https://github.com/kara-4search/bypassamsi_csharp
Bypass AMSI
https://github.com/kara-4search/bypassamsi_csharp
bypass bypass-amsi bypass-windows-defender csharp pentest-tool redteam redteam-tools
Last synced: 6 months ago
JSON representation
Bypass AMSI
- Host: GitHub
- URL: https://github.com/kara-4search/bypassamsi_csharp
- Owner: Kara-4search
- Created: 2021-08-05T08:04:32.000Z (about 4 years ago)
- Default Branch: main
- Last Pushed: 2021-08-08T15:48:30.000Z (about 4 years ago)
- Last Synced: 2025-04-02T17:01:33.645Z (6 months ago)
- Topics: bypass, bypass-amsi, bypass-windows-defender, csharp, pentest-tool, redteam, redteam-tools
- Language: C#
- Homepage:
- Size: 19.5 KB
- Stars: 14
- Watchers: 2
- Forks: 3
- Open Issues: 0
-
Metadata Files:
- Readme: README.md
Awesome Lists containing this project
README
# BypassAMSI_CSharp
Blog link: none
- Bypassing AMSI via "patch memory".
- Tested on x64/x86.
- Steps
1. Locate amsi.dll's address.
2. finding the "DllCanUnloadNow" base on the address
3. Using egg hunt to find the function we need to patch.
4. Patch it with the byte[] "patch64/patch86".
- **You may need modify the code, make sure the code could by the EDR/AVs**
- I only tested on windows defender,works fine.
## Usage
1. Launch through a white-list application
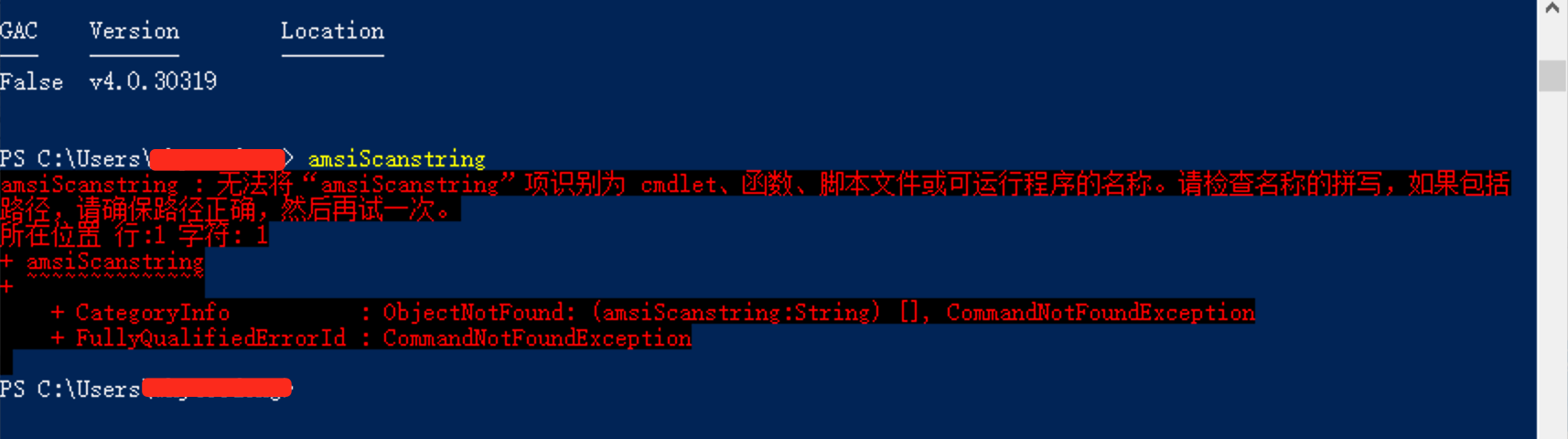
- Without bypassing AMSI
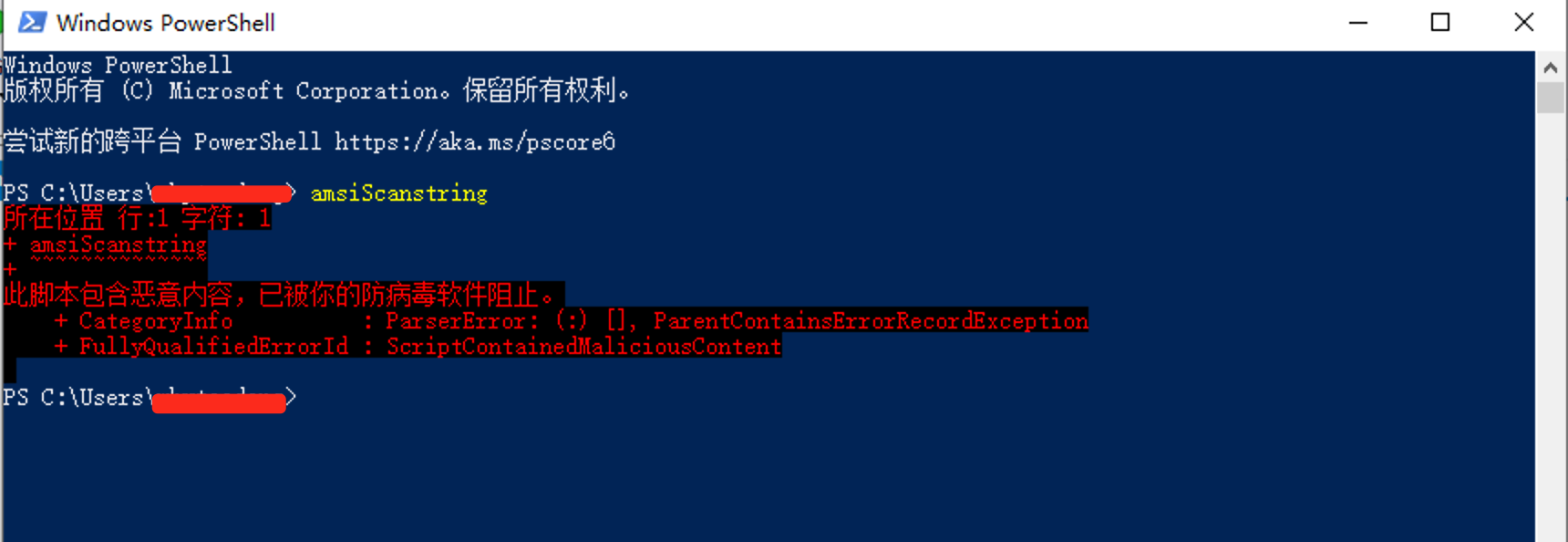
- With Bypassing AMSI
## TO-DO list
- There are indeed other methods to bypass, I may gonna update about that.
- Obfuscated the code.
## Reference link:
None :)
Just Google it, too many documents about bypassing AMSI :)