_ -> _Custom Integrations_ -> _Bots_
* Add a new bot configuration
* username: aws-iam-notifier
* Copy the API Token.
* Don't worry about other parameters - the notifier over-rides them anyway
## AWS Setup
* Grab the latest Lambda function zip from [Releases](https://github.com/Signiant/aws-iam-slack-notifer/releases)
* Create a new cloudformation stack using the template in the cfn folder
The stack asks for the function zip file location in S3, the slack API Key and the slack channel to post notifications to. Once the stack is created, a cloudwatch event is created to subscribe the lambda function to several IAM events around policy manipulation.
## Filtering Slack Alerts
Using some optional environment variables defined on the Lambda function, you can also exclude certain Slack notifications for specific policy manipultation events. Set the following variables on the function to `0` if you wish to exclude these events from notifying Slack:
* CREATE_POLICY_NOTIFY
* CREATE_POLICY_VERSION_NOTIFY
* ATTACH_GROUP_POLICY_NOTIFY / DETACH_GROUP_POLICY_NOTIFY
* ATTACH_USER_POLICY_NOTIFY / DETACH_USER_POLICY_NOTIFY
* ATTACH_ROLE_POLICY_NOTIFY / DETACH_ROLE_POLICY_NOTIFY