https://github.com/haopeiwen/sniffer
IS301 Computer Communication and Network Project
https://github.com/haopeiwen/sniffer
pyqt5 sniffer
Last synced: 5 months ago
JSON representation
IS301 Computer Communication and Network Project
- Host: GitHub
- URL: https://github.com/haopeiwen/sniffer
- Owner: HaoPeiwen
- License: mit
- Created: 2017-12-06T14:19:59.000Z (over 7 years ago)
- Default Branch: master
- Last Pushed: 2018-12-11T11:25:33.000Z (over 6 years ago)
- Last Synced: 2024-11-15T22:34:52.942Z (5 months ago)
- Topics: pyqt5, sniffer
- Language: Python
- Homepage:
- Size: 21.8 MB
- Stars: 9
- Watchers: 1
- Forks: 2
- Open Issues: 0
-
Metadata Files:
- Readme: README.md
- License: LICENSE
Awesome Lists containing this project
- awesome-network-stuff - **9**星
README
# Sniffer
 

IS301 Computer Communication and Network Project
计算机通信网大作业 - 网络抓包器
*作者 -* [*Evander*](https://github.com/HaoPeiwen) *&* [*Xynnn_*](https://github.com/Xynnn007)
## Getting Startted
### Prerequisites
- Python 3.x on Win-64 platform
