https://github.com/azagramac/adguardhome-docker
Official Adguard Home image to deploy in a docker container, DNS server blocking ads and trackers in the whole network, with DNS over TLS, DNS over HTTP, DNSSEC..., all in a docker container, compatible with RaspberryPi, NanoPi, Synology...
https://github.com/azagramac/adguardhome-docker
adguard adguard-blocklist adguard-dns adguard-home adguard-home-blocklist adguard-list adguardhome docker docker-compose docker-container docker-image docker-images docker-swarm
Last synced: 4 months ago
JSON representation
Official Adguard Home image to deploy in a docker container, DNS server blocking ads and trackers in the whole network, with DNS over TLS, DNS over HTTP, DNSSEC..., all in a docker container, compatible with RaspberryPi, NanoPi, Synology...
- Host: GitHub
- URL: https://github.com/azagramac/adguardhome-docker
- Owner: azagramac
- License: gpl-3.0
- Created: 2023-12-10T18:30:05.000Z (almost 2 years ago)
- Default Branch: master
- Last Pushed: 2025-01-10T19:37:05.000Z (10 months ago)
- Last Synced: 2025-04-02T07:21:59.811Z (7 months ago)
- Topics: adguard, adguard-blocklist, adguard-dns, adguard-home, adguard-home-blocklist, adguard-list, adguardhome, docker, docker-compose, docker-container, docker-image, docker-images, docker-swarm
- Homepage:
- Size: 49.8 KB
- Stars: 7
- Watchers: 2
- Forks: 0
- Open Issues: 0
-
Metadata Files:
- Readme: README.md
- Funding: .github/FUNDING.yml
- License: LICENSE
Awesome Lists containing this project
README
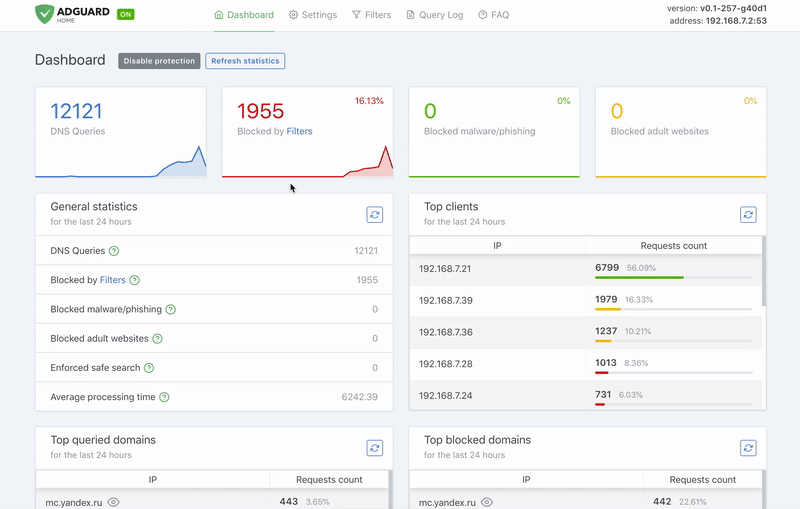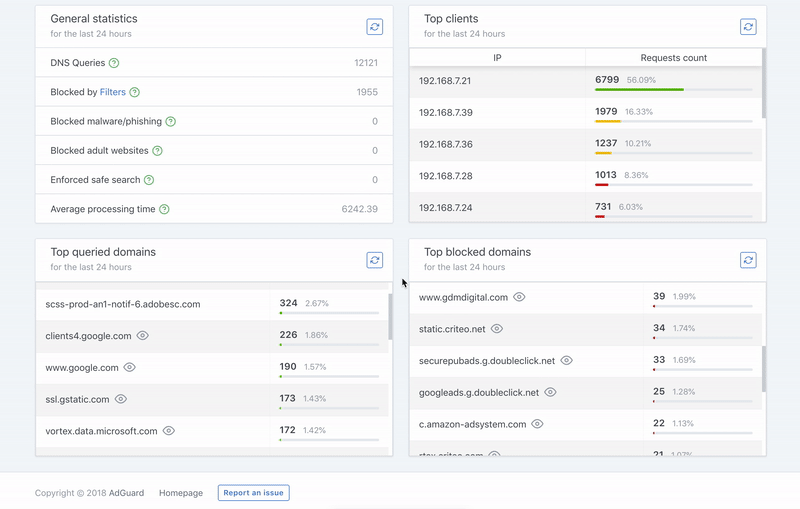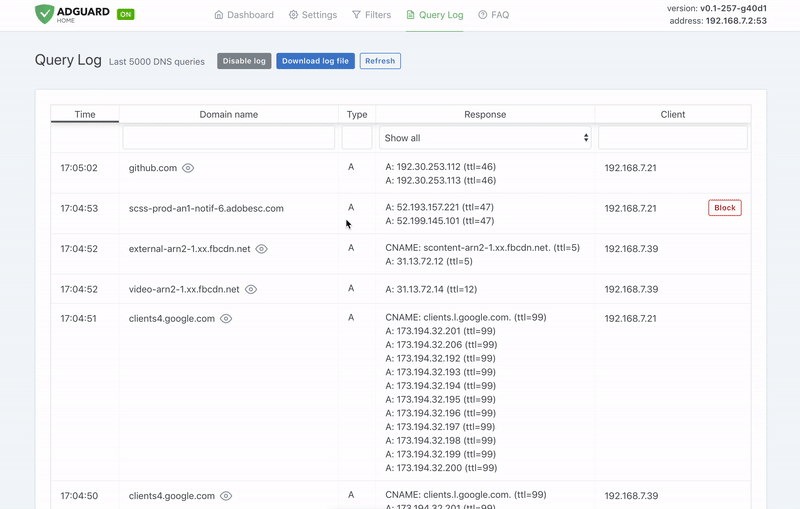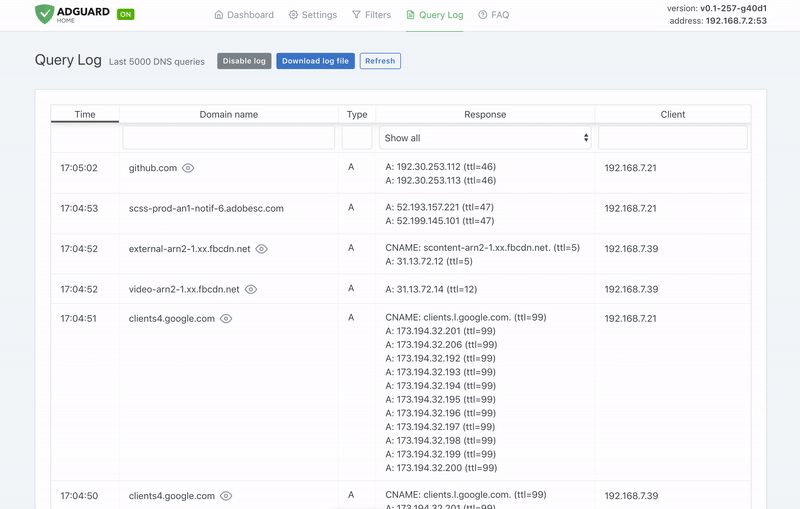
### Requeriments
- Service docker running
### Install Docker
sudo apt update && sudo apt install git vim wget curl net-tools ca-certificates gnupg -y
sudo install -m 0755 -d /etc/apt/keyrings
sudo curl -fsSL https://download.docker.com/linux/debian/gpg -o /etc/apt/keyrings/docker.asc
sudo chmod a+r /etc/apt/keyrings/docker.asc
echo \
"deb [arch=$(dpkg --print-architecture) signed-by=/etc/apt/keyrings/docker.asc] https://download.docker.com/linux/debian \
$(. /etc/os-release && echo "$VERSION_CODENAME") stable" | \
