https://github.com/kgretzky/evilginx2
Standalone man-in-the-middle attack framework used for phishing login credentials along with session cookies, allowing for the bypass of 2-factor authentication
https://github.com/kgretzky/evilginx2
Last synced: 10 months ago
JSON representation
Standalone man-in-the-middle attack framework used for phishing login credentials along with session cookies, allowing for the bypass of 2-factor authentication
- Host: GitHub
- URL: https://github.com/kgretzky/evilginx2
- Owner: kgretzky
- License: bsd-3-clause
- Created: 2018-07-10T09:59:52.000Z (over 7 years ago)
- Default Branch: master
- Last Pushed: 2025-01-21T15:16:19.000Z (about 1 year ago)
- Last Synced: 2025-04-23T17:19:54.337Z (11 months ago)
- Language: Go
- Homepage:
- Size: 6.42 MB
- Stars: 12,886
- Watchers: 317
- Forks: 2,237
- Open Issues: 270
-
Metadata Files:
- Readme: README.md
- Changelog: CHANGELOG
- Funding: .github/FUNDING.yml
- License: LICENSE
Awesome Lists containing this project
- awesome - kgretzky/evilginx2 - Standalone man-in-the-middle attack framework used for phishing login credentials along with session cookies, allowing for the bypass of 2-factor authentication (Go)
- awesome-penetest - Evilginx2 - Standalone Machine-in-the-Middle (MitM) reverse proxy attack framework for setting up phishing pages capable of defeating most forms of 2FA security schemes. (Social Engineering / Social Engineering Tools)
- awesome-entra - Evilginx - Man-in-the-middle attack framework [](https://badgen.net/github/stars/kgretzky/evilginx2) (Tools / CLI)
- awesome-nicc - Evilginx - \"Evilginx is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows to bypass 2-factor authentication protection.\" `BSD-3-Clause` `Windows/Mac/Linux` (Entries / Web)
- penetration-testing - Evilginx2 - Standalone Machine-in-the-Middle (MitM) reverse proxy attack framework for setting up phishing pages capable of defeating most forms of 2FA security schemes. (Social Engineering / Social Engineering Tools)
- awesome-network-stuff - **2829**星
- awesome-termux-hacking - evilginx2 - Standalone man-in-the-middle attack framework used for phishing login credentials along with session cookies, allowing for the bypass of 2-factor authentication.[](https://github.com/kgretzky/evilginx2/stargazers/) (Uncategorized / Uncategorized)
- awesome-pentest - Evilginx2 - Standalone Machine-in-the-Middle (MitM) reverse proxy attack framework for setting up phishing pages capable of defeating most forms of 2FA security schemes. (Social Engineering / Social Engineering Tools)
- awesome-phishing - Evilginx2
- venom - `Evilginx2` - Standalone Machine-in-the-Middle (MitM) reverse proxy attack framework for setting up phishing pages capable of defeating most forms of 2FA security schemes. (Social Engineering / Penetration Testing Report Templates)
- fucking-awesome-pentest - Evilginx2 - Standalone Machine-in-the-Middle (MitM) reverse proxy attack framework for setting up phishing pages capable of defeating most forms of 2FA security schemes. (Social Engineering / Social Engineering Tools)
- awesome-pentest-reference - Evilginx2 - Standalone man-in-the-middle attack framework. (Social Engineering Tools / Penetration Testing Report Templates)
- awesome-go-security - evilginx2 - Standalone man-in-the-middle attack framework used for phishing login credentials along with session cookies, allowing for the bypass of 2-factor authentication. (Phishing)
- awesome-hacking-lists - kgretzky/evilginx2 - Standalone man-in-the-middle attack framework used for phishing login credentials along with session cookies, allowing for the bypass of 2-factor authentication (Go)
- awesome-csirt - evilginx2 - in-the-middle attack framework used for phishing login credentials along with session cookies, allowing for the bypass of 2-factor authentication. (Phishing / Steganography)
- awesome-rainmana - kgretzky/evilginx2 - Standalone man-in-the-middle attack framework used for phishing login credentials along with session cookies, allowing for the bypass of 2-factor authentication (Go)
