https://github.com/casdoor/casdoor-spring-security-example
Spring Security example app integrated with Casdoor
https://github.com/casdoor/casdoor-spring-security-example
auth authn casdoor iam oauth oidc spring spring-security spring-security-oauth2 sso
Last synced: 7 months ago
JSON representation
Spring Security example app integrated with Casdoor
- Host: GitHub
- URL: https://github.com/casdoor/casdoor-spring-security-example
- Owner: casdoor
- License: apache-2.0
- Created: 2022-09-02T03:16:23.000Z (about 3 years ago)
- Default Branch: master
- Last Pushed: 2023-12-20T13:55:55.000Z (almost 2 years ago)
- Last Synced: 2025-01-13T22:16:28.287Z (9 months ago)
- Topics: auth, authn, casdoor, iam, oauth, oidc, spring, spring-security, spring-security-oauth2, sso
- Language: Java
- Homepage: https://casdoor.org/docs/integration/spring-security/spring-security-oauth
- Size: 18.6 KB
- Stars: 0
- Watchers: 3
- Forks: 1
- Open Issues: 0
-
Metadata Files:
- Readme: README.md
- License: LICENSE
Awesome Lists containing this project
README
# casdoor-spring-security-example
This example shows how a Spring Security application can connect to Casdoor via OAuth 2.0.

## Deploy Casdoor
We assume you have deployed Casdoor in your own URL (refer to: [Server Installation](https://casdoor.org/docs/basic/server-installation)), in this example, we use the Casdoor demo site: https//door.casdoor.com
## Configuration
In the application edit page of your Casdoor (like: https://door.casdoor.com/applications/casbin/app-vue-python-example), you can get the `Client ID` and `Client secret` of the application. Remember to add your application's URL: `http://localhost:8080/` to Casdoor's "Redirect URLs":
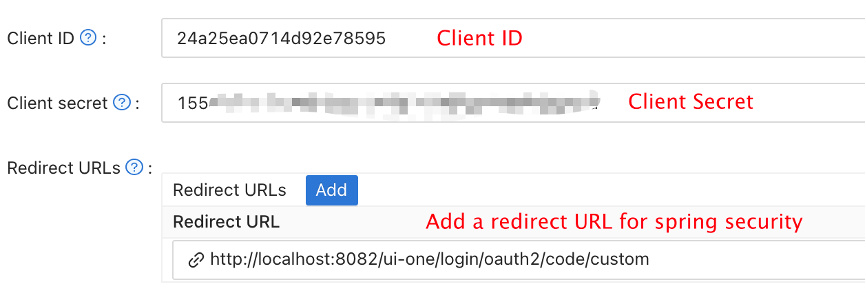
Open in a browser: https://door.casdoor.com/.well-known/openid-configuration, you will get the OIDC endpoints of Casdoor.
```json
{
"issuer": "https://door.casdoor.com",
"authorization_endpoint": "https://door.casdoor.com/login/oauth/authorize",
"token_endpoint": "https://door.casdoor.com/api/login/oauth/access_token",
"userinfo_endpoint": "https://door.casdoor.com/api/userinfo",
"jwks_uri": "https://door.casdoor.com/.well-known/jwks",
"introspection_endpoint": "https://door.casdoor.com/api/login/oauth/introspect",
"response_types_supported": [
"code",
"token",
"id_token",
"code token",
"code id_token",
"token id_token",
"code token id_token",
"none"
],
"response_modes_supported": [
"query",
"fragment",
"login",
"code",
"link"
],
"grant_types_supported": [
"password",
"authorization_code"
],
"subject_types_supported": [
"public"
],
"id_token_signing_alg_values_supported": [
"RS256"
],
"scopes_supported": [
"openid",
"email",
"profile",
"address",
"phone",
"offline_access"
],
"claims_supported": [
"iss",
...
],
"request_parameter_supported": true,
"request_object_signing_alg_values_supported": [
"HS256",
"HS384",
"HS512"
],
"end_session_endpoint": "https://door.casdoor.com/api/logout"
}
```
Replace the settings in this application's YAML file: [application.yml](https://github.com/casdoor/casdoor-spring-security-example/blob/master/src/main/resources/application.yml) with your own Casdoor's settings.