sudo tee /etc/apt/sources.list.d/docker.list > /dev/null
sudo apt update && sudo apt install docker-ce docker-ce-cli containerd.io docker-buildx-plugin docker-compose-plugin -y
sudo usermod -aG docker $USER
sudo reboot
### Test Docker
$ docker version
Client: Docker Engine - Community
Version: 24.0.2
API version: 1.43
Go version: go1.20.4
Git commit: cb74dfc
Built: Thu May 25 21:52:41 2023
OS/Arch: linux/arm64
Context: default
$ docker compose version
Docker Compose version v2.18.1
### Clone repo
git clone https://github.com/AzagraMac/adguardhome-docker.git
### Running
cd adguardhome-docker
docker-compose up -d
### Check
docker ps -a
### Running on docker swarm
cd adguardhome-docker
docker stack deploy --compose-file compose.yml adguard
### Check on docker swarm
docker service ls
ID NAME MODE REPLICAS IMAGE PORTS
6vi2dutbvbqp adguard_adblock replicated 1/1 adguard/adguardhome:latest
docker service ps adguard_adblock
ID NAME IMAGE NODE DESIRED STATE CURRENT STATE ERROR PORTS
jslnz3p5xj8i adguard_adblock.1 adguard/adguardhome:latest master Running Running about an hour ago *:53->53/udp,*:443->443/tcp,*:53->53/tcp,*:68->68/udp,*:8853->8853/udp,*:443->443/udp,*:67->67/udp,*:784->784/udp,*:5443->5443/tcp,*:68->68/tcp,*:5443->5443/udp,*:3000->3000/tcp,*:853->853/tcp
## Adguard Home® configuration: 
### Setting to have DNS over TLS or DNS over HTTPS enabled
In AdGuard settings, DNS settings:
- Upstream DNS servers, copy one of these URLs:
For Cloudfare DoH-DoT:
```
https://dns.cloudflare.com/dns-query
tls://1dot1dot1dot1.cloudflare-dns.com
```
For DoH-DoT de Quad9:
```
https://dns.quad9.net/dns-query
tls://dns.quad9.net
```
and check the option: "**Load balancing**", by default this option is checked.
- Boot DNS servers, we put the DNS of our choice:
Cloudflared in both IPv4 and IPv6:
```
1.1.1.1
1.0.0.1
2606:4700:4700::1111
2606:4700:4700::1001
```
Quad9 in both IPv4 and IPv6:
```
9.9.9.9
149.112.112.112
2620:fe::fe
2620:fe::fe:9
```
- DNS server configuration, check the option "**Enable DNSSEC**".
## Add domain for DoH and DoT:
### Create the certificate with Let's Encrypt
Create the self-signed personal certificate with Let's Encrypt:
