Ecosyste.ms: Awesome
An open API service indexing awesome lists of open source software.
https://github.com/excalibra/scripts
Platform: Windows/Mac/Linux. Scripting: Various, no restrictions; customized as needed. Tasks: Desktop checks, software cracking, AV evasion, privilege execution, firmware read/write, password checks, Wi-Fi scans, cloud security, log analysis, NLP, and data analysis in humanities/social sciences.
https://github.com/excalibra/scripts
automation ban-ip clawer linux macos security spiders update wi-fi windows
Last synced: about 1 month ago
JSON representation
Platform: Windows/Mac/Linux. Scripting: Various, no restrictions; customized as needed. Tasks: Desktop checks, software cracking, AV evasion, privilege execution, firmware read/write, password checks, Wi-Fi scans, cloud security, log analysis, NLP, and data analysis in humanities/social sciences.
- Host: GitHub
- URL: https://github.com/excalibra/scripts
- Owner: Excalibra
- Created: 2024-11-15T00:02:01.000Z (about 2 months ago)
- Default Branch: main
- Last Pushed: 2024-11-19T04:15:24.000Z (about 1 month ago)
- Last Synced: 2024-11-19T05:21:07.009Z (about 1 month ago)
- Topics: automation, ban-ip, clawer, linux, macos, security, spiders, update, wi-fi, windows
- Language: Jupyter Notebook
- Homepage: https://github.com/Excalibra/scripts/
- Size: 305 KB
- Stars: 0
- Watchers: 1
- Forks: 0
- Open Issues: 0
-
Metadata Files:
- Readme: README.md
Awesome Lists containing this project
README
## Disclaimer: All content is for informational research, learning, and exchange purposes only, to be used in a lawful and compliant manner. Thank you.
## Introduction
The project involves interdisciplinary applications and analysis of information: desktop baseline checks, software activation/cracking, antivirus evasion and privilege escalation, firmware identification and read/write for penetration support, host account null password detection, Wi-Fi password scanning, cloud host security hardening, host system log analysis, natural language processing, and data analysis in humanities and social sciences.
* **System Platforms**: Windows/Mac/Linux; **Scripting Languages**: Multiple, flexible; customized as needed.
* **Research Focus**: Basic information automation, cloud host/local desktop security processing, social science information technology, and data analysis.
The project code involves component version compatibility issues. Click here for more details; regarding the inability to preview ipynb on GitHub, [please refer here](https://blog.reviewnb.com/jupyter-notebook-not-rendering-on-github/); to generate automated information processing reports, check the [d-xlsx](./d-xlsx) directory for more details.
## Analysis of Common Platform Hot Searches and Rumor Refutation
This section involves interdisciplinary and basic research of humanities and social science journals and paper research subjects (including colleague interviews, online forum surveys, etc.).
* HTML web page parsing, web UI automation
* Data collection, filtering, classification, and archiving
* Basic mathematical statistics of "averages/extremes," word segmentation, sentiment value calculation and summary (natural language processing)
Basic operations when first starting, simple information collection test.
One-click access to China News information Text version
python3 -c "$(curl -fsSL https://ghproxy.com/https://raw.githubusercontent.com/hoochanlon/scripts/main/d-python/get_chinanews.py)"
One-click access to China News information in Ruby
ruby -e "$(curl -fsSL https://ghproxy.com/https://raw.githubusercontent.com/hoochanlon/scripts/main/d-ruby/get_chinanews.rb)"
One-click generate global information reports Text version
python3 -c "$(curl -fsSL https://ghproxy.com/https://raw.githubusercontent.com/hoochanlon/scripts/main/d-python/get_worldometers.py)"
One-click collect the top five answers from Zhihu
python3 -c "$(curl -fsSL https://raw.githubusercontent.com/hoochanlon/scripts/main/d-python/zhihu_answers_demo.py)"
Collect 90 job posts and salary details from Boss Zhipin Text version
python3 -c "$(curl -fsSL https://ghproxy.com/https://raw.githubusercontent.com/hoochanlon/scripts/main/d-python/zhipin_demo.py)"
Platform Hot Search and Rumor Refutation Summary and Analysis
Prerequisite: Before starting, first copy and run the following command to install the pip package. Data involving Stanford University’s language model [stanza](https://stanfordnlp.github.io/stanza) requires an external network connection.
pip3 install --no-cache-dir -r https://ghproxy.com/https://raw.githubusercontent.com/hoochanlon/scripts/main/d-txt/requirements.txt
Hot Search Collection and Analysis for Toutiao, Douyin, Weibo
One-click collect today’s hot searches from Toutiao, Douyin, and Weibo. Text version (NLP: Stanza)
python3 -c "$(curl -fsSL https://ghproxy.com/https://raw.githubusercontent.com/hoochanlon/scripts/main/d-python/get_resou_today_s.py)"
- Automated categorization; overall match rate: 84%~96% range.
- Word frequency statistics; hot searches common across all three platforms indicate lasting public interest, with higher information density.