```yaml
spring:
security:
oauth2:
client:
registration:
casdoor:
client-id: 294b09fbc17f95daf2fe
client-secret: dd8982f7046ccba1bbd7851d5c1ece4e52bf039d
scope: read,write
authorization-grant-type: authorization_code
redirect-uri: http://localhost:8080/login/oauth2/code/custom
provider:
casdoor:
authorization-uri: https://door.casdoor.com/login/oauth/authorize
token-uri: https://door.casdoor.com/api/login/oauth/access_token
user-info-uri: https://door.casdoor.com/api/get-account
user-name-attribute: name
```
## Run the demo!
In the browser, visit: http://localhost:8080/foos. It will automatically redirect to Casdoor's login page. Login with username: `admin` and password: `123`.
If you visit your root page: http://localhost:8080, you will see:
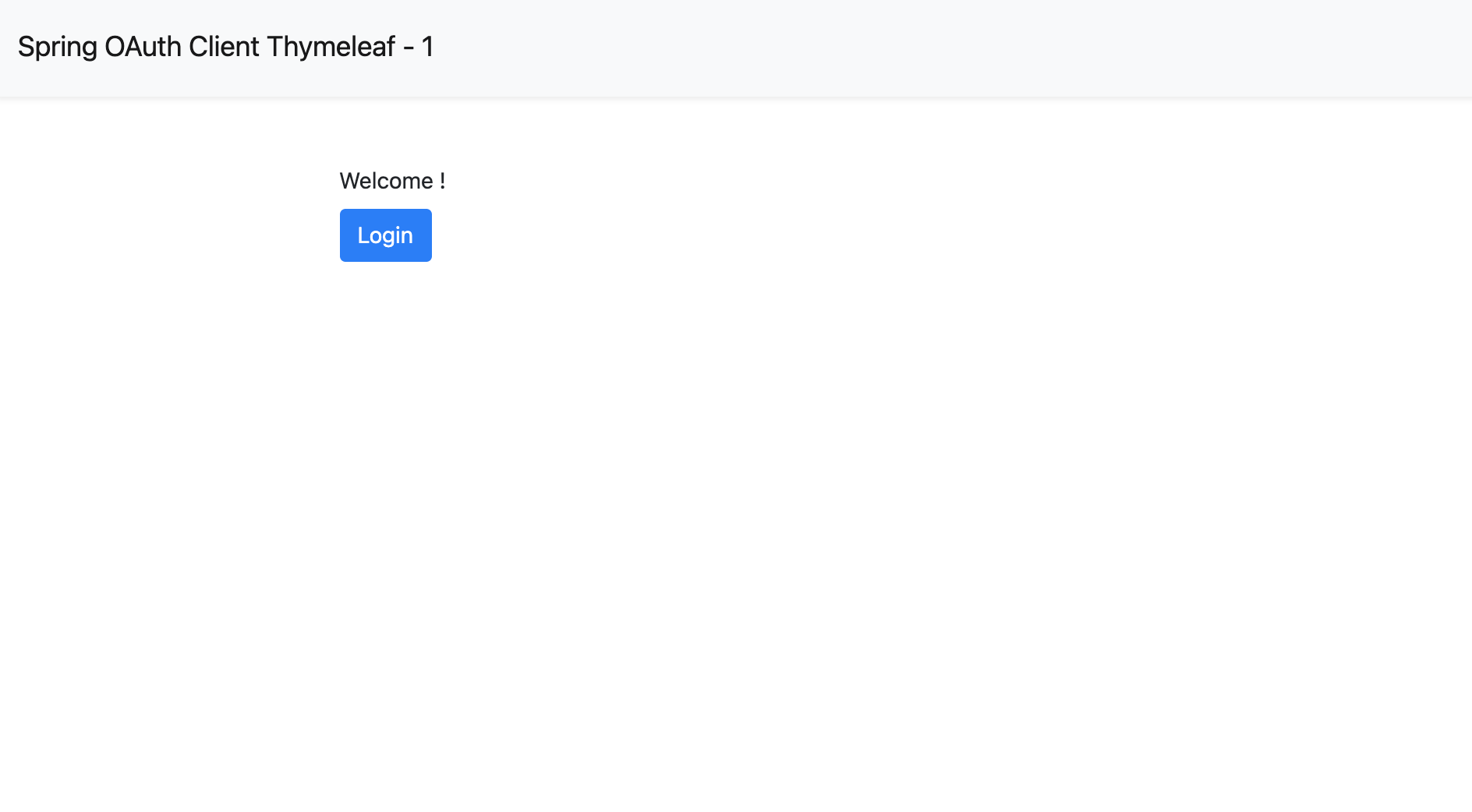
Click the `Login` button to redirect to Casdoor's login page.
