https://github.com/luccasa/pingcastle-notify
Monitor your PingCastle scans to highlight the rule diff between two scans
https://github.com/luccasa/pingcastle-notify
pingcastle plateforme slack slack-bot teams
Last synced: 3 months ago
JSON representation
Monitor your PingCastle scans to highlight the rule diff between two scans
- Host: GitHub
- URL: https://github.com/luccasa/pingcastle-notify
- Owner: LuccaSA
- License: mit
- Created: 2022-09-13T15:06:16.000Z (almost 3 years ago)
- Default Branch: main
- Last Pushed: 2024-08-08T13:28:01.000Z (11 months ago)
- Last Synced: 2025-03-26T06:34:37.032Z (4 months ago)
- Topics: pingcastle, plateforme, slack, slack-bot, teams
- Language: PowerShell
- Homepage:
- Size: 68.4 KB
- Stars: 109
- Watchers: 8
- Forks: 18
- Open Issues: 5
-
Metadata Files:
- Readme: README.md
- License: LICENSE
Awesome Lists containing this project
README
PingCastle Notify
===
PingCastle Notify is a tool that will monitor your PingCastle reports ! You will be notified every time a change between a scan and a previous scan is made.
How it works ? PingCastle-Notify is a PS1 script that will run a PingCastle scan, compare the difference between a previous scan, highlight the diff and send the result into a Slack / Teams channel or a log file !
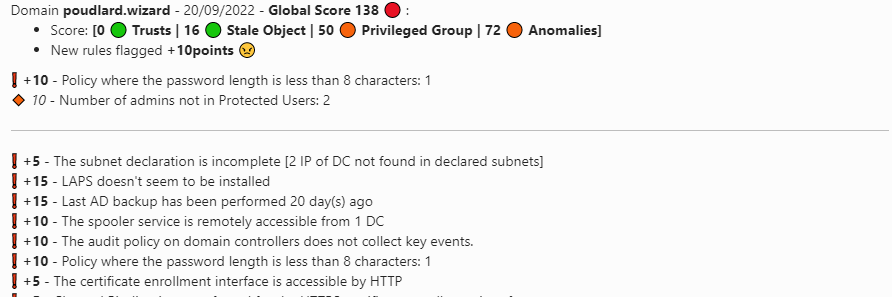
