https://github.com/korolr/gui-form-brut
GTK3+
https://github.com/korolr/gui-form-brut
brute-force brute-force-attacks bruteforce firefox gtk3 gui linux python python-3 selenium xpath
Last synced: 7 days ago
JSON representation
GTK3+
- Host: GitHub
- URL: https://github.com/korolr/gui-form-brut
- Owner: korolr
- Created: 2017-01-12T19:07:51.000Z (over 8 years ago)
- Default Branch: master
- Last Pushed: 2017-05-02T16:58:14.000Z (about 8 years ago)
- Last Synced: 2025-04-08T19:47:34.394Z (about 1 month ago)
- Topics: brute-force, brute-force-attacks, bruteforce, firefox, gtk3, gui, linux, python, python-3, selenium, xpath
- Language: Python
- Homepage:
- Size: 1.98 MB
- Stars: 23
- Watchers: 2
- Forks: 1
- Open Issues: 0
-
Metadata Files:
- Readme: README.md
Awesome Lists containing this project
README
GUI-brut-form
===================
Brutforce web forms has never been so easy
----------
## Quick start
```
$ sudo pacman -S python-gobject
$ pip3 install selenium
$ python3 main.py
```
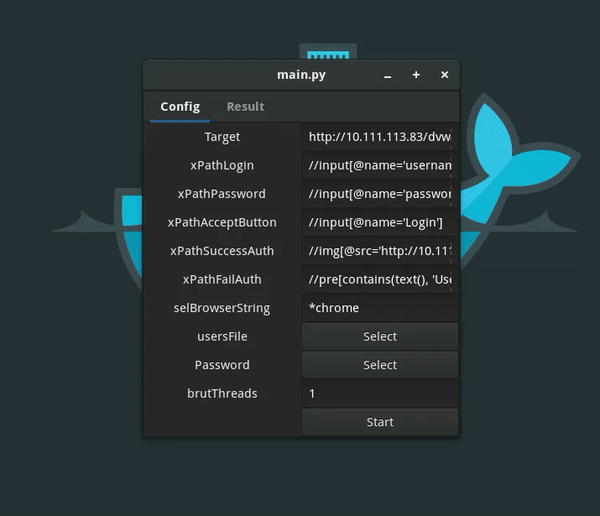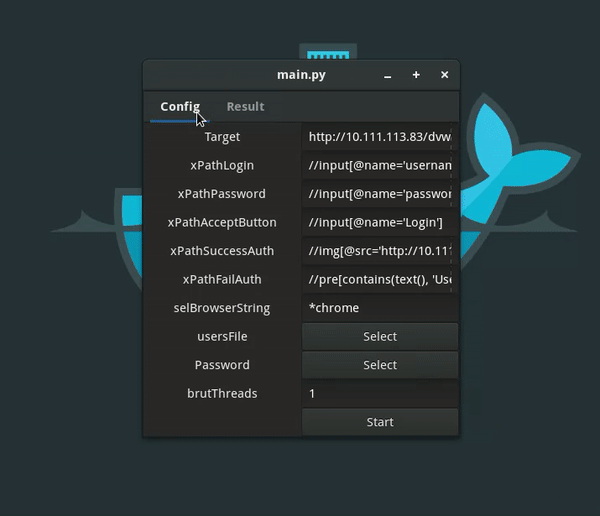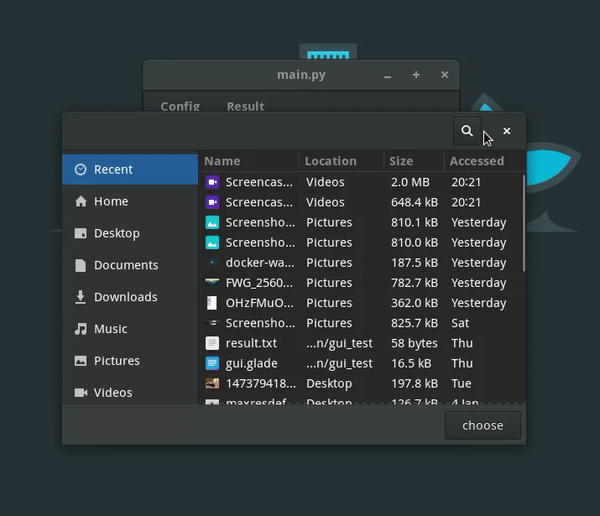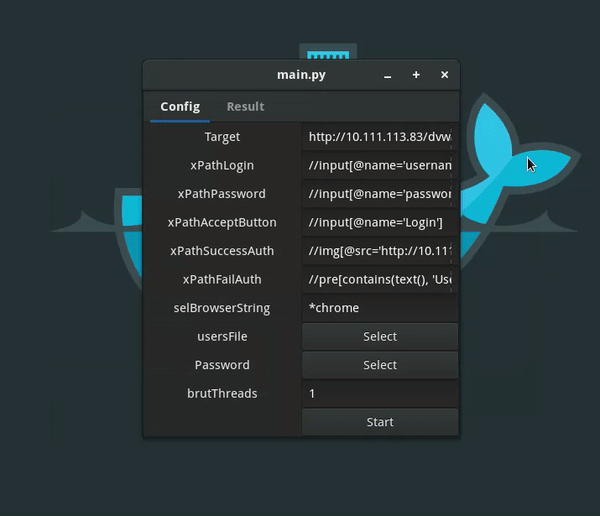
**Preferences**
1. target = 'http://mysite.com/admin/' # target page with a form-based
2. authentication. xPathLogin = "// input [@ name = 'login']" # xPath for the login field.
3. xPathPassword = "// input [@ name = 'password']" # xPath for the field password.
4. xPathAcceptButton = "//input [@ type = 'submit']" # xPath to enter the confirmation button.
5. xPathSuccessAuth = "// a [@ id = 'loginLink']" # xPath fo successful authorization conditions. xPathFailAuth = "// div [@ id ='error']" # xPath authorization failure conditions.
6. selBrowserString = '* firefox' # browser shows Selenium WebDriver which browser you want to run: * firefox, * chrome, * ie.
7. selFFProfile = 'ff_profile' # Profile Mozilla. This option is only used ff. This is a relative path to the directory with the profile. Parameters for brute forcer:
8. usersFile = 'dict / users.txt' # path to a file with a list of
9. usernames. passwordsFile = 'dict / pwd.txt' # path to a file with a list of passwords.
10. resultFile = 'result.txt' # path to the file tooutput the results.
11. brutThreads = 1 # The number of threads to run brute force.