https://github.com/loseys/BlackMamba
C2/post-exploitation framework
https://github.com/loseys/BlackMamba
command-and-control offensive-security pentest pentest-tool post-exploitation pyqt5 python python3 qtframework red-team security-tools spyware
Last synced: 8 months ago
JSON representation
C2/post-exploitation framework
- Host: GitHub
- URL: https://github.com/loseys/BlackMamba
- Owner: loseys
- License: mit
- Created: 2021-02-09T14:09:45.000Z (about 5 years ago)
- Default Branch: main
- Last Pushed: 2021-07-28T13:29:14.000Z (over 4 years ago)
- Last Synced: 2024-08-05T17:45:12.634Z (over 1 year ago)
- Topics: command-and-control, offensive-security, pentest, pentest-tool, post-exploitation, pyqt5, python, python3, qtframework, red-team, security-tools, spyware
- Language: Python
- Homepage:
- Size: 1.59 MB
- Stars: 1,012
- Watchers: 66
- Forks: 154
- Open Issues: 1
-
Metadata Files:
- Readme: README.md
- License: LICENSE
Awesome Lists containing this project
- awesome-hacking-lists - loseys/BlackMamba - C2/post-exploitation framework (Python)
README

BlackMamba
Command and Control
### What's BlackMamba?
Black Mamba is a Command and Control (C2) that works with multiple connections at same time. It was developed with Python and with Qt Framework and have multiples features for a post-exploitation step.
### Some Features
- [x] Multiple clients.
- [x] Real-time communication.
- [x] Encrypted communication
- [x] Screenshot gathering.
- [x] Real-time video capture.
- [x] Locking of client mouse.
- [x] Download and upload of files.
- [x] Keylogger.
- [x] Web downloader.
### Call for Contributions⚠️
Hey, before you go to gallery you need to know that the BlackMamba is a open project, so, if you finds this tool useful and wants to add some functionality, improve the code performance or improve something in the BlackMamba, the best way to get it added is to submit a pull request <3
### Gallery
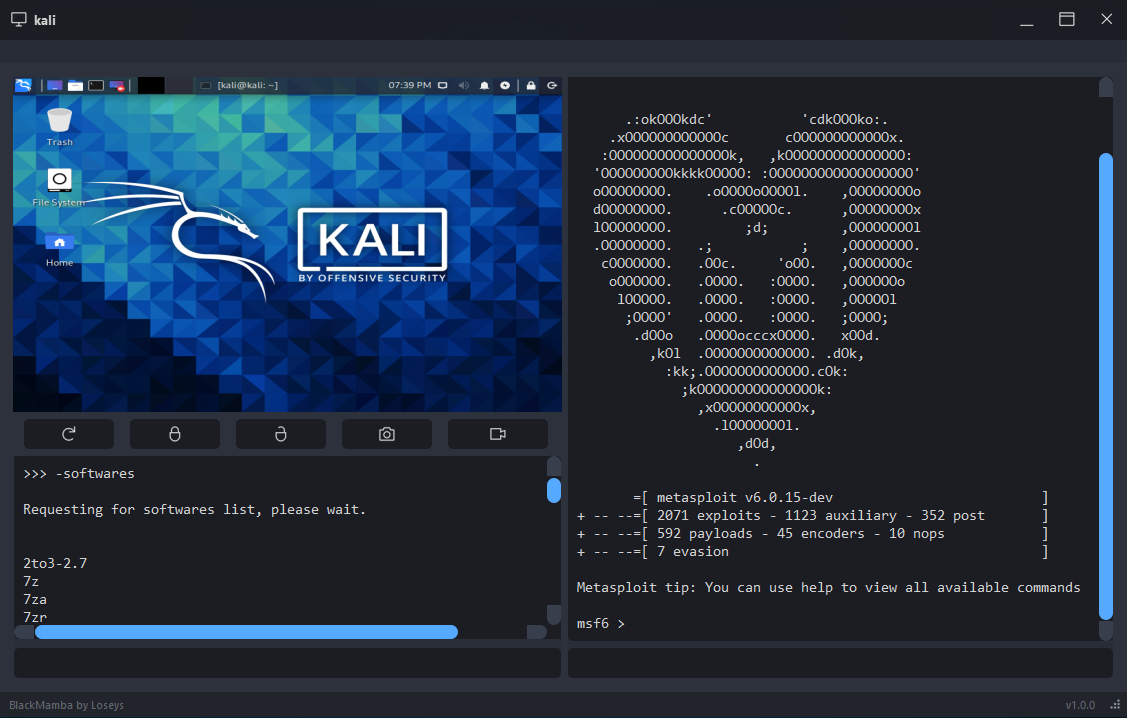


### Installation
1º - Download the BlackMamba;
2º - Install the PIP packages;
pip install -r requirements.txt
3º - Open the port 65000 and 65005 in your Gateway or Router (the port number is optional);
4º - Create an exception in the firewall for BlackMamba or disable it;
5ª - Go to "BlackMamba/bin/profile/socket.txt" and input the port number opened;
SERVER_IP=0.0.0.0
PORT=65000
PORT_VIDEO=65005
>IMPORTANT: Do not change the 0.0.0.0.
6º (OPTIONAL) - Go to the BlackMamba folder and open the "keygen.py" file. Copy the resulting
key and paste in the "BlackMamba/bin/profile/crypt_key.py" ;
The BlackMamba uses a default cryptography key. It is interesting that you change it.
7º - Back to BlackMamba root folder and open the "main.py" file;
WINDOWS
python main.py
KALI LINUX
(sudo chmod 777 main.py)
(sudo python3 main.py)
ANOTHER LINUX
sudo chmod 777 main.py
sudo python3.8 main.py
8º - Click on the button that has a person icon and plus signal;
9º - Input the path where the Python file will be created, input both port numbers and
the IP address (external or local) of your host, then click on the "Create" button.
### Client Installation
After creating the Client script, you'll need to open the script in the host target:
>WINDOWS
python script.py
>GNU/LINUX
1º Download the packages:
scrot -y
python3-pip -y
python3-tk -y
python3-dev -y
2º sudo python3.8 script.py
KALI LINUX
(sudo python3 script.py)
*IMPORTANT: The script of the client does not have persistence. If you want to do persistence, you'll need
to make it by yourself. Another important point is that the client script maybe delay some seconds or few
minutes for connect/reconnect.*
### Author
Gustavo ([Loseys](https://github.com/loseys))
### Acknowledgments, Contributors & Involuntary Contributors
**(In no particular order)**
- [Random Davis](https://stackoverflow.com/users/6273251/random-davis)
- [Wanderson-Magalhaes](https://github.com/Wanderson-Magalhaes)
- [@byt3bl33d3r](https://github.com/byt3bl33d3r)
- **Vitor**
- [cybernobie](https://github.com/cybernobie)
- [w0rk3r](https://github.com/w0rk3r)
- [wesley587](https://github.com/wesley587)