- Sentiment average, sentiment value for each headline; main focus: the intensity of sentiment for manually pinned hot searches.
- Part-of-speech analysis; highlights words likely to have guiding or implanted awareness components, such as excessive use of attributive and adverbial phrases, which are often promotional in nature.
Weibo has the most noise in automated categorization, with low informational value, large amounts of superficial content, and higher distortion. The hot search headlines across platforms also have unmarked rumor components, so it's best to use the National Rumor Refutation Platform for verification. Despite its heavy entertainment focus, Weibo's social media model allows rapid dissemination of information when social events trend, sparking public attention and discussion.
Recommended Papers:
- He Qi Mao, "The News Reading Service Function of Weibo Hot Search under the Big Data Background," Master's thesis in Journalism, Jilin University, March 2017.
- Guoming Yu, "The Overall Situation and Structural Characteristics of Public Opinion in China under Big Data Analysis," Journal of Renmin University of China, Issue 5, 2013.
- Xiaoxin Wang, "The Reading Tendencies of Audiences for Online News in China — Taking Baidu Hot Search Terms as an Example," "Today Media," Issue 9, 2013.
- Nuo Xu, "Research on the 5W Extraction of Social Risk Events Based on Baidu Hot Search News Terms," "Systems Engineering Theory and Practice," Volume 40, Issue 2, 2022.
Automated Collection of Rumor Refutation Items and Language Analysis
The function is generally similar to the previous example, performing grammatical analysis on high-frequency words. (NLP: ThuLAC)
python3 -c "$(curl -fsSL https://ghproxy.com/https://raw.githubusercontent.com/hoochanlon/scripts/main/d-python/get_rumor_analysis.py)"
urllib3: https://github.com/urllib3/urllib3/issues/3020#issuecomment-1557412175
Definition of rumors: Gordom W. Allport and Leo Postman first defined rumors as propositions related to current events, circulated between people through oral media, lacking specific evidence to verify their accuracy. 1
Concept of rumors: Essentially, rumors generally have two attributes: widespread dissemination and uncertainty. Based on this, this paper defines rumors as information that is widely spread and carries a high degree of uncertainty. "Uncertainty" mainly refers to the uncertainty about the truth of the information. 2
Currently, among various rumors during emergencies, there are relatively few with clear malicious intent or with goals such as achieving political, economic, or other interests. Most rumors are formed out of fear and based on erroneous judgments. (Hu Qi, 2022) From the collected rumors analysis, the two largest categories are social topics and healthy eating, accounting for 48% and 43%, respectively.
However, the blending of multiculturalism and fragmented interpretations in the "post-truth" era has intensified the value divergence among the public, eroding the trust foundation. On one hand, the complex interests, diverse social ideologies, and various modes of communication intersect to create a diverse network culture in the "post-truth" era, increasing collisions and friction between mainstream and non-mainstream cultures. While non-mainstream cultures can be a beneficial supplement to mainstream culture, negative elements like "Buddhism culture," "internet celebrity culture," and "lying flat culture" often deviate from mainstream culture, especially distorting aesthetics and promoting money worship, which can mislead audiences with limited knowledge and experience, leading to political biases and eroding existing political trust. On the other hand, in the "post-truth" era, faced with an overwhelming amount of information, people tend to piece together facts and interpret the truth in fragmented ways. Once it concerns complex political rumors about social divisions, interest distribution, political corruption, and policy failures, people easily fall into continuously interpreting and reconstructing fragmented information, creating multiple "truths" that further ferment, thus causing frequent doubts about established political consensus, resulting in the loss of political trust and providing opportunities for the spread of rumors. 3
Referring to Yang Yunyi and Zhao Xiqun, personal life mostly involves money matters such as food, clothing, housing, and transportation, and social division is a normal phenomenon. The differences between "individual-collective" and "collective-individual" are primarily centered on national construction. The following two pieces of information are worth researching:
- Zhihu - How to view CCTV's new video "Only by working hard can one feel at ease, it’s the life belief of countless ordinary people"?
- Bilibili - They say I touch, they say I pose, who cares about the helplessness of workers?
References
[1] Hu Qi, "Psychological Mechanisms and Governance Paths of Online Rumors in the Era of Omnimedia," P135, 137, [J] Social Scientist, 2022(11)
[2] Lei Xia, "Cognitive Dissonance and Correction Mechanism of Rumors in Elderly Groups," [J] Modern Communication, 2023(3)
[3] Yang Yunyi, Zhao Xiqun, "Representation, Attribution, and Governance of Political Rumors in the 'Post-Truth' Era," P155, [J] Journal of Hunan University of Science and Technology (Social Science Edition), 2022(11)
## Bilibili User Comments and Danmaku Research
The script features include:
1. Video title, author, release date, views, favorites, shares, accumulated Danmaku, comment count, video description, video category, video link, cover image link.
1. 100 Danmaku, sentiment values, part-of-speech analysis, publication time, user ID.
1. 20 popular comments, like count, sentiment values, topic reply entries, member ID, member name, comment time.
