https://github.com/cr0hn/vulnerable-node
A very vulnerable web site written in NodeJS with the purpose of have a project with identified vulnerabilities to test the quality of security analyzers tools tools
https://github.com/cr0hn/vulnerable-node
analyzer common-vulnerabilities identified-vulnerabilities nodejs security-analyzers vulnerability whitebox
Last synced: 7 months ago
JSON representation
A very vulnerable web site written in NodeJS with the purpose of have a project with identified vulnerabilities to test the quality of security analyzers tools tools
- Host: GitHub
- URL: https://github.com/cr0hn/vulnerable-node
- Owner: cr0hn
- License: other
- Created: 2016-06-09T14:00:23.000Z (over 9 years ago)
- Default Branch: master
- Last Pushed: 2024-08-20T15:34:11.000Z (over 1 year ago)
- Last Synced: 2025-04-08T16:05:22.330Z (9 months ago)
- Topics: analyzer, common-vulnerabilities, identified-vulnerabilities, nodejs, security-analyzers, vulnerability, whitebox
- Language: JavaScript
- Homepage:
- Size: 1.2 MB
- Stars: 464
- Watchers: 16
- Forks: 694
- Open Issues: 11
-
Metadata Files:
- Readme: README.md
- Funding: .github/FUNDING.yml
- License: LICENSE
Awesome Lists containing this project
- awesome-cyber-skills - Vulnerable Node
- awesome-mobile-CTF - Vulnerable-node
- awesome-dva - NodeVulnerable
README
Vulnerable Node
===============

*Vulnerable Node: A very vulnerable web site written in NodeJS*
Codename | PsEA
-------- | ----
Version | 1.0
Code | https://github.com/cr0hn/vulnerable-node
Issues | https://github.com/cr0hn/vulnerable-node/issues/
Author | Daniel Garcia (cr0hn) - @ggdaniel
# Support this project
Support this project (to solve issues, new features...) by applying the Github "Sponsor" button.
# What's this project?
The goal of this project is to be a project with really vulnerable code in NodeJS, not simulated.
## Why?
Similar project, like OWASP Node Goat, are pretty and useful for learning process but not for a real researcher or studding vulnerabilities in source code, because their code is not really vulnerable but simulated.
This project was created with the **purpose of have a project with identified vulnerabilities in source code with the finality of can measure the quality of security analyzers tools**.
Although not its main objective, this project also can be useful for:
- Pentesting training.
- Teaching: learn how NOT programming in NodeJS.
The purpose of project is to provide a real app to test the quality of security source code analyzers in white box processing.
## How?
This project simulates a real (and very little) shop site that has identifiable sources points of common vulnerabilities.
## Installation
The most simple way to run the project is using docker-compose, doing this:
```bash
# git clone https://github.com/cr0hn/vulnerable-node.git vulnerable-node
# cd vulnerable-node/
# docker-compose build && docker-compose up
Building postgres_db
Step 1 : FROM library/postgres
---> 247a11721cbd
Step 2 : MAINTAINER "Daniel Garcia aka (cr0hn)"
---> Using cache
---> d67c05e9e2d5
Step 3 : ADD init.sql /docker-entrypoint-initdb.d/
....
