Ecosyste.ms: Awesome
An open API service indexing awesome lists of open source software.
https://github.com/goldfiglabs/rpCheckup
rpCheckup is an AWS resource policy security checkup tool that identifies public, external account access, intra-org account access, and private resources.
https://github.com/goldfiglabs/rpCheckup
aws aws-security cloudsecurity cspm ec2 infosec resourcepolicy s3
Last synced: 3 months ago
JSON representation
rpCheckup is an AWS resource policy security checkup tool that identifies public, external account access, intra-org account access, and private resources.
- Host: GitHub
- URL: https://github.com/goldfiglabs/rpCheckup
- Owner: goldfiglabs
- License: mpl-2.0
- Created: 2021-02-26T00:17:52.000Z (almost 4 years ago)
- Default Branch: main
- Last Pushed: 2021-04-22T21:39:51.000Z (almost 4 years ago)
- Last Synced: 2024-08-03T12:01:28.391Z (6 months ago)
- Topics: aws, aws-security, cloudsecurity, cspm, ec2, infosec, resourcepolicy, s3
- Language: Go
- Homepage: https://www.goldfiglabs.com/
- Size: 140 KB
- Stars: 157
- Watchers: 7
- Forks: 14
- Open Issues: 1
-
Metadata Files:
- Readme: README.md
- Contributing: CONTRIBUTING.md
- License: LICENSE
- Code of conduct: CODE_OF_CONDUCT.md
Awesome Lists containing this project
- awesome-cloud-sec - rpCheckup - - rpCheckup is an AWS resource policy security checkup tool that identifies public, external account access, intra-org account access, and private resources. (Other Awesome Lists / Auditing)
README
# rpCheckup - Catch AWS resource policy backdoors like Endgame

rpCheckup is an AWS resource policy security checkup tool that identifies public, external account access, intra-org account access, and private resources. It makes it easy to reason about resource visibility across all the accounts in your org.
## Why?
We ([Gold Fig Labs](https://goldfiglabs.com)) built rpCheckup based on a part of how we assess customer AWS accounts. While there are many tools to assess and analyze IAM policies, the same treatment for policies attached to resources is a blind spot. As product iteration sometimes necessitates overprovisioned access to just get things working, finding such issues after the fact across a slew of different AWS resource types, accounts, and regions isn't straightforward.
rpCheckup generates an HTML & CSV report to make this easy.
## Supported AWS Resources
rpCheckup uses the resources supported by [Endgame](https://endgame.readthedocs.io/en/latest/) as the high-water mark for analyzing attached policies.
| Resource Type | rpCheckup | Endgame | [AWS Access Analyzer][1] |
|------------------------------------------------|--------|---------|----------------------------------|
| ACM Private CAs | ✅ | ✅ | ❌ |
| CloudWatch Resource Policies | ✅ | ✅ | ❌ |
| EBS Volume Snapshots | ✅ | ✅ | ❌ |
| EC2 AMIs | ✅ | ✅ | ❌ |
| ECR Container Repositories | ✅ | ✅ | ❌ |
| EFS File Systems | ✅ | ✅ | ❌ |
| ElasticSearch Domains | ✅ | ✅ | ❌ |
| Glacier Vault Access Policies | ✅ | ✅ | ❌ |
| IAM Roles | ✅ | ✅ | ✅ |
| KMS Keys | ✅ | ✅ | ✅ |
| Lambda Functions | ✅ | ✅ | ✅ |
| Lambda Layers | ✅ | ✅ | ✅ |
| RDS DB Snapshots | ✅ | ✅ | ❌ |
| RDS Cluster Snapshots | ✅ | ❌ | ❌ |
| S3 Buckets | ✅ | ✅ | ✅ |
| Secrets Manager Secrets | ✅ | ✅ | ✅ |
| SES Sender Authorization Policies | ✅ | ✅ | ❌ |
| SQS Queues | ✅ | ✅ | ✅ |
| SNS Topics | ✅ | ✅ | ❌ |
## Pre-requisites
* AWS credentials (~/.aws/, env variables, metadata server, etc)
* Docker
* If running from source; go version >= go1.15
## Installing
1. Download the latest [release](https://github.com/goldfiglabs/rpCheckup/releases):
Linux:
curl -Lo rpCheckup https://github.com/goldfiglabs/rpCheckup/releases/latest/download/rpCheckup_linux
chmod a+x ./rpCheckup
OSX x86:
curl -Lo rpCheckup https://github.com/goldfiglabs/rpCheckup/releases/latest/download/rpCheckup_darwin_amd64
chmod a+x ./rpCheckup
OSX M1/arm:
curl -Lo rpCheckup https://github.com/goldfiglabs/rpCheckup/releases/latest/download/rpCheckup_darwin_arm64
chmod a+x ./rpCheckup
2. Run from source:
```
git clone https://github.com/goldfiglabs/rpCheckup.git
cd rpCheckup
go run main.go
```
## Usage
Run `./rpCheckup` and view the generated report found in `output/`.