1. Enhanced functionality: Danmaku: username, birthday, registration date, followers count, following count (cookie); Comments: display the IP location of the comment user (webbui).
1. Finally generate an xlsx file with median sentiment value, word frequency statistics, word cloud, bar chart.
Click for details
Prerequisite: Ensure that your basic library components are complete.
pip3 install --no-cache-dir -r https://ghproxy.com/https://raw.githubusercontent.com/hoochanlon/scripts/main/d-txt/requirements.txt
Then run the script Text version
python3 -c "$(curl -fsSL https://ghproxy.com/https://raw.githubusercontent.com/hoochanlon/scripts/main/d-python/get_bv_baseinfo.py)"
Basic Text Analysis
Stopword text clustering comprehensive statistical analysis, see the image below 1
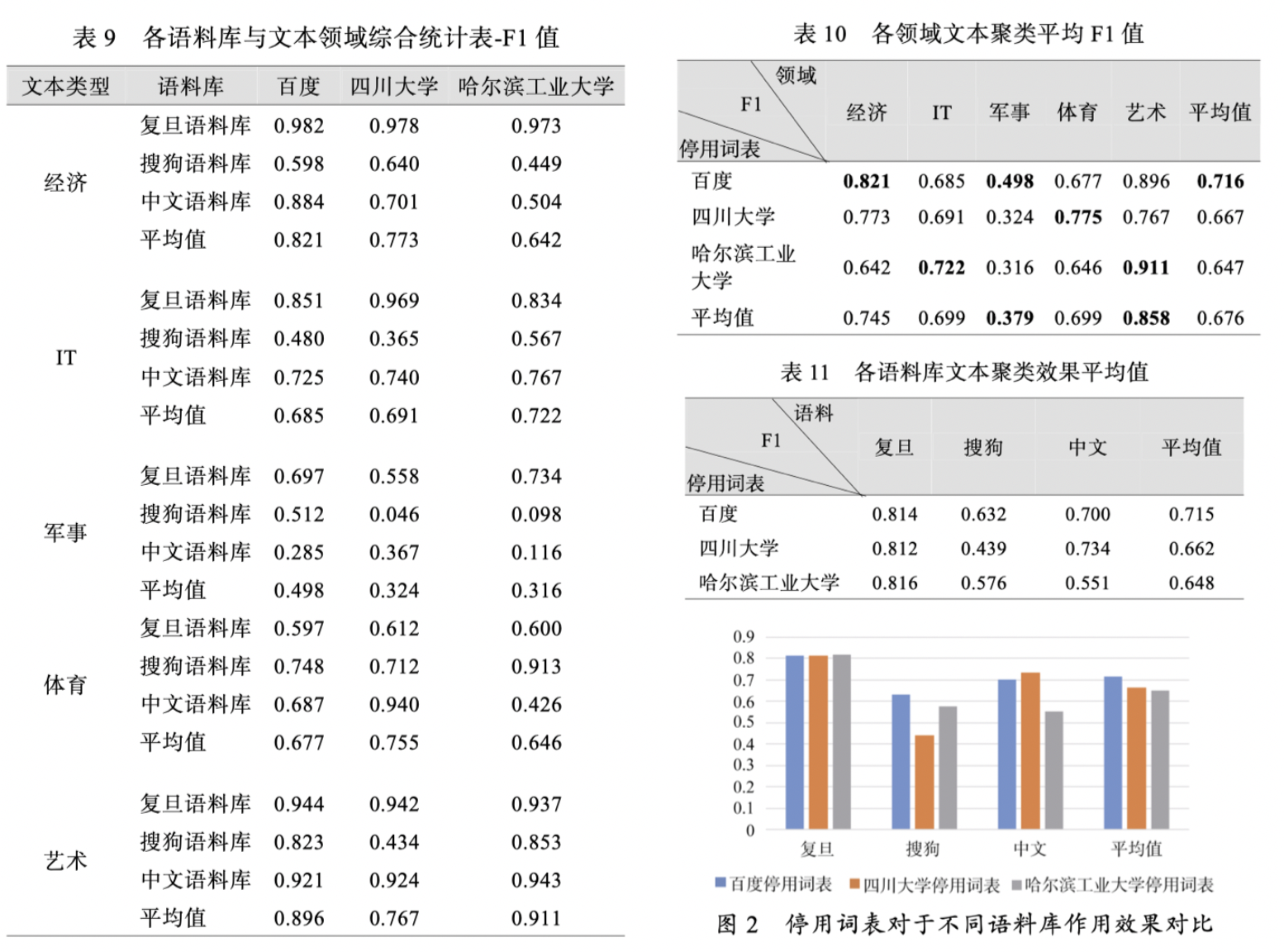
In fact, different stopword lists have their applicable scopes. Most educational institution corpora are based on academic literature, so stopword lists from institutions like Fudan and Sichuan University are more suited for documents and emails. In contrast, portal websites' corpora are more suited for news reports, each with its own characteristics.
