https://github.com/astefanutti/kubebox
⎈❏ Terminal and Web console for Kubernetes
https://github.com/astefanutti/kubebox
console cui dashboard gui kubernetes monitoring openshift terminal tui
Last synced: 9 months ago
JSON representation
⎈❏ Terminal and Web console for Kubernetes
- Host: GitHub
- URL: https://github.com/astefanutti/kubebox
- Owner: astefanutti
- License: mit
- Created: 2016-11-18T18:21:27.000Z (about 9 years ago)
- Default Branch: master
- Last Pushed: 2024-06-17T13:05:26.000Z (over 1 year ago)
- Last Synced: 2025-05-09T22:49:43.360Z (9 months ago)
- Topics: console, cui, dashboard, gui, kubernetes, monitoring, openshift, terminal, tui
- Language: JavaScript
- Homepage: http://astefanutti.github.io/kubebox
- Size: 18.4 MB
- Stars: 2,200
- Watchers: 47
- Forks: 143
- Open Issues: 40
-
Metadata Files:
- Readme: README.adoc
- License: LICENSE
Awesome Lists containing this project
- awesome-k8s-resources - Kubebox - Terminal and Web console for Kubernetes (Tools and Libraries / Command Line Tools)
- awesome-blessed - kubebox
- awesome-cloud-native - kubebox - Terminal console for Kubernetes clusters. (Developer Workspaces & Productivity)
- k8s_awesome_document - Kubebox - --Kubebox是Kubernetes集群的终端控制台,它允许您使用漂亮的老式界面来管理和监控集群活动状态。Kubebox显示pod资源使用情况、集群监控和容器日志等。此外,您可以轻松导航到所需的名称空间,并执行到所需的容器中,以便快速进行故障排除/恢复。 (🏗相关开源项目 / 监控工具)
- awesome-ops - astefanutti/kubebox - 11-18|2024-06-17 | K8s 终端版管理工具 | (K8S-Tools)
- terminals-are-sexy - kubebox - Terminal console for Kubernetes. (Tools and Plugins / Windows)
- awesome-kubernetes - Kubebox - Terminal console for Kubernetes (Monitoring Services / [Jenkins](#jenkins))
