https://github.com/kapytein/jsonp
jsonp is a Burp Extension which attempts to reveal JSONP functionality behind JSON endpoints.
https://github.com/kapytein/jsonp
burp burp-extensions infosec pentesting
Last synced: 9 months ago
JSON representation
jsonp is a Burp Extension which attempts to reveal JSONP functionality behind JSON endpoints.
- Host: GitHub
- URL: https://github.com/kapytein/jsonp
- Owner: kapytein
- License: mit
- Archived: true
- Created: 2019-08-24T11:58:31.000Z (over 6 years ago)
- Default Branch: master
- Last Pushed: 2021-02-15T10:34:00.000Z (almost 5 years ago)
- Last Synced: 2024-08-02T00:23:02.766Z (over 1 year ago)
- Topics: burp, burp-extensions, infosec, pentesting
- Language: Python
- Homepage:
- Size: 8.79 KB
- Stars: 150
- Watchers: 4
- Forks: 29
- Open Issues: 1
-
Metadata Files:
- Readme: README.md
- License: LICENSE
Awesome Lists containing this project
- awesome-burp-extensions - jsonp - jsonp is a Burp Extension which attempts to reveal JSONP functionality behind JSON endpoints. This could help reveal cross-site script inclusion vulnerabilities or aid in bypassing content security policies. (Vulnerability Specific Extensions / Cross-site scripting)
- awesome-burp-suite - **104**星 - site script inclusion vulnerabilities or aid in bypassing content security policies. (<a id="b6b5b261338c5d44d981bc9f239219f2"></a>工具 / <a id="285c52a4e04dd2f86646c8e1235c9332"></a>工具)
README
# jsonp
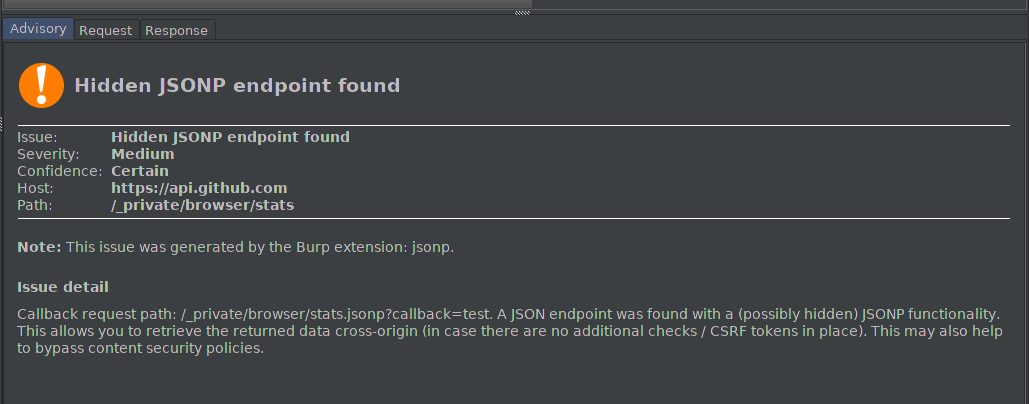
jsonp is a Burp Extension which tries to discover JSONP functionality behind JSON endpoints. It does so by appending parameters and/or changing the extension of the requested URL. The payloads are taken from payloads.txt.
The extension acts as a passive scanner (while it actually is not, since it creates requests based on the original request). For every request responding with `application/json`, the plugin will send `4` altered requests, using the payloads from `payloads.txt`. Only the request path and method will be altered. All requests made by the plugin are using the request method `GET`.
JSONP functionalities (if not restricted) could be used to bypass content security policies. Besides that, in case there's authenticated data, you could attempt a cross-site script inclusion attack if no CSRF token or equivalent is used to migitate the exploitability.
It's common that JSONP functionalities are hidden behind JSON endpoints, as learned on [Liberapay](https://hackerone.com/reports/361951). The template rendered using `jsonp_dump`, which would return valid JSON with content type `application/json` when no `callback` parameter is supplied.
## Installation
The extension is currently not in the BApp Store. You have to install it manually via "Extender > Add".
## Common false-positivies for exploitability
The extension uses the cookies and (possibly additional) authentication headers from the original request. This means that the extension does not detect whether the JSONP functionality on the endpoint is exploitable or not.