#### Create the self-signed personal certificate with Let's Encrypt:
Installing a free SSL certificate with CertBot:
1. We update the list of packages.
~~~
sudo apt-get update
~~~
2. Install the Certbot package
~~~
sudo apt-get install certbot
~~~
3. Run the following command modifying the valid email to acquire a Wildcard certificate:
~~~
certbot certonly --manual --preferred-challenges=dns --rsa-key-size 4096 --email usuario@ejemplo.com --agree-tos --server https://acme-v02.api.letsencrypt.org/directory -d "*.your_domain"
~~~
4. Finally, it will ask to make an _acme-challenge TXT record in our name server provider with the content it tells us:
It creates the following files, in the directory /etc/letsencrypt/live/:
- fullchain.pem – your SSL certificate encrypted in PEM.
- privkey.pem – your private key encrypted in PEM.
#### Configuración de Lets encrypt
Steps to follow after requesting the certificate:
* You will be prompted to enter the domain to be certified, enter it using *. plus the domain you wish to certify to obtain the Wildcard.
* Finally, it will ask you to register _acme-challenge TXT type in our name server provider with the content you indicate.
To check if the certificate will self-renew:
* Renewal test (simulación):certbot renew --dry-run
* Check the status of the Certbot timer service: systemctl status certbot.timer
* To renew a certificate: certbot renew
* To force self-renewal: --force-renewal
* To list jobs: systemctl list-timers --all Debe aparecer el siguiente configurado para la renovación automática: certbot.timer - certbot.service
* Listing certificates: certbot certificates
To revoke a certificate:
* Delete a certificate completely: certbot delete --cert-name example.com
* From the account for which the certificate was issued: certbot revoke --cert-path /etc/letsencrypt/archive/${YOUR_DOMAIN}/cert1.pem
* Using the certificate's private key: certbot revoke --cert-path /PATH/TO/cert.pem --key-path /PATH/TO/key.pem
If you don't want to go through all these steps, you can obtain the certificate with [Zero SSL](https://zerossl.com/). but the wildcard certificate is via payment.