- fucking-terminals-are-sexy - kubebox - Terminal console for Kubernetes. (Tools and Plugins / Windows)
README
= Kubebox [small]#^⎈❏^#
Antonin Stefanutti
// Meta
:description: Terminal and Web console for Kubernetes
// Settings
:idprefix:
:idseparator: -
:experimental:
// Aliases
ifdef::env-github[]
:note-caption: :information_source:
:icon-check: :heavy_check_mark:
:icon-edit: :pencil2:
endif::[]
ifndef::env-github[]
:icons: font
:icon-check: icon:check[]
:icon-edit: icon:pencil[fw]
endif::[]
// URIs
:uri-kubebox-download: https://github.com/astefanutti/kubebox/releases/download/v0.10.0
:uri-kubebox-twitter: https://twitter.com/kubebox
:uri-kube-apiserver: https://kubernetes.io/docs/admin/kube-apiserver/
:uri-ingress-controllers: https://kubernetes.io/docs/concepts/services-networking/ingress/#ingress-controllers
:uri-service-account: https://kubernetes.io/docs/tasks/configure-pod-container/configure-service-account/
:uri-xterm-js: https://github.com/xtermjs/xterm.js
:uri-cadvisor: https://github.com/google/cadvisor
{description}
// image::./docs/kubebox.png[kubebox, align="center"]
++++
++++
=== Features
* [x] Configuration from _kubeconfig_ files (`KUBECONFIG` environment variable or `$HOME/.kube`)
* [x] Switch contexts interactively
* [x] <> (bearer token, basic auth, private key / cert, OAuth, OpenID Connect, Amazon EKS, Google Kubernetes Engine, Digital Ocean)
* [x] Namespace selection and pods list watching
* [x] Container log scrolling / watching
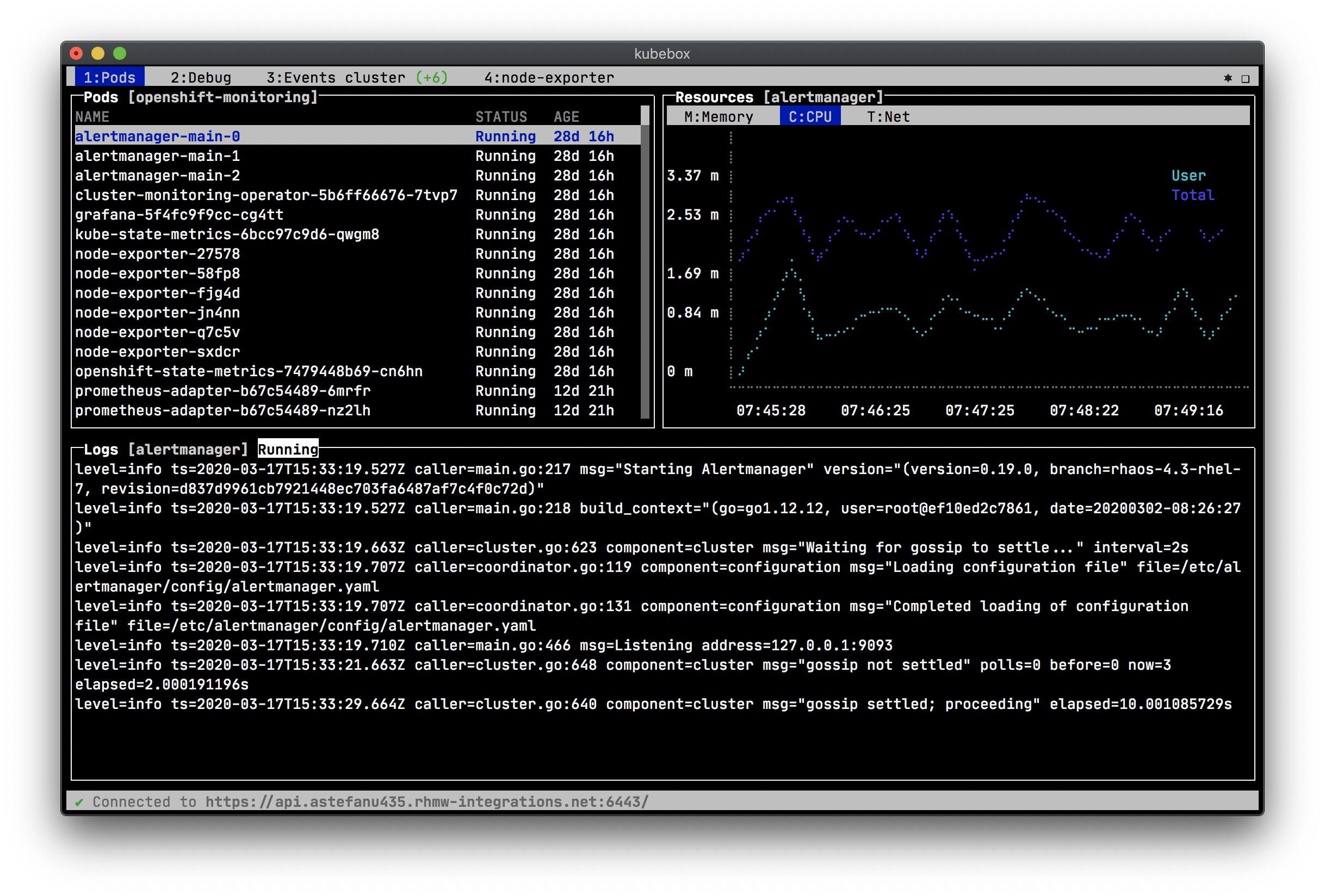
* [x] Container resources usage (memory, CPU, network, file system charts) footnote:[Requires {uri-cadvisor}[cAdvisor] to be deployed as a DaemonSet. See the <> section for more details.]
