https://github.com/iann0036/cfn-analyse
CloudFormation static analysis tool.
https://github.com/iann0036/cfn-analyse
aws aws-security cloudformation
Last synced: 4 months ago
JSON representation
CloudFormation static analysis tool.
- Host: GitHub
- URL: https://github.com/iann0036/cfn-analyse
- Owner: iann0036
- License: mit
- Created: 2018-07-13T23:53:56.000Z (over 7 years ago)
- Default Branch: master
- Last Pushed: 2018-12-04T22:37:11.000Z (almost 7 years ago)
- Last Synced: 2025-05-07T10:52:30.665Z (6 months ago)
- Topics: aws, aws-security, cloudformation
- Language: Python
- Size: 15 MB
- Stars: 11
- Watchers: 2
- Forks: 6
- Open Issues: 0
-
Metadata Files:
- Readme: README.md
- License: LICENSE
Awesome Lists containing this project
README
# CloudFormation Analyse #
## Overview
This pipeline enables organizations to impose restrictions on the content of their AWS CloudFormation templates using a [custom ruleset](https://github.com/iann0036/cfn-analyse/blob/master/lambda/rules.yml). It performs evaluation against the set of rules then posts to a Slack channel (usually managers) for them to approve the stack operation. Unlike other tools, the pipeline performs some resolution of Intrinsic Functions before evaluating the ruleset.
