https://github.com/devanshbatham/CertEagle
Weaponizing Live CT logs for automated monitoring of assets
https://github.com/devanshbatham/CertEagle
asset-monitoring bughunting cybersecurity osint reconnaissance ssl-certificates subdomain-enumeration subdomain-finder subdomain-monitor
Last synced: 8 months ago
JSON representation
Weaponizing Live CT logs for automated monitoring of assets
- Host: GitHub
- URL: https://github.com/devanshbatham/CertEagle
- Owner: devanshbatham
- Created: 2020-08-10T08:07:40.000Z (over 5 years ago)
- Default Branch: master
- Last Pushed: 2021-09-12T17:39:23.000Z (about 4 years ago)
- Last Synced: 2025-03-28T19:21:22.337Z (9 months ago)
- Topics: asset-monitoring, bughunting, cybersecurity, osint, reconnaissance, ssl-certificates, subdomain-enumeration, subdomain-finder, subdomain-monitor
- Language: Python
- Homepage:
- Size: 320 KB
- Stars: 133
- Watchers: 8
- Forks: 36
- Open Issues: 1
-
Metadata Files:
- Readme: readme.md
Awesome Lists containing this project
- awesome-hacking-lists - devanshbatham/CertEagle - Weaponizing Live CT logs for automated monitoring of assets (Python)
README
## CertEagle - Asset monitoring utility using real time CT log feeds
### Detailed Description about this can be found here :
Read Blog here : https://medium.com/@Asm0d3us/weaponizing-live-ct-logs-for-automated-monitoring-of-assets-39c6973177c7
### Introduction
In Bugbounties “**If you are not first , then you are last**” there is no such thing as silver or a bronze medal , Recon plays a very crucial part and if you can detect/Identify a newly added asset earlier than others then the chances of you Finding/Reporting a security flaw on that asset and getting rewarded for the same are higher than others.
Personally I am monitoring CT logs for domains/subdomains for quite a long time now and it gave me a lot of successful results , The inspiration behind this was “[Sublert : By yassineaboukir](https://github.com/yassineaboukir/sublert/)” which checks crt.sh for subdomains and can be executed periodically , However I am using somewhat different approach and instead of looking into crt.sh periodically, I am extracting domains from Live CT log feeds , So chances of me finding a new asset earlier is higher as compared to others.
### Workflow
- Monitoring Real Time CT log feed and extracting the domain names from that feed
- Matching the extracted subdomains/domains against the domains/Keywords to be matched
- Sending a Slack notification if a domain name matches
#### Requirements :
- A VPS (UNIX up and running)