* [x] Container remote exec terminal
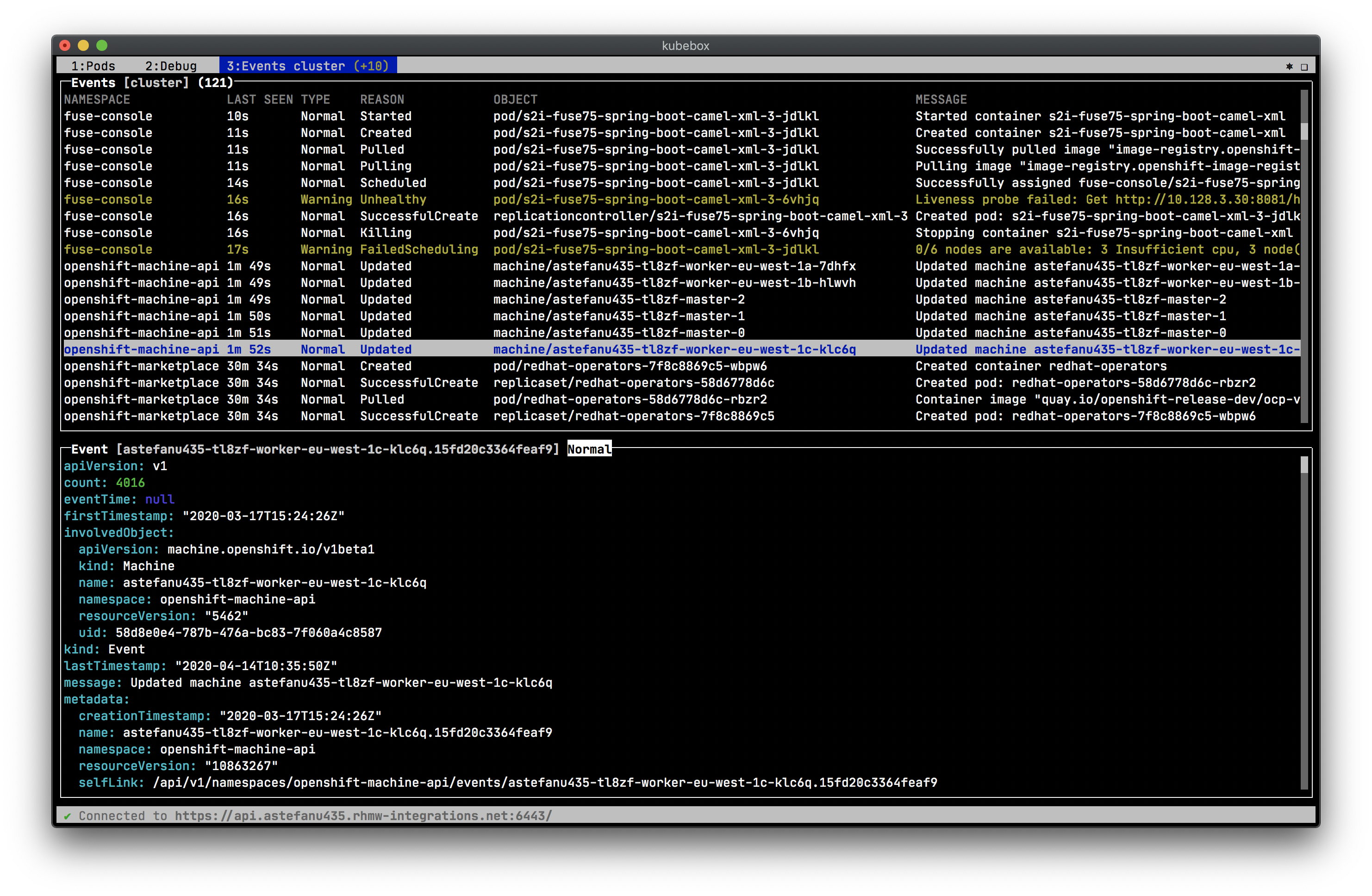
* [x] Cluster, namespace, pod events
* [ ] Object configuration editor and CRUD operations
* [ ] Cluster and nodes views / monitoring
See the <> section for some examples, and follow image:https://img.shields.io/badge/%40kubebox-00ACEE.svg?&logo=twitter&colorA=555&logoColor=fff[link={uri-kubebox-twitter}] for some updates.
