https://github.com/gfw4fun/shadowtls-singbox
ShadowTLS-SingBox auto installer, v2ray xray shadow tls fake sni
https://github.com/gfw4fun/shadowtls-singbox
geoip installer shadowsocks shadowtls sing-box singbox sni stls tls v2ray xray xtls
Last synced: 8 months ago
JSON representation
ShadowTLS-SingBox auto installer, v2ray xray shadow tls fake sni
- Host: GitHub
- URL: https://github.com/gfw4fun/shadowtls-singbox
- Owner: GFW4Fun
- Created: 2023-09-29T17:55:13.000Z (about 2 years ago)
- Default Branch: master
- Last Pushed: 2023-10-01T08:27:36.000Z (about 2 years ago)
- Last Synced: 2024-12-21T14:20:18.174Z (10 months ago)
- Topics: geoip, installer, shadowsocks, shadowtls, sing-box, singbox, sni, stls, tls, v2ray, xray, xtls
- Language: Shell
- Homepage:
- Size: 223 KB
- Stars: 6
- Watchers: 1
- Forks: 2
- Open Issues: 0
-
Metadata Files:
- Readme: README.md
Awesome Lists containing this project
README
# ShadowTLS-SingBox
ShadowTLS-SingBox
- Auto Installer last sing-box
- Auto reload and geo update every day
- Auto Config generation
- with geoip rule, block ads
## Installer
```
bash <(wget -qO- https://raw.githubusercontent.com/GFW4Fun/ShadowTLS-SingBox/master/ShadowTLS-Singbox.sh)
```
- Enter your vps ip!
- Enter a popular domain, non-blocked, TLS1.3 like: apple.com
- Enter :port
- Save output to config.json
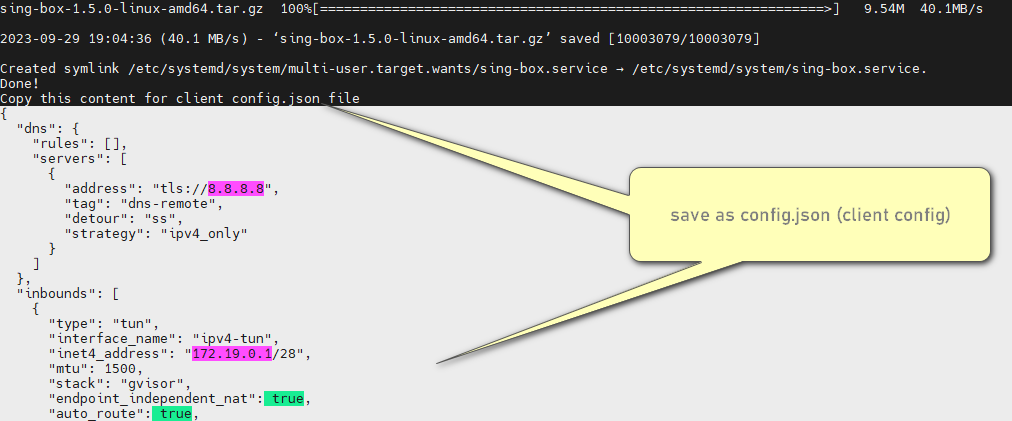
> Download > [sing-box](https://github.com/SagerNet/sing-box/releases)
>
> Download > [sing-box.cmd](https://raw.githubusercontent.com/GFW4Fun/ShadowTLS-SingBox/master/media/sing-box.cmd)
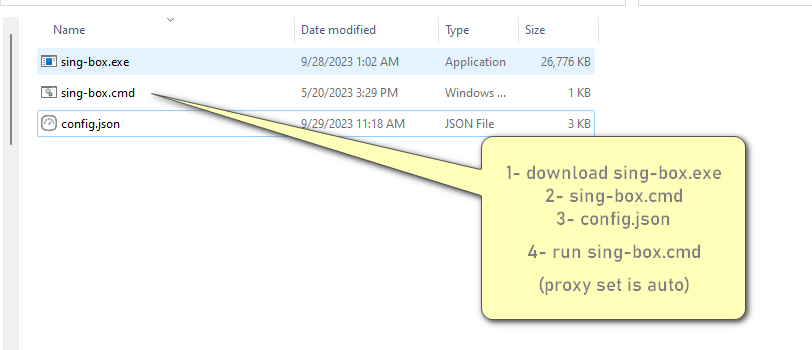
> or drag&drop *.json to sing-box.cmd
>
> or sing-box run -c config.json