## Usage
To use this tool, create a [Slack Outgoing Webhook](https://my.slack.com/services/new/outgoing-webhook) then create a new CloudFormation stack using the cfn-validator-infra.yml file. You will need to provide the webhook URL and the name of a bucket where new stacks are to be uploaded (currently, only Sydney region has the required website files deployed).
Once the stack creation has completed, we're ready to begin. Upload a CloudFormation YAML template to the newly created bucket. If you specify `stackname` as a Tag or Metadata value, it will use this name when creating the new CloudFormation stack, after approval.
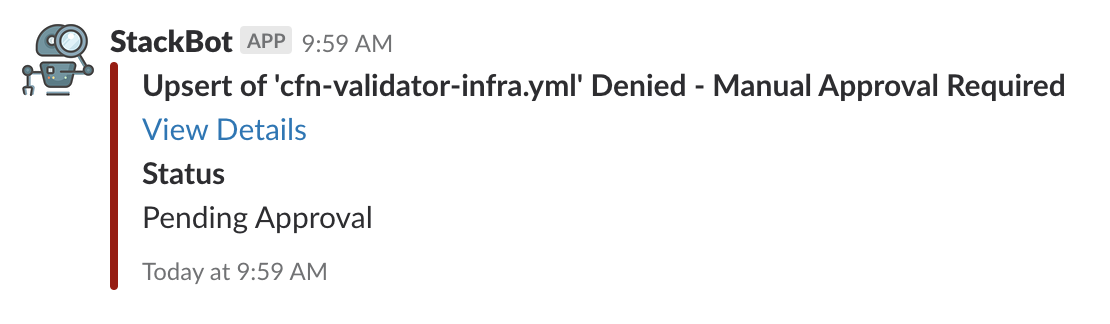
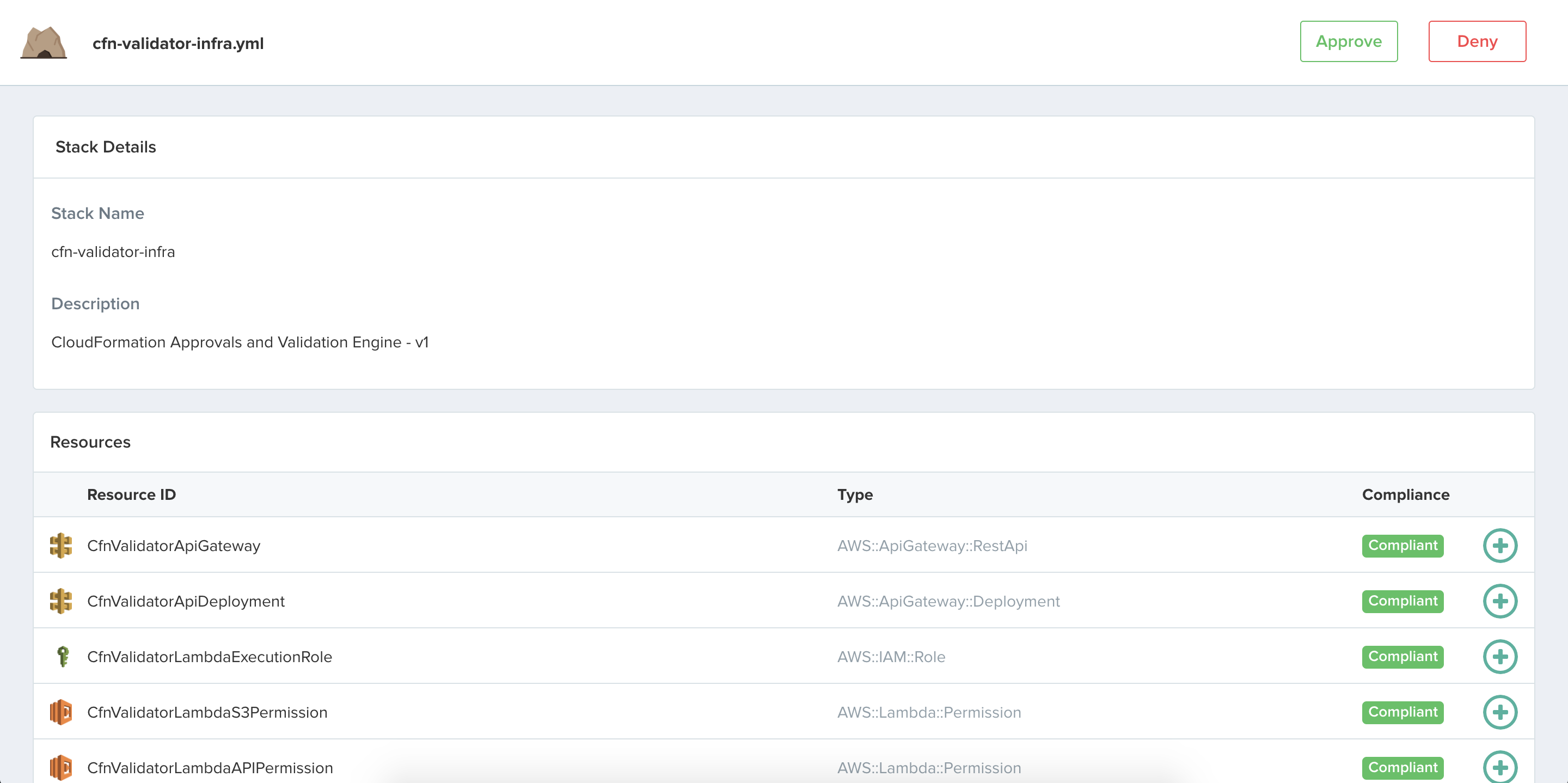
A Slack message will be posted with information and a unique link to perform operations with the stack. Clicking this link will take you to a website where you can review all resources propsed to be created and review each resources compliance with the ruleset.