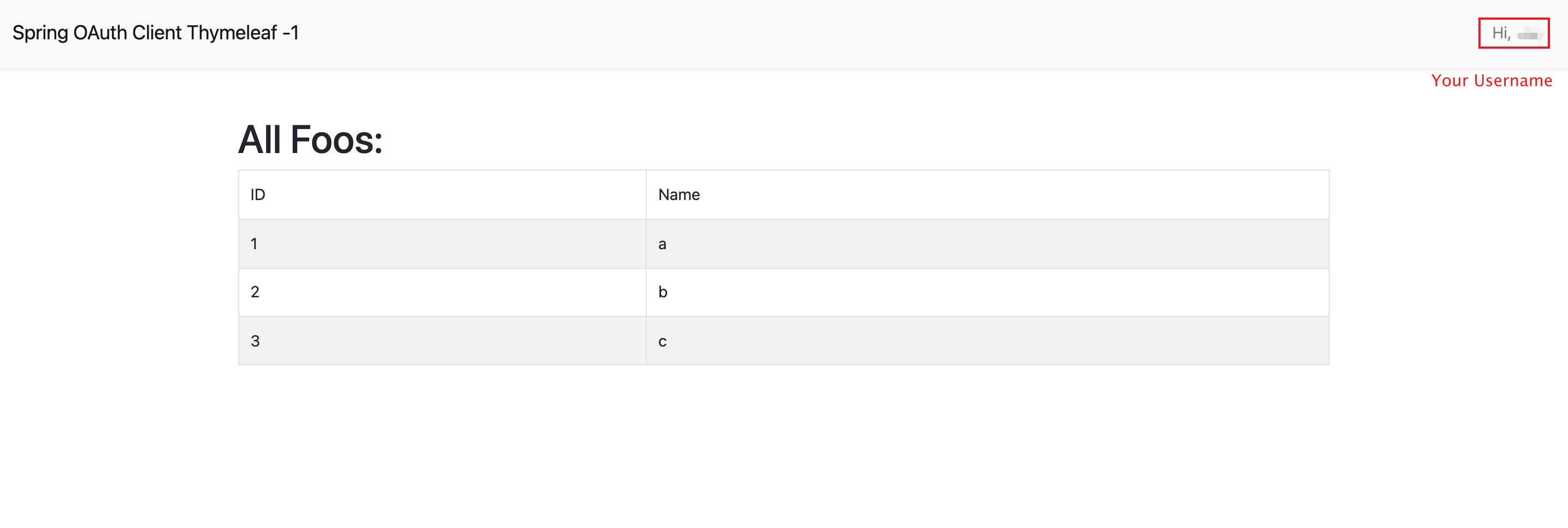
After you logged in, the page will redirect to `/foos`.
## How is this demo developed? (No need for actions)
1. Create a Spring Boot application in `SSOClientApplication`.
2. Add a configuration which protects all endpoints except `/` and `/login**` for users to login `UiSecurityConfiguration`.
3. Add a naive page for user to login in `resources/templates/index.html`. When user clicks the `login` button, he will be redirected to `casdoor`.
4. Define our protected resource. We can export an endpoint called `/foos` and a web page for display.