== Run
The following alternatives are available for you to use Kubebox, depending on your preferences and constraints:
=== Executable
Download the Kubebox standalone executable for your OS:
[source,shell,subs=attributes+]
----
# Linux (x86_64)
$ curl -Lo kubebox {uri-kubebox-download}/kubebox-linux && chmod +x kubebox
# Linux (ARMv7)
$ curl -Lo kubebox {uri-kubebox-download}/kubebox-linux-arm && chmod +x kubebox
# OSX
$ curl -Lo kubebox {uri-kubebox-download}/kubebox-macos && chmod +x kubebox
# Windows
$ curl -Lo kubebox.exe {uri-kubebox-download}/kubebox-windows.exe
----
Then run:
```sh
$ ./kubebox
```
=== Server
Kubebox can be served from a service hosted in your Kubernetes cluster.
Terminal emulation is provided by {uri-xterm-js}[Xterm.js] and the communication with the Kubernetes master API is proxied by the server.
To deploy the server in your Kubernetes cluster, run:
```console
$ kubectl apply -f https://raw.github.com/astefanutti/kubebox/master/kubernetes.yaml
```
To shut down the server and clean-up resources, run:
```console
$ kubectl delete namespace kubebox
```
For the Ingress resource to work, the cluster must have an Ingress controller running.
See {uri-ingress-controllers}[Ingress controllers] for more information.
Alternatively, to deploy the server in your OpenShift cluster, run:
```sh
$ oc new-app -f https://raw.github.com/astefanutti/kubebox/master/openshift.yaml
```
=== Kubectl
You can run Kubebox as an _in-cluster_ client with `kubectl`, e.g.:
```sh
$ kubectl run kubebox -it --rm --env="TERM=xterm" --image=astefanutti/kubebox --restart=Never
```
If RBAC is enabled, you'll have to use the `--serviceaccount` option and reference a service account with sufficient permissions.
=== Docker
You can run Kubebox using Docker, e.g.:
```sh
$ docker run -it --rm astefanutti/kubebox
```
You may want to mount your home directory so that Kubebox can rely on the `~/.kube/config` file, e.g.:
```sh
$ docker run -it --rm -v ~/.kube/:/home/node/.kube/:ro astefanutti/kubebox
```
=== Online
Kubebox is available online at https://astefanutti.github.com/kubebox.
Note that it requires this address to match the allowed origins for CORS by the API server.
This can be achived with the {uri-kube-apiserver}[Kubernetes API server CLI], e.g.:
```sh
$ kube-apiserver --cors-allowed-origins .*
```
== Authentication
We try to support the various authentication strategies supported by `kubectl`, in order to provide seamless integration with your local setup. Here are the different authentication strategies we support, depending on how you're using Kubebox:
[cols="<,^,^,^",options="header"]
|===
||Executable|Docker|Online
|OpenID Connect
|{icon-check}
|{icon-check}
|{icon-check}footnote:[Custom IDP certificate authority files are not supported in Web versions.]
|Amazon EKS|
{icon-check}
|
|
|Digital Ocean
|{icon-check}
|
|
|Google Kubernetes Engine|
{icon-check}
|
|
|===
If the mode you're using isn't supported, you can refresh the authentication token/certs manually and update your _kubeconfig_ file accordingly.