- [PyQt5](https://riverbankcomputing.com/software/pyqt/download5) GUI
- [ansi2html](https://github.com/ralphbean/ansi2html) used to parse ANSI ESCAPE Sequence to html css.
### Usage
pip3 install pyqt5
pip3 install ansi2html
cd ./src
python ./main.py
# Or just run bin/sniffer_v1.exe
pip3 install pyqt5
pip3 install ansi2html
cd ./bin
./sniffer_v1.exe
*Note: Python 3.x only, and the script may contains any other packages, just search for installing them.*
## Features
### Sniffing & Searching
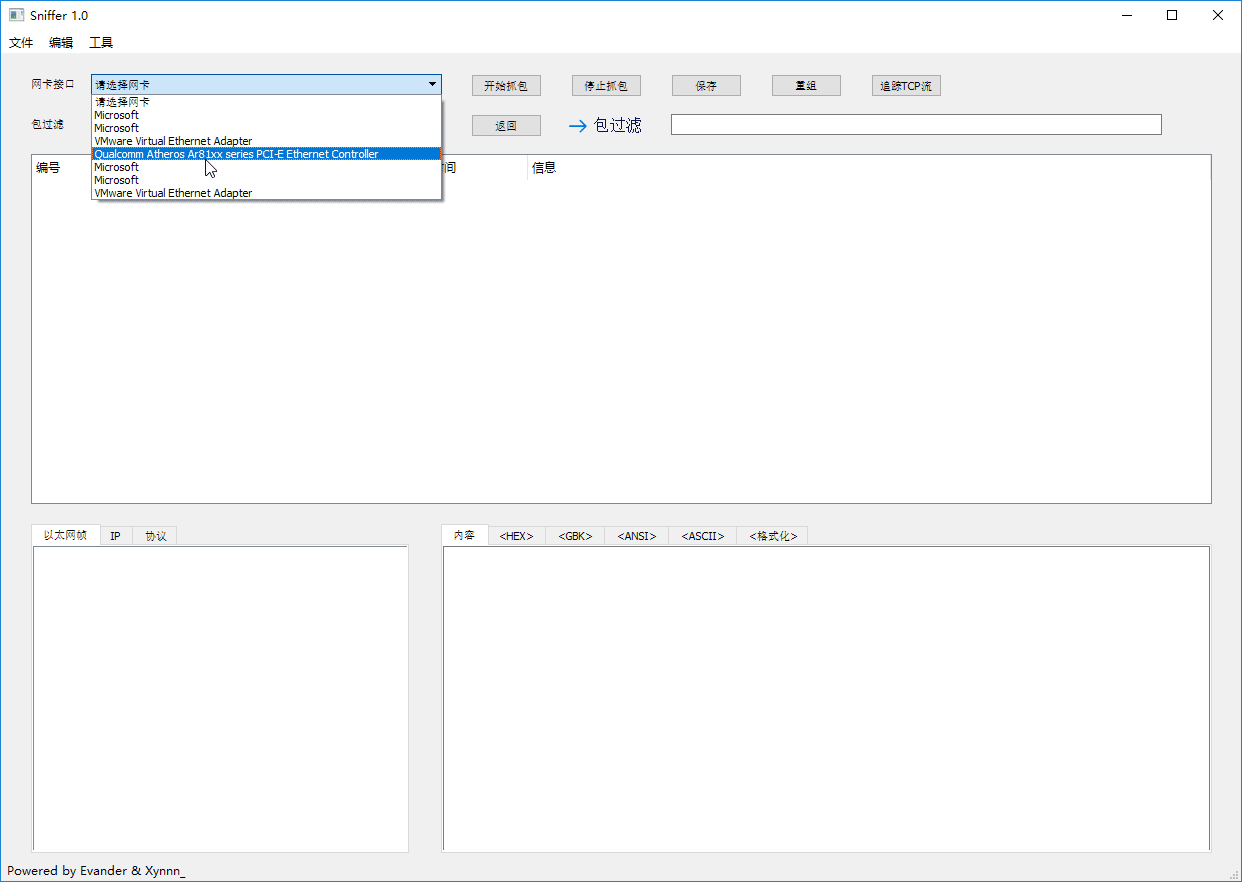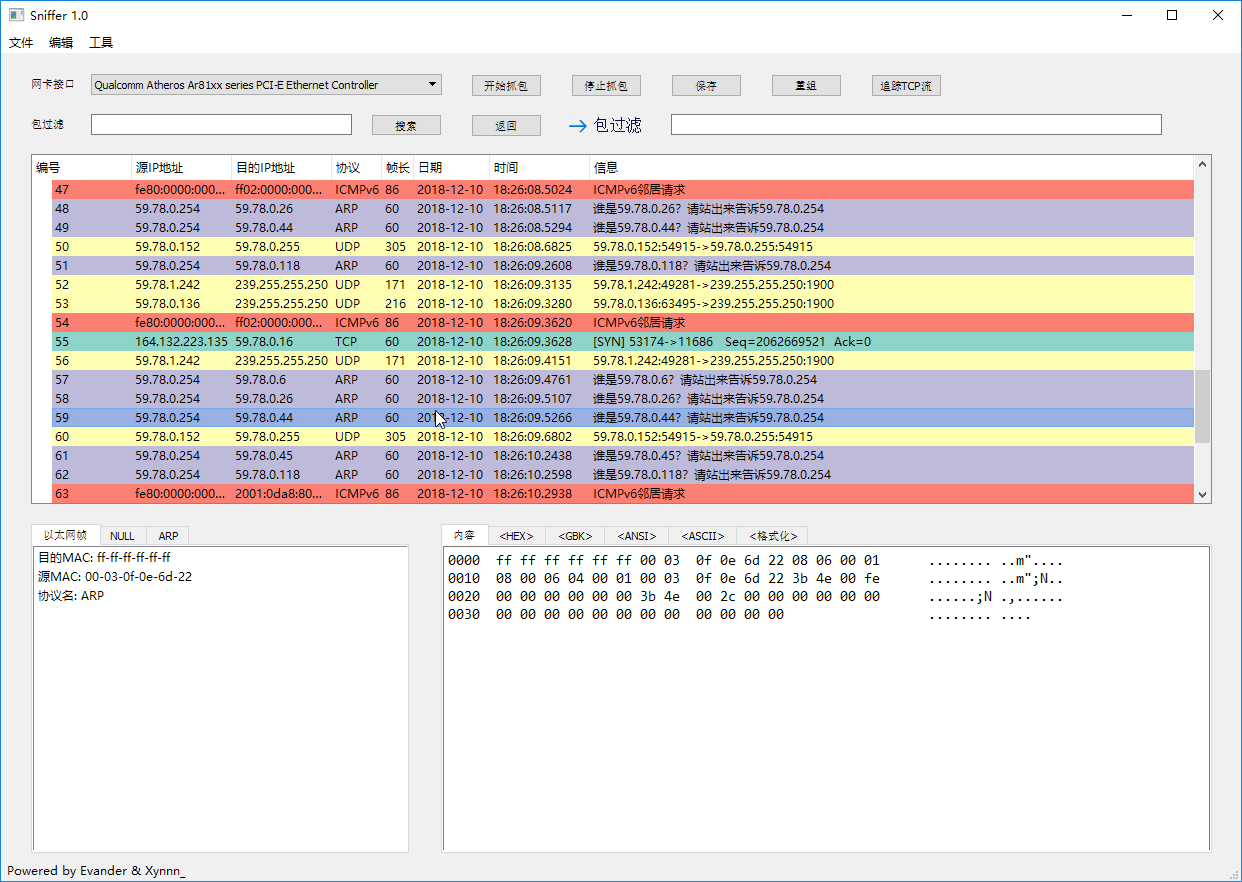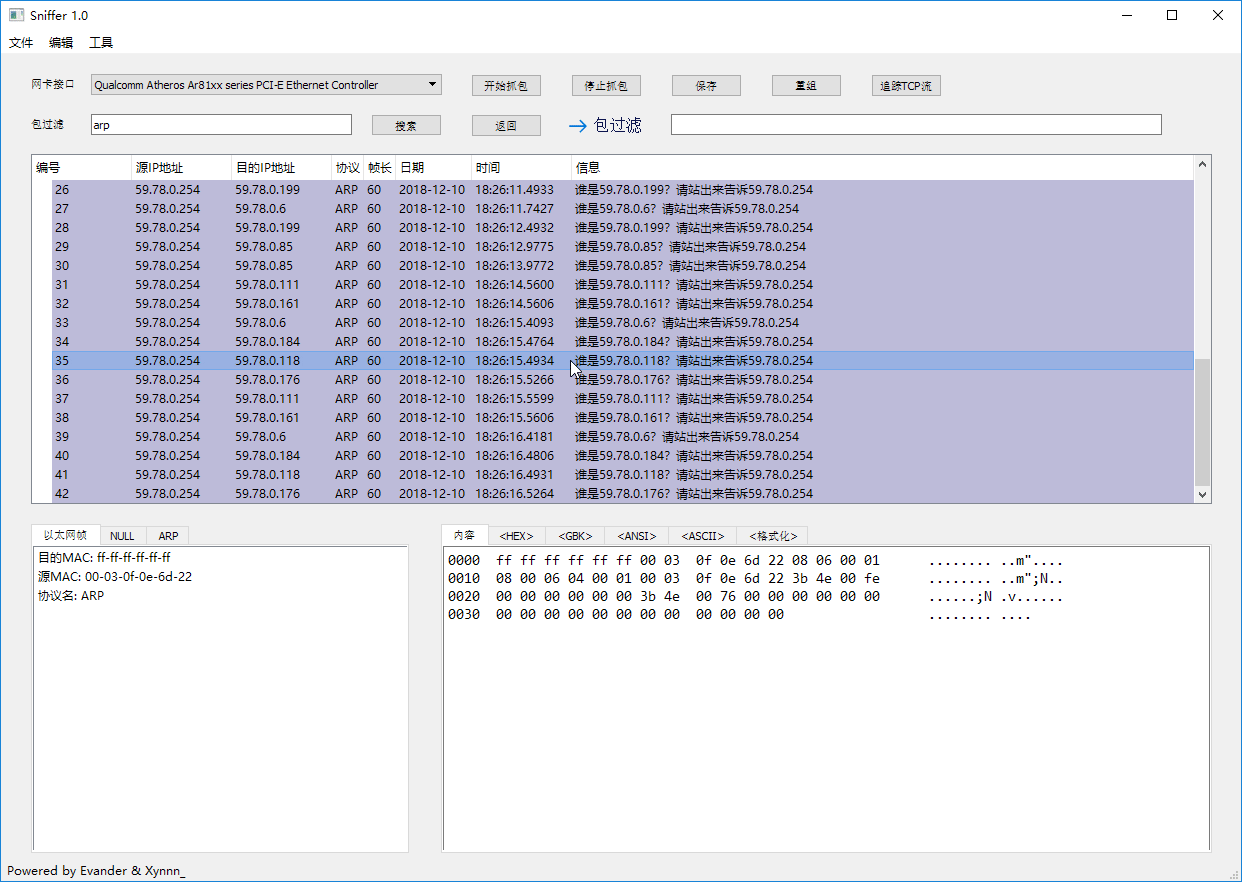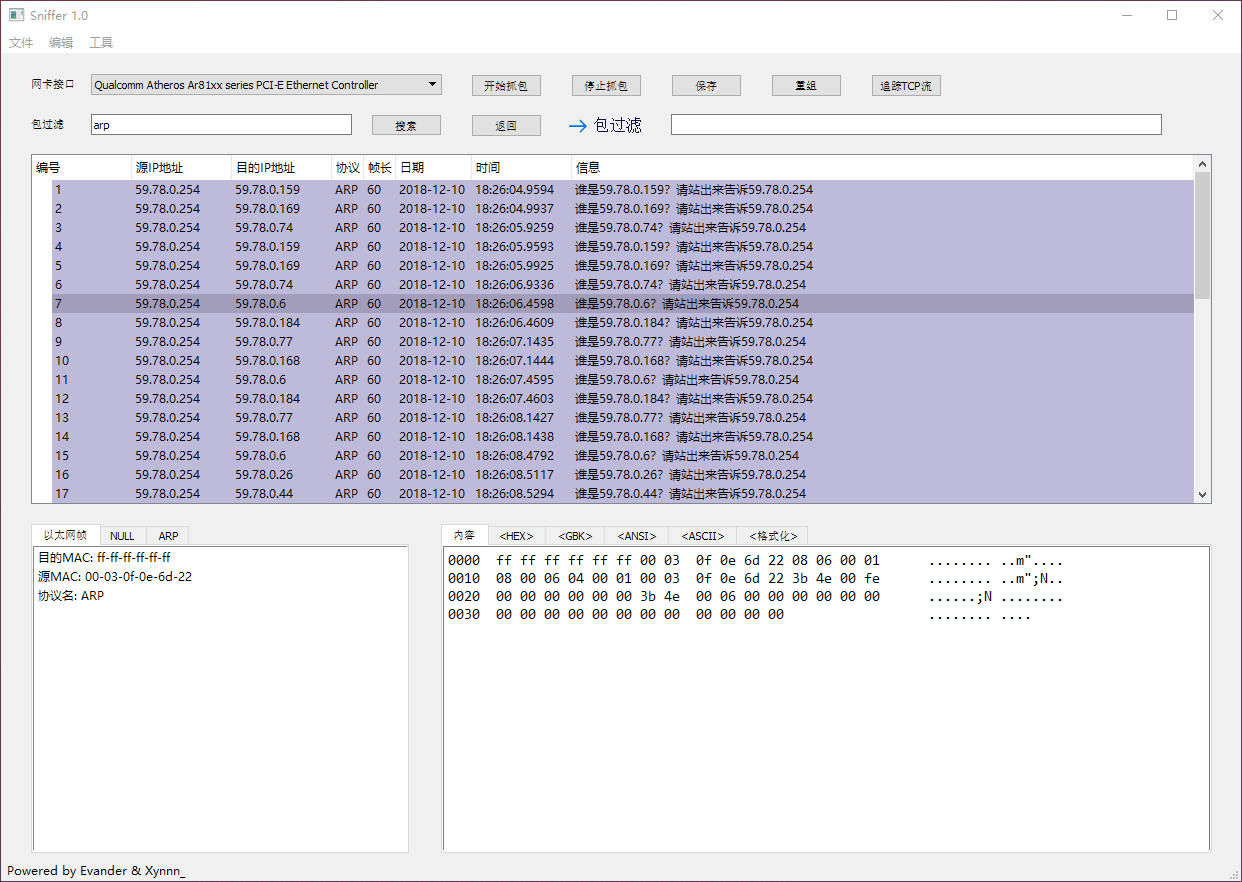