```
## Running
Once docker compose was finished, we can open a browser and type the URL: `127.0.0.1:3000` (or the IP where you deployed the project):
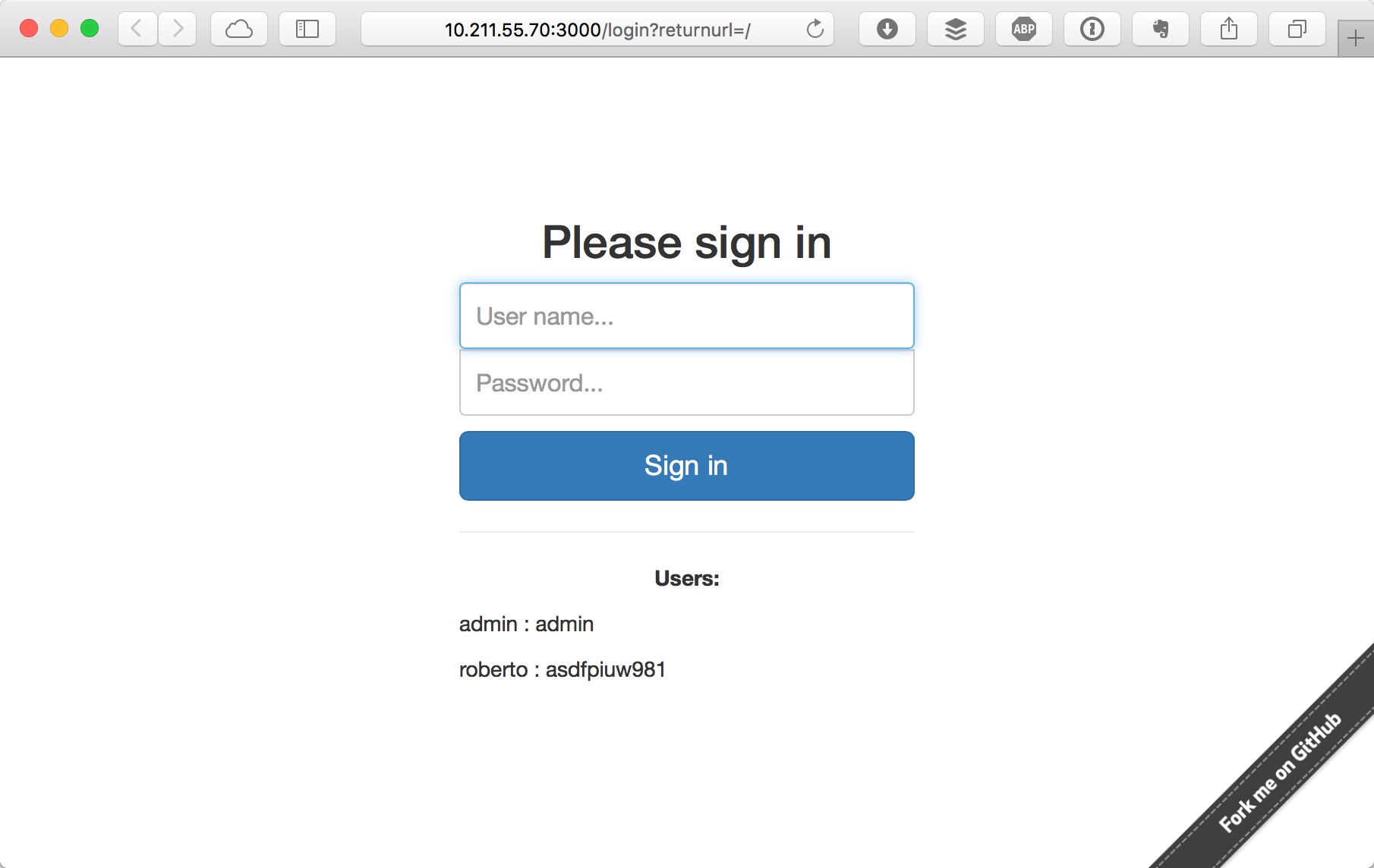
To access to website you can use displayed in landing page:
- admin : admin
- roberto : asdfpiuw981