== cAdvisor
Kubebox relies on {uri-cadvisor}[cAdvisor] to retrieve the resource usage metrics.
Before version 0.8.0, Kubebox used to access the cAdvisor endpoints, that are embedded in the _Kubelet_. However, these endpoints are being deprecated, and will eventually be removed, as discussed in https://github.com/kubernetes/kubernetes/issues/68522[kubernetes#68522].
Starting version 0.8.0, Kubebox expects cAdvisor to be deployed as a https://kubernetes.io/docs/concepts/workloads/controllers/daemonset/[DaemonSet].
This can be achieved with:
```sh
$ kubectl apply -f https://raw.githubusercontent.com/astefanutti/kubebox/master/cadvisor.yaml
```
It's recommended to use the provided `cadvisor.yaml` file, that's tested to work with Kubebox.
However, the DaemonSet example, from the {uri-cadvisor}[cAdvisor] project, should also work just fine.
Note that the cAdvisor containers must run with a _privileged_ security context, so that they can access the container runtime on each node.
You can change the default `--storage_duration` and `--housekeeping_interval` options, added to the cAdvisor container arguments declared in the `cadvisor.yaml` file, to adjust the duration of the storage moving window (default to `5m0s`), and the sampling period (default to `10s`) respectively.
You may also have to provide the path of your cluster container runtime socket, in case it's not following the usual convention.
== Hotkeys
[cols="1v,2v"]
|===
|Keybinding |Description
2+^.e|General
|kbd:[l], kbd:[Ctrl+l]
|Login
|kbd:[n]
|Change current namespace
|[kbd:[Shift]\+]kbd:[←], kbd:[→] +
[kbd:[Alt]+]kbd:[1], ..., kbd:[9]
|Navigate screens +
(use kbd:[Shift] or kbd:[Alt] inside exec terminal)
|kbd:[Tab], kbd:[Shift+Tab]
|Change focus within the active screen
|kbd:[↑], kbd:[↓]
|Navigate list / form / log
|kbd:[PgUp], kbd:[PgDn]
|Move one page up / down
|kbd:[Enter]
|Select item / submit form
|kbd:[Esc]
|Close modal window / cancel form
|kbd:[Ctrl+z]
|Close current screen
|kbd:[q], kbd:[Ctrl+q]
|Exit footnote:[Not available in Web versions.]
2+^.e|Login
|kbd:[←], kbd:[→]
|Navigate Kube configurations
2+^.e|Pods
|kbd:[Enter]
|Select pod / cycle containers
|kbd:[r]
|Remote shell into container
|kbd:[m]
|Memory usage
|kbd:[c]
|CPU usage
|kbd:[t]
|Network usage
|kbd:[f]
|File system usage
|kbd:[e]
|Pod events