Text mining and word segmentation statistics involve stopword issues, which are enhanced by integrating stopword lists from Harbin Institute of Technology, Sichuan University, and Baidu, as well as Fudan’s stopword list collected from CSDN, to strengthen the clustering effect of text on "economy," "society," and "literature" to better target keywords.
Text analysis work content is shown in the referenced image 2. The objectives are similar, only the methods differ slightly, but the results are the same.
References
[1] Huang Jun, "The Emotional Impact of Workplace Abuse and Behavioral Responses, and the Spread of Social Media like Bilibili," P149, [J] Communication Innovation Research, 2021(12)
[2] Guan Qin, Deng Sanhong, Wang Hao, "A Comparative Study of Common Stopword Lists for Chinese Text Clustering," P76, [J] Data Analysis and Knowledge Discovery, 2017(3)
## Basic Research on Sociological Topics
This section focuses on analyzing internet news media and network community organization mobilization.
Click for details
Summary of Subculture Perspective Commentary and Bullet Screen Survey
Overall, in the post-emotional era, I realized that people's emotional experiences are diverse. Just based on the interviewees' quotes regarding topics like "shipping CPs" and "cute pets," it is concluded that some interviewees have simplistic, idealized thoughts. This is unreliable and cannot be generalized. A more realistic perspective should be that some interviewees may not care about such topics, or they haven't given them much attention or deeper understanding. Furthermore, the data cannot draw conclusions about the interviewees' emotions, thoughts, or behavioral logic; it only highlights certain connections. To clarify the truth and underlying logic of these matters, more time and effort need to be spent on research.
Analysis of People's Livelihood and Timely Comment News Media and Audience Behavior
Positive Behavioral Role of People's Livelihood Commentary Media
In a one-dimensional society1, people from different regions often face similar life difficulties and social disputes. Through media selection of typical people's livelihood cases, it is easy for the public to gain a personal experience, creating cross-regional emotional resonance. Timely commentary based on this follows the principle of seeking truth from facts, analyzing various public opinion hot topics scientifically and rationally, while proposing feasible and constructive plans for the future. To a certain extent, this alleviates social contradictions, guides public emotions, and helps open the people's minds. However, it is important to emphasize that the purpose of opening the people's minds is for them to develop critical thinking, independent thought, and objective analysis of problems. It highlights the need for social progress, not to belittle the intellectual level and capabilities of the public.
Attribution of Focus Loss Phenomenon in People's Livelihood Commentary News Audiences
On one hand, audiences receive people's livelihood and timely commentary information due to personal resonance, curiosity, and other factors. On the other hand, living in a risk society3, audiences develop a psychological rejection of serious content and need a topic for casual conversation and entertainment to relieve anxiety, seek pleasure, and simultaneously look for groups with similar interests. This can also explain my previous question: "Why do I see my colleagues handle daily work efficiently, but when it comes to TV dramas or news reports, they are like parrots with no opinions, like idiots?" In general, the phenomenon of losing focus in public opinion is inevitable and normal. The audience's curiosity about news headlines, their patience for waiting and deep thinking about events no longer meets the expectations of some audience members. With limited attention and energy, these audience members turn to other topics with entertainment value and casual discussions, like popcorn-style leisure entertainment (gossip), to relieve stress and gain pleasure.
Analysis of the "Little Pink" Group
The term "Little Pink" is used by the public to refer to the online patriotic youth group. "Little" refers to their young age, which makes them seem naive but full of energy and passionate; "Pink" refers to the unique way of expression on the internet, such as using cute language and various "kawaii" emoticons. Moreover, due to their youth, their life experiences have not yet shaped their minds; "Red" refers to the strong patriotism and love for the party and leader, which is commonly associated with the Chinese Communist Party in the Chinese context.4
Liu Fang's definition of the "Little Pink" group is accurate. She further divides the group into different age ranges, social classes, and occupational backgrounds. Among those aged 18 to 24, the student group accounts for a large proportion of the "Little Pink," most of whom come from working-class families. However, prior to the popularity of the Old Bull Sail model, a significant number of "Little Pink" came from middle-class urban families, which also needs to be noted. In any case, both groups share a common characteristic: the "Little Pink" group has strong social consumption ability and purchasing power, bears relatively less social pressure, and is a beneficiary and witness to the increasing national power brought by China's reform and opening up.
Reading "Research on Discourse Expression and Community Mobilization in the 'Emperor Bar Expedition' Event"
Emperor Bar Expedition: Group Mobilization and Public Opinion Guidance
When the culture of a group aligns with the values and goals they advocate, it forms a driving force that encourages group members to culturally identify with the Emperor Bar community from multiple perspectives and to engage in collective interaction. Through organized mobilization, Emperor Bar profoundly influences the values and thinking patterns of its members, thereby motivating their enthusiasm and unity to support collective activities within the community.