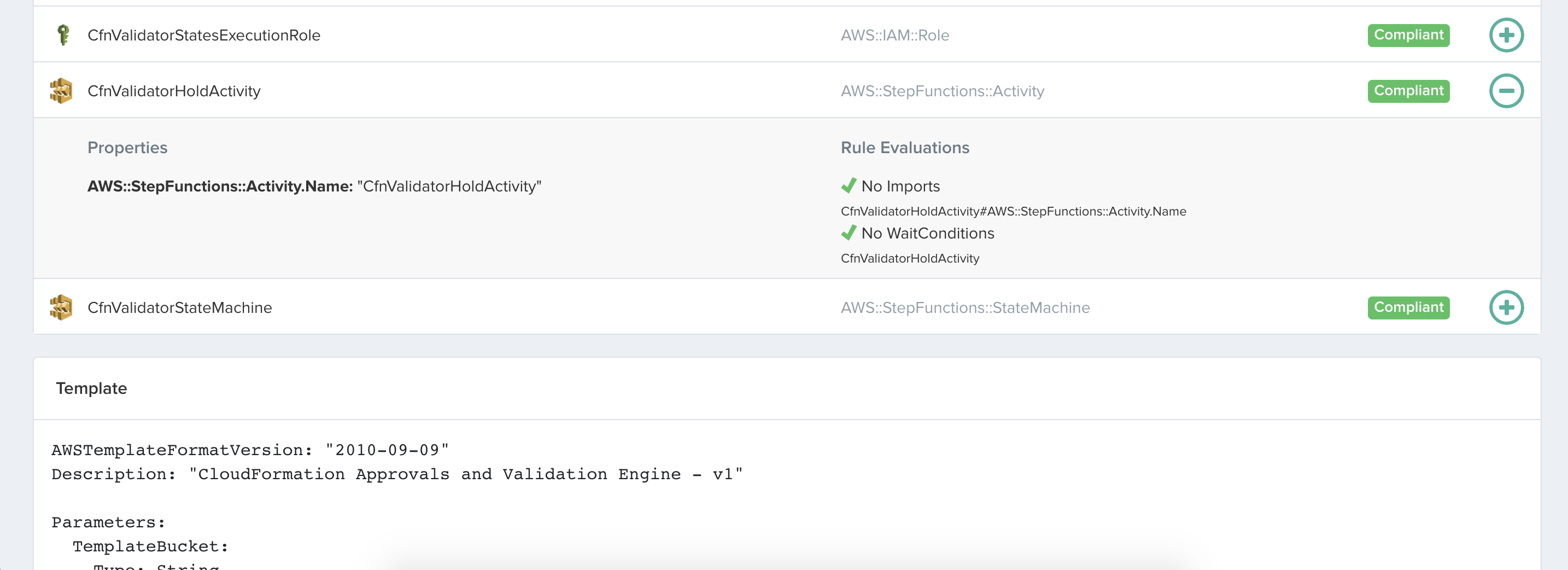
Clicking on a specific resource will expand the row to reveal compliance information and resolved values for each field. Fields with unresolvable information will have that information shown in italics.
Clicking the Approve button will initiate the CloudFormation stack upsert and will track the status of that stack until completion. Once completed, a message will be posted to the Slack channel.
## Technical Implementation
The pipeline uses S3 Event Triggers, which triggers a new Step Function execution used to track progress. The following diagram shows the state machine:
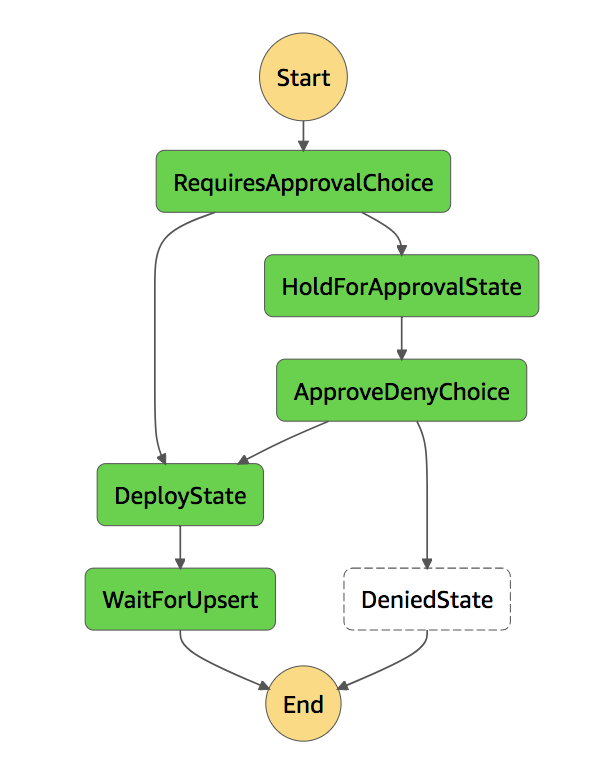
A single Lambda function is deployed to perform operations on all non-activity states. In order to process the users inputs, an API Gateway fronts the Lambda execution for the AJAX calls from the website. Due to the implementation of Step Functions, the execution token is used to uniquely identify the workflow being interacted with.