### Create the self-signed personal certificate with OPENSSL:
Create the self-signed personal certificate:
#### Crear el certificado personal autofirmado:
Info: [INFO](https://www.busindre.com/comandos_openssl_utiles_para_certificados)
1. We update the list of packages.
~~~
sudo apt-get update
~~~
2. Install the openssl package
~~~
sudo apt-get install openssl
~~~
3. Create the directory where we want to store the certificates:
~~~
mkdir certs
cd certs/
~~~
4. Create certificate with the following command, changing the certificate path or leave the name of the .key and dot crt to store it in the directory:
~~~
sudo openssl req -x509 -nodes -days 1825 -sha384 -newkey ec:secp384r1 -keyout privkey.key -out privcert.pem
~~~
* You may ask us these questions:
Country Name (2 letter code) [AU]: USState or Province Name (full name) [Some-State]: New YorkLocality Name (eg, city) []: New York CityOrganization Name (eg, company) [Internet Widgits Pty Ltd]: Bouncy Castles, Inc.Organizational Unit Name (eg, section) []: Ministry of Water SlidesCommon Name (e.g. server FQDN or YOUR name) []: server_IP_address or domainEmail Address []: admin@your_domain.com## Configure certificate in AdGuard Home:
1. Open the AdGuard Home web interface and go to configuration.
2. Scroll down the menu to settings: Encryption settings.
3. Enable checkEnable encryption (HTTPS, DNS via HTTPS and DNS via TLS).
4. Enable Redirect to HTTPS automatically.
5. Enter your domain name in Server name. If you are entering a wildcard, enter the domain name only"example.com".
6. Copy/paste the contents of the file `fullchain.pem` in Certificados.
7. Copy / paste the contents of the file `privkey.pem` in Private key.
8. Click Save configuration.
## Configure the domain to allow private DNS DoH and DoT clients:
To create a zone in your domain for both *.example.org to enable clients, follow these steps:
#### Instructions for use:
1. Log into the control panel of your web hosting provider or domain registrar where you purchased the domain name.
2. Find the `DNS Zones` option.
3. Create a new `DNS Zones` entry. To add the entry for each client, e.g. `one.example.org`.
This will allow the client created in the `Client Configuration` panel to connect.
4. Configure `Settings/Client Configuration/Persistent clients`. Click `Add Clients` and under `Identifier` create a name.
Current instructions in the developer's documentation documentación.
## Change password in Adguard
In order to change the password in Adguard we can access these websites and create a username and password:
- [web2generators](https://www.web2generators.com/apache-tools/htpasswd-generator)
- [ipvoid](https://www.ipvoid.com/htpasswd-generator/)
- [wtools](https://wtools.io/generate-htpasswd-online)
We create the user and password. Once created, it has this format:
ser:$apr1$x4gcjzrl$qSvcJK46C2rQUGRl4z1kl0
Once the user and password have been created, we proceed to access the adguard configuration file, AdGuardHome.yaml.
We look for the following line in the configuration file and replace the created data.
- For the
user: user - For the
password: $qSvcJK46C2rQUGRl4z1kl0
users:
- name: user
password: $apr1$x4gcjzrl$qSvcJK46C2rQUGRl4z1kl0
Once the data has been changed, restart adguard.
# List for Pihole ![]() and AdGuard Home
and AdGuard Home ![]()
## Main safelist
| List | Link | Description |
| :-- | :--: | :-- |
| safelist repository | [Link](https://raw.githubusercontent.com/JuanRodenas/Pi-hole_list/main/Listas/whitelist.txt) | safelist JuanRodenas |
| safelist hagezi | [Link](https://raw.githubusercontent.com/hagezi/dns-blocklists/main/whitelist.txt) | safelist hagezi (Not tested) |
## Main Black Lists
Column Link: Pi-hole® | Adguard Home®.