### Packets Filter & IP Packets Reassembly
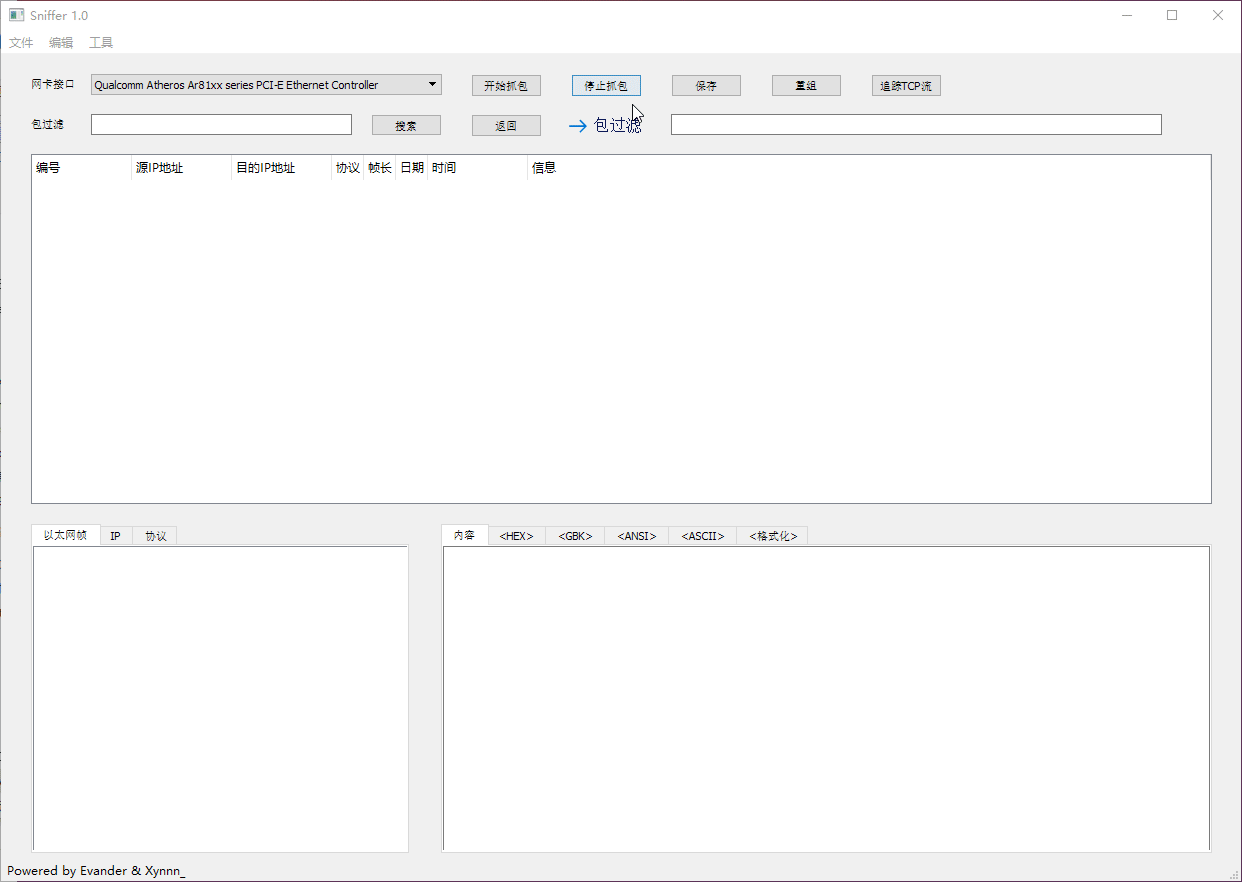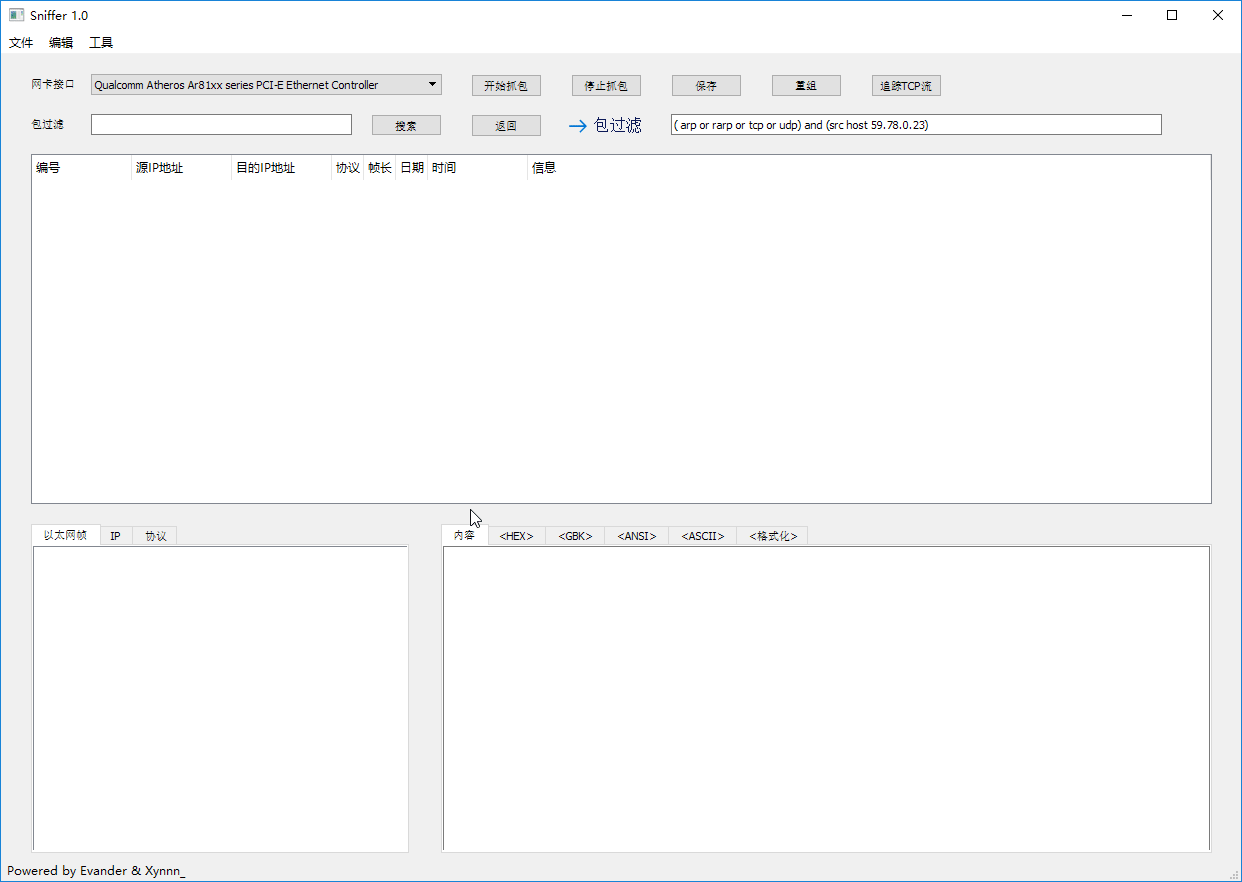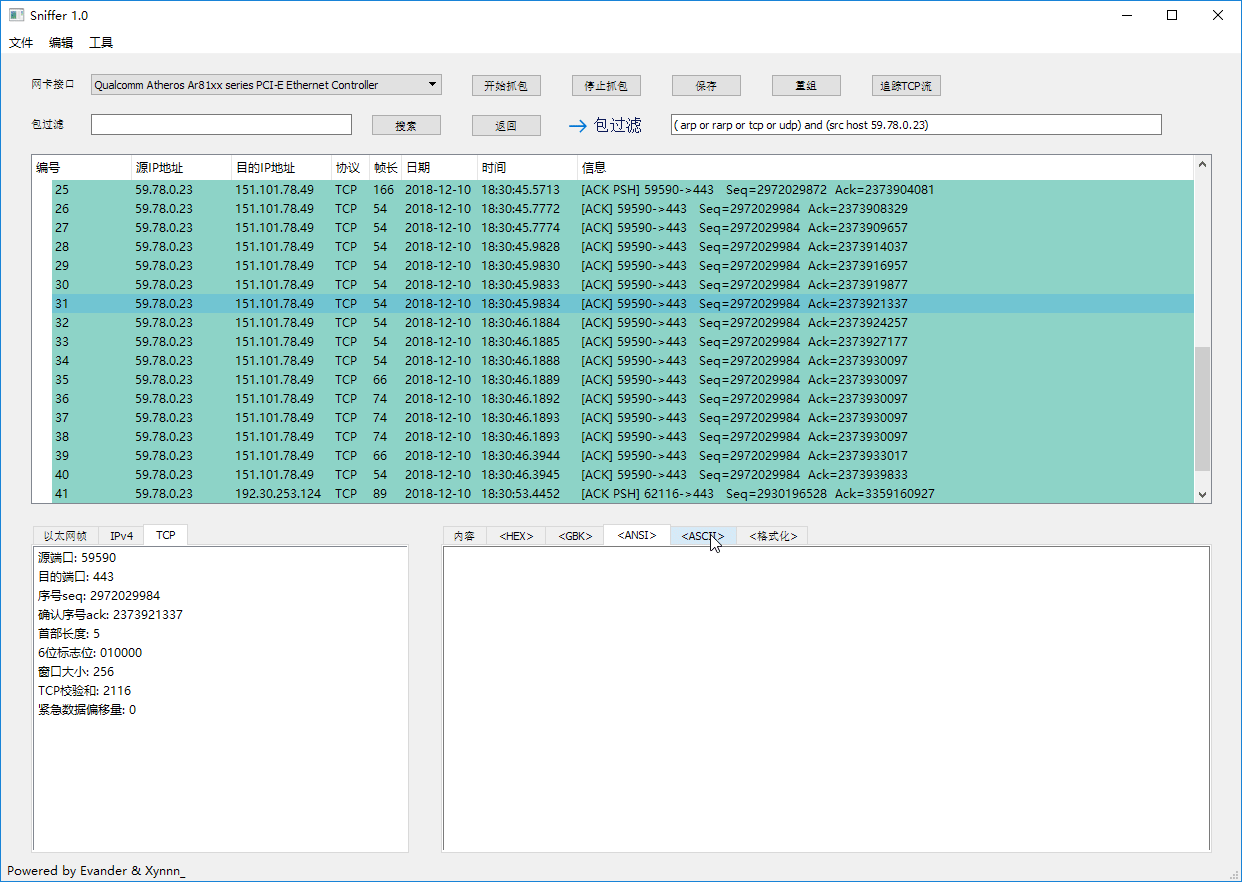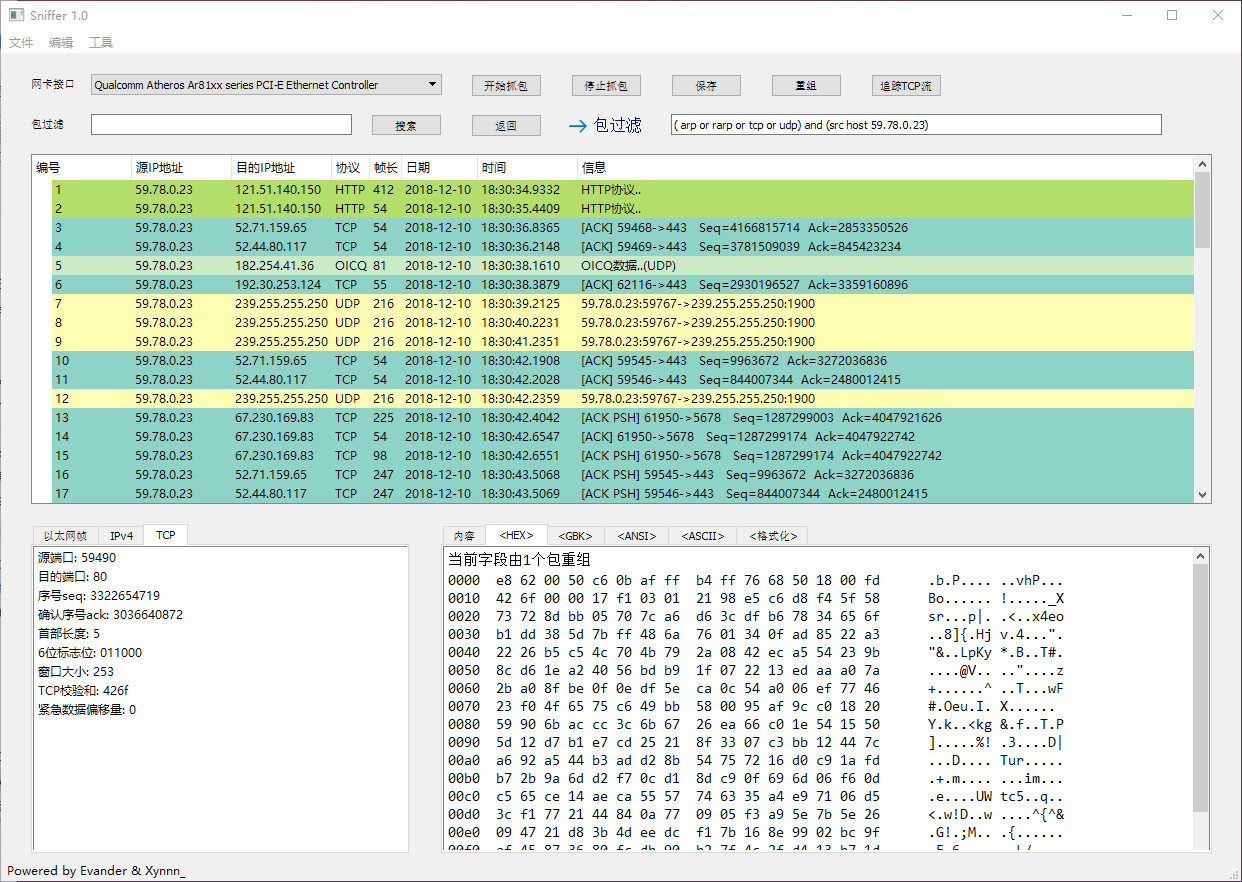
### Tracing TCP Stream
You can reassemble TCP stream packets and open it which is generated as file `nxm` automacitally in the current path.