|kbd:[Shift+e]
|Namespace events
|kbd:[Ctrl+e]
|Cluster events
|===
== FAQ
* *_Resources usage metrics are unavailable!_*
+
** Starting version 0.8.0, Kubebox expects {uri-cadvisor}[cAdvisor] to be deployed as a DaemonSet. See the <> section for more details;
** The metrics are retrieved from the REST API, of the cAdvisor pod running on the same node as the container for which the metrics are being requested. That REST API is accessed via the API server proxy, which requires proper RBAC permission, e.g.:
+
[source,shell]
----
# Permission to list the cAdvisor pods (selected using the `spec.nodeName` field selector)
$ kubectl auth can-i list pods -n cadvisor
yes
# Permission to proxy the selected cAdvisor pod, to call its REST API
$ kubectl auth can-i get pod --subresource proxy -n cadvisor
yes
----
== Development
```sh
$ git clone https://github.com/astefanutti/kubebox.git
$ cd kubebox
$ npm install
$ node index.js
```
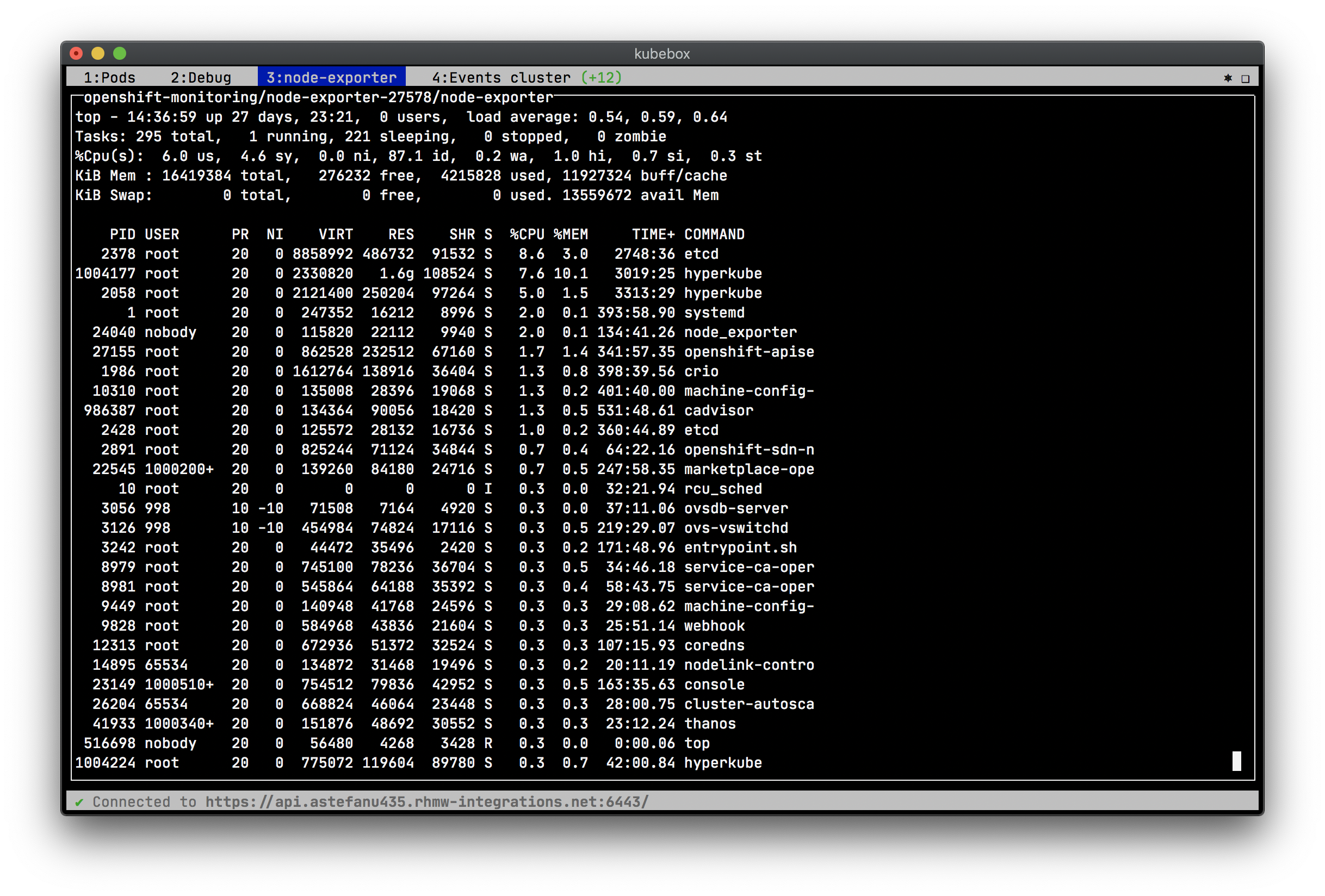
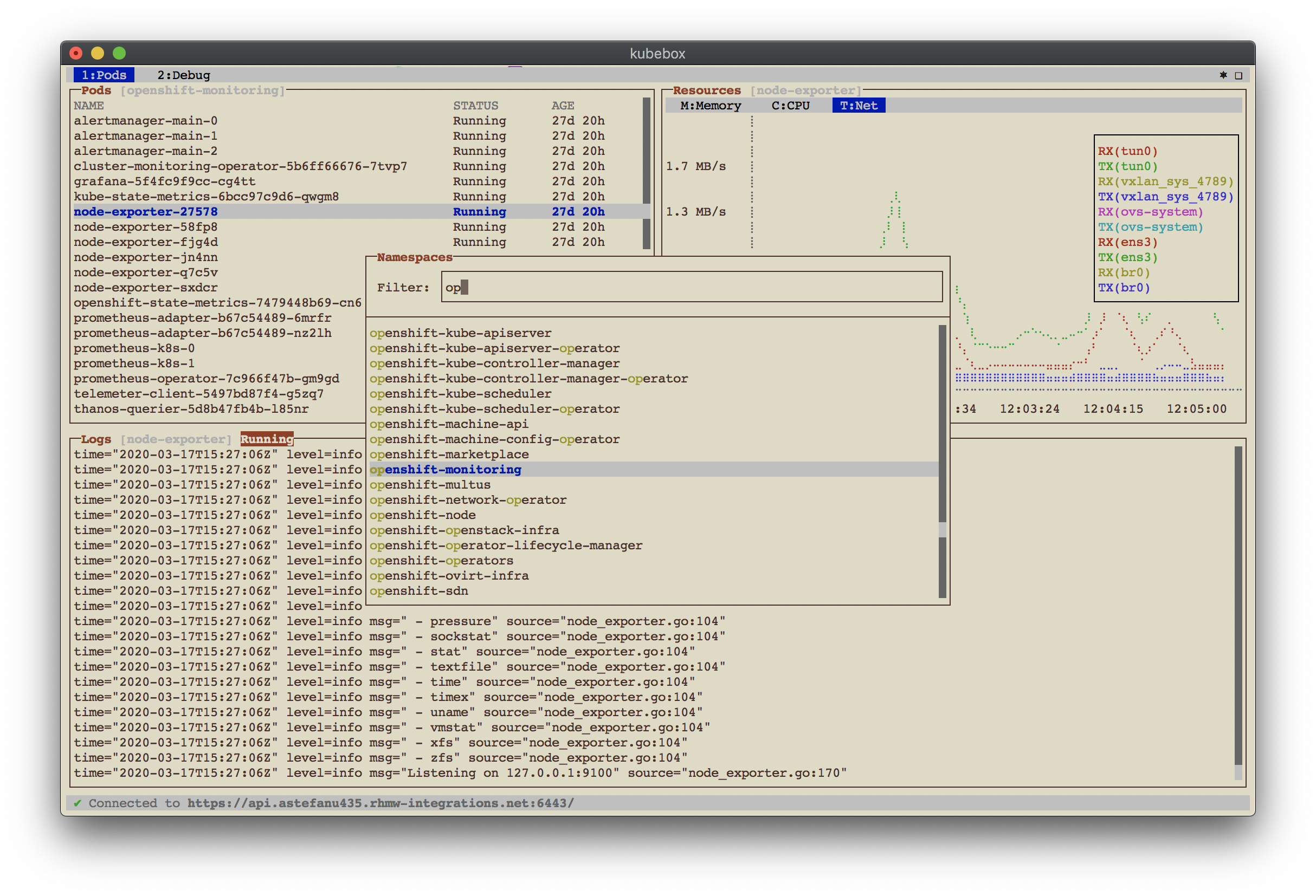
== Screenshots
Cluster events:
++++
++++
Shell into a container:
++++
++++
Terminal theme support:
++++
++++
Web browser version:
++++
++++