#### Host
| List Host | Link | Description |
| :-- | :--: | :-- |
| List oisd | [Link](https://dbl.oisd.nl) | [Link](https://abp.oisd.nl) | To Block host Adguard and domains [dbl.oisd](https://oisd.nl/) |
| The big list | [Link](https://big.oisd.nl/domains) | [Link](https://big.oisd.nl/) | The big list [oisd](https://oisd.nl/) |
| urlhaus-filter-domains | [Link](https://malware-filter.gitlab.io/malware-filter/urlhaus-filter-domains.txt) | [Link](https://malware-filter.gitlab.io/malware-filter/urlhaus-filter-agh.txt) | urlhaus-filter DEV [Link](https://gitlab.com/malware-filter/urlhaus-filter) |
| everything | [Link](https://blocklistproject.github.io/Lists/everything.txt) | [Link](https://raw.githubusercontent.com/blocklistproject/Lists/master/adguard/everything-ags.txt) | To Block everything |
| energized pro | [Link](https://energized.pro/unified/formats/hosts.txt) | [Link](https://block.energized.pro/ultimate/formats/hosts.txt) | To Block [energized](https://energized.pro/) |
| d3ward | [Link](https://raw.githubusercontent.com/d3ward/toolz/master/src/d3host.txt) | [Link](https://raw.githubusercontent.com/d3ward/toolz/master/src/d3host.adblock) | [d3ward](https://github.com/d3ward) popular list |
#### Malware / Shock / Porn / Adult
| List | Link | Description |
| :-- | :--: | :-- |
| The NSFW list | [Link](https://nsfw.oisd.nl/domains) | [Link](https://nsfw.oisd.nl/) | The NSFW list [oisd](https://oisd.nl/) |
| Gambling-porn | [Link](https://raw.githubusercontent.com/JuanRodenas/Pi-hole_list/main/List/Gambling.txt) | [Link](https://github.com/blocklistproject/Lists/blob/master/adguard/gambling-ags.txt) | To Block Gambling and porn |
| Malware | [Link](https://blocklistproject.github.io/Lists/malware.txt) | [Link](https://raw.githubusercontent.com/blocklistproject/Lists/master/adguard/malware-ags.txt) | To Block malware |
| Ransomware | [Link](https://raw.githubusercontent.com/blocklistproject/Lists/master/ransomware.txt) | [Link](https://raw.githubusercontent.com/blocklistproject/Lists/master/adguard/ransomware-ags.txt) | To Block ransomware |
| phishing | [Link](https://phishing.army/download/phishing_army_blocklist_extended.txt) | To Block phishing |
#### Tracking/Ads
| List Tracking/Ads | Link | Description |
| :-- | :--: | :-- |
| SmartTV | [Link](https://raw.githubusercontent.com/Perflyst/PiHoleBlocklist/master/SmartTV.txt) | [Link](https://raw.githubusercontent.com/blocklistproject/Lists/master/adguard/smart-tv-ags.txt) | To Block SmartTV |
| WindowsSpyBlocker | [Link](https://raw.githubusercontent.com/crazy-max/WindowsSpyBlocker/master/data/hosts/spy.txt) | To Block WindowsSpyBlocker |
| GoodbyeAds-Ultra | [Link](https://raw.githubusercontent.com/jerryn70/GoodbyeAds/master/Hosts/GoodbyeAds-Ultra.txt) | [Link](https://raw.githubusercontent.com/hagezi/dns-blocklists/main/adblock/pro.plus.txt) | To Block [hagezi](https://github.com/hagezi/dns-blocklists) and [jerryn70](https://github.com/jerryn70/GoodbyeAds) |
| ads-and-tracking-extended | [Link](https://www.github.developerdan.com/hosts/lists/ads-and-tracking-extended.txt) | To Block ads-and-tracking-extended |
| Adblock_Plus | [Link](https://raw.githubusercontent.com/notracking/hosts-blocklists/master/adblock/adblock.txt) | [Link](https://raw.githubusercontent.com/JuanRodenas/Pi-hole_list/main/List/Adblock_Plus_Ads.txt) | To Block Tracking AdBlock |
| Android tracking | [Link](https://github.com/JuanRodenas/Pihole_list/blob/main/Listas/android-tracking.txt) | Android tracking for AdGuard Home |
#### Adguard team filters
| List Tracking/Ads | Link | Description |
| :-- | :--: | :-- |
| AdGuardSDNSFilter | [Link](https://adguardteam.github.io/AdGuardSDNSFilter/Filters/filter.txt) | AdGuard team DNS filter |