Let's capture a FTP transfer file:
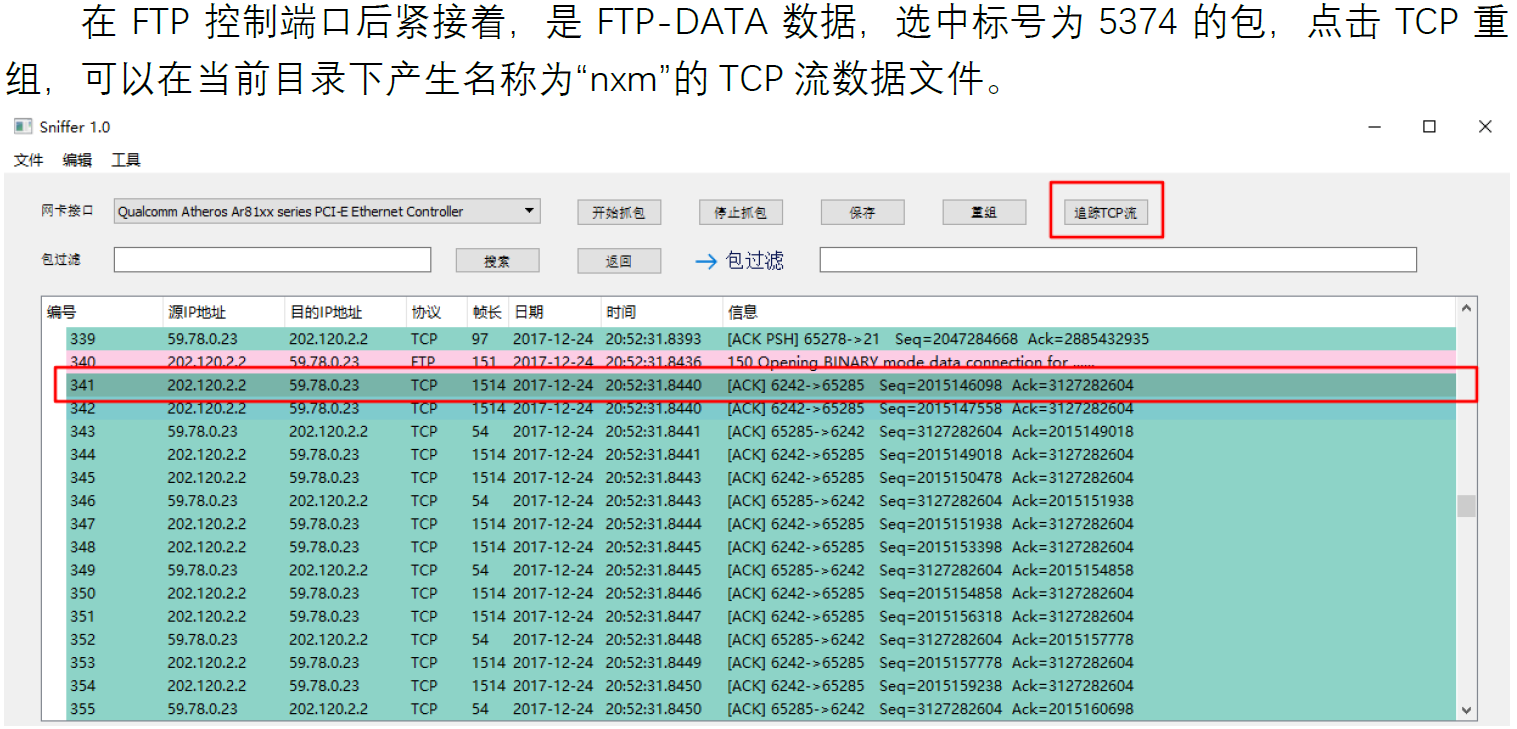
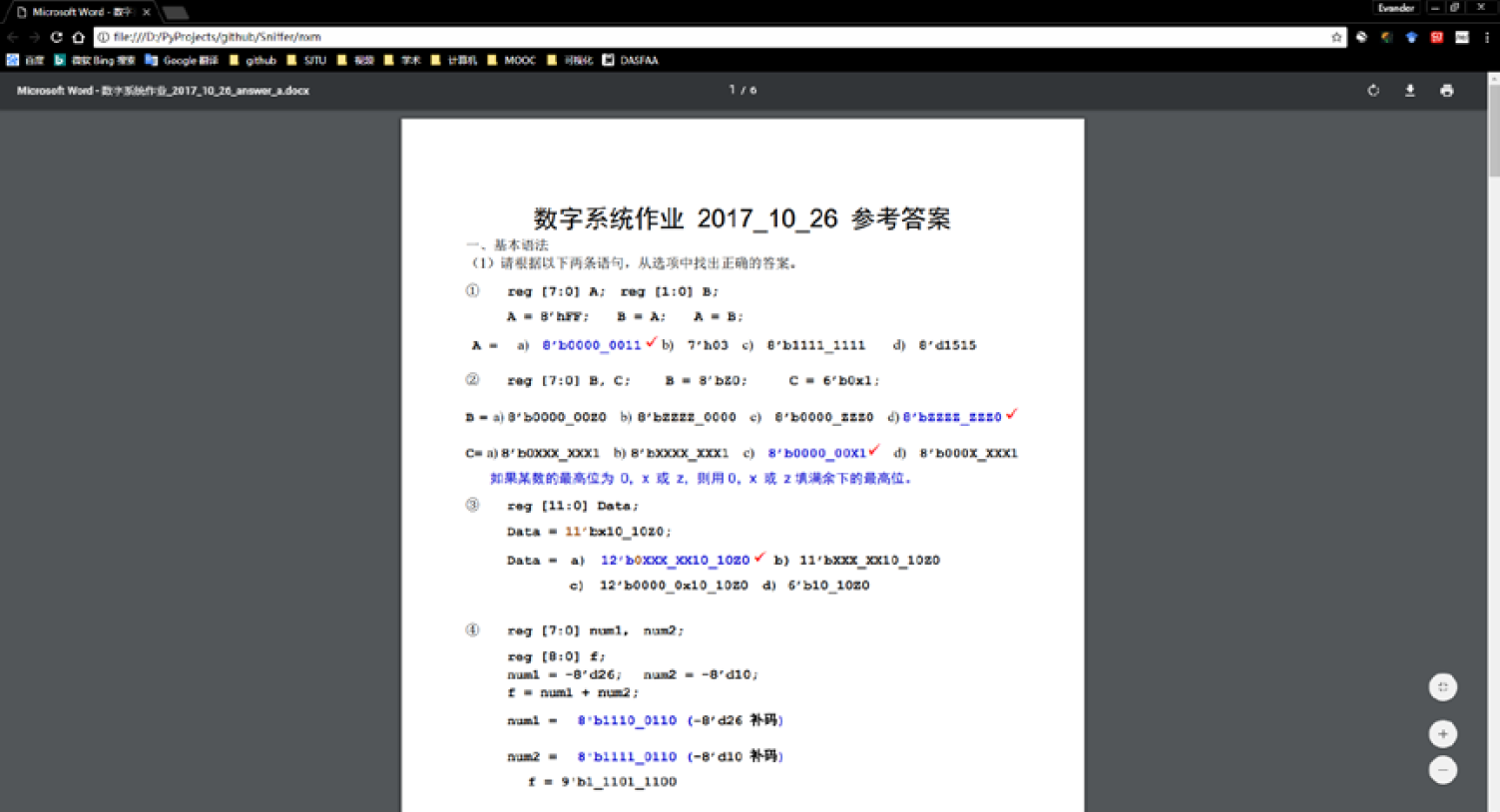
### Formatted Display
Telnet *bbs.sjtu.edu.cn* as example, after tracing TCP stream, we got code and formatted display as you can see:
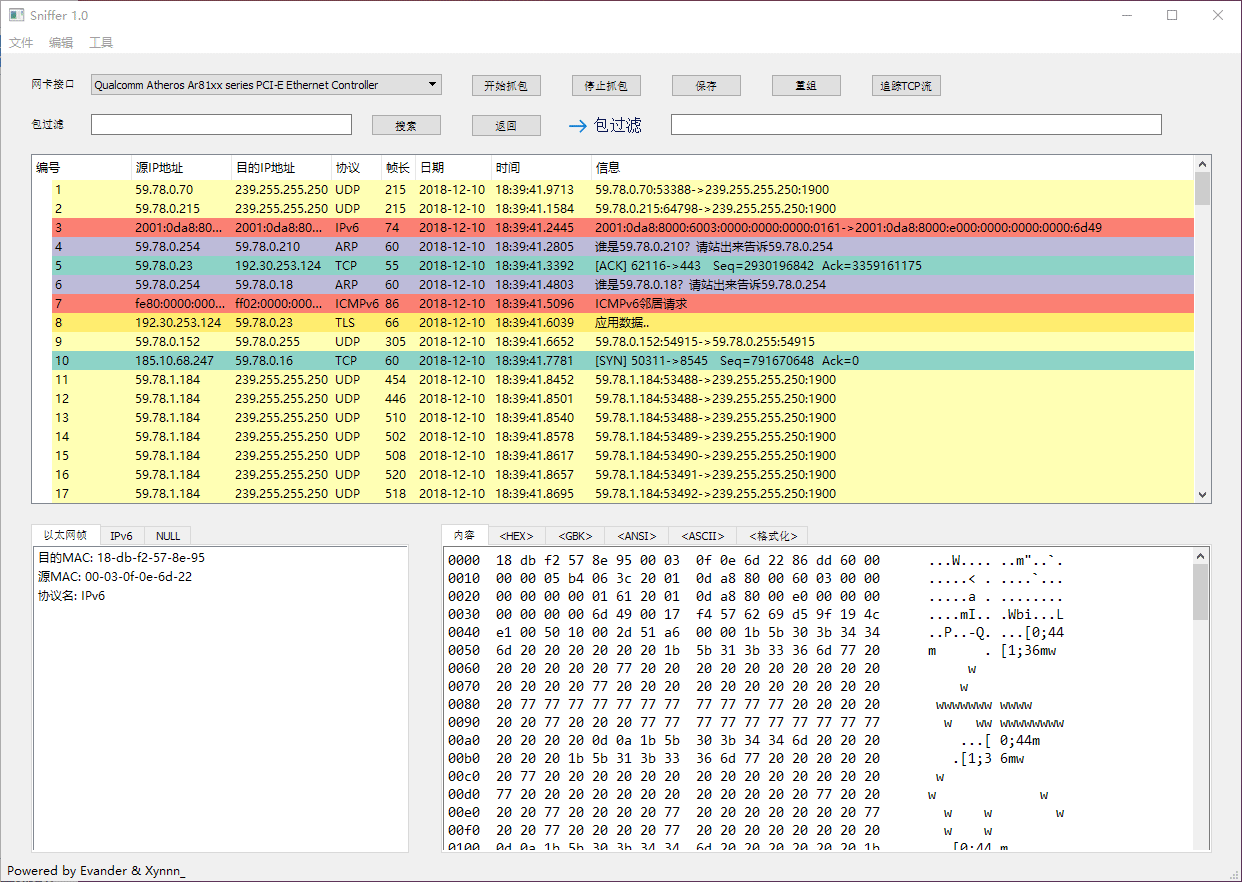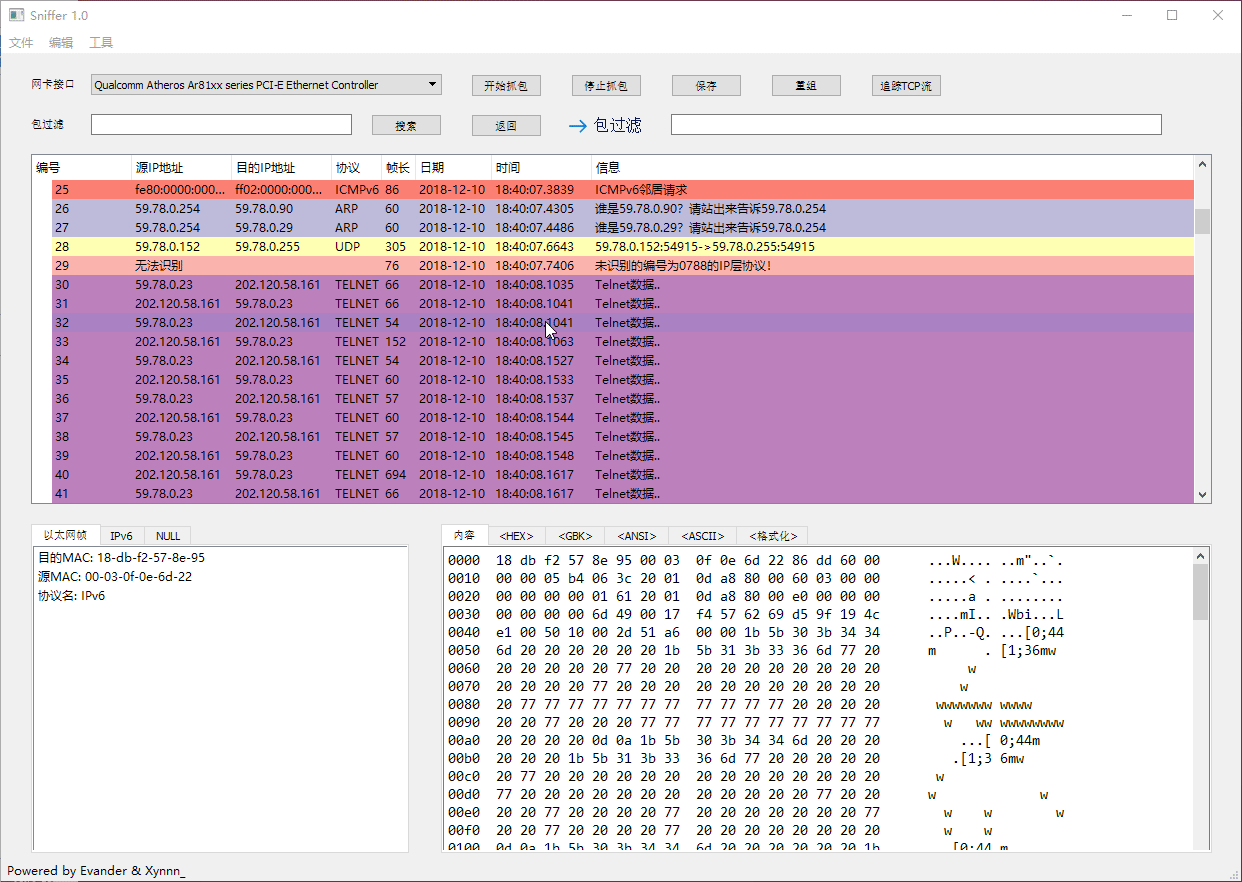