On internet platforms, the expression of nationalism has become a common phenomenon. Through shared symbols, behaviors, and establishing connections with others who share similar views, individuals express their identification with their country and ethnicity. This performance of identity politics is influenced by both the individual and external environmental factors. In the "Zhou Ziyu Incident," Emperor Bar fully utilized the connectivity of the internet, climbing rankings and driving traffic across platforms. By constructing a common "patriotism" and "nationalism" discourse, they mobilized and recruited participants. Although the "Emperor Bar Expedition" appeared to be well-organized, with participants adhering to commands, having clear departure times, discipline, and attack targets, and requiring the use of collective templates, in practice, the youth mobilized by the new discourse of Emperor Bar did not necessarily need to engage in deep logical thinking or provide arguments. Instead, the expedition became a festive and noisy game, aimed at creating a situation of collective enthusiasm. In this mobilization process, celebrity-related emoticons created a heightened atmosphere, combining stars with nationalist sentiment, further strengthening collective identification and mobilizing effects, stimulating emotional resonance among fans, and increasing their willingness to support and participate in collective actions.
Therefore, the "Emperor Bar Expedition" can be seen as an activity of collective mobilization and public opinion guidance, where the joint forces of symbols, discourse, and emotion mobilize fans to participate and support, forming a polarized group action force. This action gives network violence a "nationalism" and "patriotism" legitimized image, making it widely accepted and supported within the group.
Reading "Empirical Study on the Motives of Digital Natives' Internet Diving"
Research Purpose and Significance
Research Purpose (Micro):
- Define the concepts of "lurkers" and "digital native lurkers" to eliminate the ambiguous definition of lurking.
- Construct a motive model for lurking behavior and propose hypotheses explaining the motivations behind digital natives' lurking behavior.
- Clarify the main influencing factors and their interrelationships.
- Provide more effective suggestions for network operators and community managers.
Research Significance (Macro):
1. Theoretical Significance: Review relevant theories used in the study of lurking from sociology, economics, and psychology, and build a theoretical framework for lurking research to provide theoretical support for future researchers.
2. Practical Significance: The practical significance of studying digital natives' lurking behavior mainly lies in economic benefits, the sustainable development of the internet, and collective intelligence.
Based on "Theory of Planned Behavior", "Social Cultural Capital Theory", "Social Identity Theory", and statistical knowledge, the questionnaire design scheme
Sample questionnaire design image5
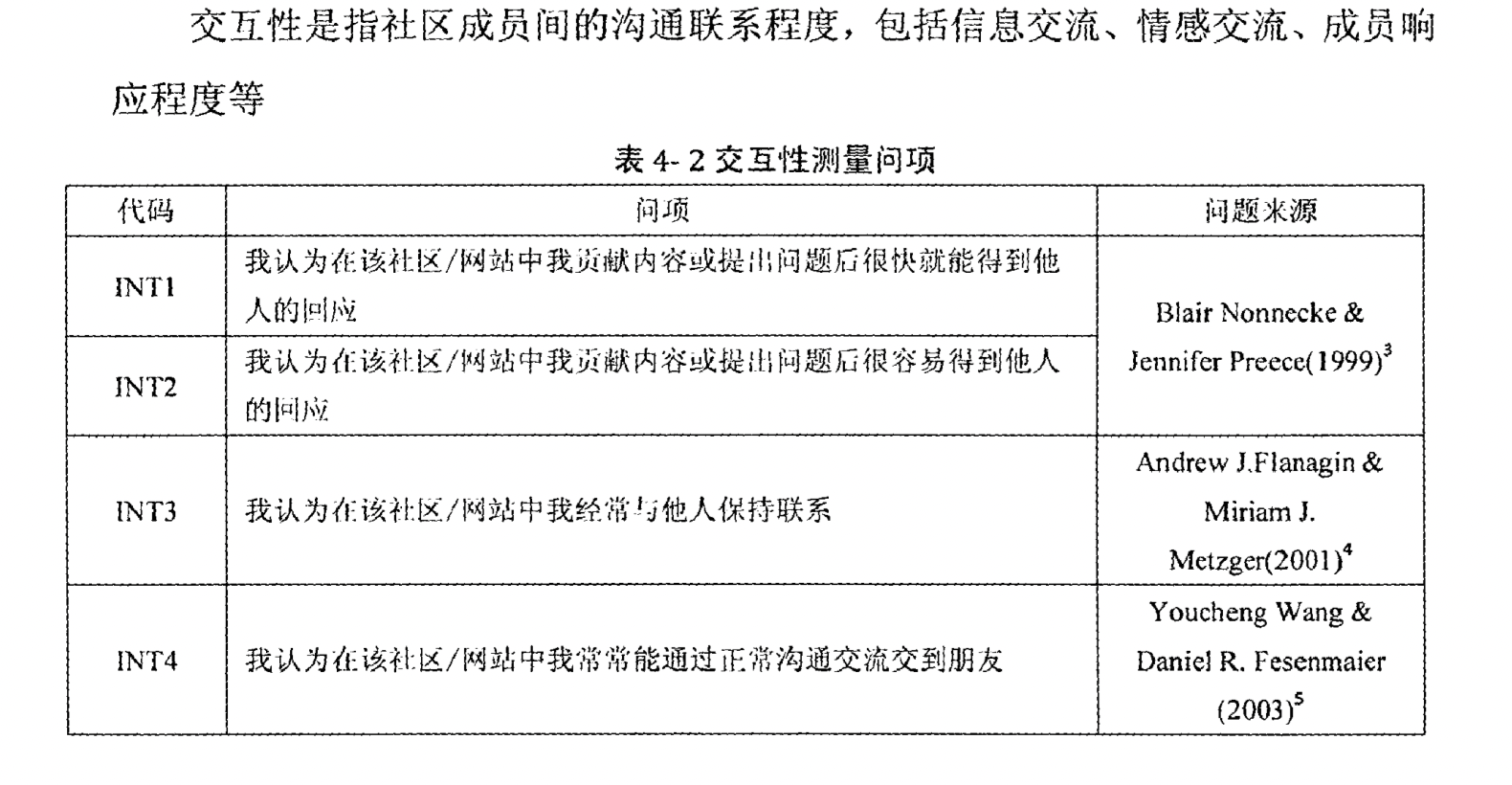
- Reliability Analysis: Focuses on whether the Cronbach's alpha value of each latent variable exceeds the critical value of 0.7.
