https://github.com/elcuervo/tangalanga
Tangalanga: the Zoom conference scanner hacking tool
https://github.com/elcuervo/tangalanga
hacking hacking-tool reversing zoom
Last synced: 7 months ago
JSON representation
Tangalanga: the Zoom conference scanner hacking tool
- Host: GitHub
- URL: https://github.com/elcuervo/tangalanga
- Owner: elcuervo
- License: gpl-3.0
- Created: 2020-05-28T03:33:50.000Z (over 5 years ago)
- Default Branch: master
- Last Pushed: 2020-10-20T21:25:19.000Z (about 5 years ago)
- Last Synced: 2025-03-24T08:26:39.913Z (7 months ago)
- Topics: hacking, hacking-tool, reversing, zoom
- Language: Go
- Homepage:
- Size: 94.7 KB
- Stars: 288
- Watchers: 22
- Forks: 42
- Open Issues: 6
-
Metadata Files:
- Readme: README.md
- License: LICENSE
Awesome Lists containing this project
README
# Tangalanga
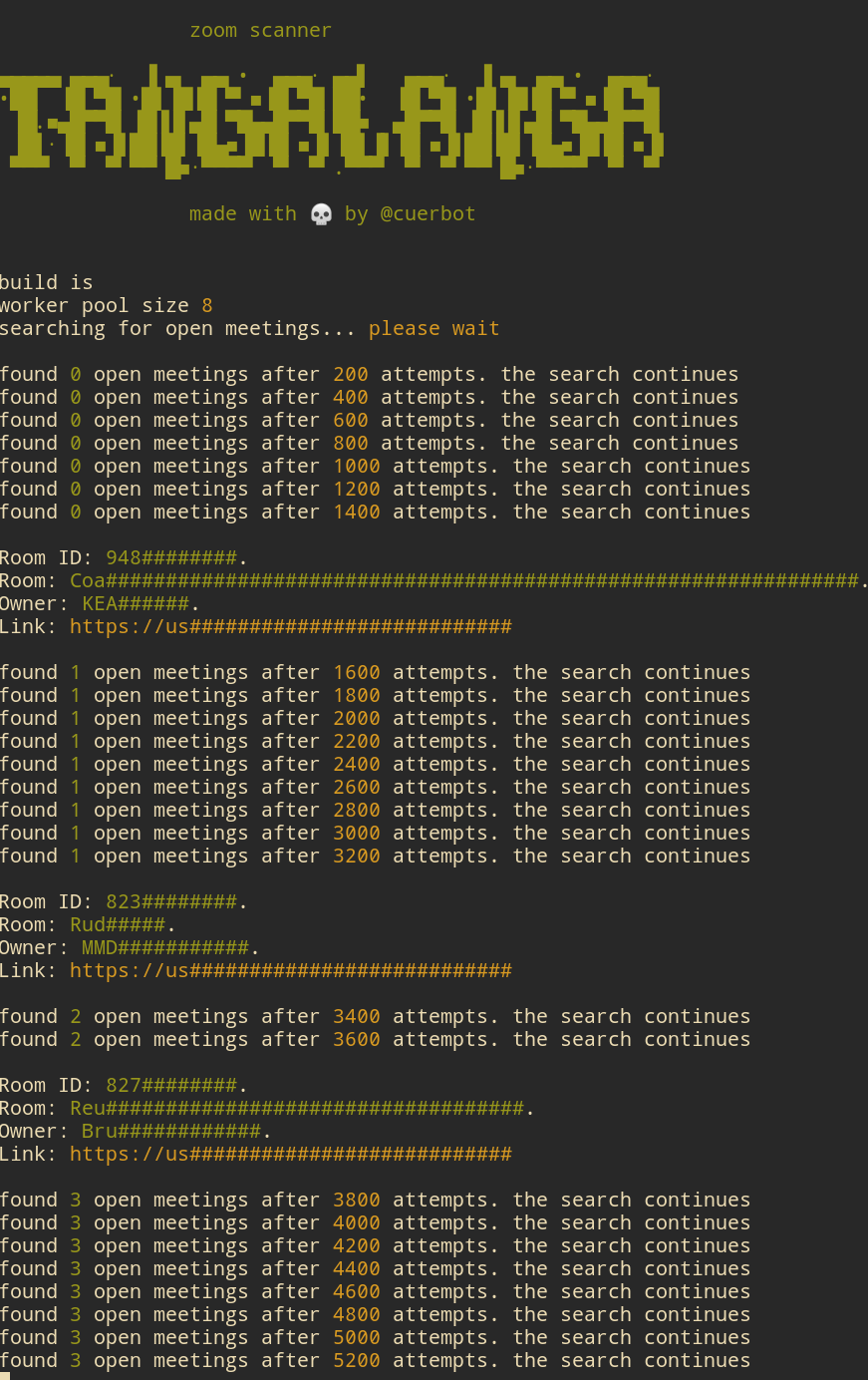
Zoom Conference scanner.