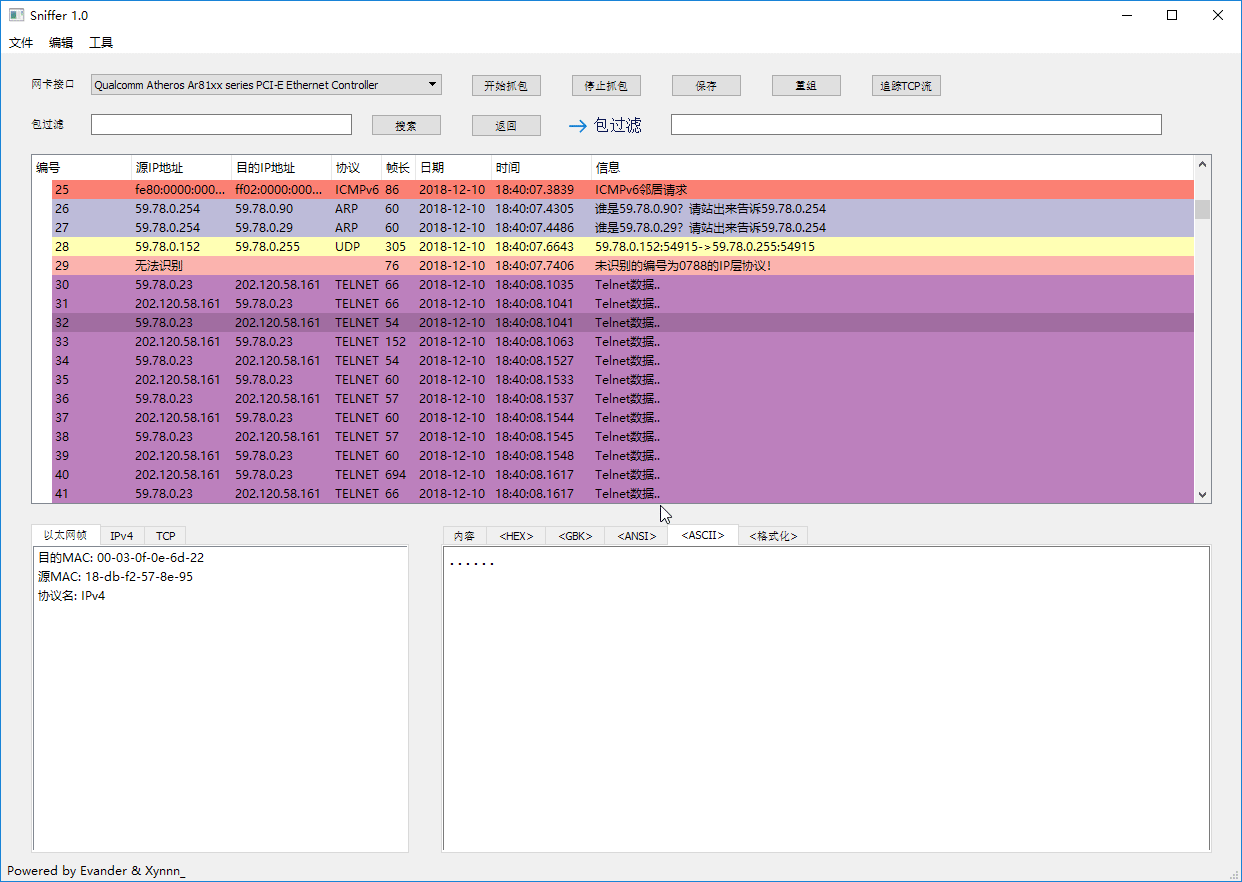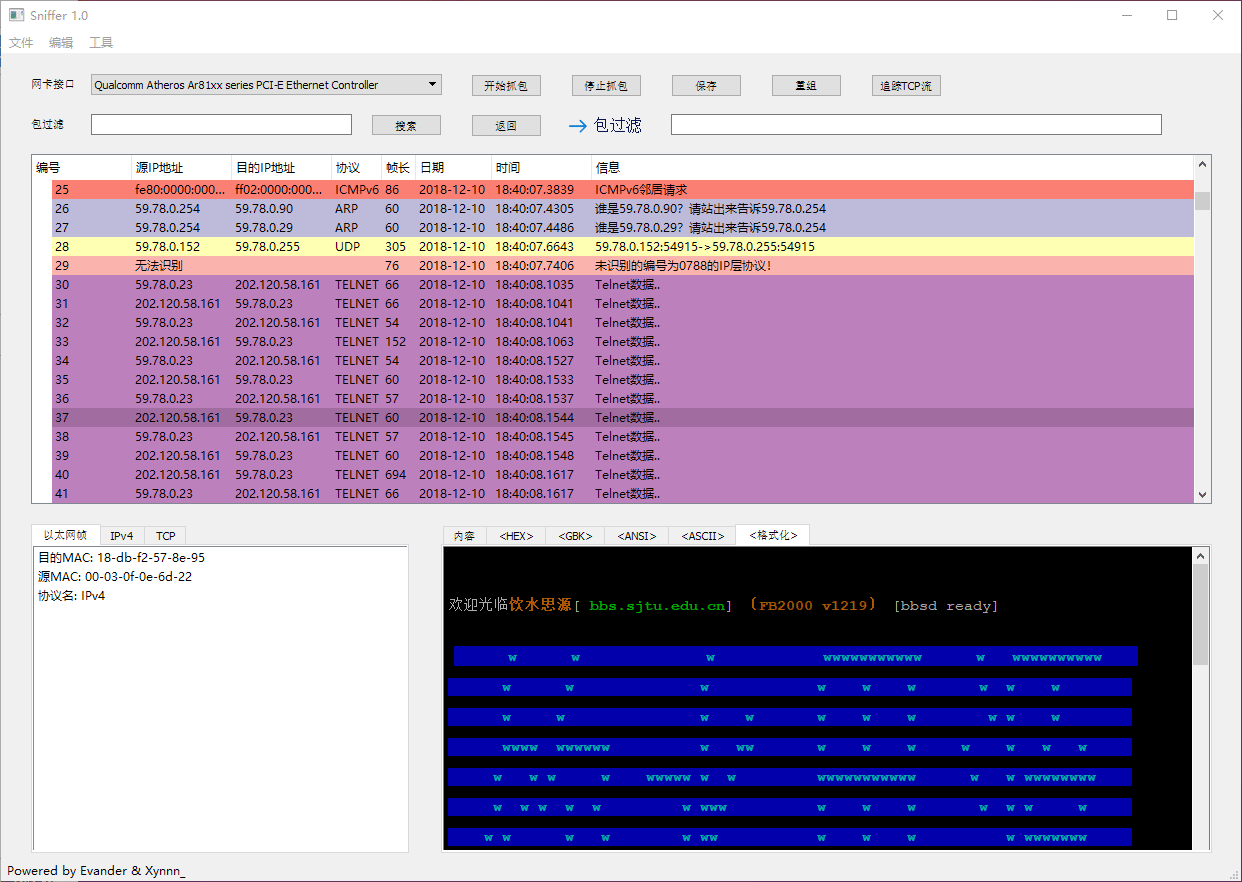
### Saving Capture Log
Click "保存" to save a file named `*.pcap` whereby you make further analysis through [*Wireshark*](https://www.wireshark.org/).
## To be continue
Want to see something else added? [Open an issue.](https://github.com/HaoPeiwen/Sniffer/issues/new)