- Validity Analysis: Mainly based on exploratory factor analysis, statistical methods are used to judge whether the data has satisfactory construct validity.
## Windows Server Domain Controller
Script Locations:
* https://github.com/hoochanlon/scripts/tree/main/d-pwsh-dc
* https://github.com/hoochanlon/scripts/tree/main/d-bat-dc
Graphical Version:
* [52pojie Forum - 【PowerShell】Batch Add Permissions Based on Text Content](https://www.52pojie.cn/thread-1981245-1-1.html)
* [52pojie Forum -【PowerShell】Convert Folder Security Permissions to Corresponding Share Permissions (Project)](https://www.52pojie.cn/thread-1980549-1-1.html)
* [52pojie Forum - View Which Shared Folders a User Has Permissions for, and Remove Permissions](https://www.52pojie.cn/thread-1979992-1-1.html)
* [52pojie Forum - A Simple Domain Account Export Script (Requires Regex)](https://www.52pojie.cn/thread-1979794-1-1.html)
* [52pojie Forum -【PowerShell】Add/Remove Domain Users, File Authorization, Organizational Units, and Domain User Recovery](https://www.52pojie.cn/thread-1976184-1-1.html)
## Windows Desktop Technical Baseline Check
First, ensure that PowerShell is enabled on your system:
* **Enable PowerShell feature: `Set-ExecutionPolicy RemoteSigned`**
* **Disable PowerShell feature: `Set-ExecutionPolicy Restricted`**
Click for Details
One-click usage, local download with GB2312 encoding Graphical Version
irm https://ghproxy.com/https://raw.githubusercontent.com/hoochanlon/scripts/main/d-pwsh/frontline_helpdesk.ps1|iex
Feature Overview:
- Check IP and network device connectivity status
- Check printer, print spooler, and scanner status
- Check basic driver information for hard drives, CPUs, memory, graphics cards, etc.
- Check device security, recent updates, scheduled tasks, certificate policies, system core file access control
- Check host active sharing protocol-related information
- Check computer sleep, reboot frequency, abnormal shutdown, program crashes, etc.
- Execute all functions of options 1–6
- Generate analysis reports for "Device Driver Check", "Five-Day Warning Events", "Login/Logout Activity Logs", "Monthly Threat Overview"
- View guidance and development instructions
By the way
Linux baseline check (PR) can be found at: al0ne/LinuxCheck. For Macs, maintaining these security services is not suitable for small and medium-sized businesses.
In the broader context, this article CSDN - Three Methods to Manage Mac Computers in Enterprises mentions management strategies that are considered effective, but compared to Windows, they are still not sufficient.
## Windows Enterprise Basic Environment Requirements
Main Involves:
* IE, Windows Defender, Windows Update, Flash & Chrome v87, DingTalk silent installation, automatic printer installation
* File checksum tools: MD5, SHA1, SHA256 hash calculation, comparison, verification tools.
* C drive space cleanup: DingTalk, WeChat, Foxmail local cache, Windows.old, Windows upgrade logs, files, etc. One-click cleanup script (C drive Thanos script).
* Basic skills required for job positions, IQ and EQ assessment, salary range summary, and demand analysis.
Click for Details
Prevent Edge hijacking IE Graphical Version
curl -L https://ghproxy.com/https://github.com/hoochanlon/scripts/raw/main/d-bat/keep_ie.bat|cmd- Note【1】: Domain Controller IE Template Graphical Version
- Note【2】: Code Address: https://github.com/hoochanlon/scripts/blob/main/d-bat/saigonoie.bat
Calculate IE compatible view website hex, one-click usage, need to convert to GB2312 encoding for local use.