The slack/teams/log message will notify you regarding the different states: correction, recession etc

> :warning: If you don't want to use Slack or Teams set the variable `$teams` and `$slack` to 0 inside the ps1 script. Skip the step "Create a BOT" and check the log file inside the **Reports** folder.
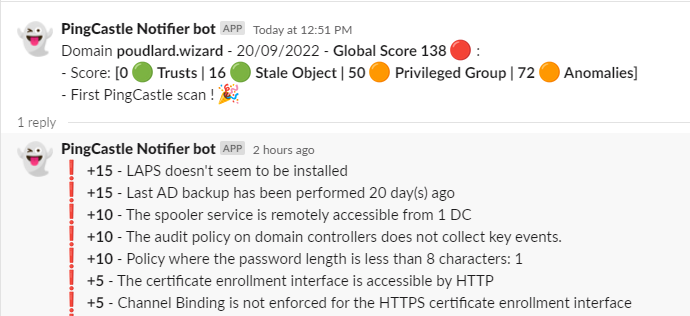
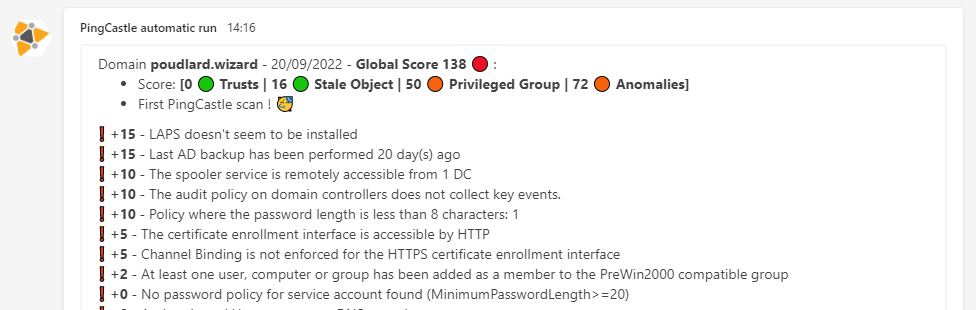
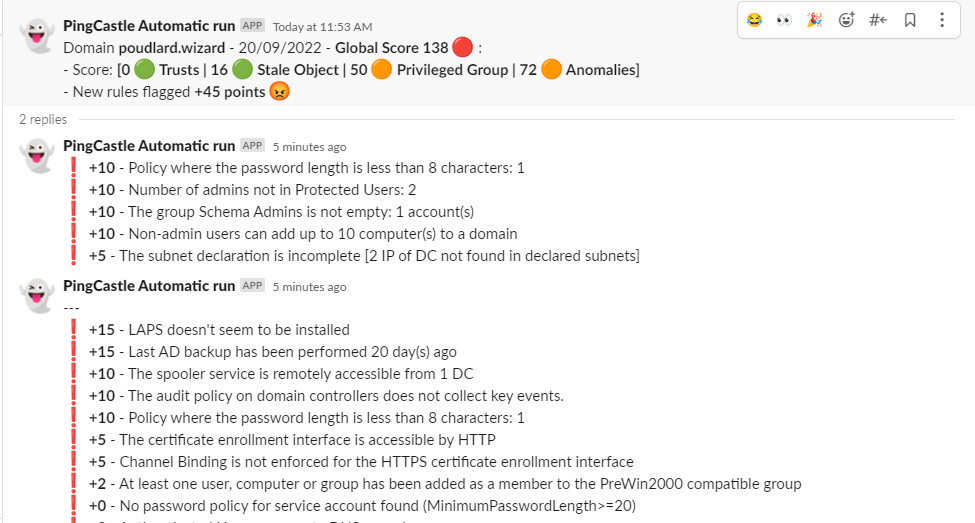
:arrow_forward: First scan
Slack | Teams
:-------------------------:|:-------------------------:
 | 
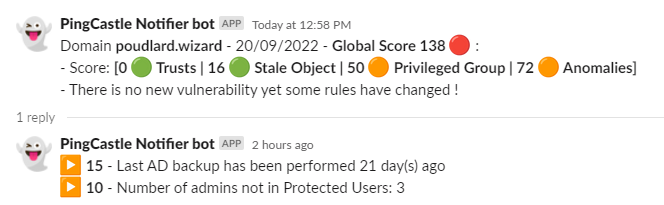
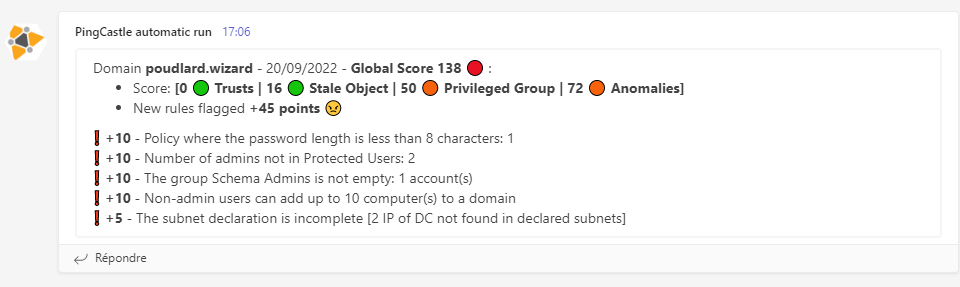
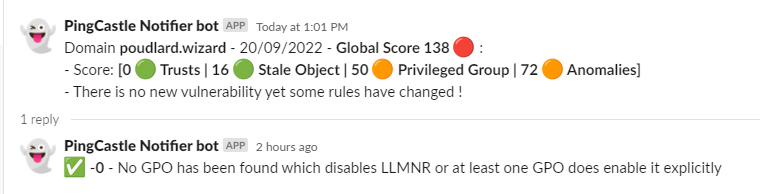
:arrow_forward: No new vulnerability but some rules have been updated
:arrow_forward: New vulnerabilty
Slack | Teams
:-------------------------:|:-------------------------:
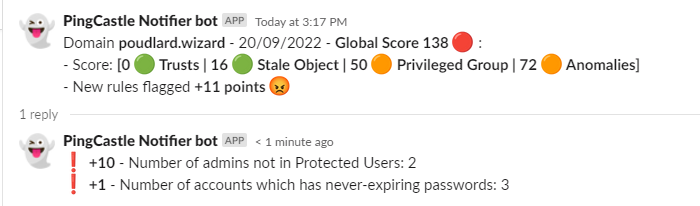 | 
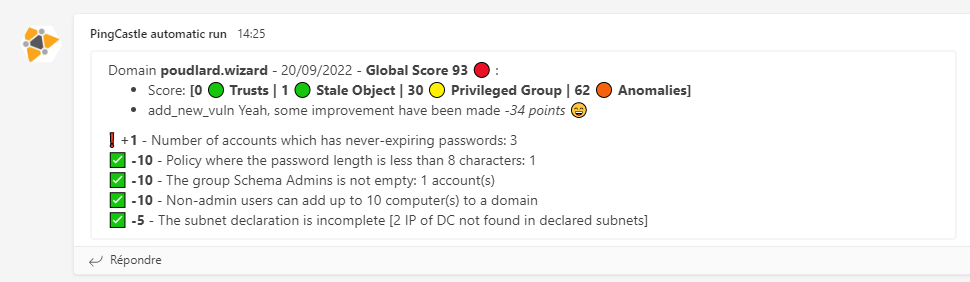
:arrow_forward: Some vulnerability have been removed
Slack | Teams
:-------------------------:|:-------------------------:
 | 
:arrow_forward: No new vulnerability
No result in slack since reports are the same
---
:beginner: Adding the result of the current scan
Set the variable `$print_current_result` to 1 in the script, the rules flagged on the current scan will be added as a thread into Slack or after the rule diff on Teams.