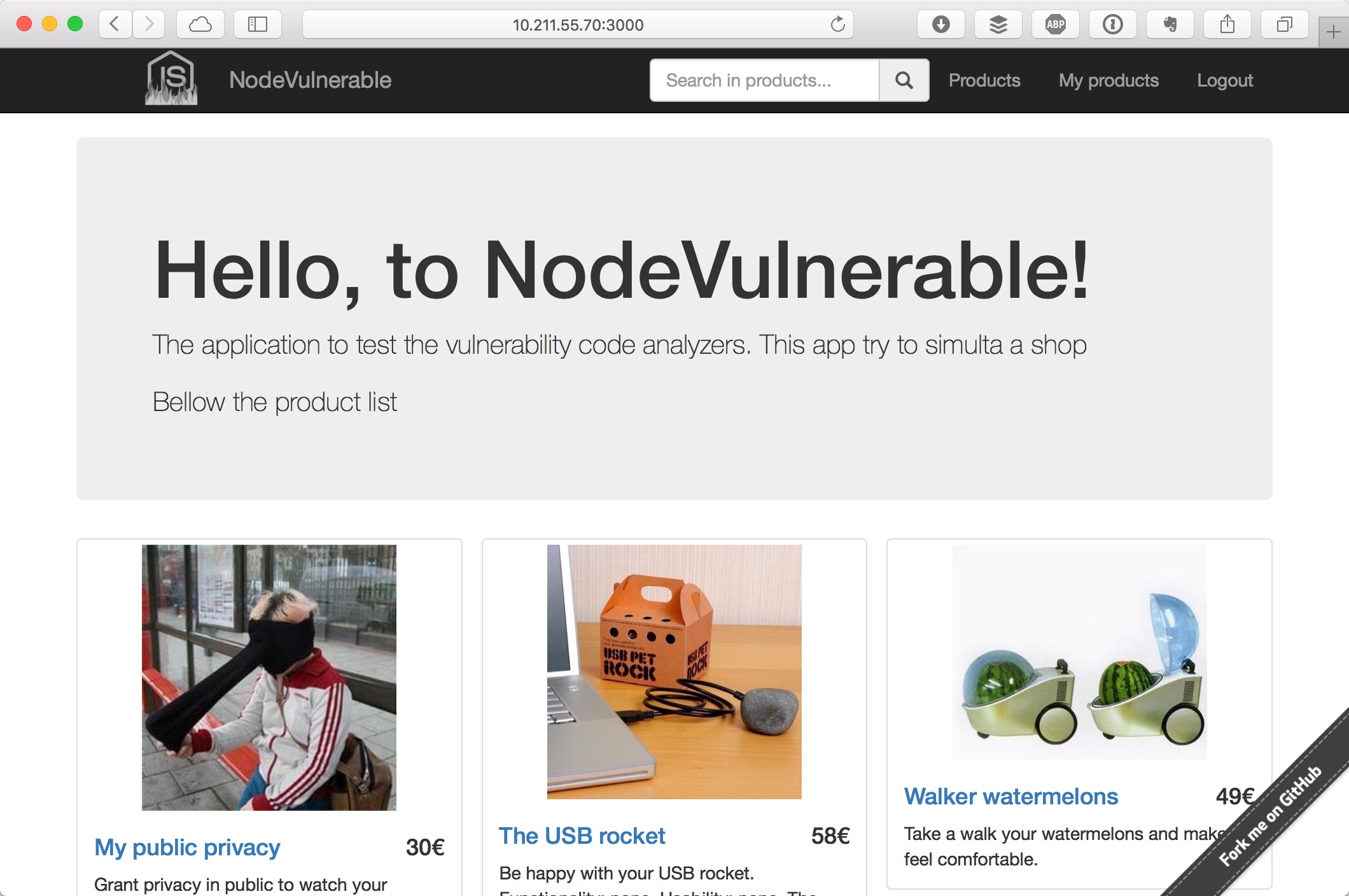
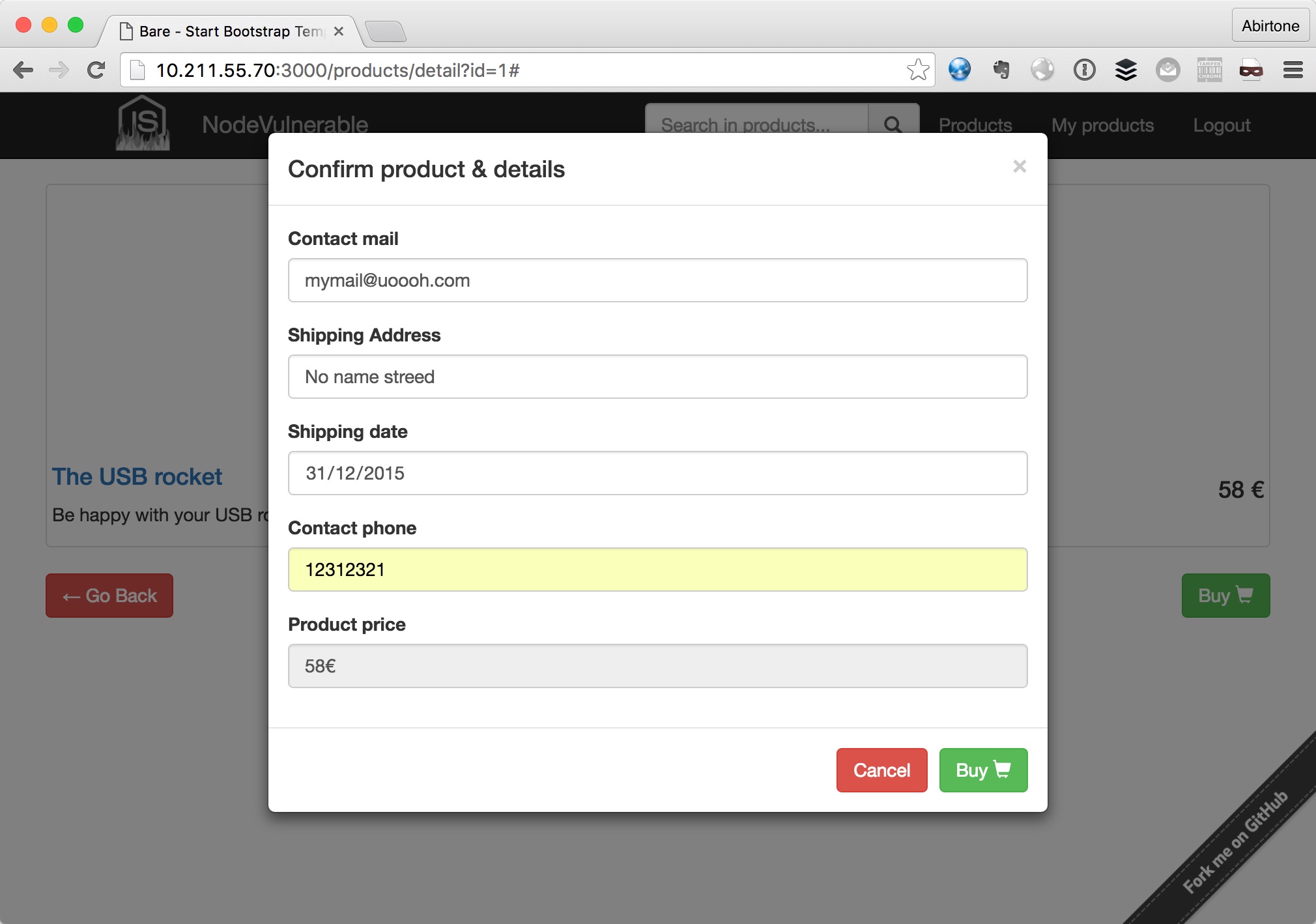
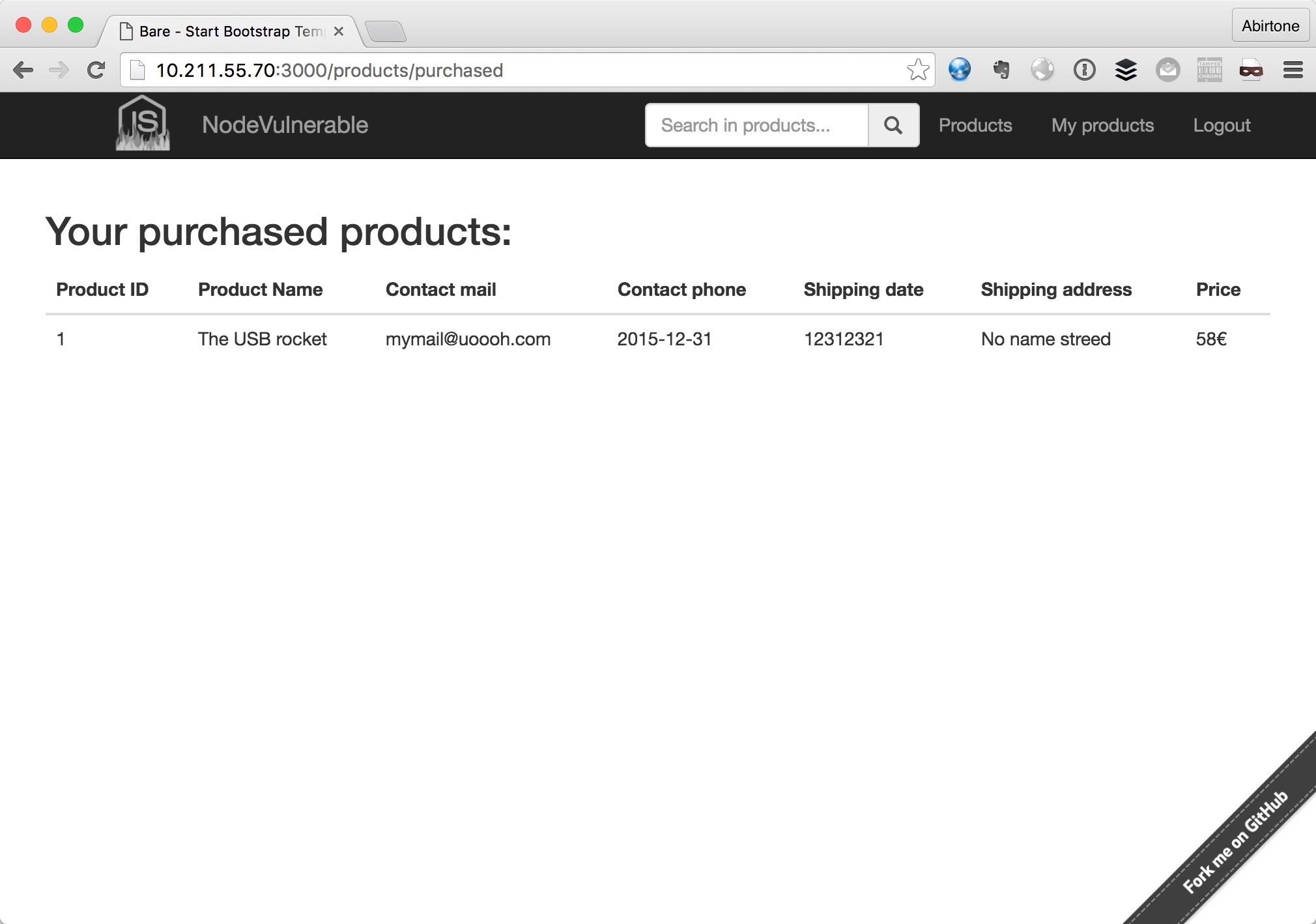
Here some images of site:
# Vulnerabilities
## Vulnerability list:
This project has the most common vulnerabilities of `OWASP Top 10 `:
- A1 - Injection
- A2 - Broken Authentication and Session Management
- A3 - Cross-Site Scripting (XSS)
- A4 - Insecure Direct Object References
- A5 - Security Misconfiguration
- A6 - Sensitive Data Exposure
- A8 - Cross-Site Request Forgery (CSRF)
- A10 - Unvalidated Redirects and Forwards
## Vulnerability code location
The exactly code location of each vulnerability is pending to write
# References
I took ideas and how to explode it in NodeJS using these references:
- https://blog.risingstack.com/node-js-security-checklist/
- https://github.com/substack/safe-regex
# License
This project is released under license BSD.