irm https://ghproxy.com/https://raw.githubusercontent.com/hoochanlon/scripts/main/d-pwsh/clac_ie_clearablelistdata_hex.ps1|iex
One-click permanently disable Windows update settings Graphical Version
curl -L https://ghproxy.com/https://github.com/hoochanlon/scripts/raw/main/d-bat/stop_update.bat|cmdOne-click restore disabled Windows update settings
curl -L https://ghproxy.com/https://github.com/hoochanlon/scripts/raw/main/d-bat/re_update.bat|cmdOne-click enable or disable Windows Defender real-time protection (discontinued, suggest using sordum.org/defender-control)
curl -OfsSL https://ghproxy.com/https://raw.githubusercontent.com/hoochanlon/scripts/main/d-bat/choice_wdrt.bat&&call choice_wdrt.batC drive Thanos script: One-click cleanup of DingTalk, WeChat, Foxmail local cache, Windows.old, Windows upgrade logs, files, etc.
curl -OfsSL https://ghproxy.com/https://raw.githubusercontent.com/hoochanlon/scripts/main/d-bat/mieba.bat&&call mieba.batOne-click check if a program runs with administrator rights
curl -OfsSL https://ghproxy.com/https://raw.githubusercontent.com/hoochanlon/scripts/main/d-bat/nano_runas.bat&&call nano_runas.batOne-click MD5, SHA1, SHA256 file verification tool
curl -OfsSL https://ghproxy.com/https://raw.githubusercontent.com/hoochanlon/scripts/main/d-bat/md5tools.bat&&call md5tools.batOne-click install Flash and configure supported Chrome version 87
curl -OfsSL https://ghproxy.com/https://raw.githubusercontent.com/hoochanlon/scripts/main/d-bat/fxxk_chxxa.bat&&call fxxk_chxxa.batOne-click block Chrome browser updates
curl -OfsSL https://ghproxy.com/https://raw.githubusercontent.com/hoochanlon/scripts/main/d-bat/deny_chrome_update.bat&&call deny_chrome_update.batOne-click PDF to PNG
python3 -c "$(curl -fsSL https://ghproxy.com/https://raw.githubusercontent.com/hoochanlon/scripts/main/d-python/PDFtoPNG.py)"One-click fix for shared printer 0x11b error
curl -OfsSL https://ghproxy.com/https://raw.githubusercontent.com/hoochanlon/scripts/main/d-bat/fix_0x11b_share_print.bat&&call fix_0x11b_share_print.batOne-click retrieve job position information and reference material websites
python3 -c "$(curl -fsSL https://ghproxy.com/https://raw.githubusercontent.com/hoochanlon/scripts/main/d-python/zhipin_demo.py)"Install specified Chrome and block updates: only_install_chrome65.bat ; DingTalk silent install source code: fuck_dingding.bat
## Various Management Maintenance Scripts
Click for Details
Complete tool, scripts, documentation
## Linux Cloud Server Security Transformation
Cloud servers purchased from cloud service providers generally have no security software protection. Every day, cybercriminals scan public networks, attempting to remotely brute-force and invade servers. Therefore, preventive and defensive measures need to be taken.
Click for details
One-click configuration for SSH login, user password policy, and Ban IP setup Image & Text Version
- SSH Login: Key-based login without password, long heartbeat connection to prevent client disconnection
- Password Policy: No restrictions on special characters or case, supports minimum length of 4-5 characters
- Ban IP: Permanently ban IP after three failed login attempts within 30 seconds, except for your own IP.
sudo bash -c "$(curl -fL https://ghproxy.com/https://raw.githubusercontent.com/hoochanlon/scripts/main/d-shell/lite_ssh_n_ban.sh)"
SSH single configuration: One-click SSH fast configuration for SSH key login policy and simple password rules. (The single configuration part restricts access to only your IP, i.e., AllowUsers)
sudo bash -c "$(curl -fL https://ghproxy.com/https://raw.githubusercontent.com/hoochanlon/scripts/main/d-shell/simple_ssh.sh)"
fail2ban single configuration: One-click fail2ban setup, from download to installation, configuration generation, and service start. (You can refresh your public IP configuration with the single part.)
sudo bash -c "$(curl -fL https://ghproxy.com/https://raw.githubusercontent.com/hoochanlon/scripts/main/d-shell/simple_ban.sh)"
One-click to create a custom user with admin privileges Image & Text Version
- Custom username
- No-password for su, sudo, and wheel group members
- Lock root remote login in sshd_config to enhance security
sudo bash -c "$(curl -fL https://ghproxy.com/https://raw.githubusercontent.com/hoochanlon/scripts/main/d-shell/diy_add_wheel.sh)"
One-click FTP setup Image & Text Version
- Shared directory: /var/ftp/share
- Limit unauthorized access to shared directories, allowing read and write.
- Secure, privatized, limited to your public IP access.
No password version, username: ftpuser, password: P@ssw0rd
sudo bash -c "$(curl -fL https://ghproxy.com/https://raw.githubusercontent.com/hoochanlon/scripts/main/d-shell/simple_vsftpd.sh)"
Custom user version
sudo bash -c "$(curl -fL https://ghproxy.com/https://raw.githubusercontent.com/hoochanlon/scripts/main/d-shell/lite_vsftpd.sh)"
## Wallpaper Settings | Quick Web Pages
Work and live simultaneously.