## Permissions
rpCheckup needs read-only access to portions of your AWS account.
A principal (user/role/group) needs the following to make full use
of rpCheckup:
```
AWS Managed Policy: arn:aws:iam::aws:policy/SecurityAudit
AWS Managed Policy: arn:aws:iam::aws:policy/job-function/ViewOnlyAccess
Additional Permissions:
"apigateway:GetRestApis",
"efs:Describe*",
"acm-pca:List*",
"acm-pca:GetPolicy"
```
Additionally, there is a [Terraform Module](./terraform) for creating a role with the appropriate credentials, as well as a [shell script](./run_with_role.sh) for running with an assumed role (requires running [./build.sh](./build.sh) first).
## Overview
rpCheckup uses [goldfiglabs/introspector](https://github.com/goldfiglabs/introspector) to snapshot the configuration of your AWS account. rpCheckup runs SQL queries to generate findings based on this snapshot. Introspector does the heavy lifting of importing and normalizing the configurations while rpCheckup is responsible for querying and report generation.
## Notes
If the account you are scanning is not the master account in an Organization, other
accounts in the Organization may be detected as external accounts. This is because
non-master accounts may not have access to see the organization structure.
Since rpCheckup relies on Introspector's snapshots, rpCheckup is unable to detect policies that are no longer attached. When detecting flapping or transient access, please use tools which utilize audit and security logs (CloudTrail, etc). See [here][2] for further information in preventing resource exposure.
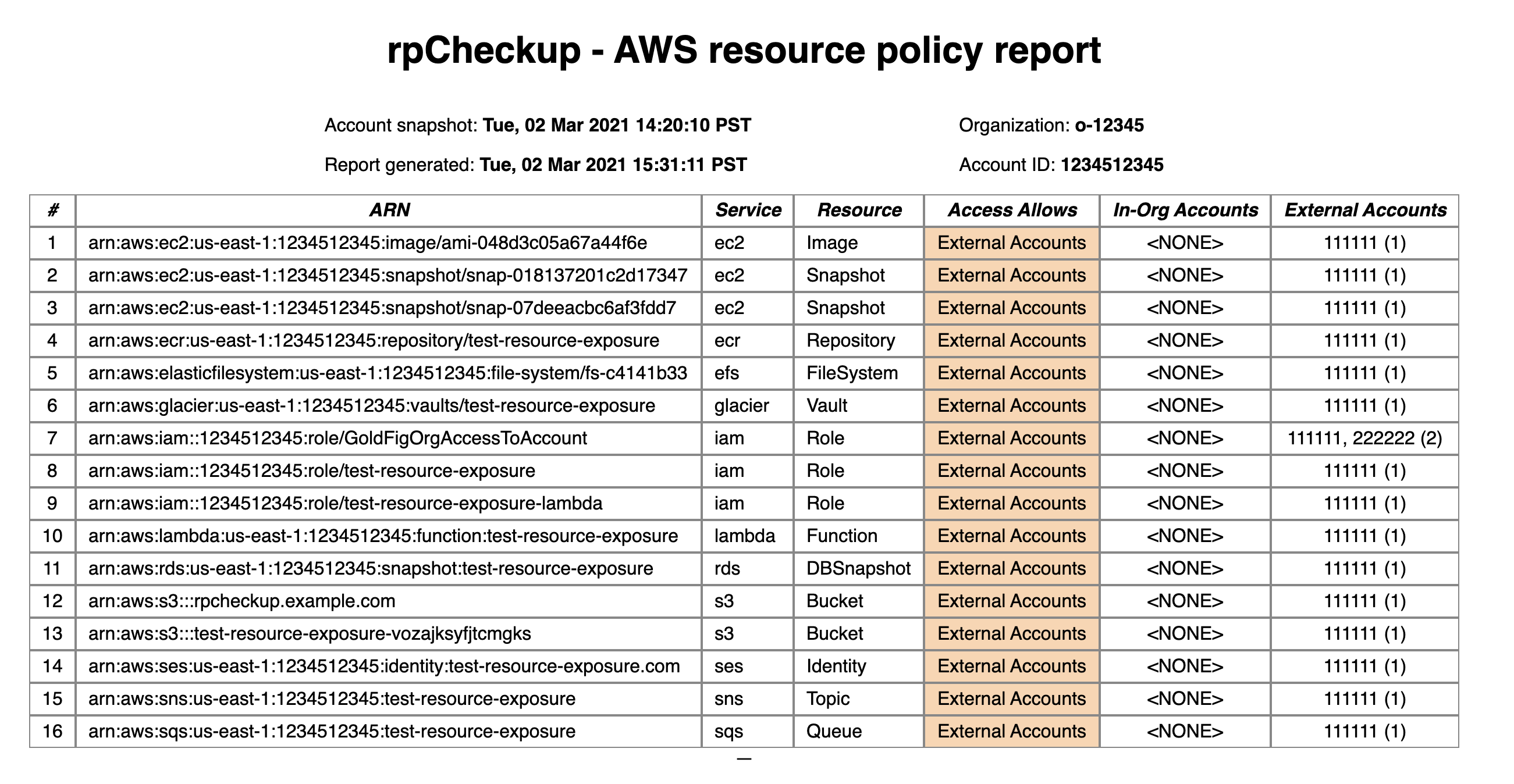
## Sample Reports
See sample reports in `sample/`
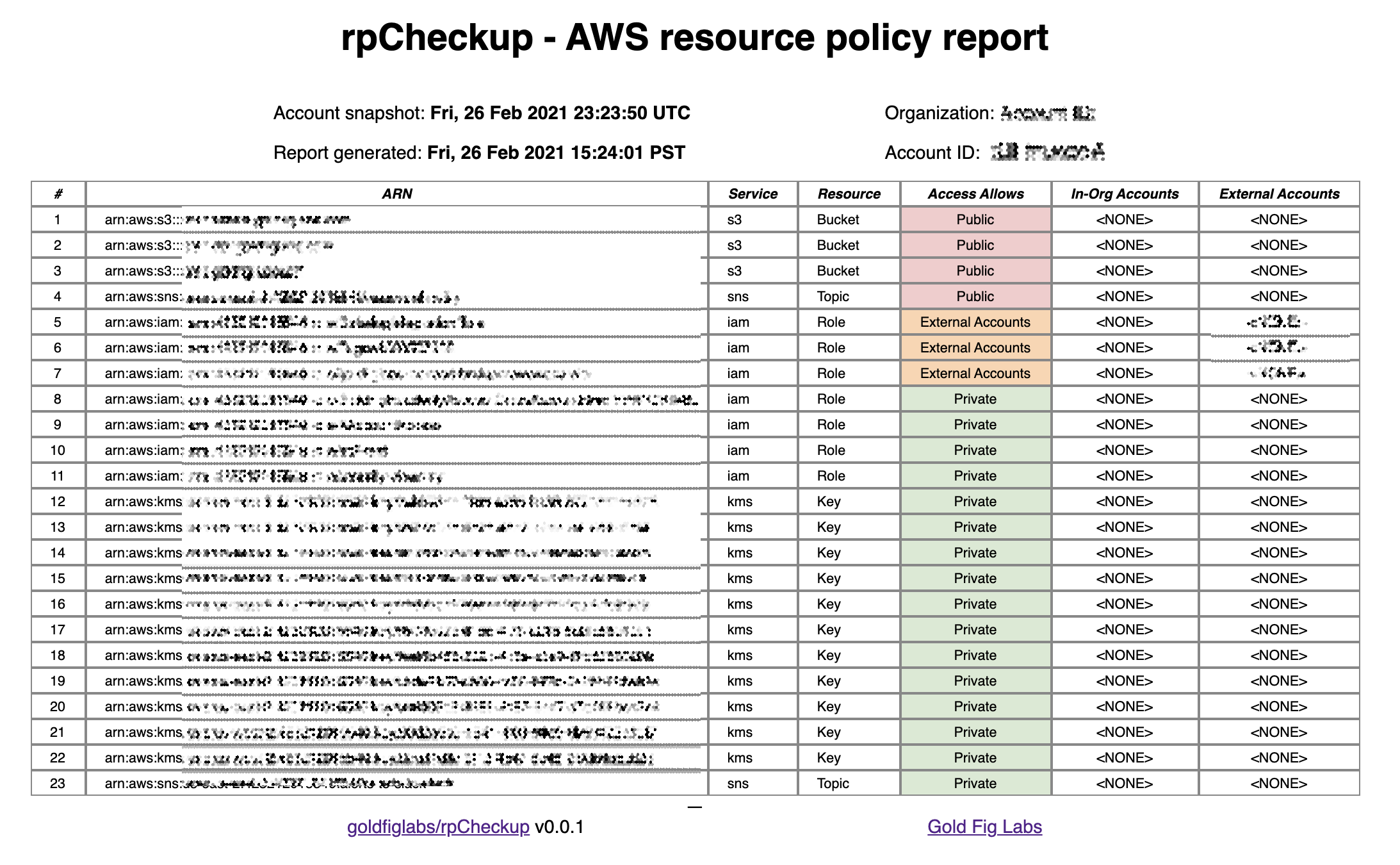
rpCheckup report against Endgame sample account:
## License
Copyright (c) 2019-2021 [Gold Fig Labs Inc.](https://www.goldfiglabs.com/)
This Source Code Form is subject to the terms of the Mozilla Public License, v.2.0. If a copy of the MPL was not distributed with this file, You can obtain one at http://mozilla.org/MPL/2.0/.
[Mozilla Public License v2.0](./LICENSE)
[1]: https://docs.aws.amazon.com/IAM/latest/UserGuide/access-analyzer-resources.html
[2]: https://endgame.readthedocs.io/en/latest/prevention/