| AdAway | [Link](https://adaway.org/hosts.txt) | AdAway default blocklist |
| Game Console Adblock List | [Link](https://raw.githubusercontent.com/DandelionSprout/adfilt/master/GameConsoleAdblockList.txt) | Game Console Adblock List |
| SmartTV-AGH | [Link](https://raw.githubusercontent.com/Perflyst/PiHoleBlocklist/master/SmartTV-AGH.txt) | Smart-TV Blocklist for AdGuard Home |
| Peter Lowe's List | [Link](https://pgl.yoyo.org/adservers/serverlist.php?hostformat=adblockplus&showintro=1&mimetype=plaintext) | Blocklist for use with Adblock Plus |
#### Services
| List Services | Link | Description |
| :-- | :--: | :-- |
| Youtube | [Link](https://raw.githubusercontent.com/blocklistproject/Lists/master/youtube.txt) | [Link](https://raw.githubusercontent.com/blocklistproject/Lists/master/adguard/youtube-ags.txt) | To Block youtube |
| Facebook | [Link](https://github.com/jmdugan/blocklists/blob/master/corporations/facebook/all) | To Block Facebook/Instagram/Whatsapp |
| Whatsapp open | [Link](https://raw.githubusercontent.com/jmdugan/blocklists/master/corporations/facebook/all-but-whatsapp) | To Block Facebook/Instagram but leave Whatsapp open |
| Google | [Link](https://raw.githubusercontent.com/jmdugan/blocklists/master/corporations/google/all) | To Block Google |
| Mozilla | [Link](https://raw.githubusercontent.com/JuanRodenas/Pi-hole_list/main/List/mozilla.txt) | [Link](https://raw.githubusercontent.com/JuanRodenas/Pi-hole_list/main/List/mozilla_adguard.txt) | To Block Mozilla tracking |
| Microsoft | [Link](https://raw.githubusercontent.com/jmdugan/blocklists/master/corporations/microsoft/all) | To Block Microsoft |
| VideoGamesAdiction | [Link](https://raw.githubusercontent.com/JuanRodenas/Pi-hole_list/main/List/VideoGamesAdiction.txt) | To Block VideoGames Adiction |
#### uBlock Origin uAssets
| List Services | Link | Link dev | Description |
| :-- | :--: | :--: | :-- |
| uBlock filters | [Link](https://raw.githubusercontent.com/uBlockOrigin/uAssets/master/filters/filters.txt) | [Link DEV](https://github.com/uBlockOrigin/uAssets/tree/master/filters) | uBlock filters |
| Badware risks | [Link](https://raw.githubusercontent.com/uBlockOrigin/uAssets/master/filters/badware.txt) | [Link DEV](https://github.com/uBlockOrigin/uAssets/tree/master/filters) | uBlock filters – Badware risks |
| Privacy | [Link](https://raw.githubusercontent.com/uBlockOrigin/uAssets/master/filters/privacy.txt) | [Link DEV](https://github.com/uBlockOrigin/uAssets/tree/master/filters) | uBlock filters – Privacy |
| Quick fixes list | [Link](https://raw.githubusercontent.com/uBlockOrigin/uAssets/master/filters/quick-fixes.txt) | [Link DEV](https://github.com/uBlockOrigin/uAssets/tree/master/filters) | Quick fixes list |
| Resource abuse | [Link](https://raw.githubusercontent.com/uBlockOrigin/uAssets/master/filters/resource-abuse.txt) | [Link DEV](https://github.com/uBlockOrigin/uAssets/tree/master/filters) | uBlock filters – Resource abuse |
| Unbreak | [Link](https://raw.githubusercontent.com/uBlockOrigin/uAssets/master/filters/unbreak.txt) | [Link DEV](https://github.com/uBlockOrigin/uAssets/tree/master/filters) | uBlock filters – Unbreak |
| i-dont-care-about-cookies | [Link](https://raw.githubusercontent.com/uBlockOrigin/uAssets/master/filters/unbreak.txt) | [Link DEV](https://www.i-dont-care-about-cookies.eu/) | i-dont-care-about-cookies |
| urlhaus-filter | [Link](https://malware-filter.gitlab.io/malware-filter/urlhaus-filter.txt) | [Link DEV](https://gitlab.com/malware-filter/urlhaus-filter) | urlhaus-filter |
A tab has been added for AdGuard with lists adapted to its format.