Slack | Teams
:-------------------------:|:-------------------------:
 | 
## How to install ?
### Structure of the project
```
SECU-TOOL-SCAN/
- PingCastle-Notify.ps1
- PingCastle/
- Reports/
- domain.local.xml
- domain.local.html
- scan.logs <-- contains the logs of the scan (diff scan)
- Pingcastle.exe
- ...
```
#### PingCastle & PingCastle-Notify.ps1
1. Download PingCastle
2. Unzip the archive
3. Create a "**Reports**" folder inside the PingCastle folder
4. Download and add the file `PingCastle-Notify.ps1` on the parent directory
#### Create a BOT
:arrow_forward: Slack BOT
1. In Slack create an application https://api.slack.com/apps
2. Add the following rights
- Click on "Add features and functionality" -> Bots (configure the name)
- Click on "Add features and functionality" -> Permissions (add the following permissions)
- Generate a "Bot User OAuth Token" on the Permissions tab
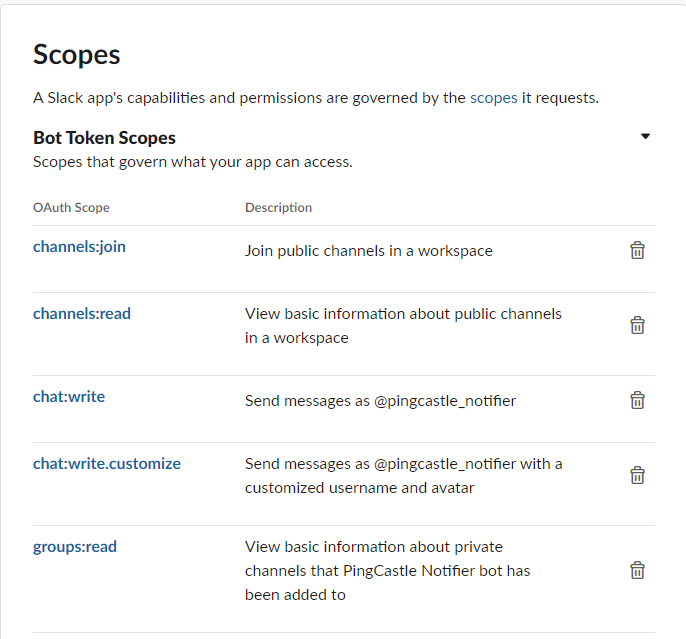
3. Get your token add it to the PingCastle-Notify.ps1 script
4. Create a slack channel and add your bot user to the channel
5. You can test your bot using https://api.slack.com/methods/chat.postMessage/test
6. Add the channel to the script
7. Run the script to test using this command:
`powershell.exe -exec bypass C:\YOUR_PATH\SECU-TOOL-SCAN\PingCastle-Notify.ps1`
:arrow_forward: Teams BOT
1. Create a channel **pingcastle-scan**
2. Click on the "..." dots and select "Connectors"
3. Search for **Webhook**
4. Add the webhook
5. Re-click on the connectors button and on the webhook click **"configure"**
6. Add a title and a logo and click **Create**, copy the wehbook URL
7. Add the url on the variable `$teamsUri`
8. Set the variable `$teams` to 1 and `$slack` to 0
#### Deploy a Scheduled Task
On your Windows Server go to
1. Create a service account that will run the PS1 script every night (no need to set the service account as domain admin)
2. Give privileges to the service account on the folder "Reports"
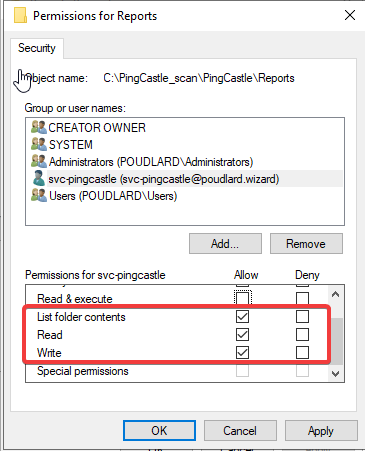
3. Run taskschd.msc to open the Scheduler Task
4. Create a Task and use the service account you just created
5. In Actions tab set "Start a program" -> "Script": `C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe` -> "Arguments" -> `-exec bypass -f C:\PINGCASTLE\Pingcastle-Notify.ps1`
6. Give the permission "Log on as Batch Job" to service account https://danblee.com/log-on-as-batch-job-rights-for-task-scheduler/
7. Run the scheduled task to test the result
8. Enjoy :)



## Acknowledgement
- Vincent Le Toux - https://twitter.com/mysmartlogon
- Romain Tiennot - https://github.com/aikiox
- Lilian Arago - https://github.com/NahisWayard
- Romain Bourgue - https://github.com/raomin
## License
MIT License