- Ruby must be version 3.0 or above
- Ruby's integration on Windows is not as smooth as on Linux/macOS.
- For this Ruby-based screen scraping and text processing, Ruby's library support is far less comprehensive than Python, suitable only for basic web scraping tasks.
- Due to network conditions in China, native writing is avoided; instead, aria2 is used for downloading, to monitor the progress.
Click for details
Wallpaper Settings
One-click Bing wallpaper downloader Image & Text Version
python3 -c "$(curl -fsSL https://ghproxy.com/https://raw.githubusercontent.com/hoochanlon/scripts/main/d-python/get_bing_wallpapers.py)"One-click download of Microsoft official design wallpapers using Ruby
ruby -e "$(curl -fsSL https://ghproxy.com/https://raw.githubusercontent.com/hoochanlon/scripts/main/d-ruby/get_msdesign_wallpapers.rb)"One-click scheduled wallpaper change (Mac only)
bash -c "$(curl -fsSL https://ghproxy.com/https://raw.githubusercontent.com/hoochanlon/scripts/main/d-shell/mac_corn_diy_wallpaper.sh)"Quick Web Pages
Windows web page opening tool
curl -OfsSL https://ghproxy.org/https://raw.githubusercontent.com/hoochanlon/scripts/main/d-bat/webtools.bat&&call webtools.batMac web page opening tool
bash -c "$(curl -fsSL https://ghproxy.org/https://raw.githubusercontent.com/hoochanlon/scripts/main/d-shell/webtools.sh)"## Fun Projects
This section contains fun projects created through my exploration, combining various online resources, source codes, and unique keys, reimagined and transformed into usable commands.
* Windows/Office, WinRAR, EmEditor, IDM, XchangePDF
* Wi-Fi, LAN IP viewer, Host IP operator and location lookup
* More...
Click for more details
CMD one-click call to switch Windows versions and activate Windows/Office Image & Text Version
curl -O https://ghproxy.com/https://raw.githubusercontent.com/TerryHuangHD/Windows10-VersionSwitcher/master/Switch.bat&&TIMEOUT /T 1&&start Switch.bat&&powershell -command "irm https://massgrave.dev/get|iex"CMD one-click install WinRAR registration and activation
powershell -command Invoke-WebRequest -Uri "https://ghproxy.com/https://raw.githubusercontent.com/hoochanlon/scripts/main/d-bat/winrar_down_reg.bat" -OutFile "C:/Users/${env:UserName}/Downloads/winrar_down_reg.bat"&&TIMEOUT /T 1&&start /b C:\Users%username%\Downloads\winrar_down_reg.bat
Powershell one-click EmEditor serial key generator
irm https://ghproxy.com/https://raw.githubusercontent.com/hoochanlon/scripts/main/d-pwsh/emeditor_random_keygen.ps1|iex
Powershell one-click IDM activation (my own solution is outdated, no updates due to copyright issues in China)
iwr -useb https://ghproxy.com/https://raw.githubusercontent.com/lstprjct/IDM-Activation-Script/main/IAS.ps1 | iex
Powershell for generating XchangePDF Editor license
curl https://ghproxy.com/https://raw.githubusercontent.com/hoochanlon/scripts/main/d-pwsh/xchange_v8_active.ps1 -Outfile xchange_v8_active.ps1 | powershell -c xchange_v8_active.ps1
Win7 "Insufficient Memory" error when opening images Image & Text Version
powershell -c "irm https://ghproxy.com/https://github.com/hoochanlon/scripts/raw/main/d-bat/exifhelper.bat -Outfile exifhelper.bat" && exifhelper.bat
## Small Utilities
Various small tools for convenience.
Click for more details
Restore Win10 right-click menu or revert Win11 right-click menu
curl -OfsSL https://ghproxy.org/https://raw.githubusercontent.com/hoochanlon/scripts/main/d-bat/right-menu.bat&&call right-menu.bat
Unlock application permission issues preventing deletion
curl -OfsSL https://ghproxy.org/https://raw.githubusercontent.com/hoochanlon/scripts/main/d-bat/delete-error.bat&&call delete-error.bat
Prevent computer from going to sleep for a specific period (Great for remote work)
curl -OfsSL https://ghproxy.org/https://raw.githubusercontent.com/hoochanlon/scripts/main/d-bat/stay-awake.bat&&call stay-awake.bat
Memory and Disk Health Check for Windows
curl -OfsSL https://ghproxy.org/https://raw.githubusercontent.com/hoochanlon/scripts/main/d-bat/win_memory_disk.bat&&call win_memory_disk.bat
Check Windows system login users and allow remote login
curl -OfsSL https://ghproxy.org/https://raw.githubusercontent.com/hoochanlon/scripts/main/d-bat/check-users.bat&&call check-users.bat
---
***Thank you for viewing. Here are the [Latex Demo](https://www.overleaf.com/read/khdnbtjxwkzx) and the [LaTex Resume Template](https://github.com/hoochanlon/resume) for fellow enthusiasts.***