### Check your SelfHosted:
fivefilters:
Page to check your selfhosted from fivefilters
https://blockads.fivefilters.org/
d3ward:
Page to check your selfhosted from [d3ward](https://d3ward.github.io/toolz/)
https://d3ward.github.io/toolz/adblock.html
canyoublockit:
Page to check your selfhosted from canyoublockit
https://canyoublockit.com/
No more ads:
Page to check your selfhosted from No more ads
https://ads-blocker.com/es/pruebas/
AdBlock Tester:
Page to check your selfhosted from AdBlock Tester
https://adblock-tester.com/
### Check DoH, DoT and DDNSSEC:
1.1.1.1 de Cloudflare:
Page to check encryption of 1.1.1.1 de Cloudflare
https://1.1.1.1/help
Tenta VPN Browser:
Page to check encryption of Tenta VPN Browser
https://tenta.com/test/
Cloudflare:
Page to check encryption of Cloudflare
https://www.cloudflare.com/es-es/ssl/encrypted-sni/
#### The technologies analysed are:
1. Secure DNS: a technology that encrypts DNS queries and includes DNS-over-TLS and DNS-over-HTTPS.
2. DNSSEC: a technology designed to verify the authenticity of DNS queries.
3. TLS 1.3: the latest version of the TLS protocol that includes many improvements and closes security holes from previous versions.
4. Encrypted SNI: stands for Server Name Indication encryption that reveals the hostname during a TLS connection. This technology aims to ensure that only the IP address can be leaked.
The only browser that supports all four technologies is Firefox.
#### To activate the technologies, go to `about:config` and activate:
network.security.esni.enabled - pulsamos en el + y se ponga en true.
network.trr.mode – (valor 2)
network.trr.uri – valor en la web Mozilla.
HTTPS-Only Mode - pulsamos en el + y se ponga en true.
DNSSEC Resolver Test:
Page to check DNSSEC
http://dnssec.vs.uni-due.de/
http://www.dnssec-or-not.com/
http://en.conn.internet.nl/connection/
https://wander.science/projects/dns/dnssec-resolver-test/
Page to check DNSSEC encryption
https://rootcanary.org/test.html
DNS leak test:
Page to check DNS leakage
https://www.dnsleaktest.com/
## Applications for Android or iOS.
Link to the developer of the application: [](https://github.com/JGeek00 "view the source for all of our repositories.")
### Adguard Home® android application
### Adguard Home® iOS application

Any and all rights and responsibilities pertaining thereto remain the property of the respective developer.
## HELP ME 🙌
If you want to contribute to improve the lists, open a issue here: ISSUE
## Credits 🚀
This repository is made with all my love and affection.
#
[](https://github.com/AzagraMac "view the source for all of our repositories.")
[](https://github.com/JuanRodenas "view the source for all of our repositories.")
# :coffee: Donations
1K7bU83Lw1LxzN2dKWrLrWjA51HDpfyzWm
0x9C4e7853cB77F57EFd834F540Bc31F4f06562A11
DJfiHJGmJK6iCB8iugG879a4L6ixNHtYg1
LgWSf87Vfcz5yejVjZJWvSbi5WwBRaRsZg
# 🎉 ¡Ready!
These files/texts are provided "AS IS", without warranties of any kind, express or implied, including, but not limited to, warranties of merchantability, fitness for a particular purpose and non-infringement. In no event shall the authors or copyright holders be liable for any claims, damages or other liability arising out of or relating to the files or the use thereof.
Any and all trademarks are the property of their respective owners.
I will be updating with information and adding procedures in my spare time.