This scanner will check for a random meeting id and return information if available.
## Install
First try to see if there's any prebaked version for the date: https://github.com/elcuervo/tangalanga/releases.
This versions already have a token ready to use.
Either way you can find the Windows, Linux and Mac version on Releases https://github.com/elcuervo/tangalanga/releases.
Download, uncompress and enjoy.
## Usage
This are all the possible flags:
```bash
tangalanga \
-token=user-token \ # [default: env TOKEN] user token to use.
-colors=false \ # [default: true] enable/disable colors
-censor=true \ # [default: false] censors output
-output=history \ # [default: stdout] write found meetings to file
-debug=true \ # [default: false] show all the attmpts
-tor=true \ # [default: false] enable tor connection (will use default socks proxy)
-hidden=true \ # [default: false] enable embedded tor connection (only linux)
-rate=7 \ # [default: ncpu] overwrite the default worker pool
-proxy=socks5://... \ # [default: socks5://127.0.0.1:9150] proxy url to use
```
## Tokens
Unfortunately I couldn't find the way the tokens are being generated but the core concept is that
the `zpk` cookie key is being sent during a Join will be usable for ~24 hours before expiring. This
makes trivial to join several known meetings, gether some tokens and then use them for the scans.
Tokens can be sniffed after a join attempt to a meeting.
This means that to "fish" a token you'll need a setup that can sniff traffic and also spoof
certificates.
Using Wireshark, Charles or any other of the ssl-proxying-capable tools out there will do the trick.
## TOR (only linux)
Tangalanga has a tor runtime embedded so it can connect to the onion network and run the queries
there instead of exposing your own ip.
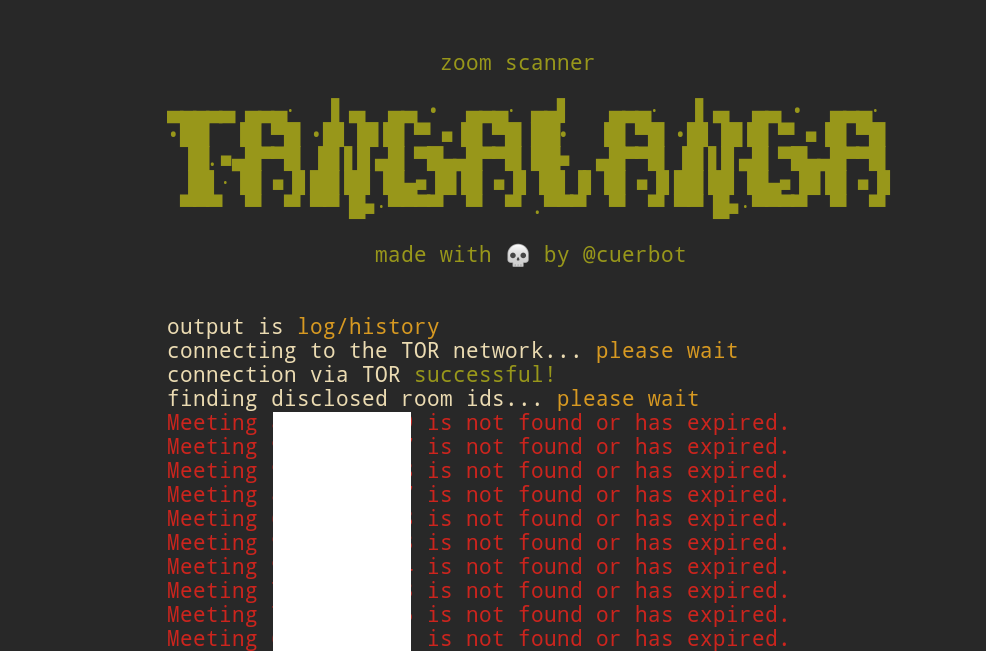
For any other system I recommend a VPN
## Why the bizarre name?
This makes reference to a famous 80s/90s personality in the Rio de la Plata. [Doctor Tangalanga](https://en.wikipedia.org/wiki/Dr._Tangalanga)
who loved to do phone pranks.