- Python 3x (Tested with Python 3.6.9)
- Slack Workspace (optional)
### Setup
I am assuming that you have already done with your setup of slack workspace .
Now Create a channel named “subdomain-monitor” and set up a incoming webhook
#### Enabling Slack Notifications :
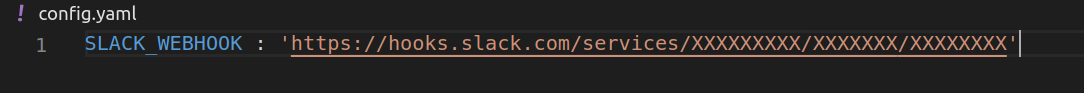
Edit `config.yaml` file and paste your slack webhook URL there , It should look something like this
#### Keywords and domains to match :
You can specify keywords and domains to match in `domains.yaml` file , You can specify names
**For Matching subdomains :**
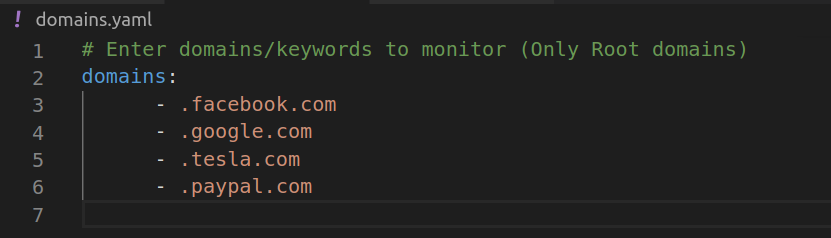
Note : Notice that preceding dot [ . ]
Lets take “.facebook.com” as example , domains extracted from Real time CT logs will be matched against the word “.facebook.com” , if matched they will be logged in our output file (found-domains.log) . The thing to note here is , It will give some false positives like “test.facebook.com.test.com” , “example.facebook.company” but we can filter out them later on by using use regex magic
#### For Matching domains/subdomains with specific keywords :
Lets assume that you want to monitor and log domains/subdomains that are having word “hackerone” in them , then our domains.yaml file will look something like this
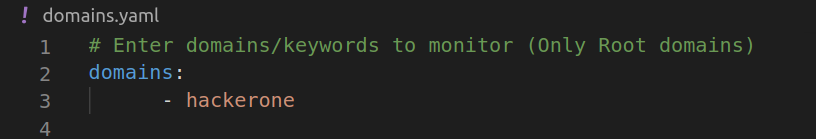
Now all the extracted domains/subdomains that are having word “hackerone” in them will be matched and logged (and a slack notification will be sent to you for the same)
Okay we are done with our initial setup , Lets install the required dependencies and run our tool
`$ pip3 install -r requirements.txt`
`$ python3 certeagle.py`
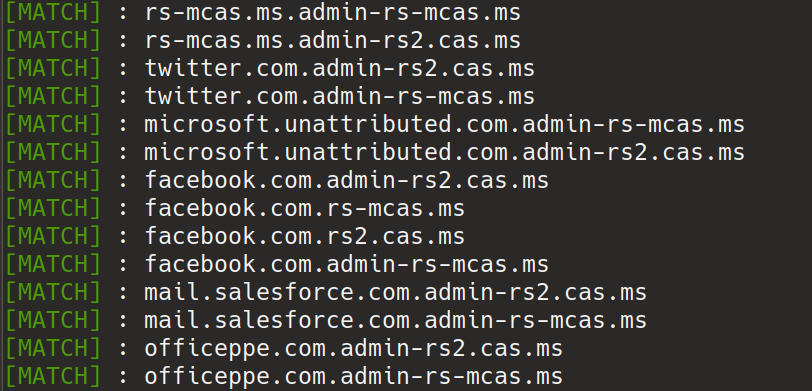
**Matched domains will look like this :**
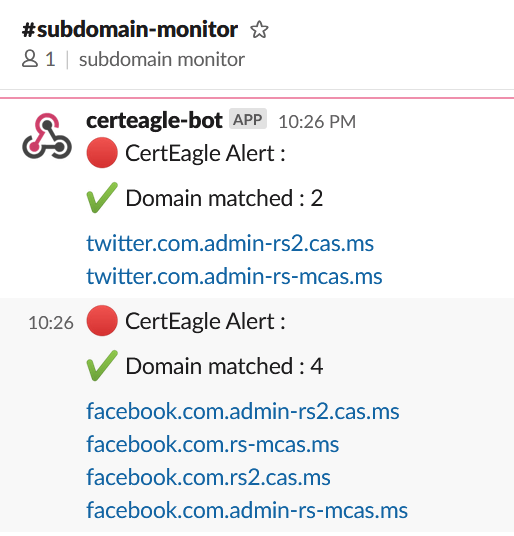
**Slack Notifications will look like this :**
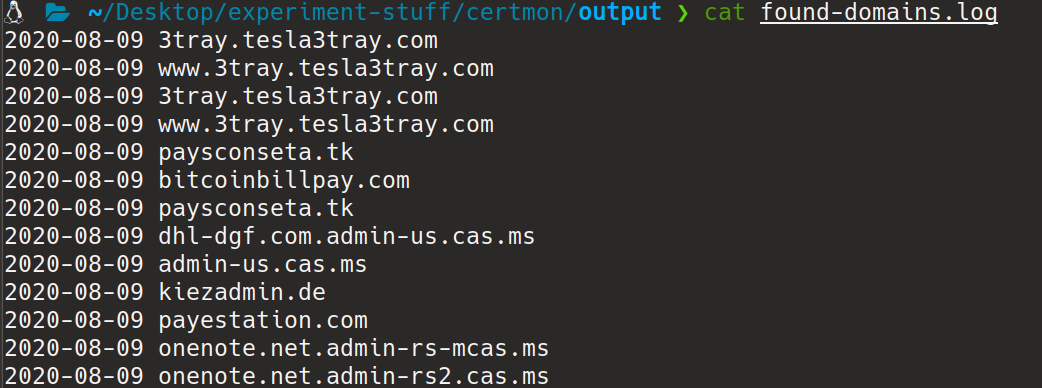
**Output files :**
The program will keep on running all the matched domains will be saved under output directory in found-domains.log file
**Strict Warning : Do not monitor assets of any organisation without prior consent**
### Inspiration
[Sublert](https://github.com/yassineaboukir/sublert/)
[Phishing Catcher](https://github.com/x0rz/phishing_catcher)
### Contact
Shoot my DM : [@0xAsm0d3us](https://twitter.com/0xAsm0d3us)
## __Want to support my work?__
If you think my work has added some value to your existing knowledge, then you can [Buy me a Coffee here](https://www.buymeacoffee.com/Asm0d3us) (and who doesn't loves a good cup of coffee?')
[](https://www.buymeacoffee.com/Asm0d3us)