- awesome-starz - kgretzky/evilginx2 - Standalone man-in-the-middle attack framework used for phishing login credentials along with session cookies, allowing for the bypass of 2-factor authentication (Go)
- awesome-repositories - kgretzky/evilginx2 - Standalone man-in-the-middle attack framework used for phishing login credentials along with session cookies, allowing for the bypass of 2-factor authentication (Go)
- awesome-pentest - Evilginx2 - Standalone man-in-the-middle attack framework. (Social Engineering Tools / Penetration Testing Report Templates)
- cybersecurity-golang-security - evilginx2 - Standalone man-in-the-middle attack framework used for phishing login credentials along with session cookies, allowing for the bypass of 2-factor authentication. (Phishing)
- awesome-pentest - Evilginx2 - Standalone Machine-in-the-Middle (MitM) reverse proxy attack framework for setting up phishing pages capable of defeating most forms of 2FA security schemes. (Social Engineering / Social Engineering Tools)
README

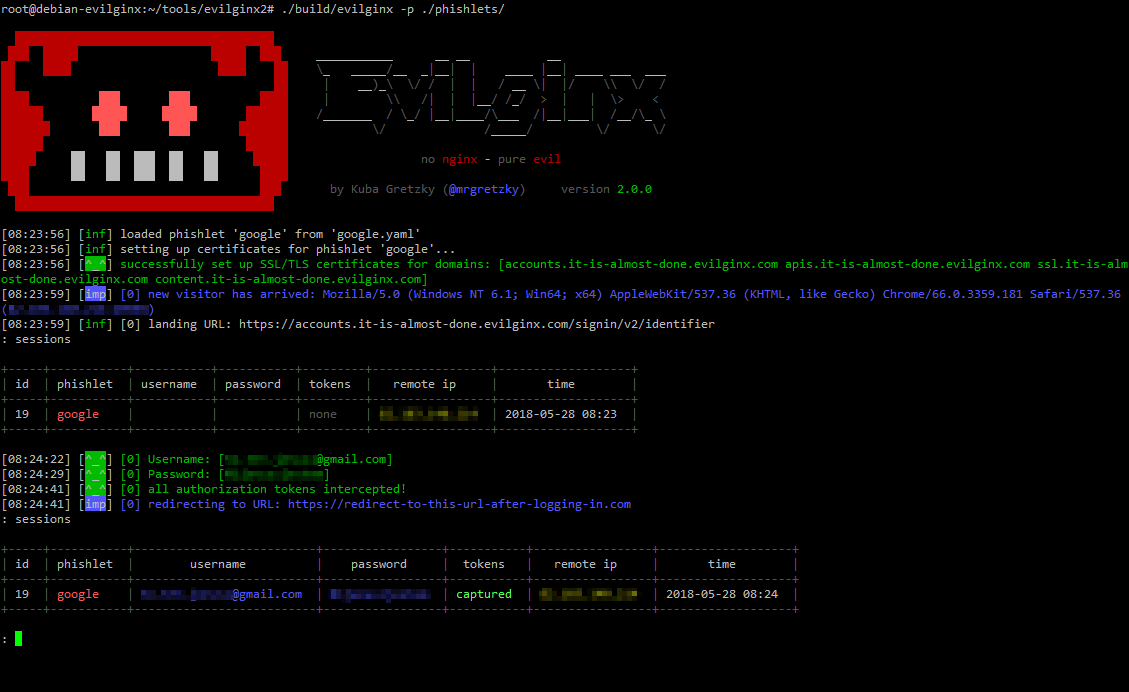
# Evilginx 3.0
**Evilginx** is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows to bypass 2-factor authentication protection.
This tool is a successor to [Evilginx](https://github.com/kgretzky/evilginx), released in 2017, which used a custom version of nginx HTTP server to provide man-in-the-middle functionality to act as a proxy between a browser and phished website.
Present version is fully written in GO as a standalone application, which implements its own HTTP and DNS server, making it extremely easy to set up and use.
## Disclaimer
I am very much aware that Evilginx can be used for nefarious purposes. This work is merely a demonstration of what adept attackers can do. It is the defender's responsibility to take such attacks into consideration and find ways to protect their users against this type of phishing attacks. Evilginx should be used only in legitimate penetration testing assignments with written permission from to-be-phished parties.
## Evilginx Mastery Training Course
If you want everything about reverse proxy phishing with **Evilginx** - check out my [Evilginx Mastery](https://academy.breakdev.org/evilginx-mastery) course!
Learn everything about the latest methods of phishing, using reverse proxying to bypass Multi-Factor Authentication. Learn to think like an attacker, during your red team engagements, and become the master of phishing with Evilginx.
Grab it here:
https://academy.breakdev.org/evilginx-mastery
## Official Gophish integration
If you'd like to use Gophish to send out phishing links compatible with Evilginx, please use the official Gophish integration with Evilginx 3.3.
You can find the custom version here in the forked repository: [Gophish with Evilginx integration](https://github.com/kgretzky/gophish/)
If you want to learn more about how to set it up, please follow the instructions in [this blog post](https://breakdev.org/evilginx-3-3-go-phish/)
## Write-ups
If you want to learn more about reverse proxy phishing, I've published extensive blog posts about **Evilginx** here:
[Evilginx 2.0 - Release](https://breakdev.org/evilginx-2-next-generation-of-phishing-2fa-tokens)
[Evilginx 2.1 - First Update](https://breakdev.org/evilginx-2-1-the-first-post-release-update/)
[Evilginx 2.2 - Jolly Winter Update](https://breakdev.org/evilginx-2-2-jolly-winter-update/)
[Evilginx 2.3 - Phisherman's Dream](https://breakdev.org/evilginx-2-3-phishermans-dream/)
[Evilginx 2.4 - Gone Phishing](https://breakdev.org/evilginx-2-4-gone-phishing/)
[Evilginx 3.0](https://breakdev.org/evilginx-3-0-evilginx-mastery/)
[Evilginx 3.2](https://breakdev.org/evilginx-3-2/)
[Evilginx 3.3](https://breakdev.org/evilginx-3-3-go-phish/)
## Help
In case you want to learn how to install and use **Evilginx**, please refer to online documentation available at:
https://help.evilginx.com
## Support
I DO NOT offer support for providing or creating phishlets. I will also NOT help you with creation of your own phishlets. Please look for ready-to-use phishlets, provided by other people.
## License
**evilginx2** is made by Kuba Gretzky ([@mrgretzky](https://twitter.com/mrgretzky)) and it's released under BSD-3 license.
